this week in security — march 2 2025 edition
THIS WEEK, TL;DR
How North Korea pulled off a billion-dollar crypto heist
Ars Technica: The North Koreans pulled off the biggest heist in history, some $1.4 billion, according to the FBI's official attribution and security researchers who traced the funds. The FBI said [PDF] the rogue state was "responsible" for the theft at Bybit, and blamed the hack specifically on the group known as TraderTraitor (aka Lazarus), which typically targets crypto thefts to fund its sanctioned nuclear weapons program. The hackers stole the funds from Bybit's cold multi-sig wallet (which is supposably offline and requires multiple authorized users to withdraw funds) that relied on manipulating the "signing interface" used to access the cold wallet, suggesting a broad and pretty deep hack of multiple Bybit systems. Details of the attack remain vague but clearly capable of pulling off an unprecedented billion-dollar hack.
More: Bybit | FBI IC3 [PDF] | Trail of Bits | TechCrunch
U.K.'s HCRG breach affects thousands of patients and employees
SuspectFile: A week after U.K. private healthcare giant HCRG (formerly Virgin Care) said it was hacked, the Medusa ransomware gang has taken credit for the breach, saying it has more than 50 terabytes of stolen data — including employees' personal information and patients' private medical records and financial data. Some of the internal data appears to contain references to HCRG's internal Windows network, showing proof of access. HCRG has more than half a million patients across the U.K. so expect this to be a potentially sizable breach. The ransomware gang has threatened to release the data if a ransom of $2 million isn't paid. HCRG still has nothing on its website for individuals affected by the incident.
More: The Register | DataBreaches.net | BBC News
U.S. soldier tried to sell hacked AT&T, Verizon data to foreign government
404 Media ($): From a massive breach of U.K. health data to the missing reams of billions of AT&T and Verizon phone logs... we're back in the U.S. with a filing from federal prosecutors asking that former U.S. Army soldier and telco hacker Cameron Wagenius, who has pleaded guilty, is kept in custody arguing that he presents a flight risk. Per the filing this week, the former soldier apparently searched the web for how to defect to Russia (very bad opsec here) and wanted to sell the information to an unspecified country's intelligence service (we can only guess...). Wagenius made off with most of AT&T's customer phone records for a year, and thousands of Verizon logs as well, proving to be one of the largest breaches of 2024.
More: Bloomberg ($) | Krebs on Security | Cyberscoop
~ ~
THE STUFF YOU MIGHT'VE MISSED
The 'worst' year in internet shutdowns
Access Now: New data from rights group Access Now shows there were at least 296 internet shutdowns across 54 countries throughout 2024, which the group says affected many countries across Africa. Internet shutdowns have been weaponized to prevent information-sharing on the ground (such as documenting abuses) amid war, conflict and authoritarian rule. Axios has some brief yarn.
Qilin ransomware gang takes credit for Lee Enterprises hack
Bleeping Computer: Prolific ransomware gang Qilin has taken responsibility for the hack at Lee Enterprises, the newspaper publishing giant that owns more than 70 media outlets. Lee said some of its critical systems were encrypted (read: ransomware). Qilin posted some of the stolen files on its dark web leak site in an attempt to extort the company. To date, much of the company's internal systems for newsgathering and printing have been knocked offline by the cyberattack.
23 billion credentials stolen by infostealer malware
Troy Hunt: Absolute monster of a leak here: some 23 billion rows of credentials stolen from the ALIEN TXTBASE stealer logs, containing around 493 million unique website and email address pairs of credentials, are now in data breach notification site Have I Been Pwned. (And yet incredibly, this breach still isn't in the site's top 10 data breaches by size.) Malware and infostealer logs are increasingly popular with bad actors; with stolen credentials (and no MFA!), hackers have gained access to customers' data stored on Snowflake, Change Healthcare, and so many mega data stores. All too often folks download dodgy or pirated software that contain password-stealing malware.
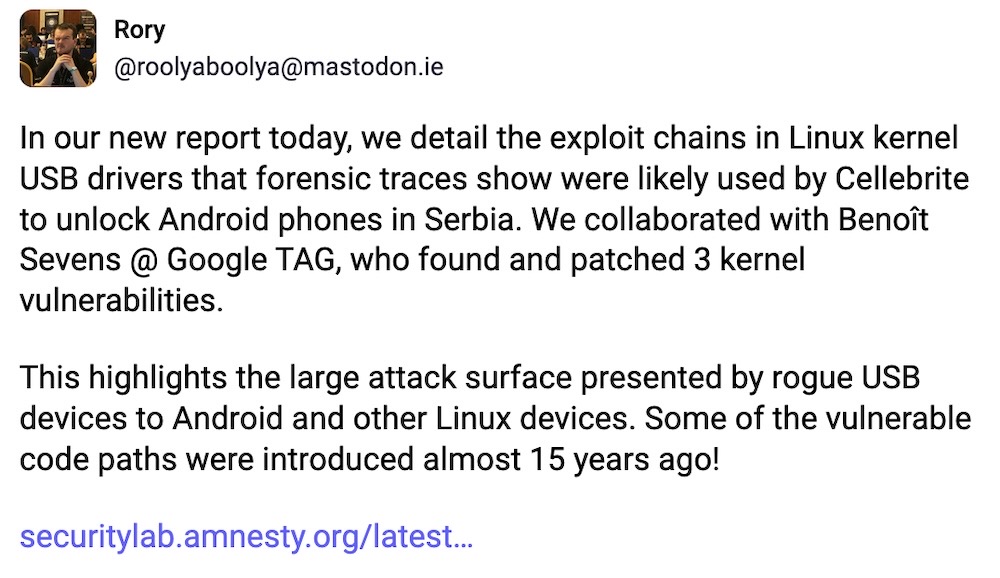
Cellebrite cuts off Serbia after further spyware abuses
Amnesty International: Weeks after Serbian cops were caught red-handed using Cellebrite's phone unlocking tech to break into the phones of arrested individuals to plant spyware, security researchers at Amnesty International caught the cops by doing it again against two further individuals. Cellebrite — which is shocked, shocked to learn that its technology was used for human rights abuses, cut off Serbia, per a statement. In the process, Google fixed three zero-day bugs in Android that Cellebrite's equipment was used to unlock affected phones. (via @tek)
Belgium probing intelligence service email hack linked to China
TechCrunch: The Belgian prosecutor's office is investigating (en français) a breach of the state intelligence agency VSSE by Chinese hackers, who were able to exfiltrate something like 10% of the organization's incoming unclassified emails by way of a bug in Barracuda's email technology.
New Zealand firm blames researcher for company's own leak
JayeLTee: Teammate App, a NZ-based firm, claims a security researcher criminally hacked its database... Just one big problem: The researcher has the receipts, and showed the company had a huge self-owning data exposure from one of its internet-connected databases that wasn't protected with a password. Instead of taking the L, Teammate App's CEO blamed the researcher — wrongly. More words from @GossiTheDog on this latest example of gross corporate behavior.
~ ~
~ ~
OTHER NEWSY NUGGETS
Four out of Five Eyes don't recommend Kaspersky: Australia has become the latest of the Five Eyes intelligence alliance of countries — though notably not New Zealand (yet — afaik!) — to ban Kaspersky products at the government level. The Aussie government said it was due to the "unacceptable security risk" that the software poses, in large part for its connections to Russia. Kaspersky said it was disappointed with the decision. (via Australian Government)
Ransomware gang hits Aussie IVF giant: Sticking with Australia for a minute; one of its largest IVF providers Genea was hacked and experienced a huge data breach amounting to almost a terabyte of data, claimed by a ransomware gang called Termite by publishing some of the stolen files on its dark web leak site. Genea says the hackers compromised its patient management system, so expect a lot of highly sensitive information to have been stolen. (via Genea, The Guardian)
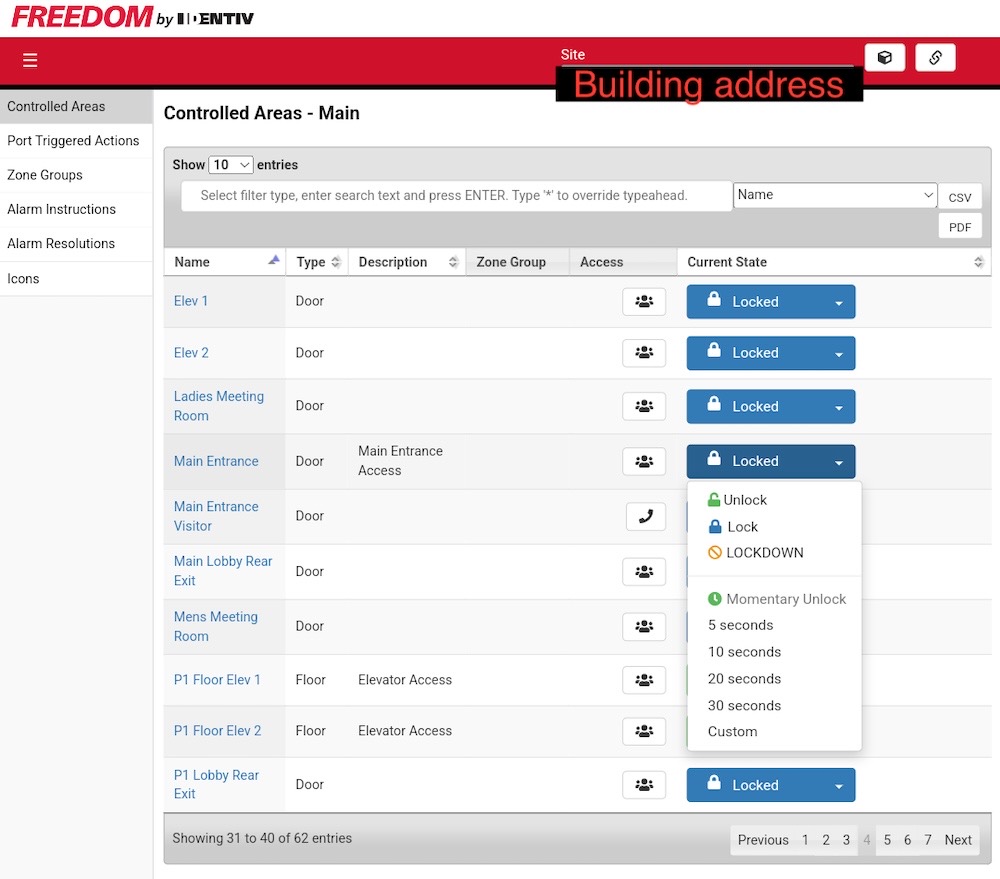
Building access control systems exposed to the 'net: Dozens of apartment buildings across the U.S. and Canada are running a Hirsch-made door access control system connected to the internet but are still using the default password that shipped with it, per Eric Daigle. Yes, default credentials are still a thing — and allowed anyone access to building door locks and elevator access controls. In this case, the company will soon fix the bug. (Disclosure alert: I wrote this story!) This is the same week that security researchers at Modat found thousands of access management systems exposed to the internet — including resident and owners' personal information. (via TechCrunch)
Tower dumps ruling a rare win for privacy: A federal judge in Mississippi says the law enforcement use of "tower dumps," where large swathes of data from cell towers are grabbed and analyzed for criminal activity, is unconstitutional (under the Fourth Amendment). Details of the case remain under seal, but the outcome is particularly good for privacy as cell tower data, much like other bulk collections of data, can include entirely innocent people's data who aren't connected to a crime. Expect appeals, but this is a good sign. An exclusive story via Court Watch, so definitely throw them a subscription if you can. (via Court Watch ($), @campuscodi)
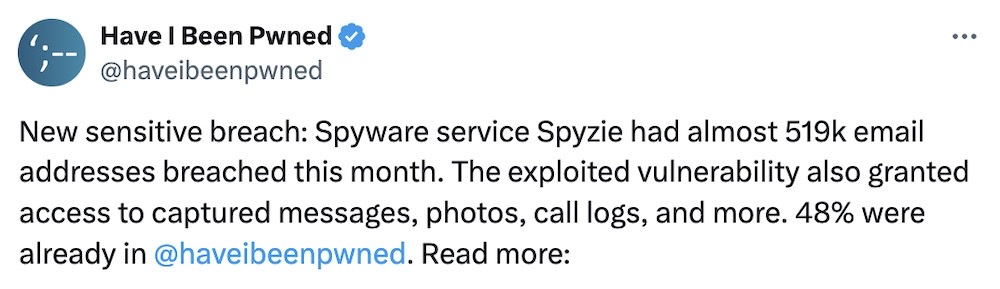
24 reasons not to use stalkerware: Another day, another buggy stalkerware. This time it's Spyzie, the third variant of Cocospy, which shares a common bug that allowed a security researcher to access half a million email addresses of Spyzie customers who use the service to snoop on the phone of someone else (often spouses and romantic partners). These email addresses of abusers are now in Have I Been Pwned. Spyzie was found on both Android devices and iPhones. The stalkerware is now the 24th phone monitoring app since 2017 to have been hacked or exposed its users' data. (Disclosure: I also wrote this!) (via TechCrunch, HIBP)
U.S. halts offensive cyber ops against Russia: The U.S. government has ordered U.S. Cyber Command to "halt offensive cyber and information operations against Russia" amid ongoing negotiations to end the war in Ukraine, which started after Russia launched its full-scale invasion of Ukraine in 2022. The Post cited officials as saying the move was a concession to bring Russia's President Putin to the negotiating table. Espionage continues, per one former official. "The reason you don’t stop espionage is you want to know if they’re lying to you," the former official said. (via Washington Post ($), The Record)
~ ~
THE HAPPY CORNER
A warm, fuzzy welcome to the happy corner... but please, shhh...
This digital sign is an absolute mood.

A lot of folks who work in government have been affected by layoffs and workforce reductions, including cyber and digital folks at CISA, 18F, and GSA among others. Former CISA director Jen Easterly posted on LinkedIn setting up a site matching CISA alumni with hiring employers. The Google Form is here.
And lastly, pour one out for Skype, which Microsoft is retiring on May 5 after more than two decades in operation. Skype was an early pioneer of end-to-end encryption. Skype was... buggy a lot of the time to say the least. Still, I have fond memories of using it almost every day for at least a decade.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Forest, who as you can see... clearly needs all of my passwords, and my Social Security number.... and I see no reason why Forest can't take my credit card, too... you know, for good measure, obviously. With those hypnotic eyes, Forest is a purr-fect social engineer, so here are my car keys, too. Thanks to Irene for sending in!

Keep sending in your cyber-cats! Drop me an email at any time with a photo of your cyber cat (or non-feline friend) along with their name, and they'll be featured in an upcoming newsletter. (Updates are welcome!)
~ ~
SUGGESTION BOX
And that's it for this week's busy update! Thanks so much for reading, it's a joy to write and bring this newsletter every week from the U.S. east coast to you, wherever you are in the world.
By the way... if you like this newsletter, please tell a friend or feel free to forward this email along. I don't do any advertising for this newsletter beyond the occasional Mastodon post, but always keen to reach news readers.
I'll be back next week with everything you need to know from the week. Get in touch if you have anything to share; including any good news and your cyber cats!
Until next,
@zackwhittaker