this week in security — march 20 edition
THIS WEEK, TL;DR
Germany warns against Russian anti-virus use
BBC News: Germany's cybersecurity office is warning organizations across the country against using software made by Kaspersky, a Russian-headquartered antivirus giant. Germany's BSI said (in German) that Kaspersky's antivirus, which to function relies on deep access to its host operating system, could be forced to spy or launch cyberattacks at the request of the Russian government in the wake of the Ukrainian war. Kaspersky said the decision was a "made on political grounds." @hatr, a reporter in Germany, explains more in a tweet thread. The U.S. banned Kaspersky in 2019 citing fears that the firm could be used to spy by Russia.
More: Cyberscoop | @BSI_Bund (German) | @KimZetter
Exposing initial access broker with ties to Conti
Google: Conti hobbles on, seemingly undeterred by a slew of leaks into its own operations, as new victims come to light. Google's Threat Analysis Group dropped new details on an initial access broker (IAB) with ties to the Conti ransomware group. The IAB, dubbed "Exotic Lily," breaks into networks and hands off access to the highest bidder. Cyberscoop breaks down some of the details well. It comes as more leaked details about Conti come to light. The Washington Post ($) has 11 interesting takeaways.
More: Wired ($) | TechCrunch | @andrewcouts
CISA, FBI warn of threats to U.S. satellite networks after Viasat cyberattack
TechCrunch: CISA and the FBI are warning of possible threats to satellite communications (or SATCOM), after the Viasat cyberattack saw thousands of users across Europe and Ukraine without internet access. The outage happened at the time of the Russian invasion of Ukraine, and was a "really huge loss in communications in the very beginning of the war," per Ukrainian cyber official Victor Zhora (via @Bing_Chris). (The Ukrainian military is a big user of satellite communications.) The Viasat hack also knocked out access to turbines across Germany, reports said. CISA warns that U.S. users could also face similar cyberattacks. SATCOMs are used across the U.S. media, government and military, and energy sectors.
More: CISA | SiliconAngle | @thegrugq
Ukraine arrests 'hacker' it says was routing calls for Russian troops
Motherboard: Interesting developments in the electronic warfare side of the Ukraine war this week: Ukraine's security service detained a "hacker" who was helping Russian troops by routing calls on their behalf by leveraging Ukrainian phone networks that are blocking Russian and Belarusian numbers after forces crossed into its territory. @mcdaidc has an interesting tweet thread on the SIM box used in this story. Meanwhile, the maintainer of node-ipc, an open source project downloaded over a million times a week, sabotaged the code to wipe computers that are in Russia and Belarus. The so-called "protestware" was marked as CVE-2022-23812. @josephfcox explains more in another story for Motherboard.
More: Krebs on Security | MidSpike/Github | Ars Technica | @josephfcox
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
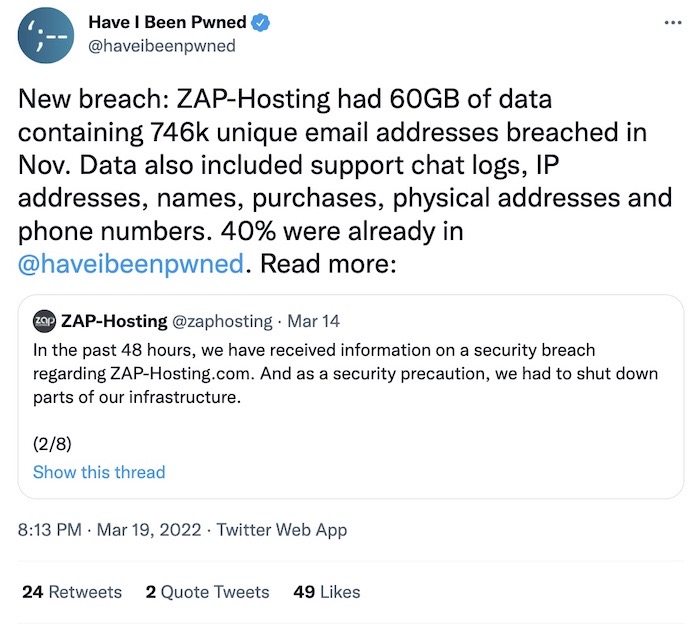
ZAP-Hosting had 60GB of data breached
Have I Been Pwned: Germany-based ZAP-Hosting has confirmed a security breach and has shut down part of its infrastructure. Payment data and passwords were encrypted, the company said in a tweet thread. Have I Been Pwned got wind of the data; it amounts to about 60GB of data, including names, phone numbers, chat logs, email addresses, etc. — just the regular personal information you probably wouldn't want out there.
City hall broken into using code '1234'
Newport News-Times: A woman allegedly broke into Newport City Hall on Monday, using the code “1234” to gain access before damaging the building and contents, reports the Oregonian newspaper. "A large potted plant had been thrown to the floor." Absolute carnage. The city manager claimed the access code was programmed temporarily for a contractor. (Yeah, but for how long are we talking about here?)
Mask unlock is finally live on iPhone as iOS 15.4 arrives
TechCrunch: Finally. With iOS 15.4, now you can unlock your phone while wearing your mask using Face ID on newer iPhones. Face ID lets you unlock your iPhone with your face — which when covered with a mask isn't so easy. It only took Apple two years... @JoannaStern also has a run-down of how the feature works. (It's far from perfect!)

How California is building the nation's first privacy police
The New York Times ($): Here's a profile of Ashkan Soltani, a former researcher and chief technologist at the FTC, who now "faces the daunting task of overseeing the first government body in the United States with the sole job of regulating how Google, Facebook, Amazon and other companies collect and use data from millions of people." Soltani is the first head of the California Privacy Protection Agency, which will enforce the state's privacy law, one of the strictest in the country.
~ ~
OTHER NEWSY NUGGETS
Lawmakers probe early release of top Russian hacker: Here's the curious case of Russian cybercriminal Aleksei Burkov, who after being extradited to the U.S. and jailed for nine years was curiously released just a year into his sentence. The big question is why, and lawmakers want to know. Burkov was once one of Russia's most elusive hackers, and was for a time a pawn in a diplomatic spat that saw him floated for a potential prisoner exchange. Much of his court docket is sealed. Where did his sentence go?
Ukrainian hackers say HackerOne blocked payments: Ukrainian hackers and security researchers said HackerOne was withholding bug bounty rewards, citing U.S. sanctions against Russia and Belarus, but which don't affect Ukrainians. Hackers said they were unable to withdraw in some cases thousands of dollars in earnings. HackerOne CEO's tweets (which he later deleted and recast) and support staff added to the confusion, but HackerOne said it would resolve the situation "within the week." (Disclosure: I wrote this story.) Turns out companies don't know sanctions work. Thankfully we have some solid analysis from @k8em0 on the bug bounty front.
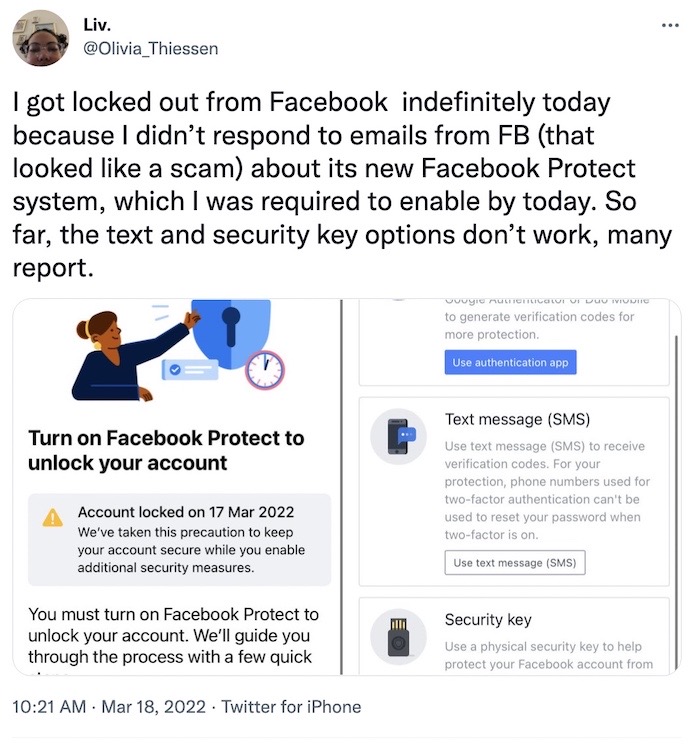
Facebook forgets how to security: Last year Facebook said it would mandate that some high risk accounts use two-factor authentication and that they would be locked out of their accounts if they didn't. It was an ultimatum at the time. But Facebook flubbed the process completely, sending users emails from non-Facebook.com domains, which many thought was spam (and ignored — you know, that thing people are supposed to do!). Behold, this week rolls around and a lot of people are understandably pissed at being locked out of their accounts.
Firms must quickly report hacks to DHS in new law: A new $1.5 trillion funding package signed into law this week by President Biden includes a provision that mandates critical infrastructure operators to notify Homeland Security of data breaches within 72 hours of discovery, or any ransomware payments within 24 hours, reports Bloomberg ($). The aim is to help officials get better insights into global hacking events. But the FBI isn't happy that DHS gets the first cut of the data, even though CISA boss @CISAJen said the DHS would "immediately" share the goods.
The deepfakes have arrived: A Ukrainian TV outlet claimed its live broadcast and website were hacked with a chyron falsely claiming the country had surrendered, according to Motherboard. At the same time, a deepfake of Ukrainian president Zelenskyy appeared this week of him apparently surrendering (he didn't, he's long said he would not surrender to Russia). No one has claimed responsibility for the alleged hack or the fake video, but it's looking like deepfakes are now part of the information war. This week also saw U.K. defense secretary Ben Wallace and home affairs secretary Priti Patel apparently targeted by "imposter" video calls who managed to get through to Wallace via "another government department." Per the BBC, the video call was "fairly sophisticated" that was not made to Wallace's own mobile phone. Deepfakes are going to pose a considerable security risk when they inevitably start to work.
~ ~
THE HAPPY CORNER
If you ever wondered what a walk signal offering bad password policy advice sounds like, well, look no further than Crystal City, VA. Luckily, there's an explanation.
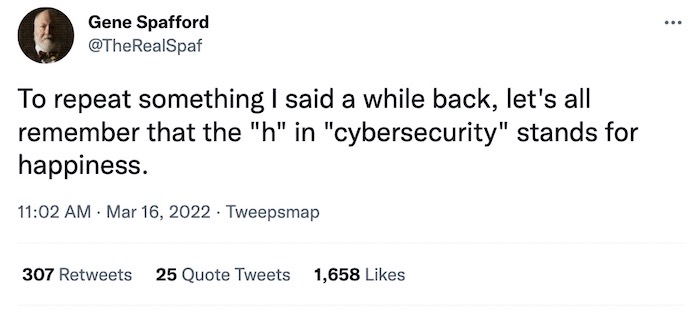
And finally this week. The "h" is silent.
To submit good news for the happy corner, reach out: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Carol. Don't look directly into her eyes, she knows things — like your password. Too late, she's already in your email. A big thanks to Rachael B. for the submission!

Keep sending in your cyber cats (and their friends!). Drop me an email here with their name and photo, and they will be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's it for this busy week. If you have any feedback, feel free to drop it in the suggestion box or send me an email. I'll be at Shmoocon in Washington DC so say hello if you see me.
Have a great week, and see you next.