this week in security — march 23 2025 edition
THIS WEEK, TL;DR
Paragon spyware used by at least six countries to snoop on civil society
Citizen Lab: The boffins at Citizen Lab are back with a new report into Paragon's spyware, dubbed Graphite, which breaks into phones and specifically targets their messaging apps, like WhatsApp (rather than the whole device) to access a target's private messages. The report focuses on at least six governments that likely have access to Graphite (based on its technical analysis via a tip from a "collaborator"), including Canada and Australia; as well as the victims, some of which include a cluster of Italians and those working as human rights defenders in Italy (which is also a Paragon customer). Paragon claims it only pitches its tech to the U.S. and its allies (both a large list and one that's increasingly narrowing), but clearly even ostensibly "responsible" spyware makers are a myth — if anything a paradox, no such thing really exists. The report helped Meta fix a zero-click flaw in WhatsApp, which notified over 90 people that they were targeted by the spyware.
More: Washington Post ($) | TechCrunch | Amnesty | Dark Reading | @billmarczak
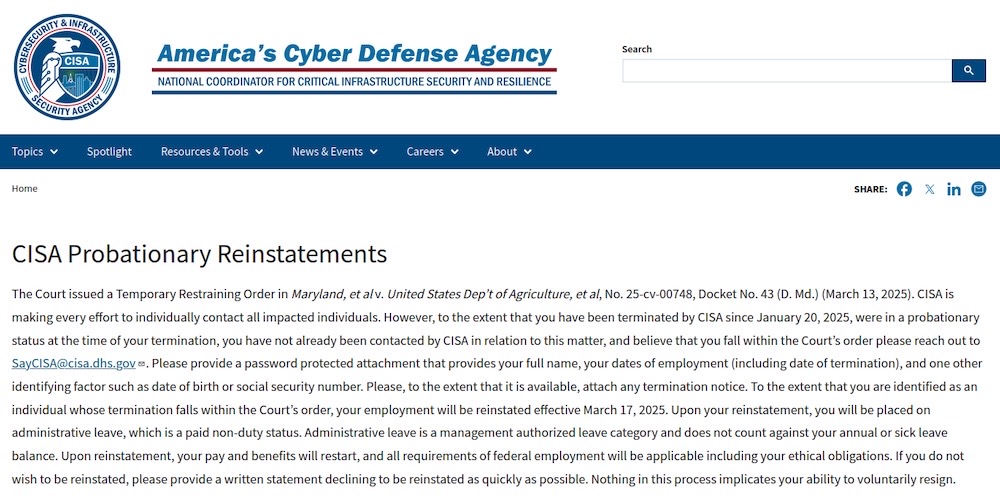
CISA scrambles to contact fired staff after court rules layoffs 'unlawful'
TechCrunch: A message posted to the top of CISA's homepage on Tuesday asked probationary staff that had been previously fired by DOGE to get in contact with the agency, after a court ruled the firings were "unlawful" and that staff must be reinstated. CISA said in the message it's seeking to contact the since-fired employees, implying the federal agency doesn't know who got fired or has everyone's contact information. CISA also asked staff to send a "password protected attachment" containing personal information to prove its them — but didn't specify how (remember: email is largely unencrypted as it travels the web). Meanwhile: USAID staffers say they've been stranded with laptops full of highly sensitive (albeit unclassified) information after their firings, amid fears that the data could get lost or fall into the wrong hands.
More: Krebs On Security | The Verge | @skiles posts
Trump administration begins shifting cyberattack response to states
WSJ Pro ($): An executive order out this week directs the White House to draw up a national resilience plan that shifts responsibilities for cybersecurity to the states and local level. That's... certainly a choice. MS-ISAC (which helps to share threat intelligence at the local level) says the cuts will leave state governments exposed to nation-state threats, given that states are very much on the "front lines" of protecting critical infrastructure. Experts say losing federal resources could result in lost visibility, from known exploited flaws to other vulnerabilities. This order also comes in the same week that the New York Times ($) had a great read on /r/fednews, the Reddit subreddit dedicated to helping feds, which has been a source of truth and support with government layoffs over recent weeks.
More: White House | BankInfoSecurity | The Guardian
~ ~
THE STUFF YOU MIGHT'VE MISSED
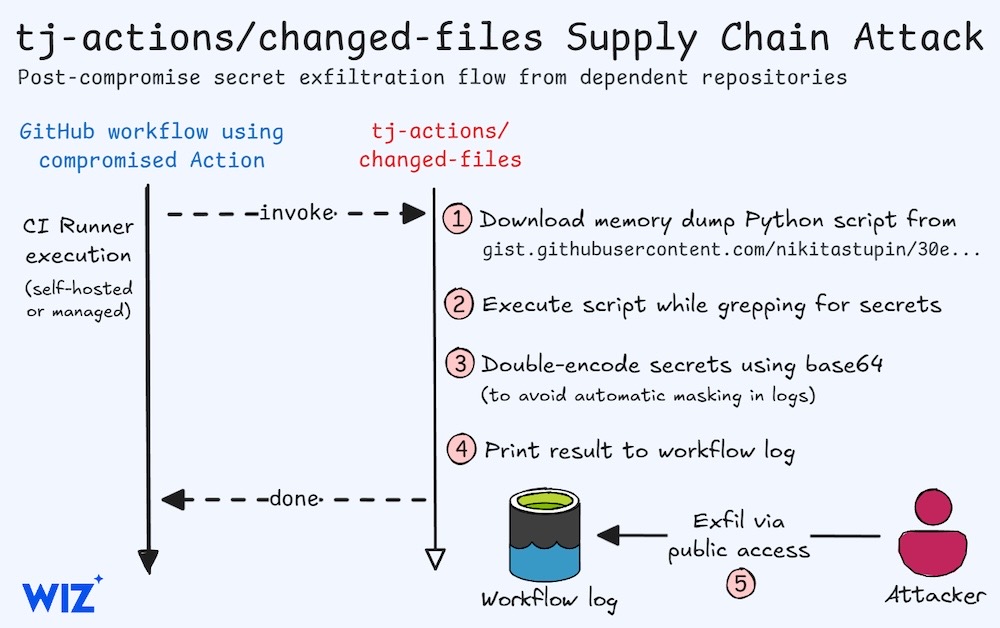
Enterprises scramble after open source code hit by supply chain attack
Ars Technica: Open source software used by at least 23,000 orgs called tj-actions/changed-files was hit by a supply chain attack, allowing malicious hackers to takeover the maintainer's account (around 4pm UTC on March 14). tj-actions/changed-files is widely used in the continuous development process. The compromised package was corrupted to include credential-stealing code. More from Step Security, which first discovered the attack, and Palo Alto, which says one of the initial attacks targeted Coinbase. (via @campuscodi)
North Korea launches new cyber unit with AI-focus
Daily NK: Yes, now even the North Koreans are going all-in on AI (not that they weren't already), according to a source close to the regime telling Daily NK, a news outlet that focuses on North Korea. Much of the unit, known as Research Center 227 (a name that just rolls off the tongue), will focus on information theft and the regime's efforts to steal "digital assets," aka crypto. You know what I'm going to say... North Korea literally only wants one thing and, well, you know the rest.
Nakivo backup unauthenticated bug under attack
watchTowr Labs: A bug in Nakvio's backup and replication software has an absolute path traversal flaw, tracked as CVE-2024-48248, which is being exploited in attacks to steal backups and other sensitive internal corporate data, per watchTowr, the security research firm with A+ meme game. Bleeping Computer has a tl;dr. CISA (or whoever's left) put out a note adding the bug to its Known Exploited Vulnerabilities database, which means federal agencies have to patch the bug on their own systems ASAP.
Oracle's data breach denial leaves questions unanswered
Bleeping Computer: Back with Bleeping, as it reports that Oracle is denying a data breach following a claim on a hacker forum claiming a breach of 6 million data records allegedly relating to Oracle's Cloud single sign-on servers. As evidence, the threat actor published data including LDAP files and the list of companies that had data allegedly stolen from the Oracle SSO platform. Oracle said there has been "no breach" and the published credentials are "not for Oracle Cloud." But Oracle couldn't (and still hasn't) explained how the threat actor was able to plant their email address on an Oracle SSO server's endpoint (since offlined). Hmmm! A curious one indeed, and Oracle still has explaining to do.
~ ~
OTHER NEWSY NUGGETS
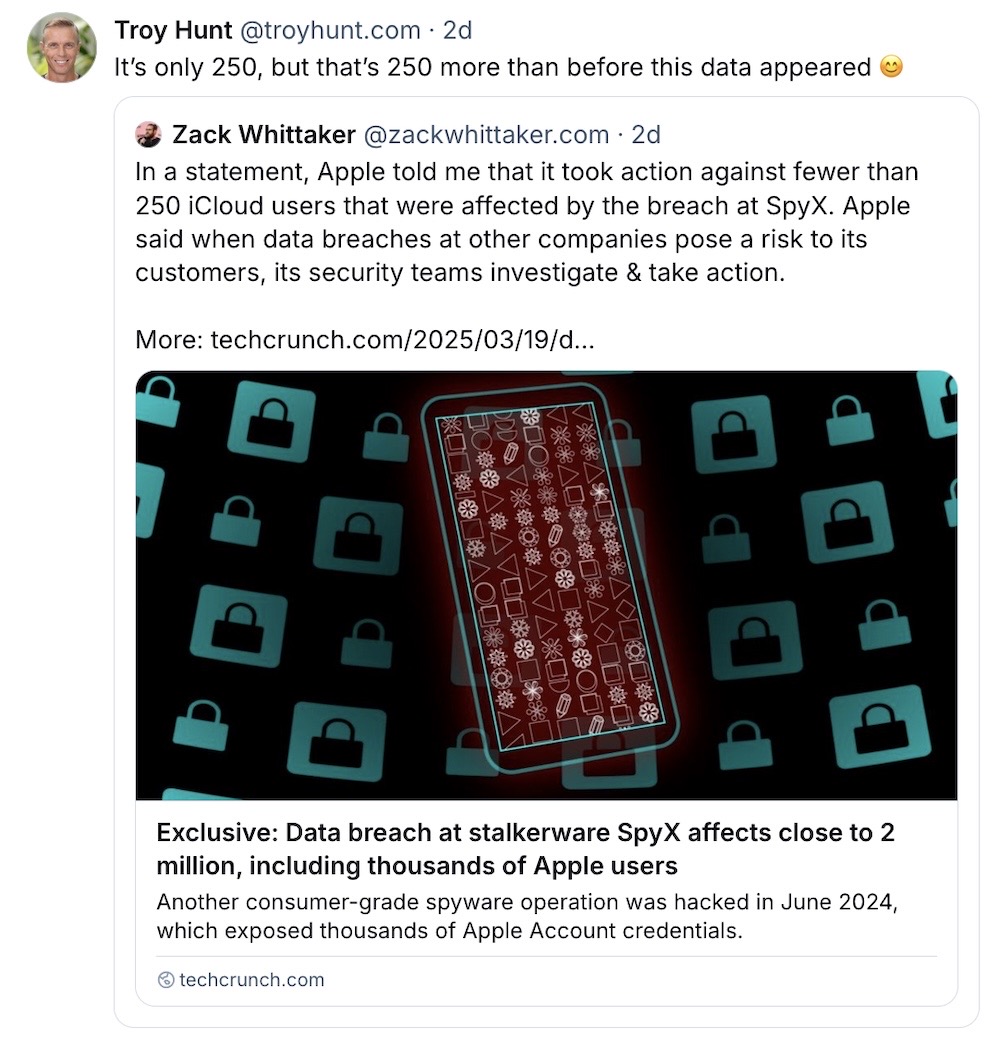
Apple nukes exposed SpyX stalkerware creds: New day, new spyware breach. SpyX has become the 25th (by TechCrunch's count) phone surveillance operation since 2017 to have been hacked or otherwise lost or spilled their users' and victims' data. SpyX, aka "stalkerware," was breached in mid-2024 and had some 2 million phones under its control, including 17,000 Apple users' plaintext credentials, which the surveillance operation uses to tap into the victims' iCloud-stored data. Apple was given the credentials, and told me that it took action to protect around 250 Apple customers. (Disclosure alert: I wrote this story!) (via TechCrunch)
Wiz's $32bn payday: Wiz will become part of Google Cloud, subject to regulatory review, in a deal worth $32 billion. The cloud security giant exploded onto the scene in January 2020 and has become one of the most valuable startups going. SecurityWeek breaks down the deal more. Google + Wiz = G-Wiz? (via Wiz, Google)
Treasury lifts Tornado sanctions: The U.S. Treasury has lifted sanctions (OFAC listing) on Tornado Cash, a cryptocurrency mixing service used by state-sponsored hackers to launder their stolen crypto. The move comes amid warnings that the move will embolden and fund North Korean hackers, which remains dedicated to stealing the world's crypto, including the $1.4bn heist at ByBit in February. The Treasury didn't give a good reason, to be clear, except for exercising its "discretion." (via Treasury, @briankrebs)
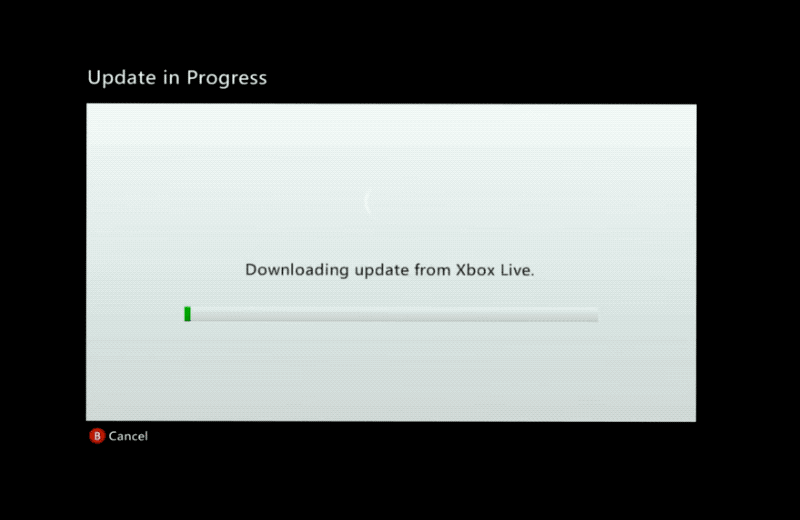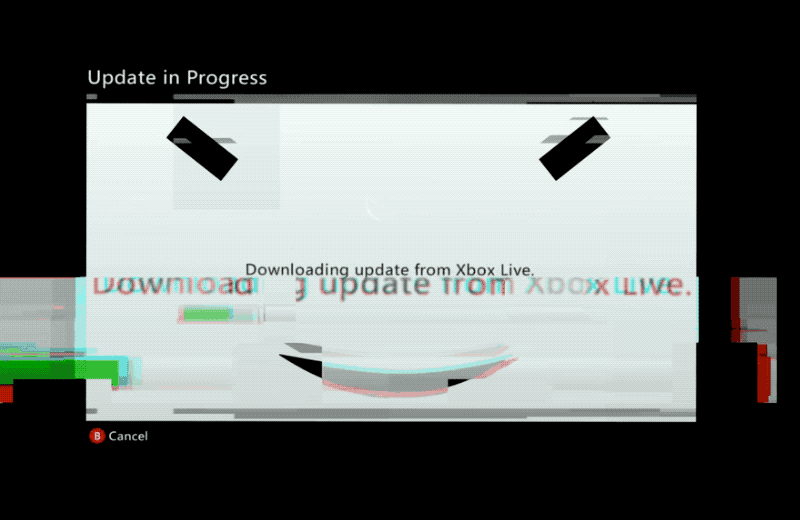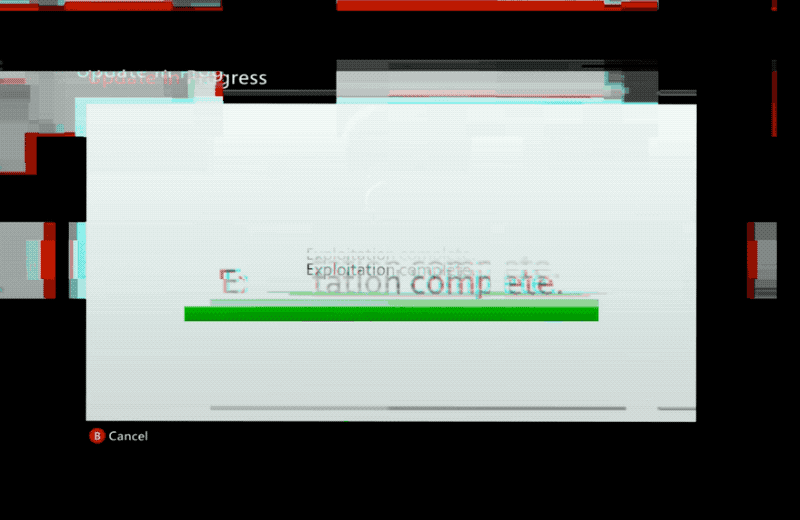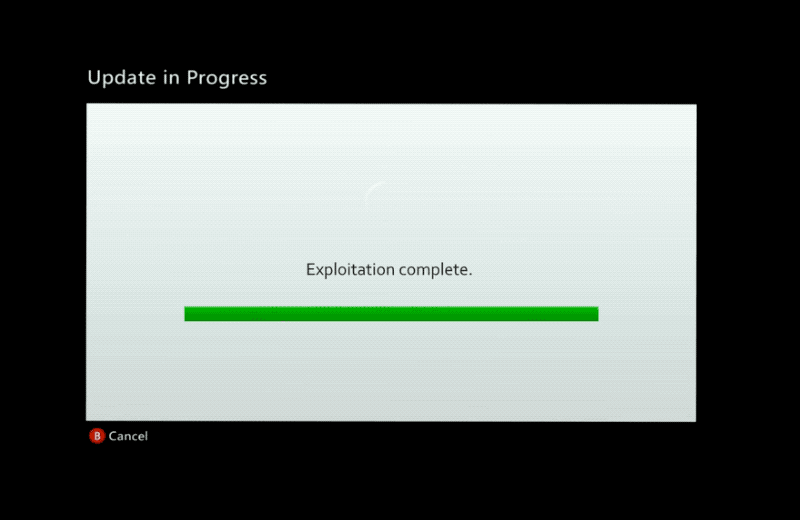
Xbox 360 hackers, assemble! Xbox 360 modders have a new way to install homebrew apps and games on their console. Using a software exploit dubbed BadUpdate allows users to use a USB key to hack the console's hypervisor protections. The exploit is non-persistent so requires exploiting every time, but doesn't require physical tampering. You will need some time and patience, though. (via The Verge)
~ ~
~ ~
THE HAPPY CORNER
Happy Sunday to all those who observe. This is the happy corner.
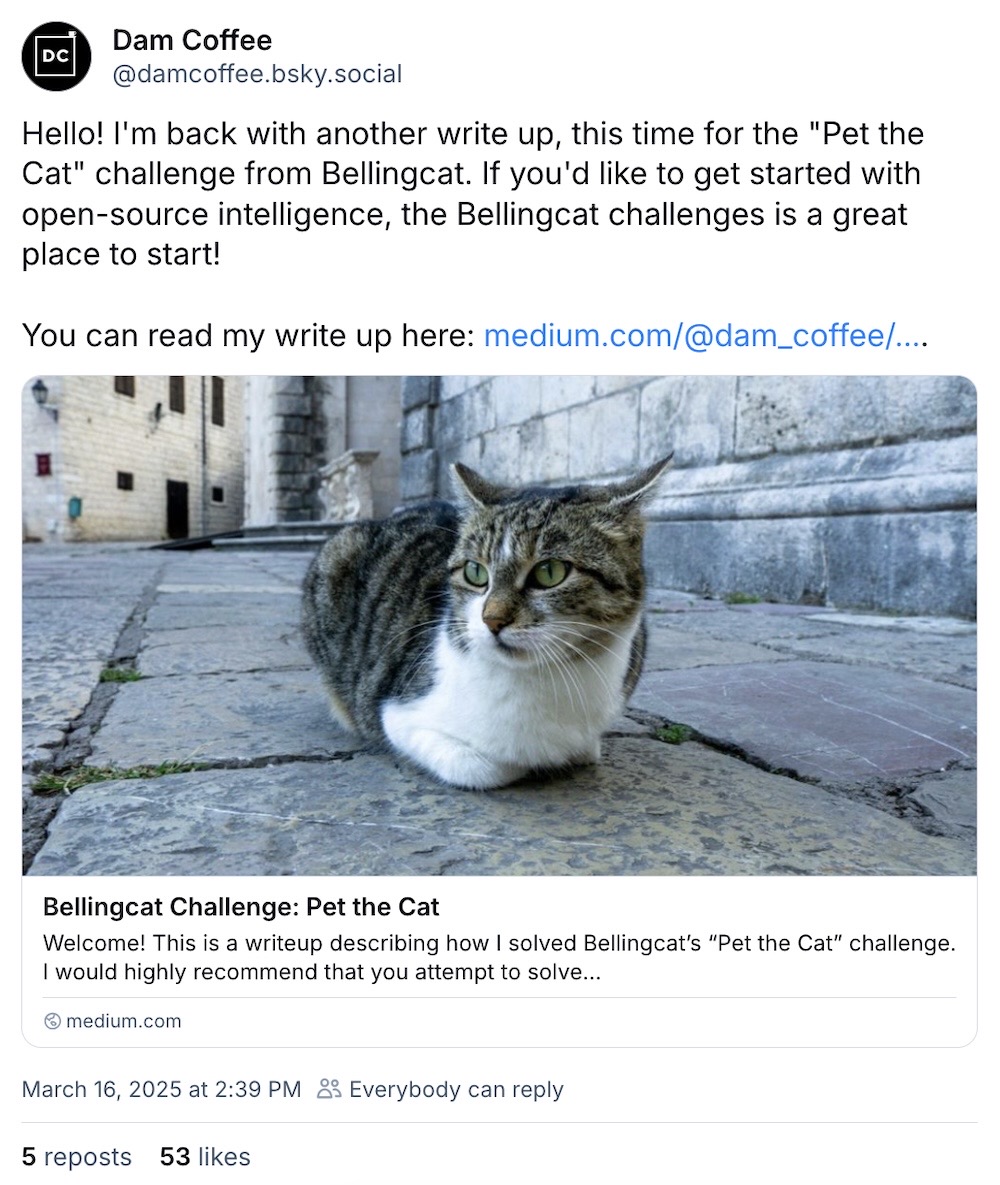
First up: it's a bonus cyber-cat, OSINT edition. The fantastic folks at Bellingcat have a "pet the cat" challenge that involves using open-source intelligence and mapping to discover the exact location of this cat. This is a fun, explanatory read.
Félicitations à la France! The French National Assembly rejected a piece of legislation that would have gutted end-to-end encryption across the country, per the EFF — not that it should've gotten this far anyway. But good to see French lawmakers have a much-needed moment of clarity. For all the good encryption does, it's not the enemy!
And finally this week, from me: My heartfelt thanks to you for reading. It has been, admittedly (and continues to be), a very political time in tech, and this newsletter, by nature, reflects what's in the news that week (otherwise it would be ~this week in only good news security~). Tech has always been political. (Everything is political in some way.) I've received a few messages from folks unsubscribing of late, accusing me of having "Trump derangement syndrome" and calling this newsletter "too biased" and "too political." Sorry to see you go. My goal is to give you the news from the week that you need to know, even if it's not always the best news in the world. (That is also why we've had the happy corner from the very start.)
I love writing this newsletter every week. This newsletter is free, and written entirely in my spare time, and usually with a cat by my side for company. I deeply appreciate you for trusting me to inform you of what's happening in the world as best as I can in this weekly email. And, I also really appreciate the messages from readers who've gotten in touch recently just to say hello, to share a cybercat, or to share a message of warmth and kindness. It really means a lot.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Marlowe, whose human tells me he is a dogged investigator kitty and can be often found fuzzing web applications with random keyboard inputs. (I've heard that the more paws on the keyboard the better!) Thanks so much to Don H. for sending in!

Keep sending in your cyber-cats! You can drop an email any time with a photo of your cyber cat (or non-feline friend) along with their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
Thanks so much again for reading. Let's do this all over again, same time next week. If you want to get in touch, please drop me a line. I always appreciate a cybercat update if you have one!
Touching grass,
@zackwhittaker