this week in security — march 24 edition
THIS WEEK, TL;DR
Four big questions for lawmakers following Change Healthcare hack
Politico: The ongoing, lingering cyberattack at UnitedHealth-owned Change Healthcare is now in its second month. Politico looks at some of the major questions we want answers to — above all, fears that the ransomware gang took off with potentially millions of patients' private health data. Change handles anything from one-third to about half of all U.S. medical records for its role in verifying patients' billing and insurance information. At this point we're just waiting for the number to drop. It comes as health groups resist efforts by the Biden administration to establish minimum cybersecurity standards across the healthcare sector, but the American Hospital Association — one of the largest critics of Change's handling of its hack — won't get behind the cyber rules, calling them "misguided." (Uh-huh.) Save the date, April 30, and bring your popcorn, as that's when UnitedHealth's CEO plans to testify before the Senate.
More: Cyberscoop | CalMatters | @johnnysaks130
Investors' pledge to fight spyware undercut by past investments in malware maker
TechCrunch: The Biden administration hailed a new set of voluntary principles for cyber VC firms investing in "safe" cyber, like not investing in startups that develop spyware and the like. Except, at least one of those signing investors, Paladin Capital, previously invested in a U.S.-based exploit maker called Boldend. According to a leaked document, @lorenzofb reports that Boldend developed an "all-in-one malware platform" called Origen, which "enables the easy creation of any piece of malware for any platform." Boldend also claimed it developed a remote access WhatsApp exploit, but this access "got burned by an update." It's not clear where this red line in the sand is of what "safe" cyber is, but clearly only the investors know.
Archive: The New York Times ($) | More: Paladin Capital | @lorenzofb
Hackers found a way to open three million hotel keycard locks
Wired ($): Two years ago, security researchers began looking at a popular hotel Saflock-branded keycard locks, which they now say can break into any of the three million doors inside some 13,000 properties globally in just a matter of seconds. It's due to weaknesses in the encryption used by the Swiss lock maker Dormakaba, which can be easily exploited with any keycard at any affected hotel. "Two quick taps and we open the door," says Lennert Wouters, one of the (many!) researchers behind the project. As for fixing it, that's less easy. "There's no hardware replacement necessary for each individual lock," is the good news. The bad: "Instead, hotels will only need to update or replace the front desk management system and have a technician carry out a relatively quick reprogramming of each lock, door by door."
More: Unsaflok | Bleeping Computer | @samwcyo

U.S. is still chasing down pieces of Chinese hacking operation, NSA says
The Record: Volt Typhoon, the China-backed hacking and espionage campaign targeting U.S. critical infrastructure, isn't done yet — and neither is the NSA done tracking them. Per NSA's (outgoing*) cybersecurity director Rob Joyce, federal investigators are "still finding victims and making sure to clear out intrusions" tied to Volt Typhoon's ongoing operation. NSA and other Western nations believe the stealthy sit-and-wait cyberattacks are part of China's ongoing efforts to prepare in the event "should a conflict" arise, such as in relation to Taiwan, which China has long had its eye on. U.S. officials fear U.S. critical infrastructure — including airlines and energy pipelines — could get hit in a possible run-up to a conflict, essentially distracting the U.S. from whatever the Chinese military aims to achieve. But details of the sprawling operation remain under classified lock and key.
More: NextGov | @martinmatishak tweets
~ ~
THE STUFF YOU MIGHT'VE MISSED
At least 91 customer GitHub tokens stolen in Mintlify breach
Mintlify: In an incident report published this week (and by all accounts two weeks too late), documentation startup Mintlify said dozens of customer GitHub read/write tokens were compromised in a recent breach. Mintlify told me that it was in part their fault due to a bug in its API, but described the incident as a malicious "attack." Mintlify allows startups to generate documentation based on their code, which requires... you guessed it, by tapping directly into a customer's GitHub.
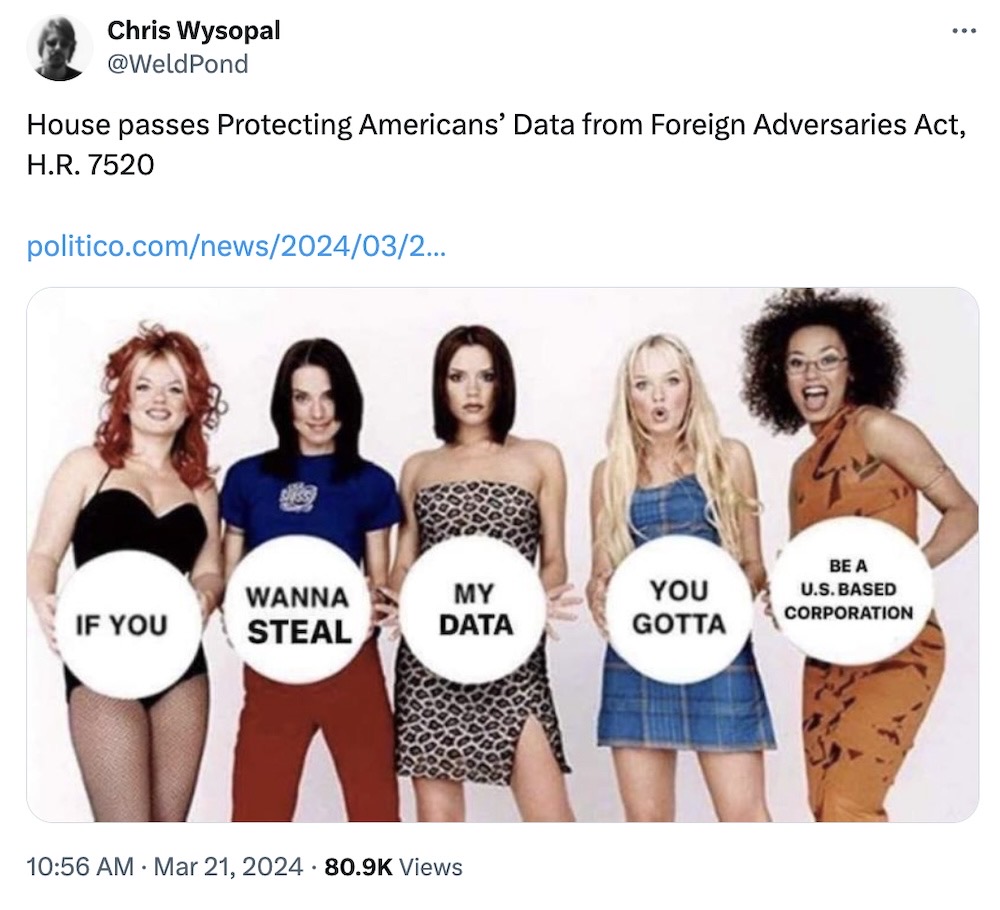
Lawmakers pass privacy bill overshadowed by TikTok fever
Politico: Who says we can't have nice things? After years of dragging their feet and still often doing nothing at all, U.S. lawmakers finally debated and voted on — can you believe it — groundbreaking privacy rules that would ban data brokers from selling Americans' data to adversaries like China, Russia, Iran, and the like. Even though TikTok fever (almost literally) took over last week's legislative debates, @alng reports that the House voted (unopposed!) to pass the bill, known as HR 7520. The bill is not perfect, but it's certainly a good start. Next stop, the Senate!
Users ditch Glassdoor, stunned by site adding real names without consent
Ars Technica: Speaking of privacy, Glassdoor users get less privacy, apparently, after the company review site started behaving like it's some kind of data broker. Users warned others to stop using Glassdoor and delete their accounts after Glassdoor began adding data to users' profiles without their consent. In one case, a Glassdoor staffer added a Glassdoor user's real name to her profile by extracting it from an email she sent asking for account help. Another user told me that the information Glassdoor added to his account wasn't completely accurate and described it as an "incoherent mix of details."
Mozilla drops Onerep after CEO admits to running people-search networks
KrebsOnSecurity: After last week's bombshell news revealing that "identity protection service" Onerep (he writes in extreme air quotes because of the following) was founded by the same person who also went on to found dozens of people-search(!) sites, Mozilla has now dropped Onerep from its paid subscription offering. Onerep's founder and CEO Dimitiri Shelest said in a statement, in part, "My affiliation with a people search business may look odd from the outside." Yeah, it really does! Great work by Krebs here.
New 'AcidRain' variant hitting Ukraine ISPs
SentinelLabs: All eyes are on AcidPour, a new kind of malware and variant of AcidRain, a wiper that took out much of Viasat's network across Europe (and Ukraine, the believed target) following Russia's invasion. Now it looks like a very similar wiper is targeting a new range of devices "covering more hardware and operating system types," per @NSA_CSDirector. According to @AJVicens's reporting, Russia may be using the new malware to target internet providers in Ukraine.
How to detect Pegasus on your iOS device
Group-IB: There are a few ways to scan your iOS device for possible spyware indicators of compromise (IOCs), such as Pegasus, by taking a full encrypted iTunes backup of your iPhone and running the list of IOCs against that backup. (Always best to do this on a computer not connected to the internet since it requires decrypting your iOS backup.) Group-IB has a good explainer on how you can check for spyware using the Mobile Verification Toolkit and corresponding IOC files.
~ ~
OTHER NEWSY NUGGETS
Fujitsu confirms it found malware, warns of breach: Multinational tech conglomerate Fujitsu said it recently discovered malware on its network and warned of a possible data breach involving "customer information." The Japan-headquartered giant notified Japanese government authorities. Fujitsu hasn't commented beyond its brief public statement. Embarrassingly, Fujitsu had an unrelated data breach involving an inadvertently public Amazon S3 bucket, containing client data and private keys. A double-breach punch like this (the second being a self-own) is what can now be known as "pulling a Capita." (via Fujitsu)
Leaked AT&T data emerges (again): A huge data breach involving AT&T customer information from 2021 has finally spilled online in full, some three years later. The data looks like AT&T data, but AT&T won't say if the data came from its systems, or even confirm if the data is valid. Even though it's been confirmed as authentic AT&T customer data, it's still not yet clear how the data ended up online. (via DataBreachToday, Bleeping Computer)
Vroom vroom, hack, hack: Exploits targeting Tesla cars and operating systems netted hackers some $1.1 million in rewards for a range of discoveries. The highest single prize of $200,000 went to the Synacktiv team who demonstrated an exploit in Tesla's electronic control unit. A bug found in the Safari, Chrome and Edge browsers landed Manfred Paul some $100,000. (via ZDI)
Apple chip flaw leaks encryption keys: A flaw in Apple's custom M-series of chips (except M3 chips, which have mitigations) allow attackers to exfiltrate encryption keys and secrets from affected Macs and iPads. As @kimzetter explains, there's nothing users can do about it and developers must update their apps to implement mitigations. But anyone storing a ton of crypto on their devices should probably take some precautions. Apple said very little about the issue until it had to. (via Zero Day, Ars Technica)
Meta E2EE showdown... delayed: In case you were wondering what happened to that upcoming courtroom showdown that was expected to see a Nevada court decide whether Meta can roll out E2EE across the state — well, we have to wait a little longer. The case was postponed while the court determines if it even has the right jurisdiction to hear the case. The court will likely hear the case again in April. Keep a close eye on this! (via Last Vegas Review-Journal, @riana)
~ ~
THE HAPPY CORNER
Finally, some good news. Welcome to the happy corner. And there's a lot this week. Buckle up.
Everyone knows this kind of developer...
...or SEO expert...
Moving on. For some actual practical advice, you should consider changing this new iPhone and iPad setting. The new Stolen Device Protection feature works by locking your phone from account or device changes in the event of a stolen phone. The feature prevents these changes away from a "familiar location" such as your home or work by starting an hour time delay. Or, per @mikko, you can just switch the feature to "always" so it kicks in every time. And if you're a Google user as well, consider bumping up your Google account protections with its Advanced Protection Program, which Runa Sandvik explains in more detail.
New dark web seizure notice just dropped — and yes, that's a real animation.

And, *finally, a shout out to NSA's Rob Joyce, who is yeeting himself into retirement after decades of public service. Since it's not the time of year for a festive light show to see him off, Joyce gets something better: unclassified government-issued memery.
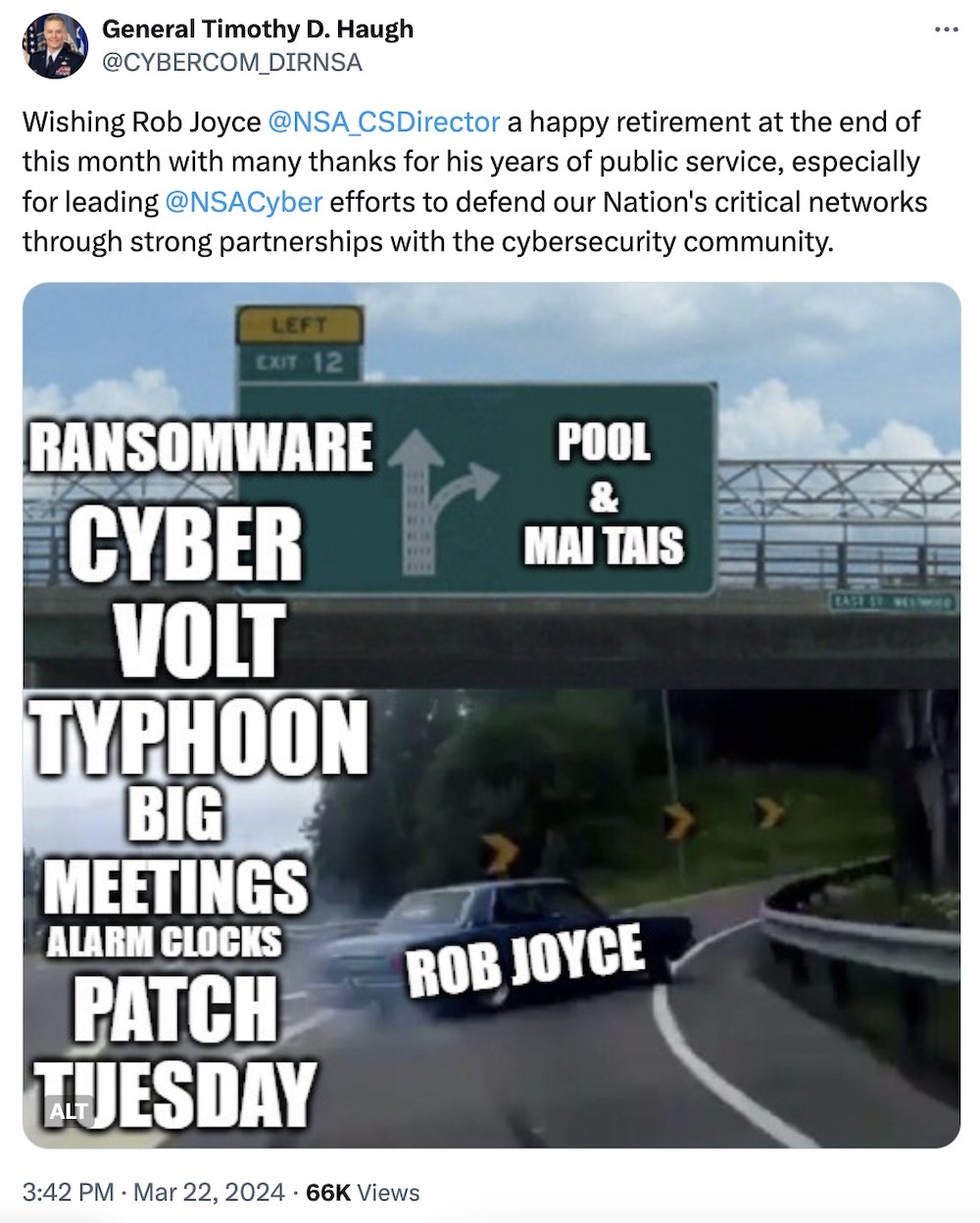
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~

~ ~
CYBER CATS & FRIENDS
Meet this week's cyber cat, Leo. A very handsome kitty and defender of all things cyber. Those whiskers are exquisite. Many thanks to Matthew S. for sending in!

Please send in your cyber cats! Drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
While it's not quite pool and Mai-Tais, I'm off to grab some breakfast and enjoy this cool but wonderful weather. Thanks for reading this busy edition! As always, get in touch by email with anything you want to share, feedback, or anything in between.
See you next,
@zackwhittaker