this week in security — march 26 edition
THIS WEEK, TL;DR
Meta manager hacked with spyware and wiretapped in Greece
The New York Times ($): It looks like "Greek Watergate," as it's been referred as, cranked up a notch after the targeting of Artemis Seaford, a former trust and safety manager at Facebook parent Meta, a Greek-U.S. dual citizen, while she was partly living was in Greece. Much of her work involves policy questions relating to cybersecurity and worked with Greek and other European officials. But when she saw her name on a list of spyware targets in Greek media, she took her phone to Citizen Lab, which confirmed her phone had been hacked with Predator, developed by a spyware company called Cytrox. Turns out the Greeks were wiretapping her phone... probably. The Greek government has denied using Predator, which was banned by Meta back in 2021. Well... then who else is using it? (Hence the standoff.) Seaford is now the fourth person to file suit in Greece involving the spyware, after an investigative reporter and two opposition politicians. How suspicious!
Background: RSF | Courthouse News | @ArtemisSeaford | @jsrailton
DOJ announces arrest of BreachForums admin and site 'disruption'
Justice Department: Well that didn't last long. BreachForums is over, according to the Justice Dept., which this week confirmed last week's arrest and indictment of its alleged admin, Conor Brian Fitzpatrick aka Pompompurin. Fitzpatrick, 20, is charged with conspiracy to commit access device fraud and faces five years in the slammer. The site's new admin, known as Baphomet, vowed to plow on but quickly reneged after — perhaps expectedly — detected the feds accessing the site's systems. In the end, the FBI — which itself had its InfraGuard network hacked, exfiltrated and shared on BreachForums — went to great lengths to get their guy. That includes getting a warrant to obtain his real-time GPS location and surveilling his house. As for the DOJ's alleged disruption, we (TechCrunch) asked — but the DOJ declined to explain what it did exactly. BreachForums doesn't seem seized, but also doesn't currently load either.
More: TechCrunch | Flashpoint | Axios | Cyberscoop | Krebs on Security
TikTok CEO raked over coals; state governments sent website data to TikTok
Wired ($): This week's House hearing was, well, a zoo, let's call it what it was. It was mostly hours of lawmakers' own dysfunction. That's America, baby! Wired's coverage of the hearing was great (always read @dellcam) and stressed that it's lawmakers' own failure to pass data protection legislation that's the problem — not just banning one app! All the while lawmakers were flinging shi...nsults and ridiculous questions about TikTok and Wi-Fi, the Wall Street Journal ($) reports that a security company found that state governments — including states that banned the app! — were using near-invisible tracking pixels on their government websites that were sending visitors' data back to TikTok. Whoops! (If you happen to read this newsletter and work in Congress, please, for the love of all that is holy, accept that the problem is here — not TikTok. Now, if you could go and tell your boss that, much appreciated.)
More: Wall Street Journal ($) | Cyberscoop | Firstpost | Reuters ($) | Axios

Fortra told companies breached by Clop that their data was safe
TechCrunch: Software maker Fortra told its corporate customers that their data was safe — even when it wasn’t — following a ransomware attack on its systems. My colleague @carlypage_ and I spoke with two Fortra customers that only learned that data had been exfiltrated from their GoAnywhere systems — a file transfer tool used for sharing large sets of data over the internet — when they received ransomware demands. Dozens of organizations have been hit by the mass-ransomware attack, all thanks to one pesky zero-day in the GoAnywhere software. Hacked organizations include Onex, the U.K.'s Pension Protection Fund, the City of Toronto, and Procter & Gamble, with many more likely to disclose. Fortra continues to decline to comment. (Disclosure: I co-wrote this story!)
More: TechCrunch | Bleeping Computer | Reuters ($) | @zackwhittaker
~ ~
THE STUFF YOU MIGHT'VE MISSED
Bitcoin ATMs hit by zero-day, $1.5 million stolen
Bleeping Computer: A zero-day bug in bitcoin ATMs made by General Bytes was exploited by attackers to steal $1.5 million in cryptocurrency. The attackers were able to access compromised ATM databases, including API keys for accessing funds in hot wallets, and more. More from the company here.
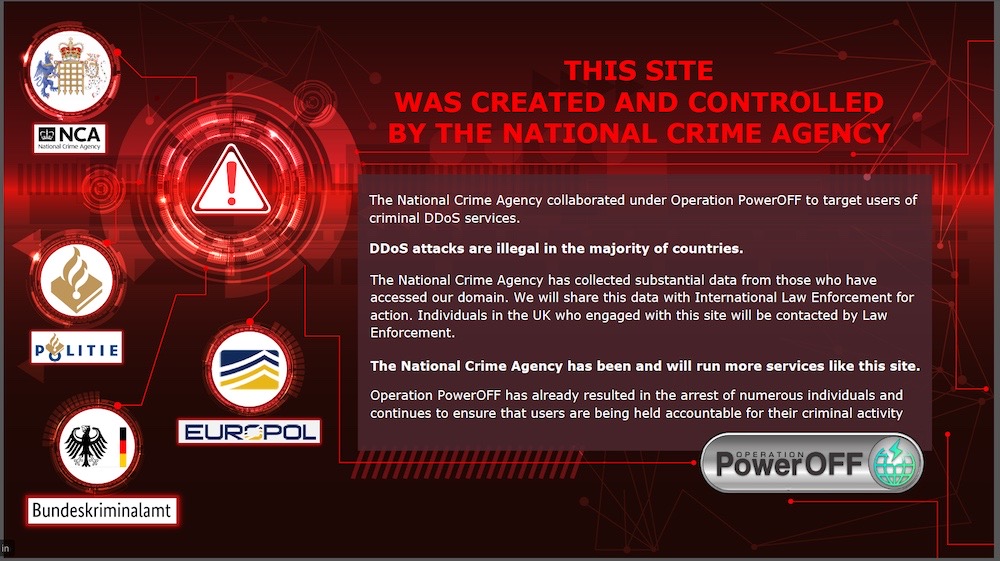
U.K. runs own DDoS site to catch booters
U.K. National Crime Agency: DDoS attacks are illegal in the U.K., so the NCA thought it would set up several sites disguised as DDoS-for-hire services in an effort to catch the cheeky sods looking to do some British crimes (which are ordinary crimes, but done in Britain and usually before supper). "After users register, rather than being given access to cyber crime tools, their data is collated by investigators," explained the fuzz.
ChatGPT already had a data breach
OpenAI: The internet's latest favorite plaything ChatGPT, the non-sentient glorified autocomplete, accidentally exposed the chat histories of users. "It’s also possible that the first message of a newly-created conversation was visible in someone else’s chat history if both users were active around the same time." In fairness, OpenAI — the plaything's maker — explains the bug in considerable detail. @sama explained that's why the chatbot was briefly downed by the self-inflicted outage.
The DEA quietly turned Apple's AirTag into a surveillance tool
Forbes ($): Because of course it did. The DEA — aka the Drug Enforcement Administration — used the tiny tracker in a pill press to conduct surveillance. It's the first known case of a federal agency using the Bluetooth tracker into a spy tool. Though, as Forbes notes, "it's unclear how successful the AirTag was in helping the DEA uncover criminality." AirTags — though popular with stalkers — have also been used by reporters to track pairs of donated shoes to uncover false recycling promises.
~ ~
~ ~
OTHER NEWSY NUGGETS
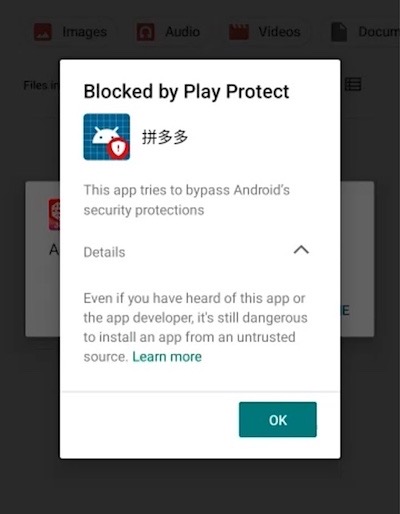
Google flags Chinese e-commerce apps as malware: Google security researchers flagged several app versions made by the Chinese e-commerce giant Pinduoduo as malware, alerting users who had them installed, and suspended the company's official app in Google Play. Pinduoduo is a rising Chinese e-commerce giant with close to 800 million active users. But security researchers have warned in recent weeks that the app contains malware. (via @lorenzofb, CNN)
USB drives that explode: I know you know, but please don't plug in random USB drives from the street. Back in the day, they used to contain malware. Today, they can explode when plugged into a reporter's laptop. More from @_MG_, who knows a few things(!) about malicious USB drives. (via BBC News)
What happens when you arrest a Russian hacker spy? If you, like me, were left wondering why the newly revealed commander of Sandworm, the Russian GRU unit dedicated to destructive hacks, was released by Dutch authorities after he was arrested in the Netherlands with a ton of hacking equipment in 2018, we have an answer! Turns out there was "quite a discussion" about it at the time, and @agreenberg closed the loop after chatting with a former Dutch official. (via @agreenberg)
Beloved hacker Kelly 'Aloria' Lum passes away at 41: Kelly Lum, aka Aloria, passed away last Sunday. Tributes poured in from across the security space. Aloria was 41, and she’s survived by her husband. My TC colleague @lorenzofb wrote about Aloria and what she meant to many folks in security. (via TechCrunch, @quine)
~ ~
THE HAPPY CORNER
Happy Sunday! Only one this week and I feel it really sums up the mood.
What little-known fact would you tell the world about cybersec.... oh. (And it's so much worse than you think.) But at least we're all in it together!
On that bright note...!
(If you have good news you want to share, get in touch at: this@weekinsecurity.com.)
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Eddie. You're supposed to think outside of the box, not get in one! Thanks to Gary M. for sending in!

Keep sending in your cyber cats (or their friends). Send in a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's it for this short but busy week. As usual, my email is always open for feedback, or feel free to drop a note in the suggestion box. Let's do this same time next week. Hopefully it'll be a little warmer. Summer can't get here fast enough.
Take care, and chat next Sunday.
—@zackwhittaker