this week in security — march 27 edition
THIS WEEK, TL;DR
Oxford teen accused of leading Lapsus$ hacking group
BBC News: A 16-year-old from the U.K. city of Oxford is accused of being one of the leaders of the Lapsus$ hacking group. In total, British police arrested seven young adults, all aged 16 to 21. News of the arrests, reported by Bloomberg ($), landed a week after the group posted screenshots revealing that they had remote access to Okta's internal systems, Slack, and other apps. Organizations around the world rely on Okta for login controls and multi-factor authentication, with fears that the hackers targeted Okta in order to hack its many customers. Okta's handling of the breach "compromise" was a fustercluck, but ultimately blamed on a customer support company called Sykes, owned by Sitel. Customer support firms are frequently targeted for their ability to allow for downstream attacks. The big question is who else was targeted? At least 366 Okta customers are affected, the company said. Okta finally explained more about the breach, but customers — like Cloudflare — are rightfully angry at the lack of disclosure — two months later! We saw behind the wizard's curtain and it does not look good.
More: Okta | Wired ($) | @billdemirkapi tweets | @_mg_ tweets
Lapsus$ hackers leak 37GB of Microsoft's alleged source code
Bleeping Computer: Keeping with Lapsus$, what feels like a century ago was... actually just a few days ago. Lapsus$ has targeted Nvidia, Okta, Samsung — and Microsoft, the latter of which admitted this week that parts of its Bing and Cortana source code was pilfered by the gang. Microsoft dropped the admission in a lengthy post describing the tools, techniques and procedures behind the Lapsus$ group, which it calls DEV-0537. Microsoft says it doesn't rely on the secrecy of its source code for security. But(!) it's reported that the company had multiple code signing certificates leaked in the process. Not great, since those can theoretically be used to sign malware to make it look like it came from Microsoft.
More: TechCrunch | @briankrebs
White House warns of possible Russian cyberstrike on US critical infrastructure
Ars Technica: The U.S. government is warning of a possible cyberattack on U.S. critical infrastructure, the White House said this week. Oh, you need IOCs? Yeah, none of those. How's Russia going to attack? Ha! Good question, we don't know. What should you be on the lookout for? LOL, good luck. Thanks, government! But the warning does indicate something, potentially (maybe?) is coming, but the U.S. cyber chiefs don't seem to know what, or are unwilling to share, fearing the very worst — like destructive attacks. We've seen Russia launch damaging cyberattacks before, even recently with the Viasat hack (more on that in a moment) and Sandworm v. Ukraine's power grid. @RobertMLee speaks as a voice of reason in the tweets. But as much as the government's cyber-messaging has been more alarming than actionable of late, the government isn't one to cry wolf. Shields up! And grab a spare, you might need one.
More: Bloomberg ($) | @RobertMLee tweets

U.S. indicts four Russian spies for targeting critical infrastructure
Justice Department: What feels like a "we got 'em" moment, the U.S. has charged four Russian government employees with targeting the global energy sector between 2012-2018 in over 130 countries. The spies are behind the Triton (Trisis) malware, which targets industrial control systems (ICS) — the devices in manufacturing, energy, and water supplies that keep critical processes ticking over and operational. Triton, if you recall, was used against a Saudi petrochemical plant back in 2017. The attack failed because the plant didn't blow up (seriously). @joetidy called it "one of the closest moments we've come to a loss of life due to a cyber attack." The Justice Department's indictment also shows that the Russian hackers targeted an energy facility slightly closer to home — a U.S. nuclear power plant.
More: ZDNet | E&E News | TechCrunch | @RidT tweets
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
How Truecaller built a billion-dollar caller ID data empire in India
Rest of World: Here's a detailed look at Truecaller, a caller ID app company that has built a huge empire in part off the back of weak security and privacy controls in India by collecting vast amounts of personal information without direct and explicit consent of the individuals in question, according to Rest of World, citing an investigation by The Caravan, an investigative and long-form Indian magazine. One lawyer who was interviewed for the piece, said: "Truecaller is a case where your personal data is collected from a contact of yours, which [then] gets used without your consent." Truecaller can also "read the content of text messages," per a former employee. Definitely worth a read.
Behold, a password phishing site that can trick even savvy users
Ars Technica: Meet BitB, or "browser in the browser," a fake browser window that's inside a real browser window designed to spoof an OAuth page (which is when you sign in via Google, Facebook, Apple etc.) Major big sites use OAuth a lot, opening up an interesting path of attack for phishers. The 'browser window' is actually built using HTML and CSS, and isn't a pop-up window at all. It just looks like one, and by all accounts it's a pretty impressive proof-of-concept phishing tactic. Great for helping defenders protect their networks. BitB is developed by @mrd0x.

Vulnerability allows hackers to lock, unlock, start Honda Civics
Nonamecoder, GitHub: Years-worth of select Honda Civics models are vulnerable to a radio replay attack, in which the radio frequency in the keyfob can be captured and replayed by someone else other than the owner. That's a problem since it allows an attacker to remotely open and start an affected vehicle. But Honda was clear — there's nothing to see here, please_disperse.gif, it's not a new attack and "doesn't merit any further reporting." You know what does warrant further reporting? The fact that researchers keep finding new issues in Honda keyfobs, as The Record notes, but has absolutely zero interest in fixing them.
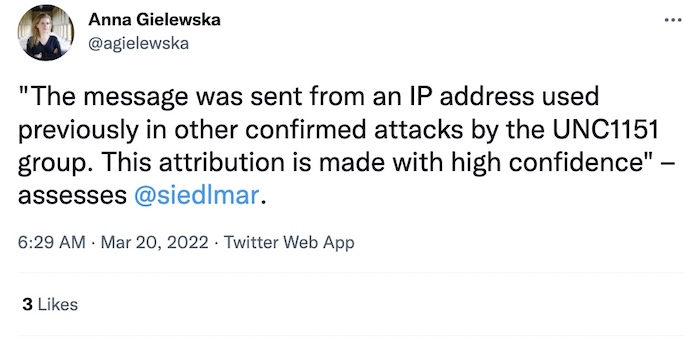
New evidence points to UNC1151 as behind Polish PM's advisor
VSquare, Frontstory: Since June 2021, the inbox of Michal Dworczyk, the right-hand man of Poland's prime minister, has been read in Polish newspapers and outlets because of a hack-and-leak operation that exposed 60,000 of his emails. Now, new evidence points to UNC1151 as being behind the breach, an operator believed to be linked to the Belarusian government that works in favor of Russian interests. It's not too dissimilar to how Russia hacked and leaked the emails of John Podesta, a senior Hillary Clinton advisor, in the run-up to the 2016 presidential election which Clinton narrowly lost to rival candidate Trump. Great read that you might've missed.
~ ~
OTHER NEWSY NUGGETS
North Korean hacker hackers caught compromising Chrome: Hackers working for North Korea are using a Chrome zero-day to target U.S. news media, and IT and crypto organizations. The bug was found by and fixed by Google, courtesy of its Threat Analysis Group, which documented the activity in a blog post this week. It's the same group of North Korean hackers that targeted security researchers last year. Remember, cryptocurrency is how North Korea funds its weapons program. As always, @ryanaraine has the details in a solid write-up.
Russia popped Viasat, says Western intel: BBC's @gordoncorera, who is sourced up to the eyeballs, is reporting that Western intelligence is privately attributing the Viasat hack — which coincided with Russia's invasion of Ukraine — to no other than the Kremlin, though no public attribution has yet been made. "It looks like the clearest example of spill-over," said one official. It comes a couple of weeks after Reuters ($) reported that the NSA was one of the agencies probing the apparent sabotage because Viasat is a U.S. defense contractor, as well as a major supplier of satellite communications to Ukraine and Europe, which was probably the real target.
Kaspersky left out in the cold: Russian cybersecurity giant Kaspersky had a rough week. The U.S. Federal Communications Commission said the company poses an unacceptable risk to U.S. cybersecurity, effectively banning the company from being used in sensitive networks, like telecoms. Kaspersky also got booted from HackerOne's platform citing sanctions, which HackerOne now seems to understand better after it unnecessarily hit Ukrainians — who aren't under sanctions — by mistake. Last week both Germany and Italy warned against using Kaspersky fearing links to Russian intelligence.
~ ~
THE HAPPY CORNER
This week's happy corner is short, but sweet.
First up, for those who know of the name, Mike Godwin (@sfmnemonic) might be best known for his eponymous law, Godwin's law, which finds that that the longer an online discussion grows, the greater the probability of a comparison involving Nazis. Well, congratulations on what looks like the creation of his as-of-yet unnamed second law. All of this to say, be good to one another.

And finally, some wise security advice courtesy of regular newsletter reader Mitch Parker, delivered in the style of meme. (I received three, but sadly my newsletter only allows image space for two.) Secure your friends, share a meme.

To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
Meet Nelly, this week's cybercat, who is, uh, absolutely not using that phone for social engineering the next order of cat food... she promises. A big thanks to Zack G. for the submission!

Don't forget to send in your cyber cats (and their friends!). Drop an email here with their name and photo, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's all for this week, thanks for reading! As always feel free to send any feedback through the suggestion box or reach out by email. Have a great week, and see you next.