this week in security — march 3 edition
THIS WEEK, TL;DR
UHG says ALPHV/BlackCat ransomware gang behind Change Healthcare hack
TechCrunch: Sorry to start on this note, but this remains a big story to watch. The cyberattack at Change Healthcare, one of the largest health tech companies in the U.S., was confirmed as ransomware this week after the company re-attributed the cyberattack to the prolific cybercrime gang ALPHV/BlackCat, which claimed — so far just a claim — to have stolen millions of people's personal health data. Change Healthcare handles billing and insurance for millions across America, and claims its system touches one-in-three U.S. patient records. UnitedHealth, the health insurance giant that owns Change, hasn't commented on the possibility of a data breach yet. Given the attackers had access to Change's network, it wouldn't be a huge leap — but time will tell. The cyberattack has already caused huge outages across the U.S. (and for U.S. military personnel around the world), with many having to pay in cash to get their medications filled or unable to know if their hospital inpatient stays will be covered. UnitedHealth finally notified those affected by publishing a security incident site, though little about the incident itself. All eyes on the company's next 8-K disclosure, since the SEC's cyber reporting rules that came into effect late last year forced this incident out into the open. (Disclosure: I wrote this story.)
More: UHG | Reuters ($) | Washington Post ($) | DataBreaches.net | @brettcallow
Biden executive order bans rival nations from buying sensitive U.S. data
Justice Department: A new executive order signed by President Biden bans the sale of sensitive Americans' data to adversarial nations, like North Korea, Russia and China. The idea is aimed at stopping rival governments from using data derived from U.S. data brokers to blackmail or otherwise leverage for intelligence or espionage. There's just one tiny problem: The order does absolutely squat-all for where some of the biggest abuses are happening — right here in the U.S.-of-A. The reality is that U.S. law enforcement and government agencies can still buy commercial data and use it against Americans or non-citizens living here (which is also bad!) without needing a warrant (think IRS, ICE, and CBP, etc.). This couldn't come at a more jarring time for the U.S. government decision-making, since U.S. feds are doing some of the very things it doesn't want others' doing. Just take @byrontau's new book on today's surveillance state, of which an excerpt this week details in extreme detail just how the U.S. spy agencies buy data from brokers to eavesdrop on the world.
More: WSJ ($) | Wired ($) | Bloomberg Law ($) | Byron Tau | @w7voa | @dnvolz
Threat actors exploiting multiple bugs in Ivanti tech as detection tool fails
CISA: OK, moving on. How are things at Iva... oh. Not great, by the sounds of it. Ivanti, the current owner of buggy tech from yesteryear, is battling with a number of zero-days in its VPN appliance, used by thousands of enterprises and organizations across the world. To save melting your face off with a blastwave of IOCs, security researchers say they are seeing "mass attempts" to exploit the multiple Ivanti zero-days. Much of the activity is traced back to China, but at this point it's a free for all given the simplicity of the bugs. The National Security Agency, whose job it is to help protect the U.S. industrial base when it's not checking your email for you (😉), says it's "aware of the broad impact" affecting the U.S. defense sector. CISA, meanwhile, says Ivanti's tool for checking of signs of compromise... doesn't seem to work, with CISA saying it is "not sufficient to detect compromise." Oh no.
More: Mandiant | TechCrunch | Axios | @ericgeller

~ ~
THE STUFF YOU MIGHT'VE MISSED
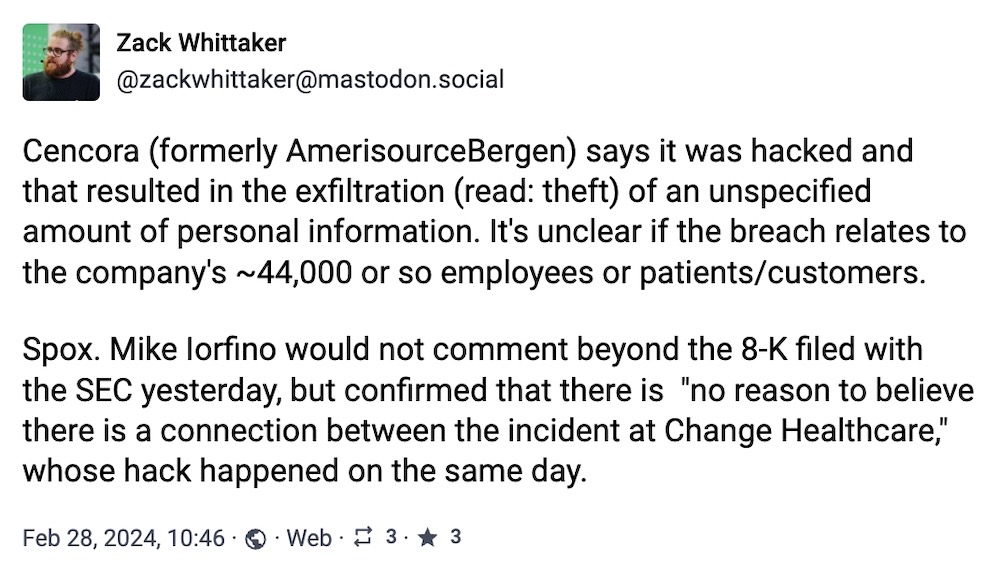
Pharma giant Cencora confirms personal information taken in data breach
Cencora: Another subject of the SEC's reporting rules, Cencora said in an 8-K filing that it was hacked and confirmed the data had been exfiltrated from its IT systems. "Some of [the data] may contain personal information," said Cencora, formerly AmerisourceBergen, a drug wholesale company that also does research. No word yet on whether patient or customer data was taken, and a Cencora spokesperson told me that there's no link to Change Healthcare's ongoing incident.
Popular whitelabel video doorbells have simple security flaws
Consumer Reports: The researchers at Consumer Reports say they have found vulnerabilities in popular video doorbells sold by Walmart, Sears, and Amazon, which allow anyone to hijack a person's camera by holding down the doorbell's pairing button. Not ideal! The doorbells are white-labeled, so they're all from the same manufacturer, but branded as Eken and Tuck, and use a common app that has more than a million Android downloads (so it's reasonable to say that these are widely used doorbells). The researchers also found that the doorbells expose JPEG thumbnail images from the live camera feeds over the internet and accessible remotely from anywhere, which doesn't feel particularly private or secure. Walmart and Temu took down the listings from sale, but Amazon keeps on selling them — why? Because it's in Amazon's financial interests to keep selling you stuff, even if it's insecure garbage.
GitHub besieged by millions of malicious repos in ongoing attack
Ars Technica: Code sharing giant GitHub is struggling to contain an ongoing flood of malware hitting millions of code repositories. The malware can steal passwords and crypto from a victim's devices. GitHub is whack-a-moling the repos but Apiiro data shows the Microsoft-owned giant hasn't yet fully contained the situation. GitHub didn't dispute the data estimates, and issued a blanket statement that suggested it was aware of the incident at least.
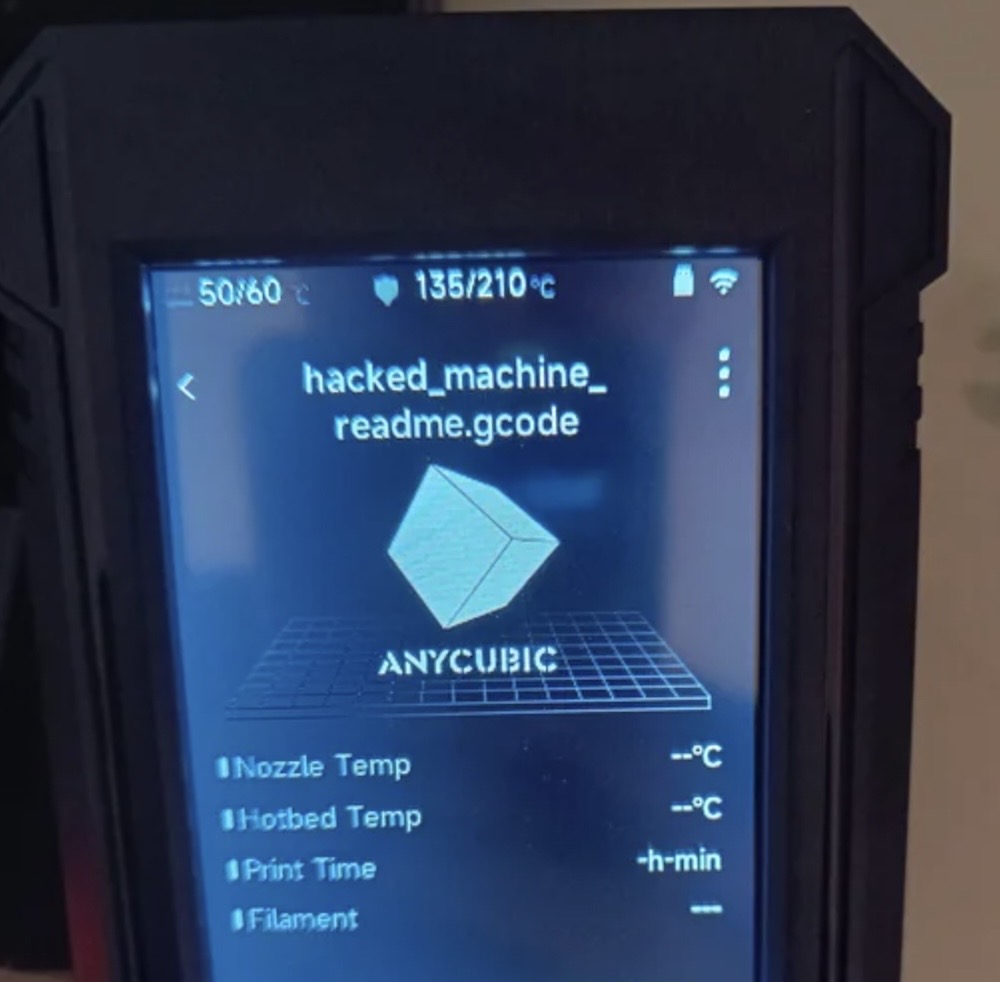
Anycubic 3D printers hacked to display security warning alert
Bleeping Computer: In an odd but potentially helpful move, an unknown hacker has mass-remotely planted a benign warning text file on millions of Anycubic 3D printers, which can be (and many are!) connected to the web. The hacker claimed to have found a bug in Anycubic's MQTT server (the details of which have not yet been confirmed) and apparently exploited the bug to alert Anycubic's customers. (Thanks, I think?) Users are advised to pull their devices from the internet in the meantime. Anycubic's founder James Ouyang responded to a request for comment but hasn't said what the issue is — yet. (Hat-tip to @dan for flagging!)
North Korean hackers exploiting Windows AppLocker driver zero-day
DataBreachToday: Hackers associated with the North Korean group of threat groups Lazarus have been exploiting a previously unknown zero-day in a Windows AppLocker driver to gain kernel-level access and the ability to nuke the in-built security tools. Microsoft fixed the bug in its February rollout of security patches. AppLocker determines which apps can be run and by which user, so messing with this can be a boon for malicious actors. Avast's security research wing digs into the bug, which it reported to Microsoft back in... *checks notes* August 2023.
~ ~
OTHER NEWSY NUGGETS
Sandvine snooping 'contrary' to U.S. national security: The mass-web monitoring and censorship-enabling company Sandvine has been added to the U.S. government's naughty entity list, effectively its deny-list blocking the company from obtaining U.S. technology. Sandvine sold its web snooping and blocking technology to oppressive regimes, like Egypt and Belarus. Sandvine joins other equally unpleasant firms, such as NSO Group, Intellexa and Cytrox, on the entity list. More from Citizen Lab's @rondeibert in the tweets. (via Bloomberg ($), Federal Register)
Ping, ping. It's the FBI snooping on your notifications: Late last year, Sen. Ron Wyden revealed the government's secret practice of snooping on the unencrypted push notifications sent to our phones. Turns out the feds can pull the data from those push notifications and trace them back to potentially bad people. The "potentially" is important, since any kind of surveillance will allow for abuses. Skip forward to today, and now the Washington Post ($) dives into the practice, especially at a time when folks living in the U.S. can face prosecution for violating state abortion bans, for example. If history shows anything, laws can literally change overnight — a person safe one day can very much be prosecuted the next — and more reason to encrypt all the things. (via Washington Post ($), @aaronjschaffer)
Wyden sounds the SS7 siren (again): Sticking with Wyden for a hot second, because the security-minded senator is warning — and not for the first or even second time — of vulnerabilities in a protocol that runs the global telecom network, known as SS7, or Signaling System 7. The obscure name is a relic of the '90s, but the point is that the protocol is very old, very flawed and easily abused by state actors to gain access to all that juicy telecoms data flowing around the world's pipes at the speed of light. Think who's calling who, location data, text messages and more. By calling on the Biden administration to do something (anything?) to overhaul telecom security standards, Wyden notes that the lax security of the world's telcos is "threatening US national security, freedom of the press and international human rights." (via Bloomberg ($), Ron Wyden, Lawfare)
Taiwan telco data stolen: Taiwan's ministry of national defense says unknown hackers (though signs seem to point to China for a number of reasons) stole about 1.7 terabytes of data from the island nation's largest telco, Chunghwa Telecom. The fear is that the data, which isn't classified, could still contain "sensitive information" about the country's military and government, especially at a time when China is eying Taiwan as its own (which it shouldn't, because it's not). (via AFP via SecurityWeek)
~ ~
THE HAPPY CORNER
Let's keep it light. It's time for the happy corner.
In a rare two-for-one sighting, this week saw two — yes, two — instances of Doom running on obscure devices. And so, bringing back the usual What Can Doom Run On series, we have both a robot mower and a toothbrush (botnet not included). Pure madness, and yet we're absolutely here for it.

And, in a world where sometimes the little things can get missed, it's worth reminding ourselves of the progress we can make and celebrating it. Canada's Supreme Court ruled that IP addresses are considered personally identifiable information and police must first obtain a warrant before seeking a person's IP. IP addresses aren't always a good indicator of where an attack (or crime) is coming from, so all the more reason to raise the legal standard.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's two-for-one cyber-cat kitten special are Indy and I-No, who are four-month old sisters. Here you can see them closely guarding the family fort, diligently, even if it looks like they have their eyes shut. Very good kitties! (but sshh, let's not stir them.). Many thanks to Rens for sending in!

Please send in your cyber cats! Drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~

~ ~
SUGGESTION BOX
And that's about as much news as I could humanely subject you to — it has been a busy week! I hope you enjoyed this week's newsletter (as much as I enjoyed writing it). I also love hearing from you with any feedback, questions, or cyber cats you want to share with me. Feel free to send me your stories, findings, research and other fun things you discover!
And thanks again to everyone who helps support the newsletter. It means the world to me. For those interested in mugs and stickers, check out my Ko-fi page.
Catch you next Sunday,
@zackwhittaker