this week in security — march 30 2025 edition
THIS WEEK, TL;DR
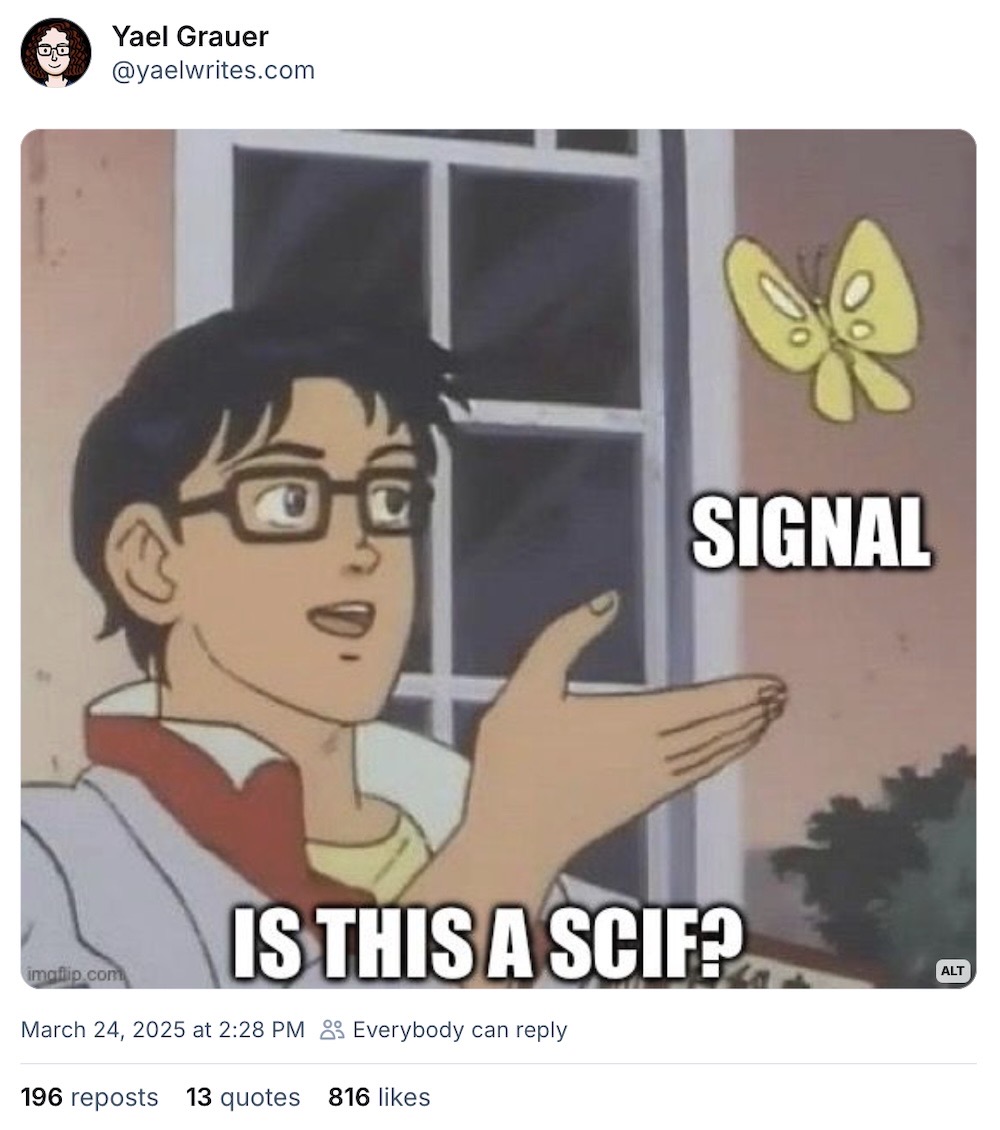
Senior Trump officials accidentally texted war plans to reporter over Signal
The Atlantic ($): Ever woken up one morning, poured a cup of coffee, made a bowl of cereal, and texted highly classified war plans to a journalist? I guess that's where we're starting this week. What were they thinking?! In what is both a huge breach of national security (and also inadvertently pretty good free advertising for Signal), several senior Trump cabinet-level officials group-texted The Atlantic's editor-in-chief (mistakenly) specific plans to launch air strikes on Houthi targets over Signal ahead of the attack. Mind-bending reporting and frankly there's just too much to discuss. It's a huge breach of security, not least because they weren't in a SCIF and Signal isn't approved for classified use. (Signal is excellent, sure, but it's the underlying consumer phones that Signal runs on that are the problem — think spyware!). We got some excellent memes out of it, though. But all this points to an incredible apathy towards security and a lack of documentation (such as records keeping) by some of the most senior people in government. At least on a classified line, you can't accidentally dial in a journalist.
More: Spiegel [DE] | Lawdork | MalwareTech | BBC News | Foreign Policy
23andMe files for bankruptcy, sparking data privacy fears
BBC News: DNA testing giant 23andMe looks like it's going under, and filed for bankruptcy protection this week. CEO Anne Wojcicki stepped down on the news after leading the company's slow decline for more than two decades. A court will later this year oversee the sale of the company and its assets, including millions of people's DNA records (and much of their family members — as is the way that DNA works). U.K. authorities sounded the alarm, as did several U.S. states (including California and New York), warning that the data could be sold to, well, anyone. You can delete your data, but 23andMe may hold onto some of it for as long as it wants. If only someone had been warning about this for years...
More: TechCrunch | 404 Media ($) | DocumentCloud | Salon
Oracle denies breach, despite mounting evidence of breach
Bleeping Computer: When is a breach not a breach? When Oracle claims it's not a breach. But where there's smoke, there's usually fire. A threat actor claims to have breached Oracle Cloud and sold authentication data and encrypted passwords of more than 6 million users, as well as 140,000 domains used by companies and governments allegedly affected. The threat actor also planted a text file on an login.us2.oraclecloud[.]com subdomain. Strange, right, especially if there's "no breach"? Now, customers are reporting that data samples shared by the threat actor are in fact real. Security firms investigating are sure there's something funky going on. CloudSEK has deep-level analysis, as does Kela. If the data is genuine, it could be a major breach of Oracle's systems. Keep a close eye on this one, and maybe don't take Oracle's word for it just yet.
More: The Register | SecurityWeek | Dark Reading
~ ~
THE STUFF YOU MIGHT'VE MISSED
Oracle Health breach compromises patient data at U.S. hospitals
Bleeping Computer: Sticking with Oracle for a second... It looks like Oracle might have a second incident on its hands, courtesy of Cerner, the health giant that Oracle acquired back in 2022 for $28 billion. Now known as Oracle Health, the unit allows hospitals and healthcare practices to access electronic health records and more. Per a notice sent to affected customers, Oracle became aware of a breach of its servers on February 20. Some of the data "may" have included patient data, according to Bleeping's sources. Bloomberg ($) also has more reporting.
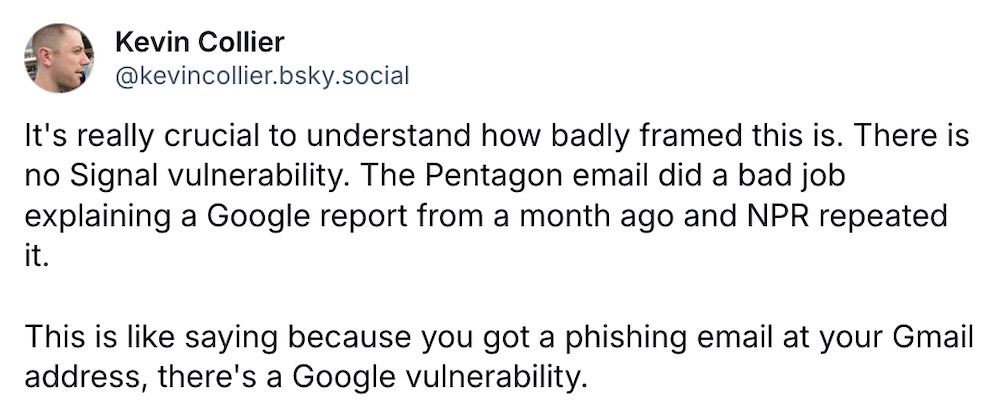
NSA's email about Signal 'vulnerability' was way off
Kevin Collier: Earlier this week, the good folks at NPR wrote a story about the NSA sending around a Pentagon-wide email about a supposed flaw in Signal. The actual NSA email, though, seemed to get things quite muddled. The issue at hand was reported last month when Google found that Russian threat actors were abusing Signal's in-built "linked devices" feature (which lets you run Signal as a desktop app) by crafting malicious QR codes. It's not a vulnerability, but good to be aware of, especially if you're on the battlefield right now. @kevincollier debunks this one so you can keep using Signal (but not for war chat discussions, please).
PSA: Not every household appliance needs an internet connection
Jeff Geerling: In what shouldn't be a controversial opinion in this day and age: Not everything needs to be connected to the internet. A household dishwasher is almost certainly going to be in that category. And yet, here is Jeff Geerling, in the year of 2025, unable to run certain dishwasher cycles because of an inexplicable requirement for an internet connection. Please, can there be a company that specifically makes "dumb" devices?
Over 3 million applicants' data leaked on NYU's website
Washington Square News: New York University's website was hacked and taken over for at least two hours last weekend, exposing over 3 million applicants' names, test scores, majors and ZIP codes, including other financial aid information dating back to 1989(!) The defacement, which was littered with racist epithets, was taken down after a couple of hours. Not clear why NYU was storing data for this long, or had the data so easily accessible. Hats-off to the student reporters who covered this story so well.
~ ~
OTHER NEWSY NUGGETS
Ukraine railway bounces back after attack: Ukrzaliznytsia, the state railway of Ukraine, is back in action after online ticket sales were knocked offline this week during a cyberattack. Train schedules weren't affected, but few could buy tickets online for several days. Details of the attack weren't released (yet) but that there was no breach of sensitive data, per @darynant reporting from Kyiv. (via The Record)
A not-very-Advanced hack settled for £3m: U.K.-based NHS vendor Advanced will pony up £3 million (around $3.8M) in a settlement to the U.K.'s data protection watchdog after a not-so-advanced ransomware attack in 2022 knocked much of the company offline and resulted in the breach of tens of thousands of people's private health information. The breach was caused by a lack of MFA at the company, per the regulator. (via ICO, TechCrunch)
Chrome, Firefox zero-days under attack fixed: Not one, but two zero-days this week were patched after Google and Mozilla released fixes for their Chrome and Firefox browsers for Windows. The bugs appear to be linked to the same hacking campaign targeting Russian journalists, government employees and education staff, per Kaspersky, which found the bugs. (via Kaspersky, @cR0w)
Fake China network trying to lure federal workers: A researcher uncovered a network of companies operated by a secretive Chinese tech firm that's trying to recruit recently laid-off U.S. government workers. Reuters found that the network of companies appeared to be fake, and potentially a front for Beijing, likely as a way to exploit former workers who were let go in recent weeks. (via Reuters ($))
~ ~

~ ~
THE HAPPY CORNER
Deep breaths, it's the happy corner. Welcome in! You've earned it.
The perfect garden doesn't exi... oh it does.

Meanwhile, the mood this week lifetime:
In a little bright spark of good news, The Journal Times in Wisconsin announced it's back to full strength after a cyberattack at its parent company Lee Enterprises knocked dozens of news outlets offline and unable to print for some time. This is good to see! (via @PogoWasRight)
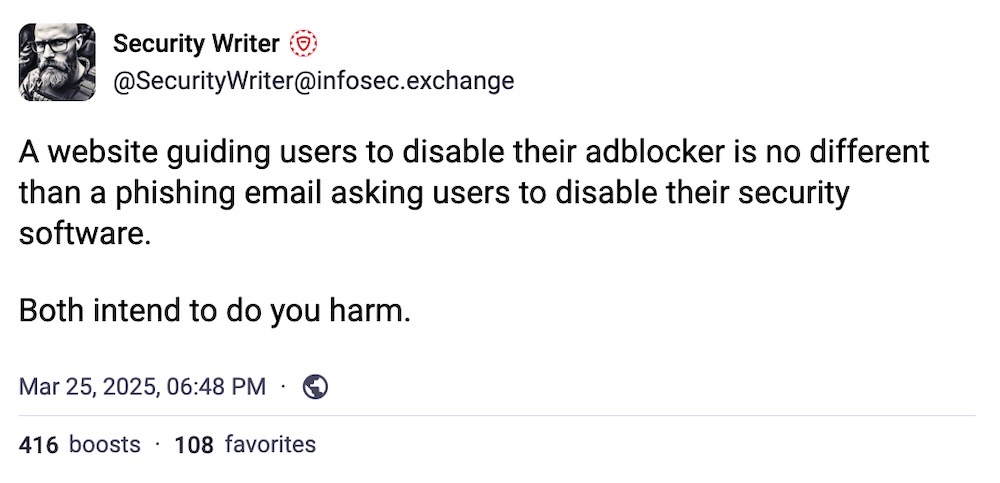
And finally, this week. A much needed moment of clarity. (Use an ad-blocker!)
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Whisper, who can be seen here absolutely kicking their humans' asses at poker (which is really saying something), in between her regular daily activity of shoulder-surfing their passwords. Genius kitty! Many thanks to Tarah and Deviant for sending in!

This newsletter runs on cybercats (seriously!). Please keep sending them in! Feel free to drop an email any time with a photo of your cyber cat (or non-feline friend) along with their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's it for this week in security, let's hope for some slightly better cybers this week. I'll be back with the usual round-up of everything you need to know from the week (plus more) next Sunday.
As always, please do get in touch if you have anything from the week, or for the newsletter, or just to say hi. I'm only an email away.
Gotta dash, my secret war Signal chat is blowing up,
@zackwhittaker