this week in security — march 31 edition
THIS WEEK, TL;DR
U.S. and U.K. accuse China's APT31 of sweeping spying campaign
Justice Department: The Biden administration has indicted and sanctioned seven key members of a Chinese state-backed hacking group dubbed APT31, which hacks and steals data as part of an ongoing, widespread and decade-long espionage campaign targeting businesses and government officials in the U.S., the United Kingdom and further afield. Per the Justice Department, APT31 conducted hacks that resulted in the "confirmed and potential compromise" of data on millions of Americans. British nationals, too, are affected by the Chinese spying efforts, with U.K. authorities accusing China of being behind a massive theft of 40 million or so voter registration records that happened in 2021 but only disclosed last year. APT31 also tried to steal U.K. lawmakers' emails also back in 2021. China denied the hacks — kind of — by noting it would "resort to lawful methods” to counter cyberattacks. Hmm.
More: U.S. Treasury | Reuters ($) | CNN | BBC News | Wired ($)
AT&T resets account passcodes after millions of customer records leak online
TechCrunch: If you heard about that huge leak of AT&T customer data, it's real, and AT&T finally took some responsibility this weekend. Some 73 million customer records, including names, Social Security numbers, and addresses, were published in full a couple of weeks ago after a hacker first advertised a sample of data (too small to verify) back in 2021. But, that full data appeared to contain encrypted customer account passcodes, security researcher @Chick3nman512 told me, and that the values could be easily decrypted without needing the decryption key. The major problem here was that those unscrambled four-digit passcodes could allow anyone access to AT&T customer accounts. We notified AT&T and held the story until the weekend so that AT&T could reset account passcodes. (Disclosure: I wrote this story!) AT&T has a brief statement and an FAQ you can read.
More: New York Times ($) | NPR | ABC News | The Verge
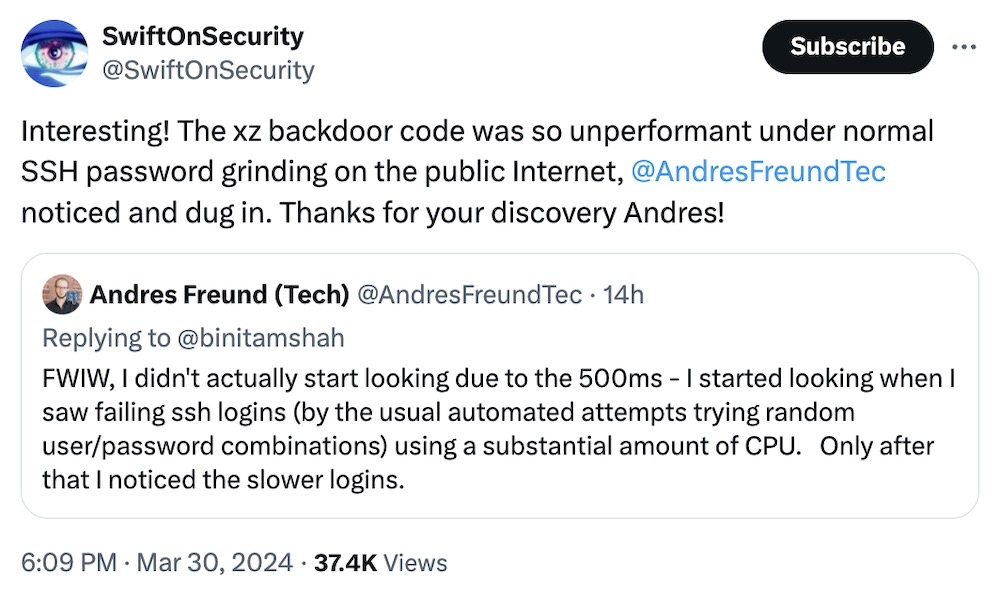
Backdoor found in xz Linux utility breaks encrypted SSH connections
Ars Technica: Researchers have found a malicious backdoor in the xz compression tool, a widely popular bit of code found in Linux distributions including Red Hat and Debian. Some Linux distros are affected, but Ars reports that there are no known reports of the backdoor making its way into any major Linux distro production releases. The backdoor was caught early (and FYI, major respect to @AndresFreundTec for this epic discovery). The backdoor is extremely sneaky and highly obfuscated, and allows for the breaking of encrypted SSH connections and potentially gaining unauthorized access to a wider system. The backdoor was allegedly planted by JiaT75, a long-running developer of the xz project, in the versions 5.6.0 and 5.6.1. It's believed xz 5.4.6 (stable) is safe, per CISA.
More: 404 Media ($) | Bleeping Computer | Decipher | Evan Boehs
~ ~
THE STUFF YOU MIGHT'VE MISSED
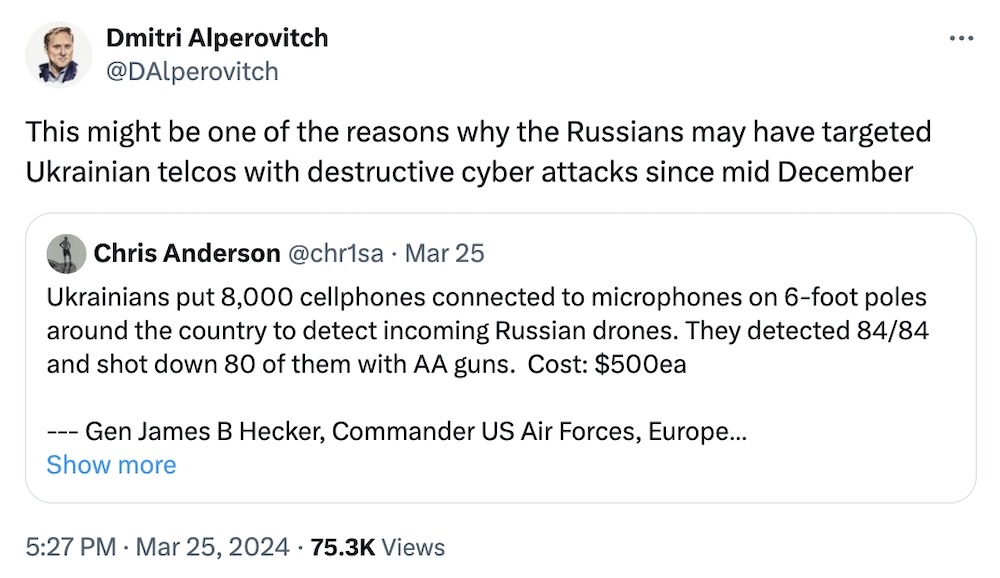
Why are Russian hackers targeting Ukrainian ISPs?
Dmitri Alperovitch: A new theory has emerged as to why Russian destructive computer-wiper malware might be targeting Ukrainian internet providers. Ukraine's air defenses includes an acoustic/audio listening system that relies on thousands of cellphones connected to microphones on six-foot poles around the country to "detect incoming Russian drones," per a video featuring a senior U.S. Air Forces commander. Each sensor is about $500 each (so pretty cheap) — but the system is highly effective — reportedly detecting every drone, with anti-aircraft cannons taking out almost every one. The Ukrainian system is called Safe Skies. It's no wonder that Russians are accused of trying to knock Ukrainian internet providers offline, which, in theory, would also knock out the anti-drone acoustic system.
UnitedHealth says it 'obtained' safe dataset of stolen patient data
Brett Callow: The aftermath of the cyberattack at Change Healthcare, the U.S. health tech giant that was hit by ALPHV ransomware hackers a couple of months ago, is still being felt as small medical practices and healthcare businesses are becoming cash-strapped due to the outage. Per @brett, UnitedHealth, the parent company of Change Healthcare, now says it's "obtained" a copy of the dataset allegedly stolen by the hackers "that is safe to use to access and analyze," (thanks, feds!) to determine what sensitive health and patient data was stolen in the cyberattack. All of this to say that it's slow, slow progress, but it's progress nonetheless. You can read the full update by heading to "Is patient health information compromised", which — probably, yes, but more details to come.
Serious security breach hits EU police agency
Politico: Highly sensitive files containing the personal information of top law enforcement executives at Europol were meant to be under lock and key in a secure basement storage at headquarters. But some of those files went missing last summer, and Europe's top law enforcement agency "has been mired in a whodunit ever since." Is it a leak? Is it a mole? Is it a spy? Maybe it was an HR stuff-up, since Europol's HR chief is on "administrative leave"? Politico has more.
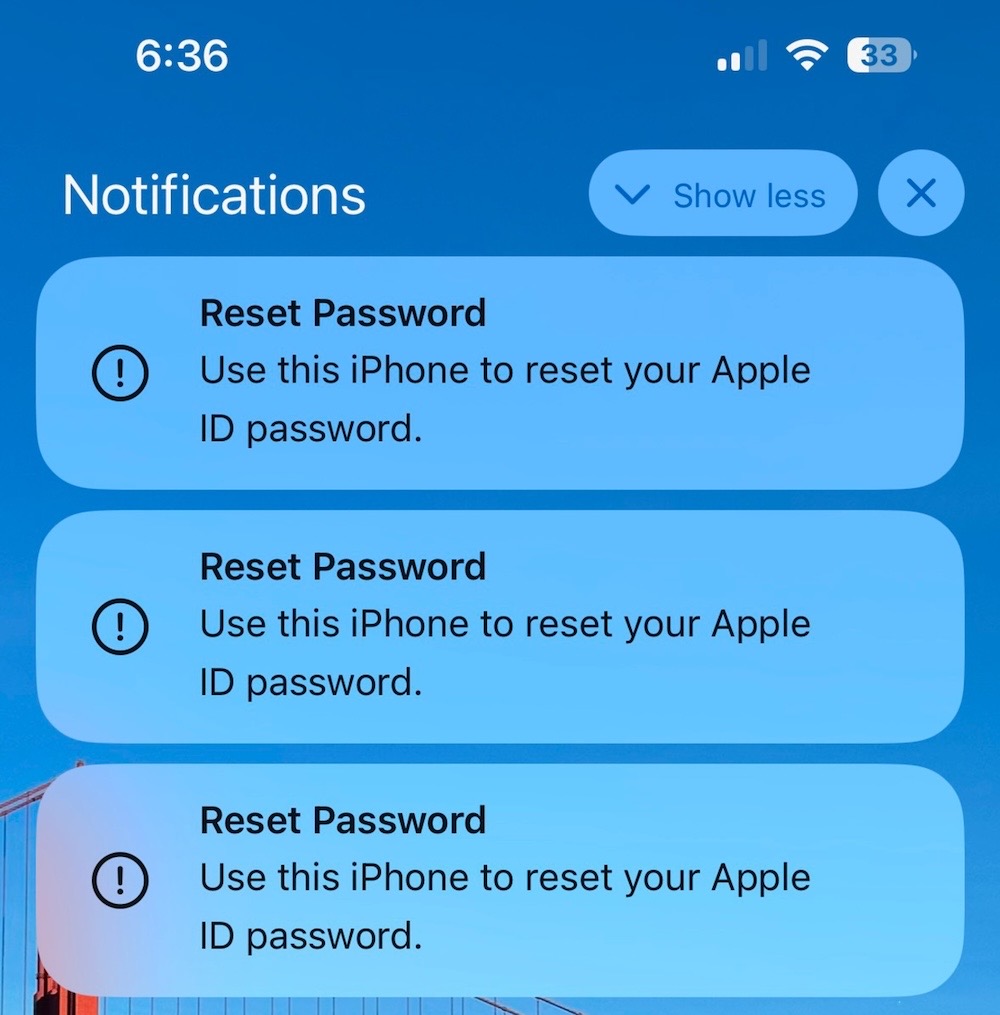
'MFA bombing' attacks target Apple users
KrebsOnSecurity: Apple customers are reporting "MFA-bombing" attacks, a malicious technique that repeatedly bombards users with password reset prompts and trick the victim into accepting one of a flood of two-factor (or MFA) requests. In being deluged with prompts, the victim may inadvertently approve a request to get back to their phone, and in doing so grant the attacker access to their account. @Parth, one of the Apple customers who was targeted, documented the incident in a tweet thread for awareness.
Facebook snooped on users' Snapchat traffic in secret project
TechCrunch: In 2016, Facebook launched a secret project designed to intercept and decrypt the network traffic between people using Snapchat’s app and its servers. This was allegedly part of Facebook's effort to understand users' behavior in the hope of gaining Facebook a competitive advantage over Snapchat. The trouble was that Snapchat's app data was encrypted in transit. So, Facebook used its on-device "research" VPN called Onavo to snoop on users' activity on the user's device before the Snapchat data was encrypted and sent over the internet. Very sneaky. So sneaky, in fact, that the project drew mixed reactions from Facebook's own security staff. "I can't think of a good argument for why this is okay," said Facebook's then-head of security engineering. The project was revealed in court papers released this week.
~ ~
OTHER NEWSY NUGGETS
Big bump in zero-day flaws, thanks to spyware: Commercial surveillance vendors (aka spyware and exploit makers) make up some 75% of known zero-day exploits targeting Google products and Android ecosystem devices in 2023, or 13 out of 17 flaws, according to Google's Threat Analysis Group's latest report into zero-days. Google also attributed 60% of the 37 zero-days targeting browsers and mobile devices in 2023 to commercial surveillance vendors that sell spyware capabilities to governments. More from The Record, and @maddiestone. (via Google TAG)
CISA rule would require cyber and ransom reporting: A new rule developed by U.S. cybersecurity agency CISA would require — if approved — covered organizations within 16 critical U.S. sectors to report cybersecurity incidents (like breaches) and ransom payments. Head's up, it's complex, but the ultimate goal is to help the government get more data and visibility so it can better understand cyberattack patterns, fill information gaps, rapidly deploy resources and help affected entities while informing others. CISA expects to publish a final rule in the next 18 months or so after public input and feedback closes. (via CISA, @johnnysaks130)
Punting for data: The University of Cambridge's medical school, one of the top in the world, has reported unspecified "malicious activity" on its network that resulted in disruption to its systems for the past month. The university has said little about the incident, but noted that "no data has been taken," though it's not clear if the university has the ability to check. (via Wired ($), @mattburgess)
Ring, ring. Yes, this is hacker: Here's the inside story of how a hacking group of mostly teenagers and young adults, which calls itself Star Fraud, broke into the casino giant MGM last year and stole an unspecified amount of customer data and caused a weeks-long outage. Star Fraud has worked with ransomware gangs and others in the wider cybercrime community, known as the Com, which was virtually unheard of a few years ago but has become one of the top cybersecurity challenges facing the United States today. (via Wall Street Journal ($))
~ ~
THE HAPPY CORNER
Good weekend to all! It's the happy corner.
There isn't much in the good news barrel this week, as it's been a real fustercluck of bad news. But if we still crack a smile at the end of it, it's worth it. So, since backdoors are the theme of this week in cyber:
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~

~ ~
CYBER CATS & FRIENDS
And since it's quieter than usual in the happy corner, let's have a two-for-one cybercat special! This week's cyber cats are Penelope and Violet, who are keeping close eyes on all things security. Remember, cybersecurity takes a village (and cats, obviously). Many thanks to Matt E. for sending in!

Send in your cyber cats! Feel free to drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
And that's it for this week's newsletter. Thanks for reading! I'll be back next Sunday with your usual roundup. I'm off to enjoy what feels like a rare moment of good weather for this time of year on the east coast.
As always, please do send in your cyber cats (or their friends). If you want to get in touch about anything else, I'm an email away.
Have a great week,
@zackwhittaker