this week in security — march 5 edition
THIS WEEK, TL;DR
Biden administration urges Congress to renew spy law
Wall Street Journal ($): Strap in for a long fight, as it's everyone's favorite time of decade: Section 702 reauthorization time. Pfffrrrbbht! 🥳 Except — serious faces now — the Biden administration might have quite the battle to keep its surveillance powers intact. Biden's top intelligence folks came in strong with their push to keep their 702 powers in a letter [PDF] to Congress, which it says are for targeting foreigners overseas to keep America safe. But, what about all the Americans whose communications get "incidentally" sucked up by the big-fat-NSA machine? That's really the big elephant in the room, since now the Republicans are also wising up to recent surveillance abuses, including the numerous times in which the FBI have raided the 702 database without having the proper legal authority. (Plus, it's not like the government doesn't already have these powers under EO 12333 anyway, but that's a whole shindig for another day.) Always read @LizaGoitein's tweets on this, since the government's only telling half the story it wants to tell.
More: New York Times ($) | White House | @nakashimae tweets
LastPass says employee's home computer was hacked and corporate vault taken
Ars Technica: In case you thought the LastPass breach couldn't get any worse, the attackers who broke in did so via an employee's laptop through a vulnerability in a very, very old version of Plex Media Server. That's a lot to unpack, but as always @dangoodin is doing the good work here breaking down exactly how LastPass missed this breach. To be clear, this isn't the employee's fault that LastPass ultimately got hacked, it's a common misconception because it's the company that is responsible for setting its security standards, including how your employees remote-in. What is clear is that keeping your software up-to-date is really, really important.
More: LastPass | PCMag | @briankrebs | @_MG_ | @kimzetter | @malwarejake
White House's new cybersecurity strategy stresses software safety
Associated Press: In other things the Biden administration did this week, it announced its updated National Cybersecurity Strategy, a huge body of work that stresses above all that companies need to make their software and technology more secure or face the consequences when things go south. Among the key focus areas are to defend critical infrastructure and make software more secure, while kicking bad actors with the full force of America. It's ambitious and frankly refreshing to see this plan take shape. Cyberscoop gets into the nuts and bolts, while CBS News looks at how regulation will play a part in enforcing its standards. And if you really want to engage your inner policy nerd mode, free agent @ericgeller doesn't spare any detail.
More: White House | Ars Technica | @k8em0 | @NicoleSganga
Dish CEO says data was stolen in ransomware attack
SecurityWeek: So, the thing that looked like ransomware and sounded like ransomware turned out to be... yeah, you guessed it. Dish confirmed the week-long outage was ransomware in an SEC filing. As such, Dish expects that data was stolen — including customers' personal information. Aside from Dish TV, most of its services were affected, including customer support. The satellite TV and media network's stock fell by 20% since the incident was first reported as a "system issue." And I can only imagine it'll get clobbered even more when the lawsuits start rolling in.
More: The Verge | TechCrunch | Bleeping Computer | Associated Press
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
BetterHelp shared users' sensitive health data, FTC says
Associated Press: Shout-out to BetterHelp for "absolute bastard" levels of awful behavior. The mental health telehealth platform shared users' sensitive health information that it promised to keep private with ad giants, including Snapchat and Facebook. BetterHelp will also pay $7.8 million to resolve the government's legal challenge, and banned it from sharing consumers' health data with advertisers. This kind of data sharing is so prevalent — it comes just after GoodRx got slapped by the FTC, too — and so there should be real scrutiny of any company that provides direct-to-consumer telehealth services via an app.
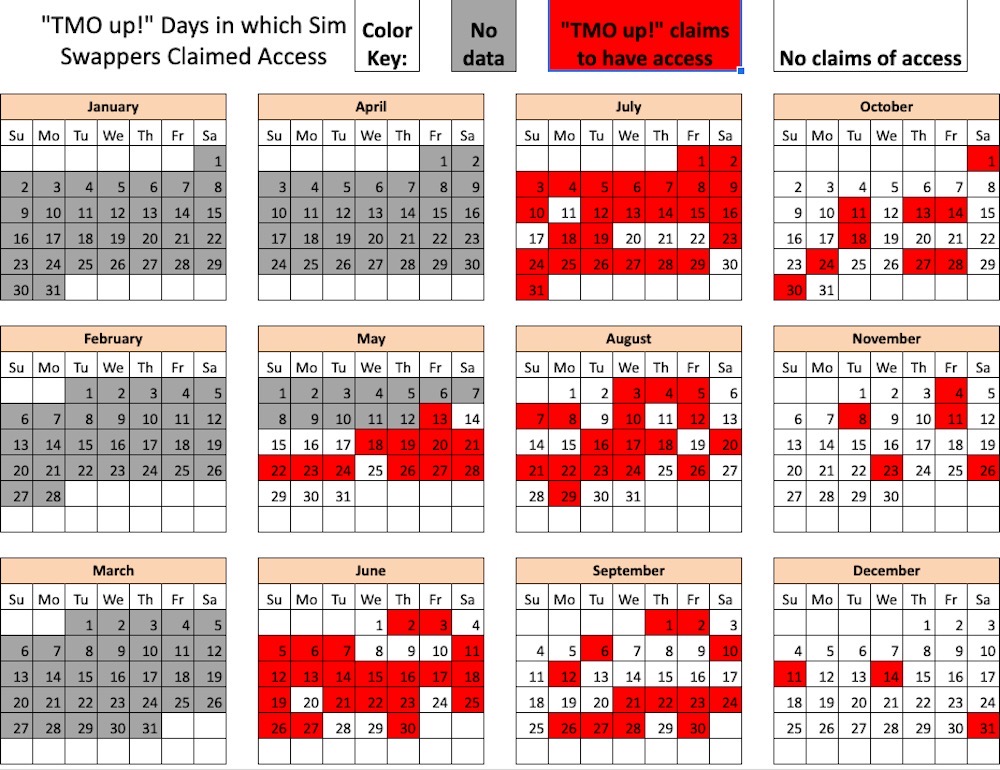
Hackers claim to have breached T-Mobile over a hundred times in 2022
Krebs on Security: @briankrebs got his hands on Telegram chat logs from three distinct cybercrime groups involved in SIM swapping attacks — essentially when hackers hijack your phone number to break into your other online accounts. By parsing the logs, Krebs found that the hackers broke into T-Mobile's network over a hundred times throughout 2022 to access internal company tools. Genuinely brilliant reporting here, I mean, this calendar alone is a work of art.
Bank says hackers used Fortra bug to steal 140,000 customer SSNs
TechCrunch: Speaking of Krebs, it was thanks to him that we all first heard about the zero-day bug in Forta's GoAnywhere file transfer tool. The first known victim was healthcare giant CHS, which saw 1 million patients' data compromised. Now the second-known victim has come forward., as digital-first bank Hatch Bank, which provides fintech infrastructure to companies offering their own brand credit cards, was also hit. Per a breach notification filed in Maine, of all places, Hatch said 140,000 people's Social Security numbers and other information was compromised in the attack on its GoAnywhere server.
Meet the investigator tackling Greece's spy scandal
Politico EU: Christos Rammos is the leading figure in the investigation into the Greek government's apparent use of Predator spyware to target opposition figures and journalists, which has been referred to as Greek Watergate. Politico profiles Rammos, who has the authority to — and has — conduct audits that lay bare some of the painful details of the government's abuses of surveillance powers. Rammos' term ends in 2025 and so he's in this for the long haul.
The life-upending flaw that USPS won’t fix
TechCrunch: A really simple flaw allows anyone to walk into a USPS post office, change someone's address and reroute their mail — and collect credit cards and other identifiable information — all because nobody checks ID when the paper form is handed in. It's a small but significant flaw that caught a former Microsoft executive off-guard when he was targeted in November. He told me his story, but when approached for comment, USPS and USPIS, its law enforcement arm, gave me the runaround. Maybe because they don't have a good reason for why this keeps happening to people — and not just the executive, but thousands of people a year. (Disclosure alert: I wrote this one)
CISA red-teamed a critical infrastructure organization for months and didn't get caught
The Record: In a new report, CISA showed off its Red Team's prowess. It took on a red-team offensive pen-testing job with a "large critical infrastructure organization," and, although the organization's security defenses worked and were blocked from accessing its core, the red team also didn't get caught. Something, something, logs and monitoring...
The role of cyber weapons in Russia's war on Ukraine
NPR: @JennaMc_Laugh takes you on an audio journey of the role that cyber weapons played in Russia's war on Ukraine, and although there's been a barrage of cyberattacks targeting Ukraine's infrastructure, "defense has proven to be far stronger than offense when it comes to attacks in cyberspace." Bloomberg ($) also dives in on the Viasat hack that knocked out satellite coverage over Ukraine in the days ahead of Russia's invasion.
~ ~
OTHER NEWSY NUGGETS
U.S. Marshals reports 'major' cybersecurity breach: The U.S. Marshals said it was hit by a ransomware attack involving a "standalone USMS system," reports NBC. The witness protection database is unaffected (because that would be absolutely catastrophic), but the Marshals said that the stolen data is sensitive — though nothing more than that. It comes not long after the FBI said it "contained" a cyber incident on its network involving a system used in investigations of images of child sexual exploitation. Let's hope the government isn't hit third-time unlucky. (via NBC News)
New bootkit bypasses Windows 11 secure boot: The developers behind the BlackLotus UEFI bootkit (think: near-unremovable malware) have packed in a new Secure Boot bypass that allows it to infect even fully patched Windows 11 systems Per Bleeping Computer, "BlackLotus is the first public example of UEFI malware that can avoid the Secure Boot mechanism, thus being able to disable security protections that come with the operating system." (via ESET)
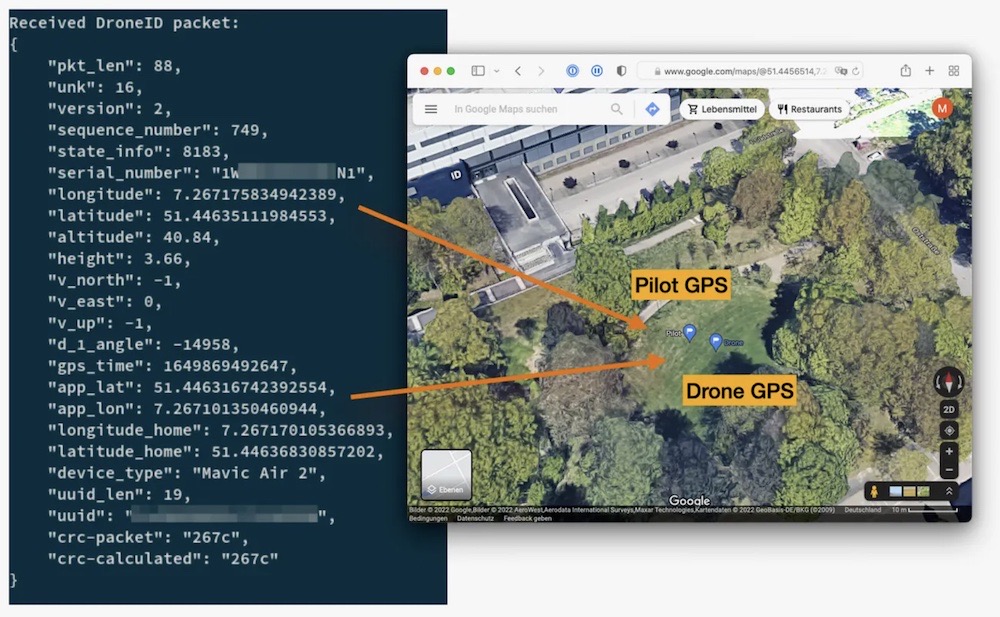
The 'e' in DJI stands for encryption: In case you didn't know, every DJI quadcopter drone broadcasts its operators' location via radio —entirely unencrypted. That's probably not good news for the folks on the ground using them in, say, warzones (like Ukraine, where they are actively used). To prove this, a group of German researchers developed a new prototype tool that exposes this major privacy (and potentially dangerous) consequence. (via Wired ($), @agreenberg)
Firearm owners' data stolen in gun auction site breach: Hackers breached a website that allows people to buy and sell guns, exposing the identities of some 550,000 users, including customers’ full names, home addresses, email addresses, plaintext passwords and telephone numbers. The data makes it possible to link a particular person to a sale or a specific weapon. (via Have I Been Pwned)
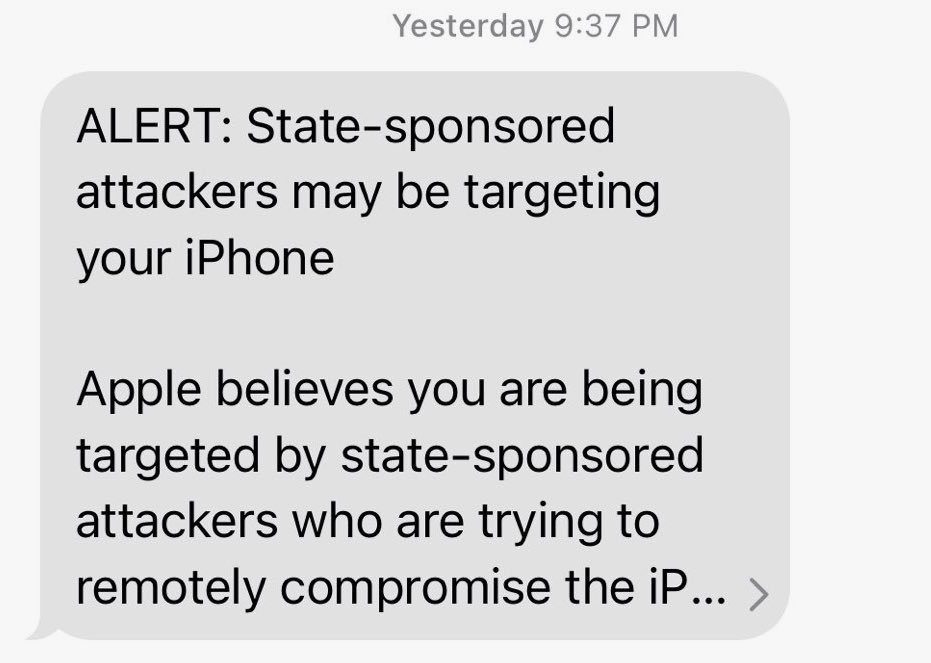
New nation state hack notifications just landed: A new round of Apple alerts went out this week notifying certain customers it believes are targeted by nation state spyware. At least one Armenian politician was targeted. It could be related to NSO's Pegasus and its alleged use by Azerbaijan intelligence, but @bing_chris says others outside Armenia were also alerted. Is it a new exploit or a re-run of those targeted by the iPhone-busting ForcedEntry bug? I guess we'll find out soon enough... (via @bing_chris, @runasand)
~ ~
THE HAPPY CORNER
Welcome, welcome. This is the happy corner. Leave any and all negative vibes at the door.
I don't know who needs to hear this — well, everyone actually. Remember, you can't give over data that you don't have.
Meanwhile, this Canadian grandma woke up one morning and chose violence — or the next best thing — revenge. According to BBC News, instead of hanging up the phone on her would-be scammer, Bonnie Bednarik, 74, went along with the ruse and ended up tricking the scammer into turning up to an address to pick up money where she had the police waiting. Apparently this was the third time a scammer had contacted her and clearly she'd had enough and took absolutely savagery into her own hands. Absolute legend.

And finally, can we commission this as a laptop sticker?

If you have good news you want to share, get in touch at: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's cyber cat kitten is Patches. Their human told me that they were experiencing a bug in the form of their 4-year-old needing a friend — and Patches seems to have worked. Best update ever! Many thanks to Jaymie A. for sending in.

Keep sending in your cyber cats! (Fluffy non-feline friends are also welcome.). Send in a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And I think that's it for now? Going once... going twice... I'll be back next Sunday with your usual roundup from the week. In the meantime, you can email any feedback or drop a note in the suggestion box.
Be well, be happy, enjoy the rest of your weekends, and see you next Sunday.
—@zackwhittaker