this week in security — march 6 edition
THIS WEEK, TL;DR
As tanks rolled into Ukraine, so did malware
The New York Times ($): Just as Russian tanks were rolling over the border into Ukraine, Microsoft said it spotted a never-before-seen destructive "wiper" malware aimed at Ukraine's government ministries and financial institutions. Microsoft alerted the White House and within three hours shared details of the code with NATO and other European countries, fearing the malware would spill across the region. The threat was largely mitigated. But U.S. and European officials still aren't completely sure why Russia hasn't yet unleashed its offensive cyber capability. It comes as Ukraine asks for as much help as it can get, including a controversial ask for ICANN to shut down Russian domains, which it denied, citing its mission "to ensure that the internet works," even in times of international conflict and war.
More: Microsoft | Ars Technica | Cyberscoop | @TonyaJoRiley
Hacktivists stoke pandemonium amid Russia's war in Ukraine
Wired ($): Meanwhile, hacktivists in Ukraine are fighting back with all it's got, including its own offensive cyber operations. This week saw over 120,000 Russian soldiers doxxed, as well as cyberattacks launched from and in neighboring Belarus targeting Belarusian and Russian infrastructure. Wired explores the rise of cyber-resistance. My colleague @ingridlunden spoke with Ukraine's deputy IT minister Alex Bornyakov, which sheds light on its "IT army" and its growing use, though non-exclusive use of Telegram. Speaking of which, @sinanaral looks at why Telegram has become so popular among Ukrainians — while @evacide has a good thread on threat modeling, and a post on how users in Russia and Ukraine can stay safe.
More: SecurityWeek | Reuters ($) | Pravda | BuzzFeed News | @dalperovitch | @selenalarson
Conti ransomware gang chats leaked by pro-Ukraine member
The Record: Talk about the motherlode: the Conti ransomware gang's chats, technical documentation, ransomware code, and other data has been leaked, in what is already proving to be a goldmine of intelligence for ransomware experts and network defenders — and journalists, like Bellingcat, who found they had been targeted by the group "acting on an FSB order." Conti is huge — raking in some $2.7 billion in bitcoin since 2017. Wild stuff.
More: Forbes ($) | Krebs on Security | @campuscodi
Cybercriminals who breached Nvidia issue one of the most unusual demands ever
Ars Technica: If you recall, Nvidia revealed a hack last week, and reports of a ransomware was "limited in scope," the company said. But hackers from a fairly new ransomware group are already leaking internal documents, thousands of employee passwords (since loaded in Have I Been Pwned), and even code-signing certificates, suggesting the breach wasn't as limited as Nvidia suggests. In broken English, the group made some bizarre demands — such as calling on Nvidia to remove LHR, or Lite Hash Rate, a feature that Nvidia introduced during a video card inventory shortage to stop their technology being snapped up by crypto-miners. It's also demanding that the company open-source its GPU drivers. The group is threatening to release silicon, graphics and computer chipset files for all its recent chips. Nvidia hasn't updated its breach page since March 1, long before the ransom demands came out.
More: TechCrunch | Have I Been Pwned | Nvidia
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
How China built a one-of-a-kind cyber-espionage behemoth to last
MIT Technology Review ($): A belter of a piece from @HowellONeill about China's rise to become a cyber-superpower, in part by its "stay in China" policy — which doesn't just apply to trying to keep the talent of security researchers inside its borders, but also security research itself. The piece also looks at China's offensive capabilities and its growing use of exploiting zero-days, including the development of a malware called Daxin, which has evaded attention for a decade.
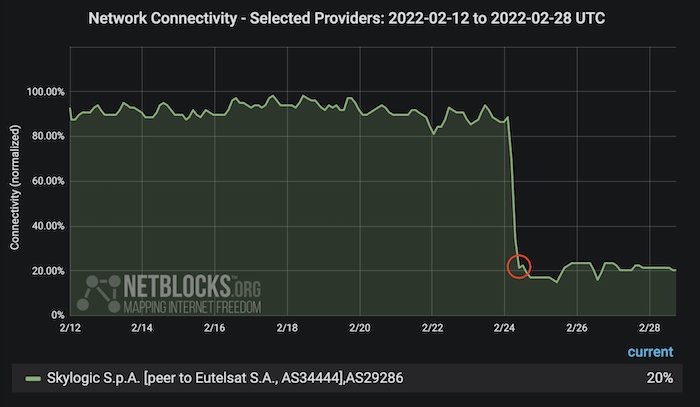
Satellite network Viasat hacked across Eastern Europe
Der Spiegel (in German): Here's a strange one. Viasat, a satellite internet network that operates across most of the world, says its Eastern European satellite network has been subject to a cyberattack for more than a week, starting at around the time of the Russian invasion. A "connection to the Ukraine conflict" is suspected, according to a German government report seen by Spiegel. A sabotage event for its KA-SAT satellite network, which operates over the region, is also suspected to be behind the failures of the satellite network. (This is one reason why you've probably seen Starlink in the news.) Not only is the cyberattack affecting customers in Ukraine, but also in Germany, where 3,000 turbines (some 11 gigawatts of energy!) are supposed to be connected to the grid via the satellite provider. Though electricity continues to be generated, the turbines are not currently accessible.
California state bar addresses breach of confidential data
State Bar of California: An embarrassing data breach for California's state bar — it confirmed about 260,000 non-public attorney discipline case records were published online by mistake, and were uploaded to a "public website that aggregates nationwide court case records." Whoops. The files were removed from the site. The organization has updates on its breach page, which suggests the aggregation was not malicious.
~ ~
OTHER NEWSY NUGGETS
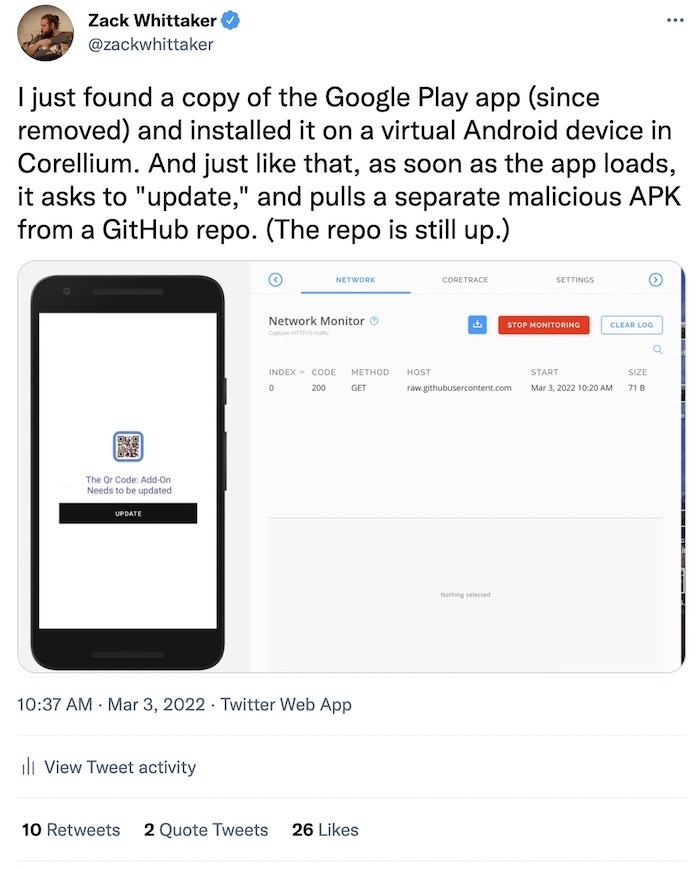
Data-stealing app found in Google Play downloaded thousands of times
TechCrunch: The TeaBot banking trojan is back, this time found in an Android app on Google Play, which was downloaded more than 10,000 times. A new report from Cleafy described how the malware app, a QR code reader, requests on startup that the user downloads an in-app update. That update is a malicious APK file stored in a GitHub repo, which when installed steals a user's data. The app was pulled from Google Play, so the app can no longer be downloaded. But the malicious GitHub repo had not yet been taken down at the time of the report's publishing. Cleafy made note of the GitHub repo in its report, but apparently made no effort to request that GitHub take the repo — or its malicious components — down. When I reported the repo as malware to GitHub, it was taken down about an hour later.
Personal data from T-Mobile breach still spreading on dark web, states warn
Cyberscoop: T-Mobile's massive data breach last year saw tens of millions of customers' data stolen, but according to state officials from New York, California and Florida that data is still circulating around the dark web. The data included IMEI numbers and other subscriber records. Its latest data breach is its fifth since 2018.
~ ~
THE HAPPY CORNER
Let's dip into this week's happy corner. First, obviously the world is in quite a bit of chaos at the moment, but I'm glad that some things remain ngrmadly. Wait, what?
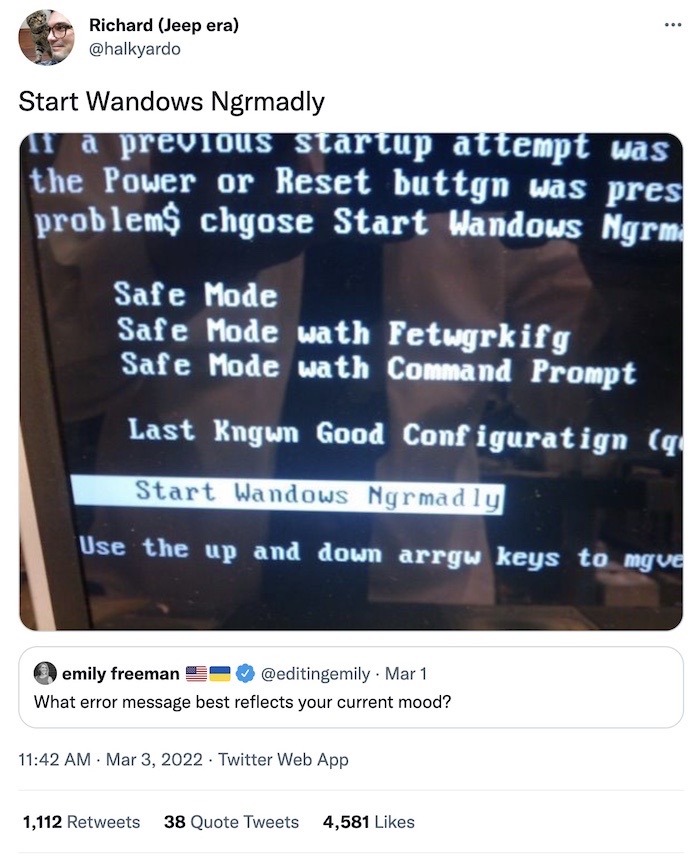
Next, this @tenderlove joke is truly terrible, so it's definitely worthy of a mention.
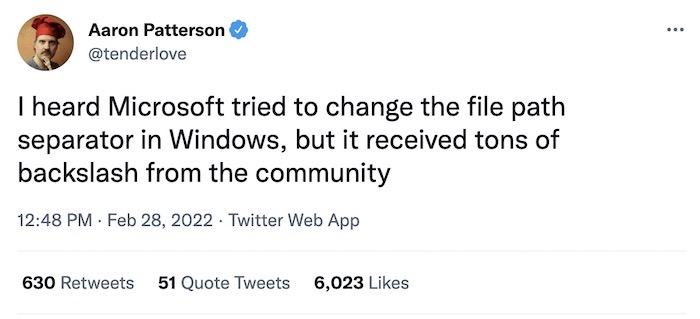
Some say that he's only The Grugq if he comes from the Grugq-region of France.
And finally. @razhael has a story about how the perfect set of circumstances led to the disclosure of a massive Russian cyberespionage campaign. It's a great story, and worth remembering that patience isn't easy but can often be worth it in the long-run, and cybersecurity — whether defensive or research — takes a village. You never know who your findings are going to help down the road.
To submit good news for the happy corner, reach out: this@weekinsecurity.com. More next week.
~ ~
CYBER CATS & FRIENDS
This week's two-for-one cybercats are Avery and Lucie, who as you can see here have been completely hijacked by what cat owners call a "treat attack." Don't worry, the side-effects are extremely tasty but short-lived. A big thanks to @devonjmalloy for the submission!

Don't forget to keep sending in your cyber cats (and their friends!). Drop me an email here with their name and photo, and they will be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's your lot for this week, thanks for reading! As always, feel free to drop your feedback in the suggestion box, or send me an email.
Be well, and see you next week. Have a great one.