this week in security — may 1 edition
THIS WEEK, TL;DR
Russia began setting the stage for cyberattacks against Ukraine a year ago
Zero Day: A Microsoft report out this week found that Russia started to lay the groundwork for launching cyberattacks against Ukraine as early as March 2021 when Russian hackers gained a foothold into Ukrainian government and critical infrastructure networks. Microsoft's report notes at least six separate Russia-aligned state hacking actors have launched more than 237 operations against Ukraine. The most notable are the destructive attacks launched by a GRU unit which researchers dub "Sandworm," which was blamed for the Ukraine power grid attacks in 2016 and 2017, and several other recent destructive attacks, including the Viasat attack that knocked out the satellite network over much of Eastern Europe. The U.S. Department of State put a $10 million bounty on six of the Sandworm hackers this week, shortly after CISA sounded the alarm over fears that the U.S. should itself brace for a Russian cyberattack.
More: Microsoft | Reuters ($) | TechCrunch
Tech giants duped into giving up data used to sexually extort minors
Bloomberg ($): Absolutely brilliant reporting by @williamturton, who uncovered that tech giants including Google and Apple processed fake emergency user data requests sent by hackers, often by breaking into the email system of a law enforcement agency. From there, the hackers file user requests for minors, which the tech giants turned over without verifying the requests. (These emergency requests are often filed amid threats to life or safety.) According to the report, the information given by tech giants was used to extort and harass minors. The tech giants have said little so far. Apple — which constantly harps on about how much it claims to care about your privacy — didn't even bother to comment. It's thanks to companies like... *checks notes*... Toontown, which helped to bring the issue to light. @nixonnixoff said that most of the companies that were duped "treated this as a shameful matter to be kept top secret." I think a lot of us will be thinking this...
More: Bloomberg ($)
How the French fiber optic cable attacks accentuate critical infrastructure vulnerabilities
Cyberscoop: Who needs a massive botnet when all you need, apparently, is a shovel? French intelligence is investigating an apparent act of sabotage that extensively disrupted internet services across France after a large number of fiber cables were cut. Now U.S. authorities are said to be on guard, knowing that fiber cables — which keep the backbone of the internet going — aren't well protected, and often their locations are widely known.
More: Washington Post ($) | Le Parisien (en français)
FBI conducted millions of searches of Americans' data last year
Wall Street Journal ($): According to the U.S. intelligence community's transparency report, pushed out every year by the ODNI since the Snowden leaks, the U.S. government conducted as many as 3.4 million searches of U.S. data previously collected by the NSA. That's without needing a warrant, since the data is collected and accessed under Section 702 of FISA, the law that allows the U.S. to spy on Americans, which is due to expire next year. The actual number of direct searches investigating Americans is probably far lower. More than half of the searches — close to 2 million — were related to a national security investigation involving attempts by alleged Russian hackers to break into U.S. critical infrastructure networks, for which the searches included efforts to identify and protect victims — including U.S. citizens. The WSJ does a good job of breaking down the figures and what they mean — and, @emptywheel, as always, has you covered.
More: CNN | The New York Times ($)
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Twitter's legal team is an aggressive defender of free speech, will that continue?
Techdirt: After the news finally dropped that Elon Musk would buy Twitter — a deal that still has to pass shareholder and regulatory approval(!) — @mmasnick dug into how Twitter's legal department has been an "aggressive defender" of free speech, in large part by pushing back on subpoenas, often filed by "thin-skinned rich and powerful users," and what Musk's Twitter buy might mean for content moderation, privacy and free speech.
European wind-energy sector hit in wave of hacks
Wall Street Journal ($): Three Germany-based wind energy companies have been targeted by cyberattacks since Russia's invasion of Ukraine, at a time where Germany is moving away from its reliance on Russian oil and gas after Western sanctions try to cut off Russia from the rest of the economic world. The problem is that Germany is highly dependent on Russian oil and gas, and switching away to less reliant fuels is likely a multi-year process. Not a huge surprise then that cyberattacks targeting renewable, non-fossil fuels have swept the country, in some cases with ransomware, aimed at disrupting energy supplies. "A simpler strike on local internet-connected services could interfere with the remote monitoring systems of wind farms," according to one security expert. You know, just how Viasat was hacked, causing roughly 5,800 wind turbines that relied on the satellite network to lose connection.
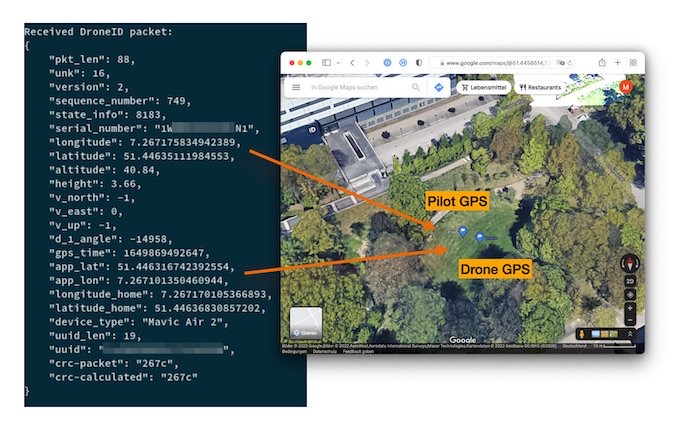
DJI insisted drone-tracking AeroScope signals were encrypted — now it admits they aren't
The Verge: In March, Ukraine's vice prime minister accused drone maker DJI of helping Russia kill Ukranians by allowing Russia to freely use its drone detection system called AeroScope. DJI claimed that AeroScope signals are encrypted. Turns out, they're not. That means governments (and others) don't need AeroScope to see the exact position of every DJI drone. It wasn't until hacker @d0tslash proved that the signals aren't encrypted that DJI finally admitted that its remarks weren't truthful.
~ ~
OTHER NEWSY NUGGETS
Mexico top court strikes down phone and biometrics registry: Reuters ($) reports that Mexico's Supreme Court ruled that the government's plans to create a national phone user registry tied to biometric data is unconstitutional. The phone carriers didn't want it as it would've been costly to implement, but the government said it would've fought crime — where Mexico has some of the highest incidences of abductions in the world. The court said the registry would've violated human rights. Mexico has some 120 million cell lines, most of which are pre-paid.
Microsoft finds critical Linux flaw: A duo of privilege escalation bugs in Linux, dubbed Nimbuspwn, can be exploited to quickly gain root/system level permissions to an affected device. Ars Technica goes deep on the technical details, including how to gain persistent root access for a future backdoor.
~ ~
THE HAPPY CORNER
A shorter newsletter than usual this week, since it was, well, kinda quiet out there after what has been a frenetic few weeks.
Great news that security.txt is finally an RFC, according to @EdOverflow, who was one of the main proponents of security.txt. For those who don't know, security.txt is a publicly accessible text file that admins can put in the root of their website directory to help researchers and hackers easily find urgent security contact information. It's a great idea that's aimed at speeding up the process of finding and alerting companies to security flaws. Some of the biggest companies use it — Yahoo and Google to name a couple. You can see how Google's security.txt, for example, looks here. Excellent news and extremely well deserved.
And finally: @TinkerSec (one of my favorite Twitter accounts for physical security and pen-tests) put up a challenge this week. Can you guess the door code? Admittedly, I spent way longer than I should've on this. The answer is in the thread but the thread is well worth the read for understanding the process — as well as how to mitigate these kinds of code-guessing attacks.

To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
Meet RiffRaff, this week's cyber cat and... bag bodyguard. We know there is no such thing as "hackproof," but there's always one exception to the rule — there's no way anyone's getting in that bag with RiffRaff on guard! A big thanks to @terpkristin for the submission.

Please keep sending in your cyber cats (or their friends)! You can drop an email here with their name and photo, and they'll be featured in an upcoming newsletter. Don't be shy!
~ ~
SUGGESTION BOX
And I'm out for this week — many thanks for reading! The suggestion box is open or feel free to email me with any feedback. Have a great week, back next Sunday.