this week in security — may 11 2025 edition
THIS WEEK, TL;DR
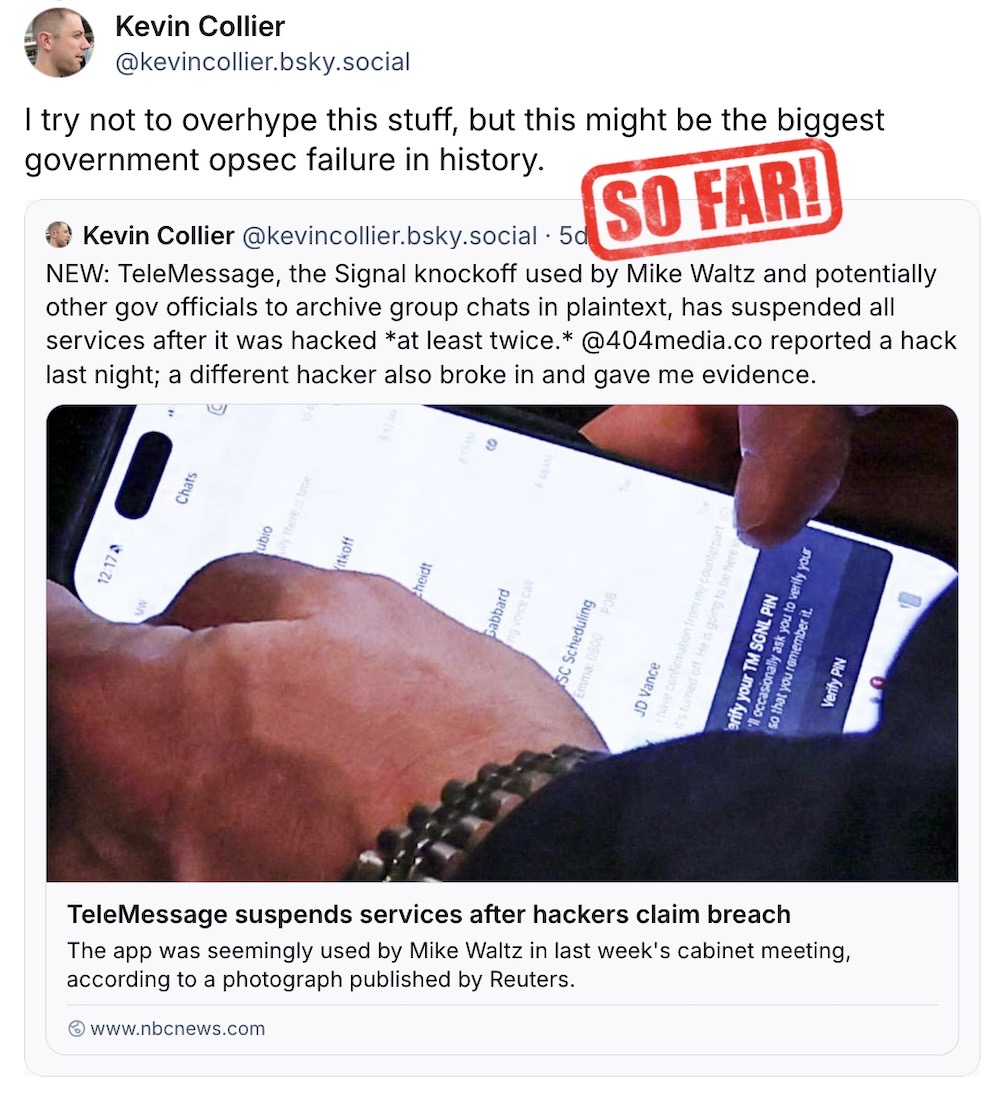
The Signal clone app used by Trump officials was hacked
404 Media ($): "Can it get worse?" I wrote last week. Well buckle up, folks, because it really, really does. Remember how Trump officials were caught using a Signal-like clone app called TM SGNL, which was designed to archive and store messages sent through the app, defeating whatever veil of ostensible end-to-end encryption the company claimed it had... Well, the company behind it, TeleMessage, was hacked, and revealed that the company had access to its users' group chats and messages. You know, White House officials. But not just that, other federal departments were using the app, as well as Coinbase and other regulated industries. The reporting is significant: Clearly this app was trusted by some of the most senior government officials and it has proven to be a hot mess of security. Soon after, TeleMessage was hacked again, and the company suspended its service. Micah Lee did a ton of analysis here, analyzing the app's source code and finding that TeleMessage could, in fact, access plaintext messages of its users. Bad security all around.
More: NBC News | Micah Lee | Wired ($) | @josephcox thread | @gregotto
NSO Group must pay $167M following 2019 WhatsApp spyware hack
TechCrunch: Spyware maker NSO was ordered this week to pony up $167 million in total damages — a number that NSO will likely appeal — after a court ruled NSO liable for a 2019 hacking campaign targeting some 1,400 WhatsApp users. NSO broke U.S. computer hacking laws in abusing WhatsApp's servers to deliver spyware to the thousand-plus victims, and this ruling was to determine how much NSO should pay as a result. It's a sizable sum, even though WhatsApp asked for only $400k or so; it means spyware makers can't hide behind the notion that "oh, we're working for governments so we're immune from prosecution" and puts these surveillance vendors on notice. My TC colleague @lorenzofb dug through the court transcript and noted five interesting takeaways from the trial and docket.
More: Courthouse News | Platformer ($) | Ars Technica | Cyberscoop | @jsrailton posts | @davidakaye | @caseynewton
PowerSchool paid a ransom, but school districts are being extorted anyway
NBC News: Edtech software maker PowerSchool was hacked late last year and paid a ransom, but refused to say how much it paid or what evidence it supposedly had that the data was "deleted" (heavy air quotes). Now, school districts across North America — including Toronto's school district and schools in North Carolina, are being extorted. PowerSchool said it's the same data in play, so it's not another hack, but said it made the "difficult decision" to pay the ransom at the time, even though it knew the hacker's claims might be bunk. Paying a ransom doesn't guarantee anything, but makes you a target for revictimization — and we know ransomware gangs don't delete the data they steal. Good on the school districts coming forward, though, clearly they're in a tough spot here.
More: Toronto District School Board | DataBreaches.net | TechCrunch
~ ~
THE STUFF YOU MIGHT'VE MISSED
Where cybercriminals are hosting their badware
Vin01: You might wonder, "why would I care where cybercriminals are hosting their crimeware?" Because it could be on your domain, pinching your server space and bandwidth without your knowledge. Bad actors exploit bugs in websites — from governments to universities and schools — as these provide cover for malicious operations. Vin01's read on this can help you narrow down where to look.
Ransomware gangs caught abusing KickIdler monitoring software
Bleeping Computer: Varonis (strong meme game) and Synacktiv have observed ransomware gangs taking advantage of the KickIdler employee monitoring software (which captures user keystrokes) to conduct reconnaissance in malicious cyber campaigns and to steal credentials. It's a new twist on efforts to trick victims into installing remote access tools, as noted by CISA in 2023. Bleeping has your simple explainer on what to look out for if you're a network admin.

DOGE technologist's computer infected by password-stealing malware
Micah Lee: Lee is back with another belter. Area DOGE bro Kyle Schutt, whose work with DOGE as a technologist gained him access to databases at FEMA and more, had malware installed on his computer that stole his passwords, according to a review of his email address in Have I Been Pwned. If Schutt's personal computer had any link to a federal system, well that could obviously be a problem. In any case, this is what the state of federal government infosec looks like in the year of 2025.
Hundreds of e-commerce sites hacked in supply chain attack
Ars Technica: Researchers at Sansec (who've done some great research looking at Magecart and other card-stealing malware) say at least 500 e-commerce sites have been hacked by way of backdoored software, which Sansec lists as IOCs. It's problematic because the backdoored code can be used to skim credit card numbers and other information submitted by customers to websites for payments.
Inside the firmware of a Starlink terminal
Darknavy: Here's an interesting inside-look at a Starlink device, the satellite-powered internet terminal. Darknavy tore apart a terminal, and extracted and analyzed the firmware (because of course), and found — among other things — at least 41 SSH public keys within the code. "Having such a large number of unknown login keys on a user product certainly raises eyebrows." Not sure using anything connected to Elon Musk these days is a good idea...
~ ~
~ ~
OTHER NEWSY NUGGETS
CrowdStrike cuts 500 jobs for "efficiencies": Cybersecurity giant CrowdStrike will cut 5% of its workforce, or 500 people, so the company can "operate more efficiently," per CEO George Kurtz and an 8-K filing. For his part, Kurtz made $46 million in executive compensation during 2024, so that seems like very much part of the problem. (via WSJ ($), TechCrunch)
NSA downsizing by 2,000 snoops: The National Security Agency is also downsizing, and expected to cut as many as 2,000 roles at the U.S. spy agency. The CIA and other U.S. intelligence agencies are also facing cuts. The NSA still doesn't have a permanent director, more than a month after then-NSA head Timothy Haugh was fired by the president without warning. (via Washington Post ($), The Record)
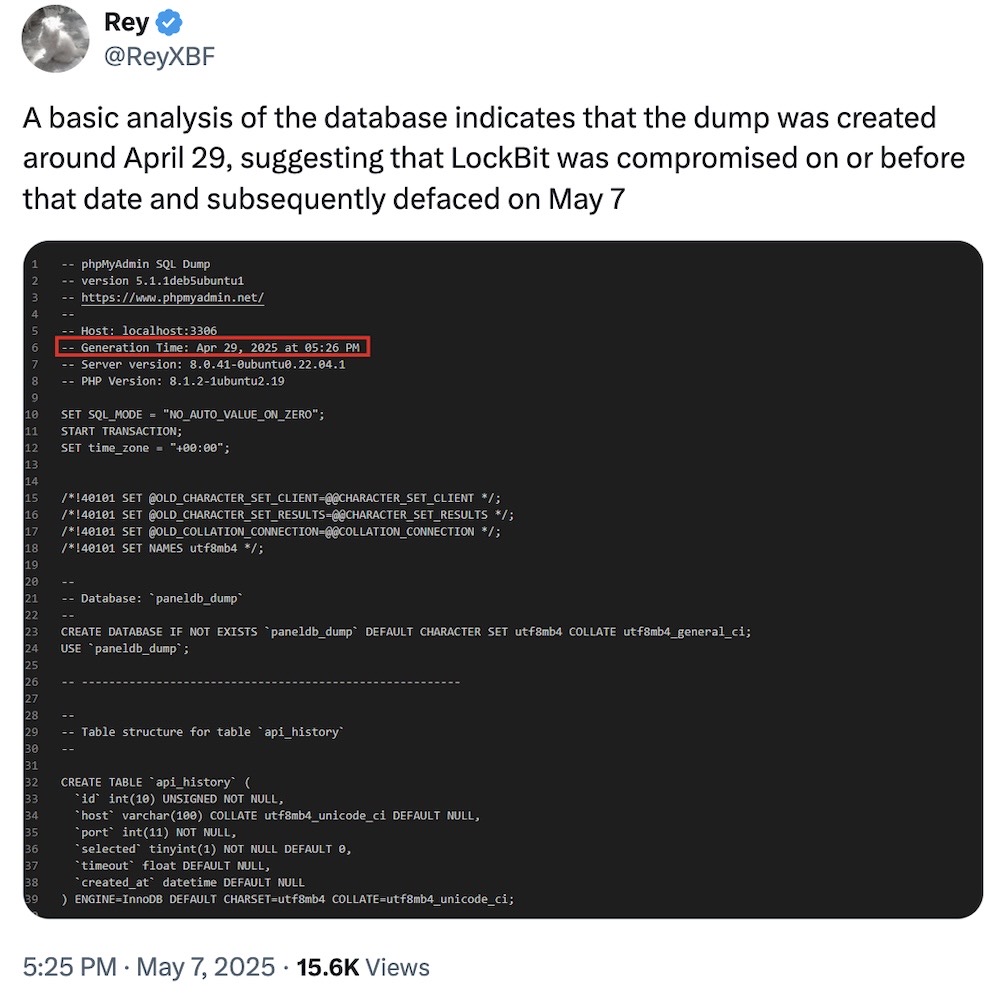
Crime is bad, LockBit edition: The LockBit gang was hacked, and its dark web leak site defaced with a message, "Don't do crime CRIME IS BAD," a message first seen a few weeks ago with the fall of the Everest ransomware gang. This time around, LockBit's server innards — including chats containing ransomware negotiations — was published in place of its website. It's another blow for the former ransomware giant, which has been seized, indicted, doxed, and now hacked. (via Bleeping Computer, @reyxbf)
Deportation Airways hacked: GlobalX, an airline used by the Trump administration for deportations, was hacked. Per a regulatory filing, the company said the full scope of the hack isn't known. But, 404 Media ($) reports that the data includes flight records and manifests — including the name of at least one individual, who was disappeared by ICE and whose name wasn't on any government deportation lists, but now appears in the hacked files as someone flown to El Salvador. In short, that means a private company may have more accurate records of where people are than... *checks notes* the federal government. (via 404 Media ($), PBS)
South Korean telco giant apologizes for huge breach: As many as 25 million customers of SK Telecom, South Korea's largest phone company, may need new SIM cards after the telco was hacked and its central database of SIM data was compromised. The company hasn't handled its scandal well, with half of the country now at risk of SIM swap attacks and government surveillance, but finally spluttered out an apology. Here's a timeline of how the breach went down. (via Korea Times)
U.K. grocery store hacks affecting shelves: The cyberattacks targeting U.K. retail and grocery giants, including the Co-op and Marks & Spencer, are reporting ongoing disruption and shelf shortages. Some food stuffs are being rationed at some more remote locations. Orders are still paused following what's been reported as a ransomware attack, so expect this to affect a lot of people's personal information, as the disruption is expected to last for some time. (via Reuters ($))

~ ~
THE HAPPY CORNER
And not a moment too soon... It's time to leave your troubled week behind, for this is the happy corner.
A Florida bill that would have required social media companies to build an encryption backdoor for accessing their users' accounts has been "withdrawn from consideration" in the Florida House, not long after the Florida Senate passed the bill. The EFF called the bill "dangerous and dumb," which says it all, really.
Denver will stop using Flock cameras, much to the delight of some. Flock cameras are controversial due to privacy concerns and fears over cooperation with immigration authorities, and so the Denver council has voted to stop using them altogether.
Anyone fancy hacking some facial recognition cameras? I hear path traversal bugs are all the rage these days... (via @da_667)

And finally, this week, keep this excuse in your back pocket when you're told you're not getting that new hire any time soon.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet Lord Meow (the Rt. Hon.?), who rules over his human master and acreage. All hail Lord Meow, chief advocate of good security and passkey defender. Long live Lord Meow and MFA All The Things! Thanks so much to Tapas for sending in!

Keep sending in your cyber-cats (or a non-feline friend!) The reservoir of cyber-cats is refilling but we're still in a drought. Drop a photo and name of your cyber-cat or friend by email, and they will be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's it for this busy week in infosec! As always, please reach out by email if you have anything to share for the newsletter, like a cyber-cat, or if you just want to say hello.
On a personal note, I want to say thank you so much for taking the time to respond to my newsletter survey over the past few weeks. Your responses, feedback, and your hundreds of comments, above all, were incredibly kind and supportive; it really means a lot. I look forward to writing this newsletter every week, and I'm excited for what the future holds.
Off to surf some interwebs,
@zackwhittaker