this week in security — may 14 edition
THIS WEEK, TL;DR
FBI disables malware Russia used to steal secrets from NATO allies
Wall Street Journal ($): This week's DOJ-athon saw prosecutors run a series of takedowns targeting international crims and spies. First up, the FBI effectively shuttered the long-running Snake malware, which Russian spies (aka Turla) allegedly used to steal data from the U.S. and NATO allies. Snake siphoned data and routed it through U.S. computers to cover their tracks. @dangoodin has an explainer on how the feds took down the operation, but in short, the FBI built a tool that could mimic Snake's commands — including telling it to shut down.
More: Justice Department | CISA | Ars Technica | TechCrunch |
U.K. national extradited, pleads guilty to 2020 Twitter hack
Justice Department: Continuing the DOJ's burst of activity this week: Prosecutors extradited a 23-year-old British hacker to the U.S. to face computer hacking charges after pleading guilty to breaking into Twitter in a high-profile 2020 hack, in which he hijacked top accounts to spread a cryptocurrency scam (badly, it seems — it only netted about $100,000). Meanwhile, the FBI and Ukrainian police also shuttered a handful of crypto laundering sites. And, topping things off, a team that calls itself Big Pipes took down its latest targets, a set of 13 so-called "booter" sites that launch network-crippling DDoS attacks. "And now, the DOJ will sleep, saving its strength for another takedown day," he says in his best Attenborough voice.
More: U.S. Attorney (EDMI) | Wired ($) | @nixonnixoff
Leak of MSI UEFI signing keys stokes fears of 'doomsday' supply chain attack
Ars Technica: A ransomware attack on hardware maker MSI exposed source code and private keys that can be used to digitally sign MSI's software and firmware. Now that key is in the wild, fears are that hackers could — in theory — use the keys to build tainted updates that look like MSI made them. Worse, there's no easy way to revoke the keys. MSI makes high-end gaming desktops and laptops, as well as motherboards for other devices. MSI has stayed hush about the incident so far.
More: Bleeping Computer | Decipher
EU urged to tighten spyware safeguards in wake of Pegasus revelations
The Guardian ($): European lawmakers have voted on measures that the EU should take to tighten protections against the use of nation-state spyware. The PEGA committee's vote to ban spyware (like NSO's Pegasus and Cytrox's Predator) is non-binding, but concludes that Hungary and Poland were among several EU member states that used spyware to monitor journalists and politicians. That could allow European parliamentarians at large to take action. But as the committee's lead author Sophie in 't Veld noted, more should be done. "Not one government has really been held accountable." @jsrailton has a toot thread explaining what actions the EU committee called for.
More: European Parliament | EPP | Amnesty International
Millions of U.K. pension savers' personal data taken in Capita hack
The Telegraph: The Capita hack continues to wreak havoc on the U.K., as one of the country's biggest outsourcers remains largely silent after its massive ransomware attack that exposed a good portion of the U.K. government sector. The breach is now said to affect some 350 corporate retirement schemes used by businesses across the U.K., some with hundreds of thousands of members, making this one of, if not the biggest hack in British history. Capita has claimed "no evidence" of data exfiltration, all the while reporters and researchers are saying, uh, yeah, a lot of data was stolen. But classic denialism isn't getting Capita very far — and it's really starting to piss off the victims, including local councils and affected companies. Here's @GossiTheDog with a running commentary of all the information Capita won't tell you.
More: SecurityWeek | BankInfoSecurity
~ ~
THE STUFF YOU MIGHT'VE MISSED
White House considers ban on ransomware payments
Cybersecurity Dive: The Biden administration is mulling what a ban on ransomware payments would look like. Though clearly nothing set in stone, NSC cyber lead Anne Neuberger said specific conditions could warrant exceptions — such as if a ransomware group knocked critical infrastructure offline. So far an outright ban hasn't taken shape because of risks of unintended consequences. That said, orgs are still encouraged not to pay as to not feed the money-making cycle. (via @brett)
MWC organizer slapped with GDPR fine for illegal biometric ID checks
TechCrunch: Mobile World Congress, one of the biggest mobile and tech events, was fined about $224,000 by Spanish regulators for collecting event-goers' biometrics via a facial recognition system for verifying a person's credentials for the show. Only a few thousand attendees used the system, but the event failed to do its due diligence — and was found to have violated GDPR under EU law. More from Dr. Anastasia Dedyukhina, who filed the complaint. (Good!)
Inside one hospital's fight to recover from a ransomware attack
NPR: Here's a look at how one Indiana hospital system battled a ransomware attack. The incident itself is remarkably similar to so many stories, but worth noting that cybersecurity insurance is lackluster — at best — and premiums only went up after the incident. As much as good security is one component, a hacker only has to be right once — and no company is impervious to a breach. But given the profit-driven nature of healthcare in the U.S., who ultimately pays for it in the end? Patients.
Twitter's encrypted DMs are a hot mess
Wired ($): Twitter's new encrypted DMs, which are limited to paying subscribers of Twitter Blue, are technically flawed, opt-in, and deeply inferior to Signal and WhatsApp. Wired's look at how Twitter built its broken encrypted DMs system is worth the read because it would be laughable if this wasn't also so incredibly serious. If you want to send E2EE messages, just use Signal. Don't take no for an answer, and certainly don't use Twitter DMs.
Testing Converso, a new encrypted messaging app's extraordinary claims
Crnkovic: Speaking of busted claims... a messaging app called Converso claimed to be a "state-of-the-art" encrypted messenger that stores no data (nor metadata) on the server. What bold claims! Shame they don't stand up under the lightest scrutiny. A closer look allowed this researcher to access the app's user database, which was inadvertently public. If you want to read a detailed, meticulous, surgical takedown of this marketing fluffed crap, crack your knuckles and get stuck in.
Security experts say more gig workers are vulnerable to account hacks
KCRA: It's sometimes overlooked that gig workers are users, too, and the companies that they contract for — the Ubers, Postmates' and DoorDashes — are as much responsible for the security of its contactors as its consumers. But KCRA found that one DoorDash driver had their earned money taken because a hacker broke into their account and changed the email address and phone number, locking the gig worker out completely. From the report: "She tried to contact the company to clear up the mistake, but she says she wasn’t able to prove that someone else was logging into her account." Yeah, that's not a driver problem, that's a DoorDash problem — and it's clear that DoorDash could figure this out if it had effective logging in place to see the email address change.
~ ~
~ ~
OTHER NEWSY NUGGETS
Personal data of federal employees stolen in DOT hack: A breach at the U.S. Department of Transportation exposed some 237,000 current and former federal employees, whose information was stored on a server for processing transit benefits that reimburse workers' commuting costs. The DOT reportedly notified Congress on Friday. (via Reuters ($))
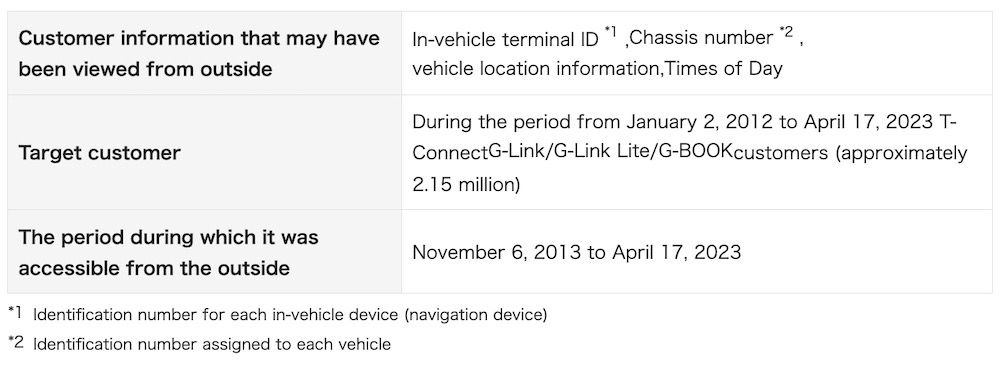
Two million Toyota cars had locations exposed for a decade: Toyota Japan apologized this week after confirming that a cloud misconfiguration exposed the vehicle data — including their locations — of more than 2 million Toyota cars in Japan to the internet for about a decade. The data also included video footage collected from the car's drive recorders. (Disclosure: I wrote this story!) (via TechCrunch, Toyota Japan)
Android phones packed with malware: Cheap Android phones, watches, TVs and other devices contain firmware with "undesirable" features – some 80 different plugins embedded within the firmware that steal data from an infected device or engage in ad-spam. By outsourcing the firmware making process, it allows upstream developers to sneak in malicious code. (via The Register)
Automation giant Rockwell under natsec probe: Rockwell, which makes automation tech for U.S. critical infrastructure and the military, is under federal investigation as to whether its China-based developers have "access to software codes that connect with those computer systems." According to the WSJ, a whistleblower claimed "that Rockwell does its code development, support and patching — updating software to fix vulnerabilities — using only Chinese nationals at the facility in Dalian, a port city at the southern tip of China’s Liaoning province." As a result, some companies and government agencies are worried about the security implications. (via Wall Street Journal ($))
~ ~
~ ~
THE HAPPY CORNER
Welcome, welcome. Hello again. It's the happy corner.
If you see a DHCP server in the wild, make sure you take an IP address with you. You never know when you'll need it. (via @paulasadoorian.
Also this week, there's plenty of chatter about domain hacks. Google this week approved .zip and .mov — common file extensions — as... top-level domains. Yes, that means you can essentially write financialstatement.zip and it leads you to... well, handily, a website noting just how problematic this might be. On the bright side, it's spurred folks to share their best "domain hacks" (that take advantage of new top-level domains for good reasons), like systemd.network's handy network configuration guide, and server.properties, which is just a low-key chill list of Minecraft server properties.
And finally. Apple has updated its Personal Safety User Guide document, which features new information on how to set up Safety Check and also use other features aimed at preventing spousal abuse, stalking and harassment. Even if you don't need this yourself, it's helpful to brush up on what these features can do in the event you can help others. (Thanks to @campuscodi for tooting.)
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat kitten(!) is Federico, who can be seen here protecting his human from clicking on phishing emails. Who needs endpoint detection when you have a watchful kitten? Many thanks to Jane C. for sending in!

Please keep sending in your cyber cats! Send in a photo and their name, and they'll be featured in an upcoming newsletter. (Cyber cats and their non-feline friends are welcome!)
~ ~
SUGGESTION BOX
It's good to be back after a week away. Thanks so much for reading! As always, you can send any feedback (or suggestions!) by email. I'll be back next week with your usual roundup from the week.
My best to you and yours,
—@zackwhittaker