this week in security — may 15 edition
THIS WEEK, TL;DR
Hackers are actively exploiting BIG-IP flaw with a 9.8 severity rating
Ars Technica: Bad news if you're an F5 BIG-IP customer after security researchers this week found a vulnerability with a severity rating of 9.8 out of 10, which is to say, not great. About half of the Fortune 50 use BIG-IP networking equipment, like firewalls and load balances, and there are some 16,000 devices exposed to the internet today. Vulnerable devices can be exploited with a simple bug that can allow an attacker to run remote commands on the device without needing a password. Given the ease of exploitation, it wasn't long before public proof-of-concept exploits began floating around, with some seeing threat actors dropping backdoors in the wild. CISA added the F5 bug to its list of known exploited vulnerabilities.
More: Cisco Talos | Randori | Bleeping Computer
Europe’s CSAM scanning plan unpicked
TechCrunch: The European Union this week formally presented its new proposal to combat child sexual abuse imagery (CSAM) across the 27 member states that would, among other things, obligate digital services to use automated technologies to detect and report existing or new CSAM. It's a complicated and dense read of a document and one that's already concerning a lot of privacy minded folks over fears that this could undermine end-to-end encryption. If you recall, last year Apple announced (then pulled after a mountain of criticism) a technology that would try to balance user privacy by scanning photos client-side, rather than breaking encryption. European Parliament members and the EU Council will get to weigh in before the proposal passes, but it's likely to face a battle.
More: European Commission | The Guardian | Wired ($)
Android 13 tries to make privacy and security a no-brainer
Wired ($): Android hasn't always had the best reputation with security and privacy, not least because Google collects vast amounts of data from you. With Android 13 around the corner, Google is looking to make its protective features easier to use. Wired looks at the new features on deck, including soon-to-be end-to-end encrypted group messages, better permissions controls, and better controls over which photos and videos you can share with an app (which iPhone users have long had). Better late than never.
More: Google Security Blog | 9to5Google
DEA investigating breach of law enforcement data portal
Krebs on Security: The Drug Enforcement Administration is investigating an apparent breach of its law enforcement data portal, which the U.S. federal agency uses to share and collect intelligence from over a dozen other agencies. The portal is online but protected with, allegedly, a PIV smart card, but the hackers who broke into the portal told Krebs that the portal "also appears to accept just a username and password" that were stolen and posted online, radically diminishing the portal's security controls. "DEA takes cyber security and information of intrusions seriously," said a spokesperson. Of course it does...
More: @briankrebs tweets
White House staffs up in cyber as U.S. warns of Russia, China threats
CNN: The Biden administration has hired former Microsoft executive Kemba Eneas Walden to be the "linchpin" of the White House's new cyber office, headed by Chris Inglis. Walden has been a major player in the U.S. counter-ransomware space. The CIA's Neal Higgins will also join the office, per CNN. Also this week: prominent U.S. lawmaker Mark Warner, who chairs the Senate Intelligence Committee, told the BBC's Hardtalk program that Russia's cyber operations was the "dog that hasn't barked" in the Ukraine conflict and warned cyberattacks could spill over to the U.S., fears echoed by NSA cybersecurity director Rob Joyce in a separate interview with the BBC. It's not just Russia that the U.S. is concerned about. U.S. chief spy Avril Haines said China currently presents the "broadest and most active and persistent" cyber espionage threat against the U.S.
More: BBC News | The Record | NPR
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Costa Rica's new president starts term declaring ransomware national emergency
Cyberscoop: A rough week for Costa Rica, whose new president Rodrigo Chaves Robles, who began a four-year term last week, declared a national emergency following a ransomware attack that forced the government to a halt. The threat group, known as UNC1756 (for an as-of-yet uncategorized threat group), used the Russian-based Conti platform to hack the country and steal 672 gigabytes of information. The country's finance, science and technology, telecoms and meteorological departments were all hit. Costa Rica did not pay the $10 million ransom. The hackers started publishing the country's files this week, including, somehow, information from Peru's national intelligence agency. The U.S. State Dept. put out a $10M bounty for the Conti hackers earlier this month. Local news outlet Amelia Rueda has more.
Anonymous social media app Yik Yak exposed users' locations
Motherboard: When is an anonymous social media app not so anonymous? When you're Yik Yak and exposing the precise location data of its users. Research by @david_teather this week showed how Yik Yak was bundling users' posts with granular location data (within 10-15 feet), which was viewable via the API. Yik Yak fixed the bug — kind of — with an updated app, but the bug was still exploitable using the API of older app versions.
U.S., U.K. and EU blame Russia for 'unacceptable' Viasat cyberattack
TechCrunch: The U.S., U.K. and EU have all formally blamed Russia for the cyberattack against satellite communications provider Viasat, which saw thousands of customers' modems bricked on the day that Russia invaded Ukraine, whose military heavily relies on satellite communications. The joint statements said the Russians used "destructive malware" to remotely brick the satellite base-station modems needed for talking to the sky. Worth reading @howelloneill's tweet thread for how we got here.
ICE uses data brokers to bypass surveillance restrictions, report finds
The Verge: Bad news if you have a driver's license and you hate surveillance. New investigative findings from Georgetown Law Center found that U.S. immigration agency ICE has access to the personal information of hundreds of millions of Americans by warrantlessly collecting data from commercial data brokers. The findings are eye-watering: ICE has the driver's license data of some 74% of U.S. adults and already run facial recognition scans on about one-third of those. "And when three out of four adults hooked up utilities like gas, water, and electricity in a new home, ICE was able to automatically update their new address." Yeah. Let that one sink in for a second (and props to @drewharwell for first reporting this particular factoid last year). This tweet thread by @GeorgetownCPT is also a good primer on their investigation
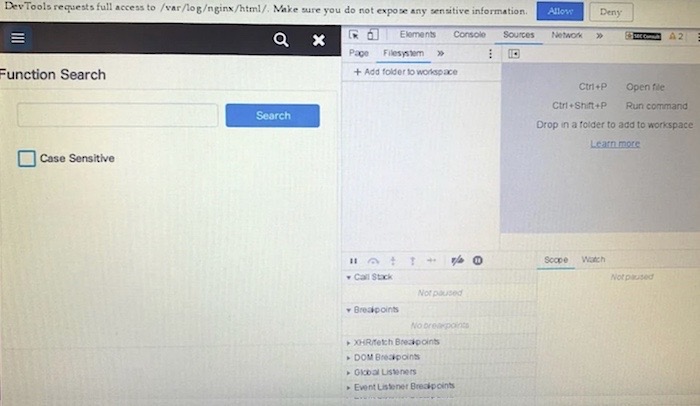
Konica printers vulnerable to hacking via F12 key
SecurityWeek: SEC Consult found three security flaws in a popular brand of Konica printers. All of the flaws required physical access to the printer, which at this point you're thinking — well it's already game over if you have physical access. But many of these printers are designed to be used in public places, like printing stores, and are run in "kiosk mode" to prevent someone tampering or changing settings. Turns out kiosk mode was basically a Chromium browser and was easily escapable by plugging in a USB keyboard and hitting the F12 key to open Chrome's developer tools.
~ ~
OTHER NEWSY NUGGETS
Illinois college closes after ransomware attack: Lincoln College, one of a handful of rural U.S. colleges that qualify as a predominantly Black institution, closed its doors Friday in part due to a ransomware attack that hampered admissions during an already difficult time due to COVID-19. The college's final commencement is today, Sunday. More than a thousand schools in the U.S. were hit by ransomware last year, of which 26 were colleges or universities.
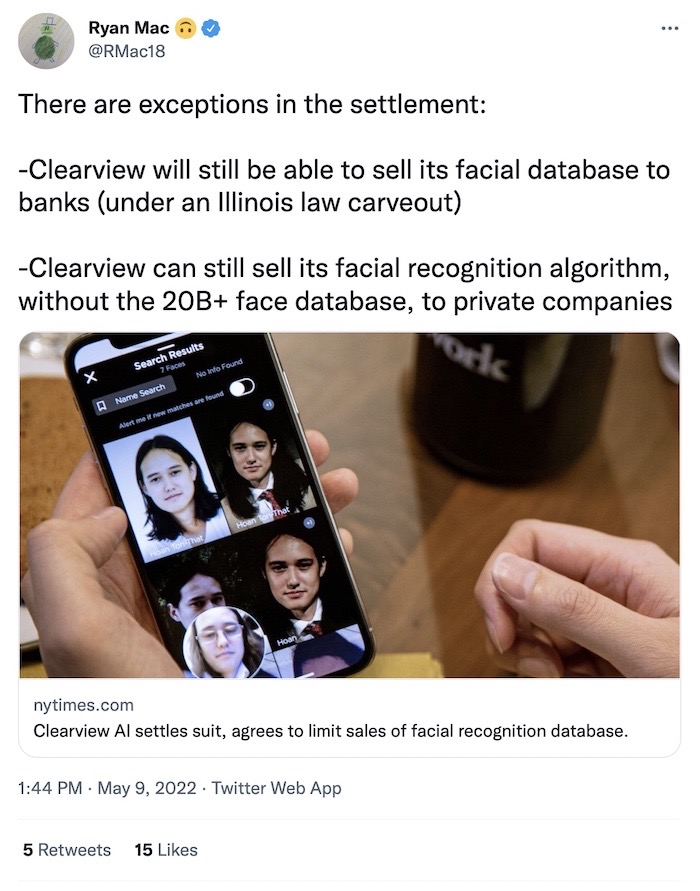
Clearview AI banned-ish from selling its database: The ACLU and others brought a case against facial recognition startup Clearview AI, which resulted this week in a settlement that will see the company banned from selling its facial recognition database of 20+ billion faceprints to private businesses and law enforcement across the United States. But there's a catch: per @rmac18, Clearview can still sell to banks, and it can also sell its algorithm but sans the faceprint database. The case was brought under Illinois' biometric laws, BIPA, which ensures Illinois residents wouldn't have their biometric data without their knowledge or consent. This is a "huge win" for privacy, at least under the current data protection regime, which is lackluster at best compared to say, the EU.
Websites see what you type before you hit 'submit': New research via Wired ($) shows thousands of the world's most popular websites are collecting some or all of your data as you type it in — before you even hit submit. While that kind of website behavior isn't new per se — customer service agents can often see what you type before you hit send — these latest findings also show how websites are also scooping up things like passwords. The full research can be found here.
Driverless cars are watching — and listening: Yet another reason why the future is terrible: Motherboard obtained documents that show police in San Francisco have used data collected from autonomous vehicles "several times" in the course of investigations. The documents show that the self-driving cars "are recording their surroundings continuously and have the potential to help with investigative leads." The EFF described this as "very concerning."
Old macOS bugs, new tricks @kjhiggins chatted with security researcher Csaba Fitzl who found three macOS flaws building off the work from older vulnerabilities, including a new bug found following a previous fix. "Although Apple fixed it properly, but still there was an extra function ... that basically opened up another vulnerability to be utilized a bit differently than the original one," Fitzl explained.
~ ~
THE HAPPY CORNER
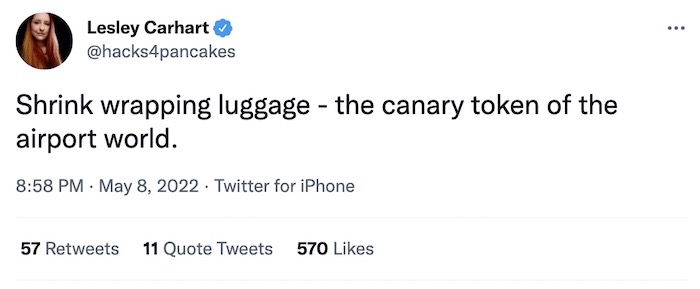
@hacks4pancakes has a great thread on shrink-wrapping luggage when you go traveling and how this is not just a space saver but a great security measure. "You shrink wrap the luggage to both deter tampering and also check to see if it has been done and potentially prove it," said Lesley. And don't forget to take a photo to check later. (I'm personally a big fan of the rolling vacuum bags since you can reuse them on the return trip.)
EFF has a quick and easy guide on how to disable (or reset) your phone's advertising ID, which makes it more difficult for websites and apps to track you. Works for both iOS and Android, though your mileage may vary depending on the software version (or device) you're using.
And @maddiestone closes out this week.
To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's cybercats are Priya (back) and Raj (front), also known as "trip hazard one" and "trip hazard two" by their human. Many thanks to Dave W. for sending them in!

Keep sending in your cyber cats — or their friends. Drop me an email here with their name and photo, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
Thanks for reading a busy week in security. As always, the suggestion box is open or feel free to drop me email me if you have any feedback. Have a great week and see you next.