this week in security — may 18 2025 edition
THIS WEEK, TL;DR
Coinbase hit by 'insider' data breach, refuses to pay hacker's ransom
Coinbase: Let's start this week with crypto giant Coinbase, which confirmed on Thursday it was breached following an insider threat, whereby support staff were bribed to hand over customers' personal information. Around 1% of the company's monthly users are affected; said to be around 80-100k people or so. Yes, even the web3 crypto-focused giants are still facing much of the Web 2.0 problems of yesteryear. Through their bribes, the hacker stole customer names, addresses, phone numbers, government-issued IDs, balance data and transaction histories — including some big name customers, such as one of Sequoia's top partners. The hacker demanded a $20 million ransom, which Coinbase said it would not pay. While no funds were directly stolen through the breach, Coinbase said it expects to incur costs of around $180 million to $400 million to cover reimbursements of its customers' lost crypto.
More: SEC 8-K | Bloomberg ($) | Reuters ($) | Dark Reading | TechCrunch
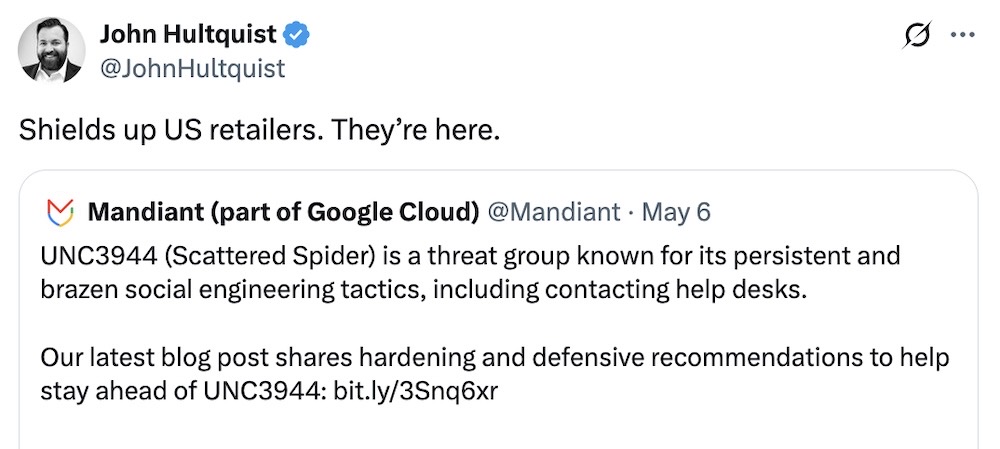
Marks & Spencer, Co-op confirm customer data stolen in cyberattacks
BBC News: U.K.-based retail giants Marks & Spencer says customer data was stolen in its recent cyberattack (said to be costing the company some $57 million a week in lost sales, plus its CEO is also taking a pay hit, per the Financial Times ($)). Store shelves are starting to recover and getting restocked, per Reuters ($). The Co-op also had a similar breach, but reportedly hit the big red button on its network before the ransomware gang could activate its server-scrambling malware. There's lots still not publicly known about the hacks, but it sounds like the two retailers are bouncing back — finally — after weeks of disruption. Meanwhile: Mandiant's top cyber sleuth @JohnHultquist warned that the same Scattered Spider tactics of socially engineering access to victim networks then handing off access to ransomware gangs are now being used to target U.S. retailers.
More: BBC News | Retail Dive | Sherwood News | @GossiTheDog posts
White House kills rule shielding Americans' private data from brokers
Wired ($): It's been [ 0 ] days hours since the U.S. government's last stuff-up... and it's all thanks to *checks notes* Russ in budgeting. Top White House official Russell Vought, the Project 2025 planner who now serves as both OMB director and acting head of the Consumer Finance Protection Bureau (you can see where this is going), said he's pulling the plug on a CFPB rule (granted, one of the final rule changes of the Biden administration) that actually would've done some good — specifically, preventing data brokers from selling Americans' personal and financial information, including Social Security numbers. Vought said in the Federal Register that the rule is "not necessary or appropriate." In short, the rule would have prevented data brokers from sharing people's private information by requiring these shady data-sellers to follow the rules of the Fair Credit Reporting Act (like credit agencies have to). It's not perfect, sure, but shy of a federal data protection law (which America still doesn't have), expect our data to keep getting sold. At least we'll know specifically who to blame when our data gets sold and stolen again.
More: Federal Register | Bloomberg Law ($) | TechCrunch | The Register | @dell
SAP zero-day bug used to compromise hundreds of servers
BankInfoSecurity: There's a new zero-day in town — two, in fact — and they're both being used to attack SAP customer servers. Onapsis has the details: The first, CVE-2025-31324, allows for unauthenticated remote code execution on NetWeaver Visual Composer servers, so this is a rare 10/10 vulnerability severity score. ReliaQuest found hackers exploiting the bug to upload webshells to affected systems, allowing for total server compromise. Meanwhile, CVE-2025-42999 is another high-severity zero-day under attack, which was found soon after the other bug. The Shadowserver Foundation said it's still tracking over 200 compromised SAP NetWeaver servers on the internet vulnerable to CVE-2025-31324, down from thousands last month, so these bugs are being exploited somewhat widely. The good news is that both bugs have been patched.
More: Bleeping Computer | SecurityWeek | The Register
~ ~
THE STUFF YOU MIGHT'VE MISSED
Rogue communication devices allegedly found in Chinese solar power inverters
Reuters ($): U.S. energy officials are said to be examining the risk posed by Chinese-made solar power inverters devices after "unexplained communication equipment" was allegedly discovered in some of them, per two sources. Reuters hasn't seen hard evidence, but claims — citing the two sources — that the undocumented communication channels can circumvent firewalls. Potentially one to watch and be aware of... but does anyone else get Bloomberg spy-chip story vibes?
VPN firm 'didn't know' customers had lifetime plans, cancels them
Ars Technica: VPNSecure has drawn ire from its customers after canceling their lifetime subscriptions, after the company's new owners said it wasn't aware of the lifetime plans when they bought the VPN provider. (Cue the sound of several facepalms all at once.) Customers are understandably furious, but worth noting that the best VPN is one you can control, operate, and encrypt yourself. (h/t Andrew Strutt, thanks for flagging!)
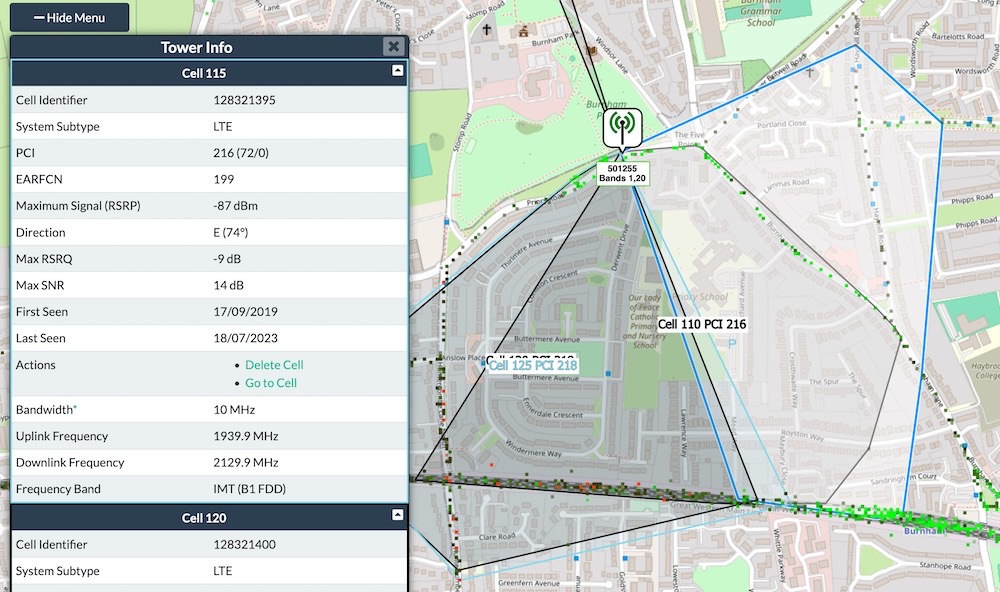
U.K. phone giant O2 leaks customer location data
Mast Database: Alarming news here from the U.K.: "Any O2 customer can be trivially located by an attacker," per David Wheatley, and there is "no way to prevent this attack." Wheatley found that the U.K. cell network's implementation of VoLTE is leaking raw cellular headers, including users' IMEI and IMSI numbers, as well as the last cell ID they were connected to. With that data, anyone can take someone's cell header data and identify roughly where they are within a cell tower's range. The issue is not fixed, as O2 doesn't have a reliable means for reporting security flaws.
TeleMessage's knock-off Signal app hacked in 20 minutes
Micah Lee: Remember that insecure Signal-clone app, developed by TeleMessage and used by Trump officials, which got hacked a few weeks back? Turns out it took the person who discovered the bugs in TeleMessage's systems about 20 minutes to find a vulnerable endpoint capable of returning a 150MB heap dump of the backend server's memory. In that memory dump were user credentials and email addresses. The full story is on Wired ($).
~ ~
~ ~
OTHER NEWSY NUGGETS
Scammers abuse government email system: At least two U.S. local governments confirmed that unknown scammers were misusing GovDelivery, an email system used by U.S. federal, state, and local governments to alert residents to news, information and emergencies. (Disclosure alert: I wrote this story!) The scammers used the email platform, maintained by govtech giant Granicus, to send "toll scam" emails that appeared to come from officials in Indiana, New Mexico, and others. Granicus said its systems weren't breached, but Indiana pointed its blame at Granicus for not disabling its accounts when its contract terminated at the end of last year. Whoops. (via TechCrunch)
CVE Foundation plans year-end launch: A last-minute reprieve for the CVE program earlier this year sparked the creation of the CVE Foundation, a new non-profit that aims to secure the future of the vulnerability reporting catalog. The foundation plans to launch by December, though not to the delight of everyone. (via Cyberscoop)
Indian health giant hacked, sent bullets: Last year, Indian health insurance giant Star Health was hacked and millions of patients' data was leaked online. Now, Reuters ($) reports that the hacker confirmed it sent bullets and death threats to the company's top executives. It's a marked escalation in the hacker's campaign, but not outside of the usual or norm for cybercriminals these days, who are increasingly relying on violence-as-a-service and so-called "wrench attacks." (via Reuters ($))
Deloitte missed Rhode Island hacker for five months: The hackers who broke into Rhode Island's benefits systems and stole citizens' data during 2024 had access for some five months before consulting giant Deloitte, which maintains the system, detected the breach. It wasn't until the hackers demanded a ransom that Deloitte became aware. Yes, this is a $67 billion revenue company, but wasn't properly monitoring its own systems. Looks like the state is readying a lawsuit following the breach of 644,000 people's data. (via Boston Globe ($), @metacurity)
Proton threatens Swiss quit over new law: A new Swiss surveillance law may see companies who operate there, like email provider Proton and others, potentially leave the country. Proton's boss Andy Yen said if the effort becomes law, "we would have no choice but to leave Switzerland." Seems fair, but probably a reminder that there are no perfect geographical safe havens, and a better time than any to remind you that there's no such thing as private email, either. (via RTS, en français)
~ ~
THE HAPPY CORNER
It's back and brighter than ever: This is the happy corner, and you've absolutely earned it this week.
First off, @kaito02 found where all the cloud storage hides out.

Move over, hooded coder stereotypes. Here's @munin on what the real Linux community looks like.
Here's your latest "admin/admin" example of how not to do security.
And finally, this week:
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Ravioli (amazing name) who can be seen here quite literally recharging after a long day of hacking. You've earned it, Ravioli. Thanks so much to Tristan for sending in!

Send in your cyber-cats (or a non-feline friend!) Drop a photo and name of your cyber-cat or friend by email, and they will be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's all there is for this week — thanks for tuning in and reading! Feel free to get in touch the usual ways if you have anything to share for next week's newsletter. It's always lovely hearing from you.
Offlining for now,
@zackwhittaker