this week in security — may 19 edition
THIS WEEK, TL;DR
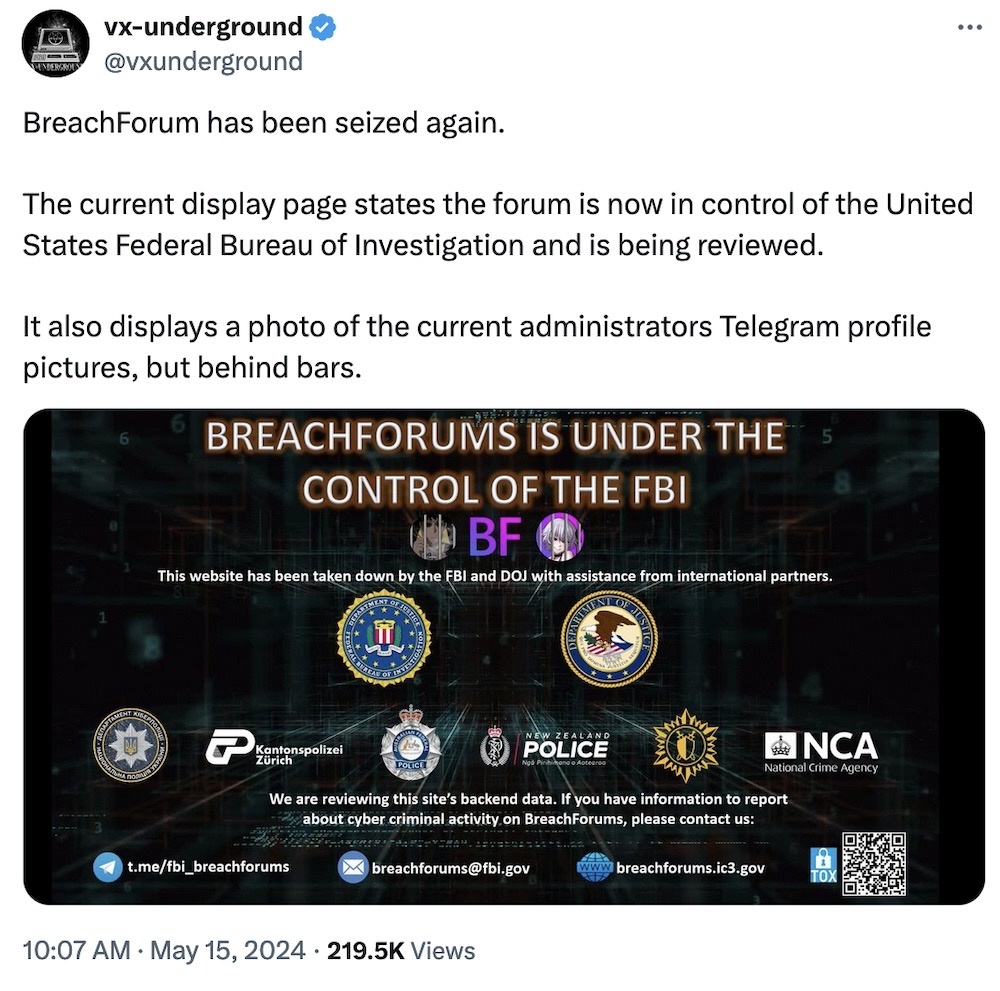
FBI seize BreachForums hacking forum used to leak stolen data
Bleeping Computer: At last, the notorious cybercrime forum BreachForums is no more... again, for a second time. Yes, the feds seized BreachForums again after arresting its administrator in 2023, but the site sprung back and the feds took another swing this week at taking down the site. The FBI also took control of the Telegram channels used by BreachForums' members to chat. BreachForums was used to "buy, sell, and trade contraband, including stolen access devices," as well as carry out identity theft and hacking tools, per the FBI's crime reporting microsite about BreachForums. But so far, the FBI has been suspiciously quiet on the second takedown, declining to comment, though not disputing its involvement with the operation. (The U.K. for its part said officials on its side were involved.) Per data breach watcher @PogoWasRight, BreachForums' second administrator, a character known as Baphomet, has been arrested. However, the second takedown operation didn't seem to go too well, since the FBI doesn't seem to be fully in control of BreachForums, which no longer displays the seizure notice but instead points to a newly created cybercrime Telegram channel.
More: DataBreaches.net | TechCrunch | Ars Technica | @ajvicens | @nixonnixoff | @pogowasright | @LawrenceAbrams
Cyber official speaks out about SS7 cell network attacks in the U.S.
404 Media ($): An official at U.S. cybersecurity agency CISA has broken with the government line and told the FCC that vulnerabilities in SS7, the protocol that routes cell communications around the world, have been repeatedly abused to track the physical location of people inside the United States. SS7 is the global protocol that routes text messages and calls around the world, but is frequently abused to gain access to the telco networks — and the major tech companies claim they're securing their networks against these kinds of attacks. The official in question, Kevin Briggs, is CISA's senior advisor for telecommunications and program lead, and wrote his comments [PDF] publicly after the FCC asked for public input on vulnerabilities within SS7 (and Diameter, a similar protocol). Briggs said the issues with SS7 are the "tip of the proverbial iceberg" of SS7-related exploits used against people in the United States. All to say, clearly there are issues with SS7 but clearly there's a wider effort to minimize the problem.
More: 404 Media ($) | The Economist ($) | @josephfcox
Microsoft's May Patch Tuesday fixes three zero-days
Bleeping Computer: And here we go with another bumper round of security updates. Microsoft fixes three zero-days, including one bug that apparently allowed the Qakbot malware (yes, the malware that never dies) to deliver phishing attacks and gaining system-level privileges on Windows devices, which Kaspersky explains in more detail. Bleeping also has a rundown of the new bug fixes from Adobe, Apple, Cisco, Google and VMware and others. Meanwhile, Apple seemingly tried to stiff one researcher out of a bug bounty payout for a macOS/iOS kernel flaw, which Apple said (after being publicly called out) that it would pay out $1,000 to the researcher for reporting in good faith.
More: Krebs On Security | Daring Fireball | @bryceabdo | @oct0xor
Three North Koreans infiltrated U.S. companies in 'staggering' telework fraud
ABC News: It's bad enough that the work market is hot garbage right now thanks to a ton of largely profitable companies laying off employees (👀). But adding insult to injury, now we've got North Korean scammers stealing U.S. jobs as part of a "staggering fraud" to generate $7 million in profit for the Kim Jong Un regime. We've heard warnings about this kind of scheme for years, but the DOJ finally nailed at least one operation, which relied on a U.S. national in Arizona stationing dozens of laptops in her residence that the North Koreans used for remote access. North Korea's regime, if you recall, is hellbent on funding its UN-sanctioned nuclear weapons program. And yet, targeting American jobs probably makes sense given how few labor laws there are here to protect U.S. workers from being exploited. North Korea could've run this operation out of Europe and its scammers would've had a far better work-life balance...
More: Wall Street Journal ($) | ABC News | @dnvolz
~ ~
THE STUFF YOU MIGHT'VE MISSED
Slack users horrified to discover messages used for AI training
Ars Technica: New AI dystopian hellscape unlocked. Now, Slack (owned by Salesforce) is training its AI model on users' data — at least, according to its terms (which have been in place since September 2023). Slack opted-in everyone to its policy, forcing organizations to email Slack directly to opt out. Ars breaks down the issue in more detail, but it's worth noting that now that so many companies are pivoting to AI (for reasons that they can't even explain or justify), any unencrypted data that a company holds is at risk of being used — and leaked — in a language model. E2EE all the things!
Jamaica's standards agency hit by cyberattack
Jamaica Gleaner ($): Local media in Jamaica is reporting that the Bureau of Standards Jamaica, the country's national standards body, was hit by a ransomware attack in February, and the bureau has spent over $231,000 (USD) so far to recover its systems. The Gleaner reports that it's the latest cyber incident to hit Jamaica since a December attack targeted the state-owned oil refinery and an earlier attack at the Financial Services Commission in September. As such, the newspaper says the latest attack "calls into question the strength of Jamaica’s cyberinfrastructure."
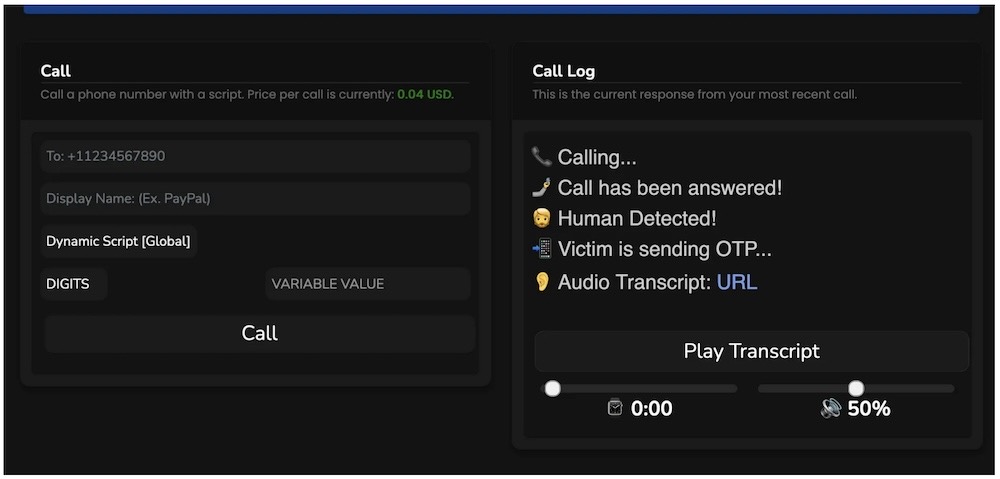
How cybercrims steal one-time passcodes for SIM swaps and raiding bank accounts
TechCrunch: This week, I looked behind the scenes of a cybercrime operation called Estate, which relies on its members tapping into the wider phone networks by abusing access to upstream providers, and tricking victims — including specific campaigns aimed at targeting older folks, aka Boomers — into handing over their one-time passcodes needed for hijacking their online accounts or draining their crypto wallets. The operation allowed its hundreds of members to make 93,000 phone calls to victims since Estate first launched in mid-2023. We know this because Estate's owner left their cybercrime operation's database leaking to the internet, with a lot of logs and information about the attacks its members carried out. (Disclosure: I wrote this story!)
U.S. intelligence spotted Chinese and Iranian deepfakes in 2020
CNN: During the closing weeks of the 2020 election campaign, U.S. officials said they saw Chinese and Iranian governments preparing fake, AI-generated content — aka deepfakes — as part of an effort to mislead voters and influence the vote. Now, some four years on and faced with another election, AI is a lot further along (visually and audibly, at least) and now U.S. officials are worried that these deepfakes will get monumentally more realistic in time for this year's go-around. It's something to keep in mind; if it looks and sounds too good to be true, it might well be.
China's spy threat is growing, but the West has struggled to keep up
BBC News: Speaking of China... the BBC's @gordoncorera has a deep-dive looking at China's espionage and spying threat and its risk to Western democracies. This is a great, inside-the-room read for understanding what China's up to — and how the Western alliance of the Five Eyes surveillance pact have been slow to react — in part because China doesn't spy like how everyone else spies.
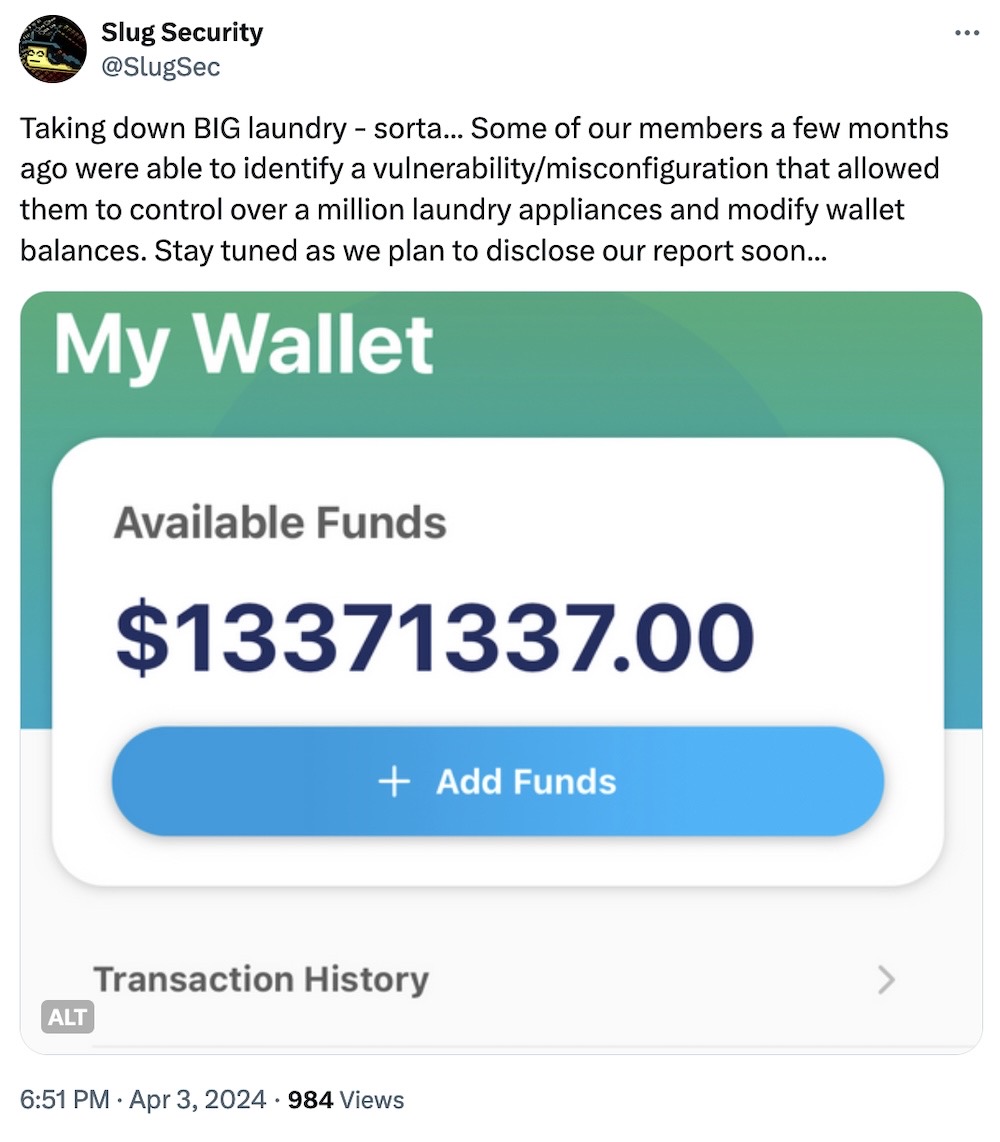
CSC ServiceWorks ignores bug that allows anyone to get free laundry
TechCrunch: Two student security researchers at UC Santa Cruz found the jackpot of security bugs — free laundry at any one of the million-plus internet-connected laundry machines operated by CSC ServiceWorks. The researchers Alexander Sherbrooke and Iakov Taranenko say any security checks are done by the CSC Go mobile app and automatically trusted by the server. Plus, thanks to CSC's published API documentation, the researchers said they could interact with any of the million machines and ostensibly top up their accounts with as much money as they want — tens of millions of dollars in one case, since the server wasn't checking anything. CSC ignored the researchers on multiple occasions, and the bugs are still active. Have fun, I guess? (Disclosure: I also wrote this, busy week!)
~ ~
OTHER NEWSY NUGGETS
New Android, new tricks: Google is bringing a slew of new security features to its upcoming Android 15 release, which includes a sprinkling of AI to detect — among other things — when your Android device has been snatched from your hands. The theft detection feature automatically locks a device's screen by looking for on-device signals that suggest foul play. Google also announced an on-device phone call eavesdropper that warns users about scams mid-call, like listening out for "transfer the money in your bank account", but that's already drawn ire from researchers who warn that on-device scanning could be expanded to dial up censorship by default. (via Google, The Verge)
Old breach, new reach: Starting in 2009, the infrastructure used to maintain and distribute the Linux operating system kernel was infected for two years by a malware that stole credentials for more than 550 system users. The infection came to light in 2011, but the maintainers reneged on a promise to publish an autopsy of the hack. Now, ESET says that the Ebury malware used in the hack has since infected around 400,000 Linux servers over the past 15-or-so years. ESET said the Ebury operators "were able to gain full access to large servers of ISPs and well-known hosting providers." Ouch. Wild reporting here. (via Ars Technica, ESET)
Major data breach hits Helsinki: The Finnish capital said it's unsure who carried out a data breach on its educational and training departments, but said the stolen data includes information on 80,000 school students and their guardians. The breach also included information on around 38,000 city employees, and amounted to tens of millions of documents. Helsinki's chief digital officer said the criminals broke in by way of a known vulnerability, which was not patched in time. (via Yle)
Australia confirms prescription hack: The Australian government said it's warning of a "large-scale ransomware data breach" following a cyberattack targeting prescription company MediSecure (what a terrible name for a company) that affected the "personal and health information of individuals." A bare bones statement on MediSecure's website said it blamed an unspecified third-party vendor. MediSecure apparently handled 143 million digital scripts between 2020 and 2023. The breach comes two years after Australian health insurance giant Medibank confirmed millions of Australians had healthcare-related information stolen, including information about drug addiction and reproductive health. Again, maybe having all these huge private companies storing gobs of sensitive data isn't the smartest idea after all? (via The Record, AFR ($))
Dell notifies EU authorities of data breach: Remember last week when a threat actor scraped nearly 50 million Dell customer records, including physical addresses, as well as email addresses and phone numbers? Now, Dell has confirmed it notified Ireland's data protection authority — as the data includes information on EU residents — which puts the technology giant potentially in line for a fine of up to 4% of its global annual revenue for any violations of GDPR. (via TechCrunch)
~ ~
THE HAPPY CORNER
And that's the news done with, here's the happy corner.
The reporters who were invited to the U.K.'s National Cyber Security Centre this week for a speech were sent a door entry code, which, well, wasn't exactly great. But at least we can laugh — right? Right?
![Jason Groves tweet: "[Journalists] arriving at the National Cybersecurity Centre for David Cameron’s [speech] are informed that the security code for the doors is 1234"](https://this.weekinsecurity.com/content/images/scraped_images/5919b075-a1b5-7182-057a-8d060e9c2a1f.jpeg)
Meanwhile, a cat on your desk is the new "dog ate my homework." Update your workplace-related excuses accordingly.

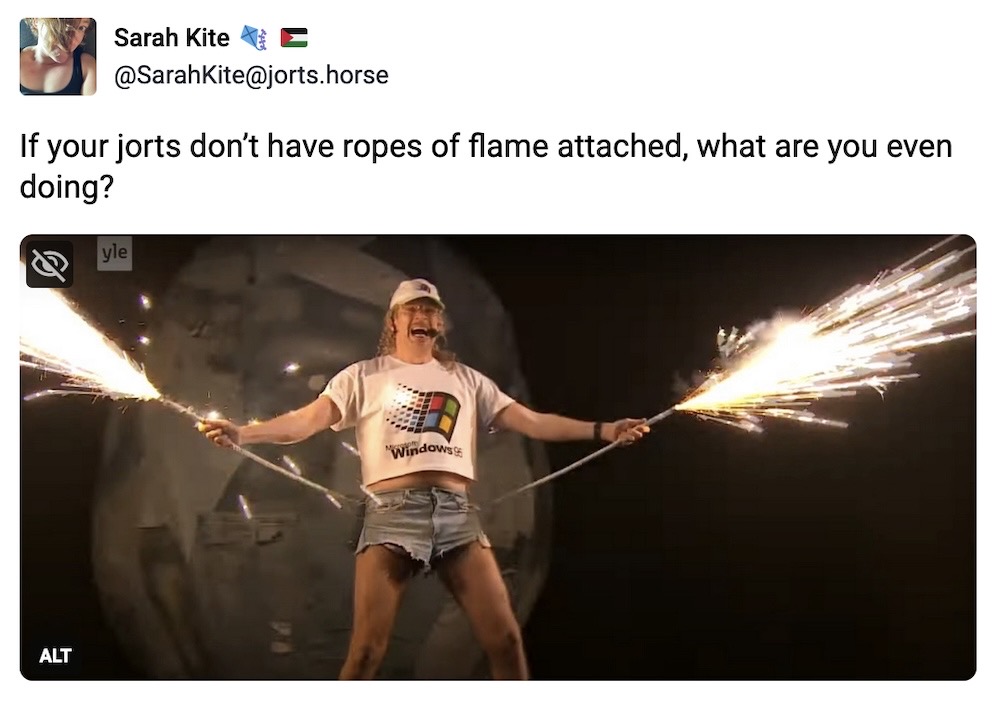
And finally in this edition. A special shout out to Finland's Eurovision entry, Windows95Man, a 38-year-old Finnish DJ and early computing enthusiast, whose performance on stage this week started with him emerging from a giant denim egg wearing a T-shirt with a blurred Windows 95 logo, and ended with him dancing around on stage Pooh bear-style followed by a dance wearing jorts with attached rope-flames. Why a shoutout, you ask? Why not? Windows95Man, we stan.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
~ ~
CYBER CATS & FRIENDS
This week's two-for-one cyber cat special features Bartholomeow (in the front) and Captain Toothpaste (back), who can be seen lounging around while their human cybers. Many thanks to Jeff G. for sending in!

Send in your cyber cats! Feel free to drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
And that's it for this very busy edition of ~this week in security~. Join me next week for the usual round-up from the last few days in cybersecurity, and more.
As always, feel free to drop me an email any time with any feedback (and cybercats).
Back next,
@zackwhittaker