this week in security — may 21 edition
THIS WEEK, TL;DR
DOJ charges Russian with ransomware attacks against critical infrastructure
Justice Department: The DOJ charged Russian national Mikhail Pavlovich Matveev, aka Wazawaka, with launching ransomware attacks against U.S. targets, including police departments and hospitals. Prosecutors say Matveev allegedly participated in conspiracies to deploy three ransomware variants, including LockBit, Babuk, and Hive. So not by any means a small fish, but since Matveev is still in Russia, the DOJ has a way to go before they can nab their guy. By offering a $10 million bounty for information, the U.S. hopes this might help grease the wheels of justice. The Treasury also sanctioned Matveev, meaning folks in the U.S. cannot transact with Matveev — think ransom payments! The Record has an interesting interview with the FBI's Bryan Smith on how it infiltrated and took down Hive, one of the variants in question, but not without siphoning off all of its encryption keys first.
More: FBI wanted posted [PDF] | SecurityWeek | TechCrunch | CNN | KrebsonSecurity

Ransomware gang steals data of 5.8 million PharMerica patients
Bleeping Computer: Speaking of ransomware... one of the biggest health breaches of the year happened and almost nobody noticed. PharMerica, a huge pharmacy service operating across the U.S., was hit by the Money Message ransomware gang in March, stealing the full names, addresses, Social Security numbers and protected health information of 5.8 million patients. Worse, the gang has started publishing the stolen data. Money Message is also accused of hacking Taiwanese computer parts maker MSI, which resulted in its non-revocable UEFI signing keys leaking to the internet.
More: PharMerica | HIPAA Journal | The Register
FTC says fertility app Premom gave advertisers pregnancy data without permission
Cyberscoop: Another week, another health app sharing gobs of personal data with advertisers, and two data analytics firms in China accused of "suspect data practices." That's exactly what happened with Premom, which the FTC has now slapped with a $100,000 civil penalty and ordered to stop sharing data with advertisers. All this came after 2020 reporting by the Washington Post ($). Of course, the data is already in advertisers' hands and there's no legal obligation for them to delete the data. (Companies: don't collect the data to begin with!) Premom is the latest app to face FTC action. (Dare I say, the FTC is on a roll of late.) In a deflective and non-apologetic statement, Premom went on the defensive instead of saying what it'll actually do to stop sharing its users' data.
Archive: Washington Post ($) | More: FTC | Fierce Healthcare
Montana becomes first U.S. state to ban TikTok
The Guardian: OK, now we have to talk about that stupid ban on TikTok, because somehow that news now. Montana became the first U.S. state to ban the app — starting January 2024 — because of its links to China. The ban prohibits app stores from offering the TikTok app in the state. How tech companies will comply with that is anybody's guess, since the chances of the law being overturned is... well, greater than zero, but who knows given the Supreme Court these days. Also — sorry, forgot to mention — it's a huge and clear violation of the First Amendment, and is expected to become a legal battleground since banning apps (like books) infringes on the constitution's fundamental rights to free expression. What kind of country bans apps? Oh yeah, China — the irony.
More: NBC News | Associated Press | BBC News
FBI misused foreign spy database for 278,000 searches
Wall Street Journal ($): The FBI improperly searched a U.S. government database gathered through its foreign spying law, FISA, for information related to the January 6 coup-attempt and... George Floyd protests, according to a blistering (albeit heavily redacted) opinion by the FISA Court, which oversees the government's use of surveillance powers. FISA is meant to require a warrant before the feds can access incidentally collected data on Americans. But that didn't happen in thousands of cases where there was no apparent nexus to foreign involvement. It's not clear in some cases even why protests were examined in this way, per the Journal. Floyd, a Black man, was killed by a white Minneapolis police officer who knelt on his neck during a callout. FISA is up for renewal this year, and it's anybody's guess how this will change the result — given this is a rare moment of bipartisan agreement. Note the recent Wyden siren: "There is important, secret information about how the government has interpreted Section 702 that Congress and the American people need to see before the law is renewed." 👀
More: Reuters ($) | Sen. Ron Wyden | @dustinvolz toots
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
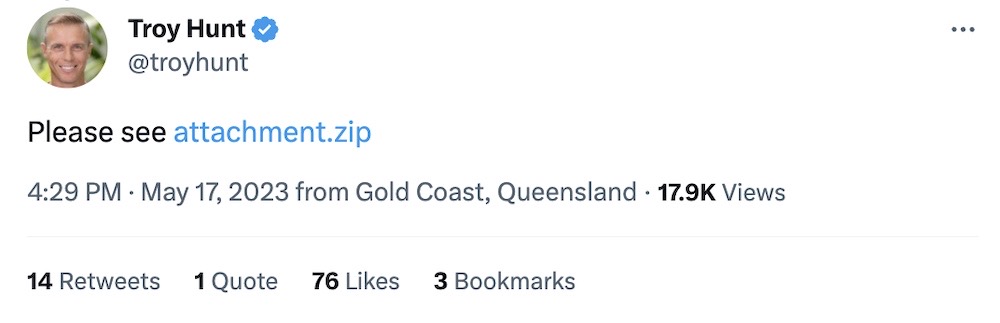
Bitbucket cloud SSH keys changed after breach
Bitbucket: Private code hosting giant Bitbucket confirmed its SSH keys will rotate on June 20 after encrypted copies of its SSH host keys were "included in a data breach of a third-party credential management vendor." I can only imagine what company this must relate to, but the only third-party credential manager I can think of that was hit in recent months is LastPass. Plan accordingly!
Free smart TV startup Telly's privacy policy is a hot mess
Shoshana Wodinsky: @swodinsky brought light to the privacy policy of Telly, a free smart TV startup whose constantly running ads on a separate television "bar" allegedly pays for itself. As you can imagine, it's a huge data collection effort to subsidize its hardware. The startup told me (disclosure alert!) that it had published a draft of its policy by mistake, which left in the startup's notes things like, "Do we have to say we will delete the information or is there another way around this" regarding... children's data.
Google pushes .zip and .mov domains onto the Internet, and the Internet pushes back
Ars Technica: Google's new top-level domains, .zip and .mov, get the @dangoodin treatment: a deep dive into the pros and cons of offering these new domains. There's considerable (and understandable!) concerns that these TLDs could enable malicious links. Truly worth the read. It looks like phishing attacks are already taking advantage of the new TLDs, with Netcraft noting several uses of .zip domains used as phishing lures. Sure, attachment.zip seems fine now, but the potential for abuse is pretty clear.
Bypass macOS defenses with new Telegram bug
Dan Revah: A new vulnerability discovered in Telegram can allow access to a macOS camera and microphone, sidestepping macOS protections that are supposed to prevent unauthorized access. @danrevah explains more about the bug in a blog post and @mattjay has a good tweet thread. Although this is a local privilege escalation bug and requires an attacker to have previously obtained initial access to the device, Telegram has not fixed the bug. Another reason to throw it out in favor of Signal.
Wemo has no plans to patch smart plug bug
Sternum: Wemo smart plugs are wildly popular internet-connected plugs that you can remotely control from your phone. But @0xamit and colleague Reuven Yakar tore the device apart (literally) and found it has a command injection vulnerability (CVE-2023-27217) that Belkin, which makes the smart plug, will not fix. Despite its wide popularity, Belkin said the device was at the end of its life and therefore won't receive updates.
~ ~
OTHER NEWSY NUGGETS
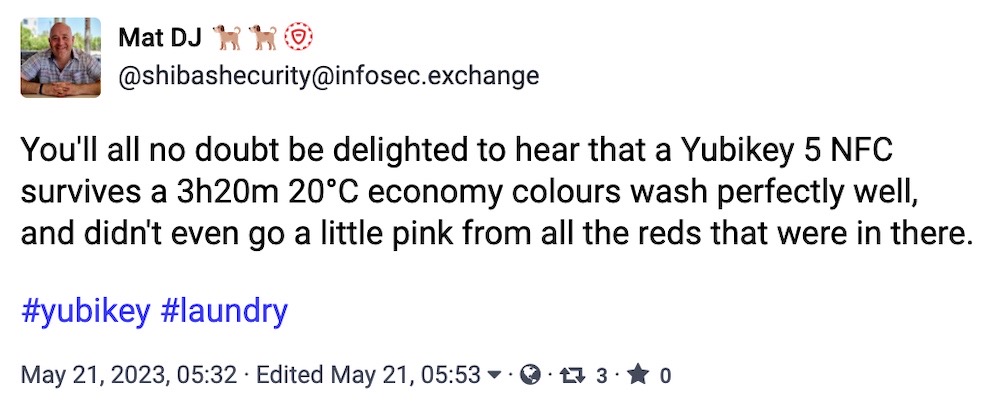
KeePass bug can recover (most of) the master password: A vulnerability (CVE-2023-32784) in how local password manager KeePass handles user input means that it's possible for an intruder — such as malware on the host computer — to obtain a near-complete copy of the user's master password, bar a digit or two, according to new research. A bug fix is likely out in June; though, KeePass 1.X, KeePassXC, and Strongbox don't seem to be affected. Not ideal by any means, but certainly worth noting. (via Bleeping Computer, @GossiTheDog)

Apple rolls out iOS, macOS updates to fix WebKit zero-day: Update your Apple devices: iOS, iPadOS, and macOS all got updates this week fixing a bunch of flaws (and packing in new features), including two WebKit vulnerabilities that were actively exploited. Apple confirmed it rolled out these fixes first through its Rapid Security Response program, which pushes out urgent security patches to help block active cyberattacks, like spyware. (via Ars Technica, @zackwhittaker)
Cybercrims actually Russian government hackers? Security researchers at BlackBerry say they believe the cybercrime group, known as Cuba Ransomware, which was previously linked to a remote access trojan known as RomCom RAT, isn't actually a cybercrime group at all — they're likely Russian government hackers, and they've recently been targeting Ukrainian military units and local governments. BlackBerry laid out its reasoning; though other researchers aren't yet making that attribution. (via TechCrunch)
Potentially millions of Android TVs and phones packed with malware: Low-cost Android devices — including phones and television set-top boxes — are laced with malware. Trend Micro says that cheap Android phones contain malware in the firmware that can steal data and ad-fraud. A similar thing with cheap Android TV devices that are sold on Amazon (and Amazon has no plans to remove — why would it when it makes money off the sale of these things?). These cheap TV boxes are part of an ad-fraud botnet, but could be used to launch DDoS attacks, according to the EFF and security researcher Daniel Milisic. (via Trend Micro, EFF)
Kiddoware app with 5M downloads has many bugs: Another day, another massively vulnerable "parental control" app (read surreptitious tracking) that's vulnerable to several security flaws. The worst flaws can retrieve MD5-hashed passwords (very bad) and information disclosure, such as the ability to read a tracked person's browser history. (via SEC Consult)
Golden Chickens malware dealer unmasked: The supplier of a notorious Russian malware called Golden Chickens, believed to have caused over $1 billion in damages, had his identity doxed. eSentire claims it knows who this dealer is — though it declined to publish his name or unmasked photos — but provided the information to U.S. law enforcement. (via Forbes ($))

~ ~
THE HAPPY CORNER
And breathe. That's the news.
The U.S. Department of Transportation named the Illinois Institute of Technology as the recipient of $10 million in federal grants to help secure ships, trains, trucks and cars from hackers and cyberattacks. The idea is to help increasingly internet-connected cars from cybersecurity threats, including trying to identify GPS spoofing and jamming.
For the younger folks in the crowd: ever wondered where the Streisand effect got its name? The Streisand effect is, essentially, when someone tries to hide something and inadvertently brings more attention to it. And yes, we're talking about Barbra Streisand and her efforts to get photos of her beachfront house taken off of the internet — with hilarious consequences. And as usual, Techdirt's @mmasnick has your explainer. Happy 20 years to the Streisand effect!
And finally, this week. Don't try this at home... but also, good to know? (For the Americans, that's 68°F in freedom units.)
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Imagine this. You just got home after a busy day at work, and you catch these two hacker cats in your house. What do you do? You give them treats, because they're this week's cyber cats, Puffin (left) and Bella (right), and they just won your heart (and their red team exercise). Many thanks to Khelsey S. for sending in!

Please keep sending in your cyber cats! Send in a photo and their name, and they'll be featured in an upcoming newsletter. (Cyber cats and their non-feline friends are welcome!)
~ ~
SUGGESTION BOX
And that's it for now — thanks as always for reading! If you have any feedback, please let me know. Have a wonderful week.
Enjoy your week, and see you next,
—@zackwhittaker