this week in security — may 22 edition
THIS WEEK, TL;DR
Costa Rica 'at war' after Conti called for government's overthrow
BBC News: Costa Rica's new president said this week that the country was "at war" with the Conti ransomware group after an attack hobbled over two-dozen government agencies, including the country's treasury, meaning civil servants won't get paid on time. Adding to that, the Russia-linked ransomware group called on Costa Ricans to "go out on the street and demand payment," adding that it is "determined to overthrow the government by means of a cyber attack." That's a major escalation from a ransomware group, but one that experts are concerned about hitting smaller governments. After making the $20M and overthrow demands, Conti allegedly shut down this week. But Conti's demand stands: the country has until May 23 to pay up or have its decryption keys deleted.
More: Motherboard | TechCrunch | Washington Post ($) | @brettcallow | @struppigel
'Multi-tasking doctor' was mastermind behind Thanos ransomware builder, DOJ says
The Record: A French-Venezuelan doctor was moonlighting as a ransomware creator, according to the DOJ, which charged against 55-year-old Moises Luis Zagala Gonzalez for designing the Thanos ransomware builder tool, which gave cybercriminals the ability to launch their own ransomware attacks. The DOJ said that the doctor even bragged about how an Iran-backed threat group known as MuddyWater used his tools, the indictment said. The "name and shame" indictment was filed in absentia since the doctor remains in Venezuela and likely won't be traveling to the U.S. any time soon. The indictment has a ton more details, including how the Thanos tool looked and worked.
More: Justice Department | Reuters ($)
Spyware vendors target Android with zero-day exploits
Wired ($): We all know that iPhones get malware, specifically zero-click spyware that Apple has tried to combat. But spyware makers aren't just targeting iPhones, as new research from Google's Threat Analysis Group this week shows that Android users are also a major target. Cytrox, a North Macedonian spyware maker known for making the Predator spyware that's targeted politicians and journalists in the past, exploited at least five zero-day vulnerabilities in Android to spy on their victims. In one case Cytrox is believed to have created a full bean-to-cup attack chain that could compromise fully up-to-date Samsung phones. @jsrailton makes an important point that NSO is just one of many spyware makers out there: "We can’t lose sight of the fact that NSO Group or any one of these vendors is just one piece of a broader ecosystem."
More: Google TAG | @lilyhnewman | @shanehuntley
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
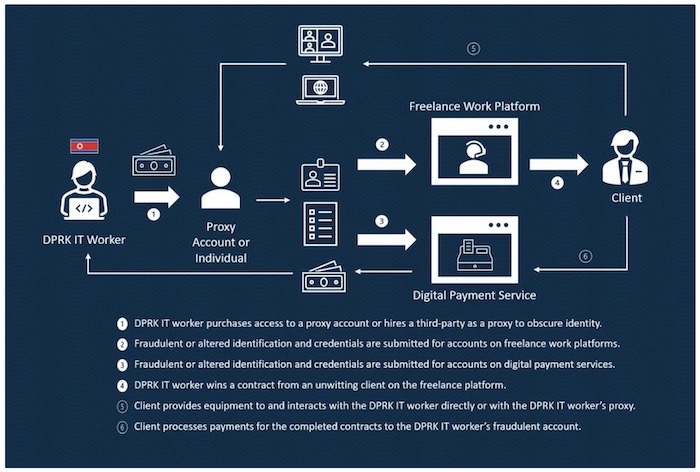
U.S. warns over risk of hiring North Korea IT workers
BBC News: The U.S. government has warned that IT workers from North Korea are trying to get remote, freelance jobs by hiding their real identities. Their aim is to get jobs, gain access, and steal money that the isolated regime uses to fund its nuclear weapons program. According to the U.S. joint report, the North Koreans have "used the privileged access gained as contractors to enable the DPRK's malicious cyber intrusions." The North Koreans use stolen or forged documents to trick their would-be employees. The Treasury has a full report [PDF] out.
When your smart ID card reader comes with malware
Krebs on Security: Millions of U.S. government employees and contractors have to use personal identity verification (PIV) readers to log onto their systems. But many employees aren't issued a card reader, prompting many to turn to low-cost readers that they find online. There's just one problem: one popular brand of smart card reader is made by Saicoo with over 11,000 mostly positive listings. But the drivers needed for the reader, according to an analysis, contain the Ramnit trojan. Saicoo denied that there was a problem, which is in itself... is a problem.
Personal information of 1.8M Texans exposed for 3 years
Texas Tribune: A bug in the website of the Texas Department of Insurance, a government agency that oversees the insurance industry in the state, exposed close to three years worth of insurance claims to the internet. The bug was discovered last year as part of a scheduled audit. In total, some 1.8 million Texans had information exposed, according to the state, including addresses, dates of birth, phone numbers, information about workers' injury, and Social Security numbers.
~ ~
OTHER NEWSY NUGGETS
ICE contractor Trust Stamp exposed dozens of people's data: Trust Stamp, a facial recognition company with a $7.2 million contract with U.S. immigration authority ICE, exposed the private data of dozens of people because credentials used for prospective clients to test the company's system were posted publicly. The data didn't appear to expose migrants' data, and some of the data contained test data. But of the dozens of people's information exposed, that included driver's license data, dates of birth and home addresses — details that Insider independently verified as accurate. Starting to lose count of how many U.S. government contractors have exposed people's data over the years...
Water companies are increasingly uninsurable due to ransomware: Even though the water supply is considered critical infrastructure, most water companies are municipal and are owned by the private sector. But the massive underinvestment in cybersecurity means more water companies are increasingly uninsurable against ransomware because insurers require more stringent cybersecurity requirements.
~ ~
THE HAPPY CORNER
Just one bit of good news this week: The U.S. Justice Department said it has a new policy for prosecuting cases under U.S. computer hacking laws, which directs that good-faith security researchers "should not be charged." This is a pretty monumental shift for the DOJ, which comes a year after the Computer Fraud and Abuse Act (CFAA), the law which prosecutes unauthorized access to a computer system, was challenged and limited by the Supreme Court. The DOJ's policy change is geared towards not prosecuting research that helps get systems fixed, while still allowing prosecutors to charge malicious hackers who try to extort owners. Clearly a big difference, but the law doesn't really differentiate between the two.
It's a good start, but a policy that could change again in the future, nor does it do anything to stop state-level prosecutions or stop civil charges from being brought. Still, better late than never. Ask your lawmaker to reform CFAA for the better!
To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Milly, who recently crossed over the rainbow bridge after a very happy 16 years with her humans. Those nine lives served her well: once a cyber cat, forever a security sensei. Many thanks to M. for the submission.

Send in your cyber-cats or their friends! Drop me an email here with their name and photo, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
A shorter than usual newsletter this week... it was surprisingly quiet by my read. Thanks for reading! As always, the suggestion box is open or feel free to drop me email me if you have any feedback. More next week as usual.
Bye for now.
—@zackwhittaker