this week in security — may 25 2025 edition
THIS WEEK, TL;DR
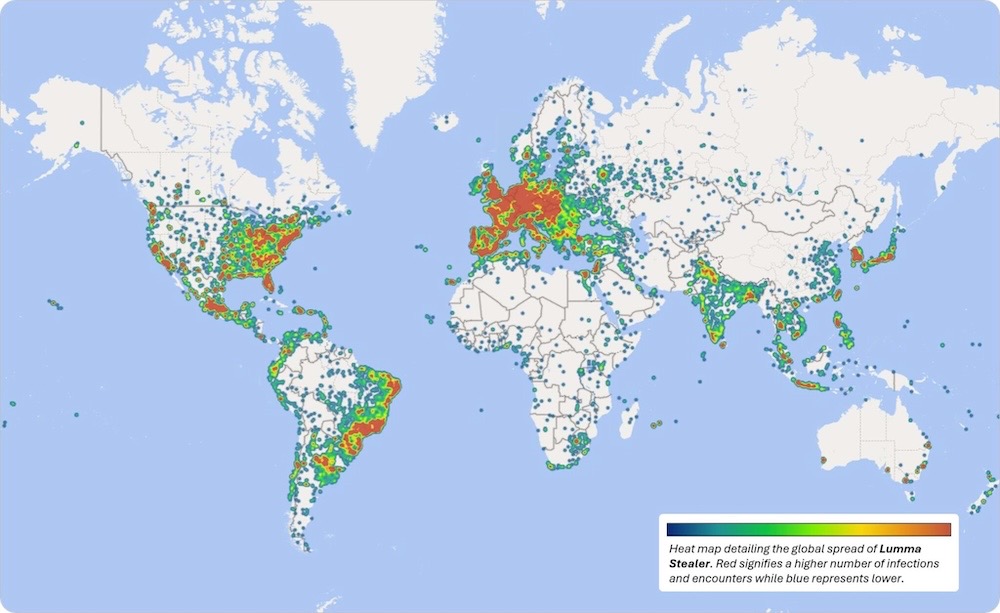
Feds disrupt Lumma malware, charge Qakbot and Danabot developers
Justice Department: The Department of Justice had a busy week taking on the cybercriminal world, disrupting the prolific Lumma password-stealing malware with the help of ESET and Microsoft, which seized domains to hamper the operation. Over a two month window alone, Microsoft found over 394,000 Lumma infections on Windows PCs, showing the scale of the malware. Then, a day later, the feds charged the developers of Qakbot and Databot, who are accused of hacking thousands of computers worldwide to facilitate fraud and ransomware. The Qakbot and Danabot charges and takedowns were part of the second wave of Operation Endgame, an international police operation aimed at taking down the cybercrime-as-a-service ecosystem. Proofpoint (via @selenalarson) digs into how Danabot rose to become a major botnet. Per Have I Been Pwned, some 15 million email addresses and over 43 million passwords were seized as part of the Qakbot and Danabot takedowns.
More: Europol | Microsoft | ESET | Bloomberg ($) | Cyberscoop | BankInfoSecurity
Massachusetts student to plead guilty to PowerSchool hack
NBC News: Sticking with the feds for a hot second (I said it was busy one!) as prosecutors have charged and obtained a guilty plea agreement from Matthew Lane, 19, who is accused of being behind the largest education data breach in recent years, PowerSchool, which was hacked late last year and held to ransom. New details emerged with the plea agreement, including that the hacker demanded some $2.85 million in bitcoin from the company to delete the 60 million students' and 10 million teachers' data. PowerSchool paid the ransom, and... of course, the hacker didn't delete the data, as evidenced by directly extorting schools directly as recently as only a few weeks ago. As a refresher, Lane is accused of using a single stolen credential to access PowerSchool's backend of student data, because the company wasn't using multi-factor authentication.
More: Justice Department | Plea agreement (DocumentCloud) | TechCrunch | WRAL
Ransomware hits U.K. food supplier as retailer hack fallout lingers
The Record: Another U.K. company was hit by ransomware this week, logistics company Peter Green Chilled, which provides refrigerated and chilled goods to U.K. supermarkets and grocery stores. This comes not so long after Marks & Spencer and the Co-op had ransomware attacks and data breaches. (Ransomware targeting the food and agriculture industry have already doubled over the past year.) Unsurprisingly, the hack on Peter Green Chilled is having its own downstream effect: Lots of food and products without any details of where to go, potentially with massive amounts of food going to waste, per the BBC. Meanwhile: the knock-on effect from M&S' hack will see the company lose some £300m (~$406m) in profit, with some disruption expected until July. It's not like years of successive U.K. governments haven't had plenty of opportunity to do something — anything — about the ransomware problem...
More: BBC News | The Register | The Guardian
~ ~
THE STUFF YOU MIGHT'VE MISSED
British Legal Aid Agency hacked; stolen data may span years
U.K. Government: Staying with the U.K. for a moment, the U.K.'s Legal Aid Agency was hacked, per a government notice. The breach exposed sensitive data (including names, addresses, criminal history, financial information, and more) on individuals who sought legal aid under U.K. law. Some of the stolen data goes back to 2010. (Why that amount of data was held for so long is beyond belief...) The data includes survivors of domestic violence, family cases, and more, and may include as many as two million pieces of data.
Coinbase breach affects over 69,000 individuals
TechCrunch: The crypto giant, which last week revealed it had been compromised by an insider threat, said in a filing with Maine's attorney general that the breach affects at least 69,461 people. The company also confirmed the breach dates back to late December, which presumably would've been ample time to detect the data theft... (Disclosure alert: I wrote this story!) Seems like Binance and Kraken were also targeted by a similar insider thread scheme, but both firms reportedly fended off the attacks without losing data, per Bloomberg ($).
TeleMessage hacker took data from across U.S. government
Reuters ($): One of the hackers (yes, remember, there was more than one!) who stole data from TeleMessage, the company that created an Signal clone with archivable messages for government customers, took messages on a "broader swathe" of American officials than previously known. Reuters identified more than 60 unique government users in the cache of leaked data, which was made available to reporters and researchers by the good folks at DDoSecrets.
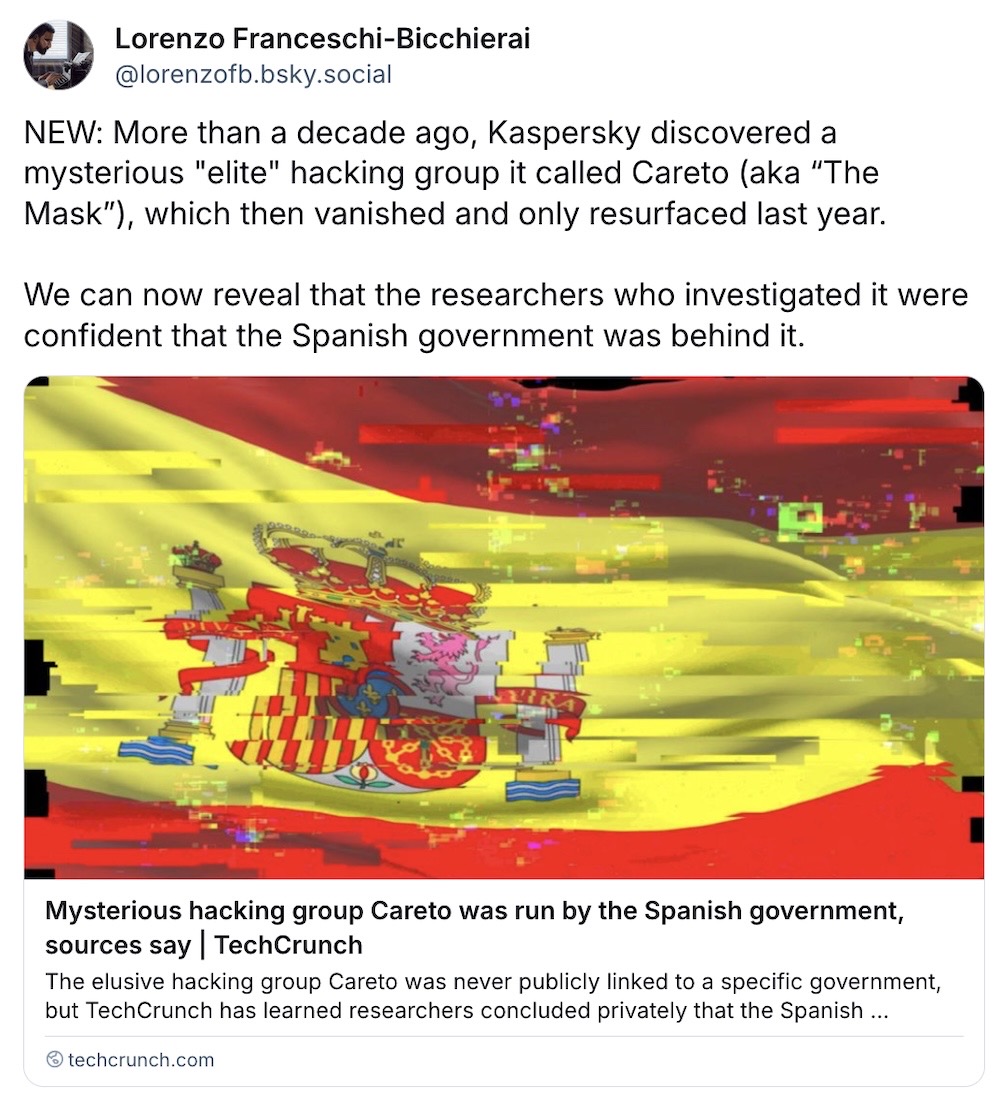
'Careto' hacking group was run by the Spanish government, per sources
TechCrunch: A mysterious hacking group dubbed 'Careto' (aka The Mask) discovered more than a decade ago was once described as the "most advanced threats" of its time, using stealthy spyware to steal data from a handful of governments. It was never publicly disclosed who was behind the hacking group, but Kaspersky researchers who discovered the attacks were convinced that Careto was run by the Spanish government. My TechCrunch colleague @lorenzofb has the inside scoop.
Police secretly monitored New Orleans with facial recognition cameras
Washington Post ($): Incredibly good reporting here: For two years, police in New Orleans secretly relied on facial recognition to scan city streets for suspects, despite municipal rules limiting the technology's use. "Police at times arrested suspects based on AI matches without independent evidence connecting them to the crime, raising the chances of a false arrest." The fact that this was happening in secret is truly horrifying. Also: Police in the U.K. are using facial recognition more and more, some 4.7 million faces scanned in 2024, suggesting that these cameras may soon be "commonplace," per one police force in the country. That's despite the fact that the tech has long been panned for its inability to properly detect darker skin tones.
~ ~
~ ~
OTHER NEWSY NUGGETS
Cuts clobbering CISA's defenses against China attacks: A senior U.S. National Security Council official wants the U.S. to fight back against China's aggressive pre-positioning of its hacking capabilities, such as U.S. critical infrastructure, likely to strike in the event of China invading Taiwan. The only trouble is that with sweeping cuts affecting CISA and other facets of U.S. cybersecurity, we might not have anyone left to defend against inevitable Chinese retaliation... security experts speaking to the Post said that the U.S. wasn't even well-defended right now... (via Washington Post ($))
Senators not alerted to surveillance demands: Sen. Ron Wyden, one of the few (only?) lawmakers in town focused on cyber, privacy, and national security, sounded the alarm among his own colleagues, after disclosing that phone giants, including AT&T, Verizon, and T-Mobile failed to develop systems for notifying lawmakers and their staff about government surveillance requests targeting Senate-owned devices... you know, surveillance requests from The White House. Despite having provisions in their Senate contracts, the phone giants never bothered to actually build the system they were required to. (via Politico ($), Ron Wyden)

Insider threat sees government contractor breached: Thoma Bravo-owned Opexus provides software for processing U.S. government records for nearly every agency, but was breached in February by two now-former employees who were previously convicted of hacking into the State Department, per reporting by the incredible @jasonleopold. The insider threat attack saw the two employees improperly access sensitive documents and compromise or delete dozens of databases from federal departments, including FOIA requests. (via Bloomberg ($))
Here's HOPE'ing for ticket sales: Hacker conference HOPE says it's expecting far fewer people at its event in New York this year following the Trump administration's border and immigration crackdown. The long-running conference says ticket sales are about 50% behind. Curious to see how the ongoing ICE raids and border detentions will affect international (and even domestic) Black Hat and Def Con attendance later this year... (via 404 Media ($))
UAE scouting for DOGE-displaced U.S. talent: A top United Arab Emirates military officer was allowed to reach out to departing staff of the Pentagon's Defense Digital Service to work on AI for the kingdom's armed forces. The recruitment effort comes in the wake of DOGE's cuts, but also a year after U.S. intelligence warned of UAE's ongoing ties to China. Let's also not forget, uhh, DarkMatter, an ostensible UAE cyber firm that developed spy tools for the Emiratis. (via Kim Zetter)
184 million logins exposed in data breach... breach: It's bad enough when infostealers and other malware steals passwords and creds from their victims' devices, but it's even worse when you leave those banks of stolen credentials in an exposed, internet-connected database with... ironically... no password. That's what happened when 184 million logins were found spilling to the web, including for some of the world's biggest tech platforms. (via Wired ($), Website Planet)
~ ~
THE HAPPY CORNER
The weather is warm... the sun is out... the birds are chirping. It's a good day to visit the happy corner.
Microsoft looks hellbent on rolling out Recall, its technology that constantly screenshots its users' screens, but seems like the smart folks at Signal aren't going to let Recall read Signal messages. There's more details from Signal's blog on how it's blocking access to the feature, and a little extra from @pwnallthethings on how to implement your own Recall screenshot-blocking feature.
Three words: parrot traffic cam.
It's that time of year again where folks are donating to send Women in Security and Privacy (WISP) scholars to DEF CON this August. If you can donate, please consider! It's more important than ever to get the most talented folks working in cyber, at a time when they are needed the most.
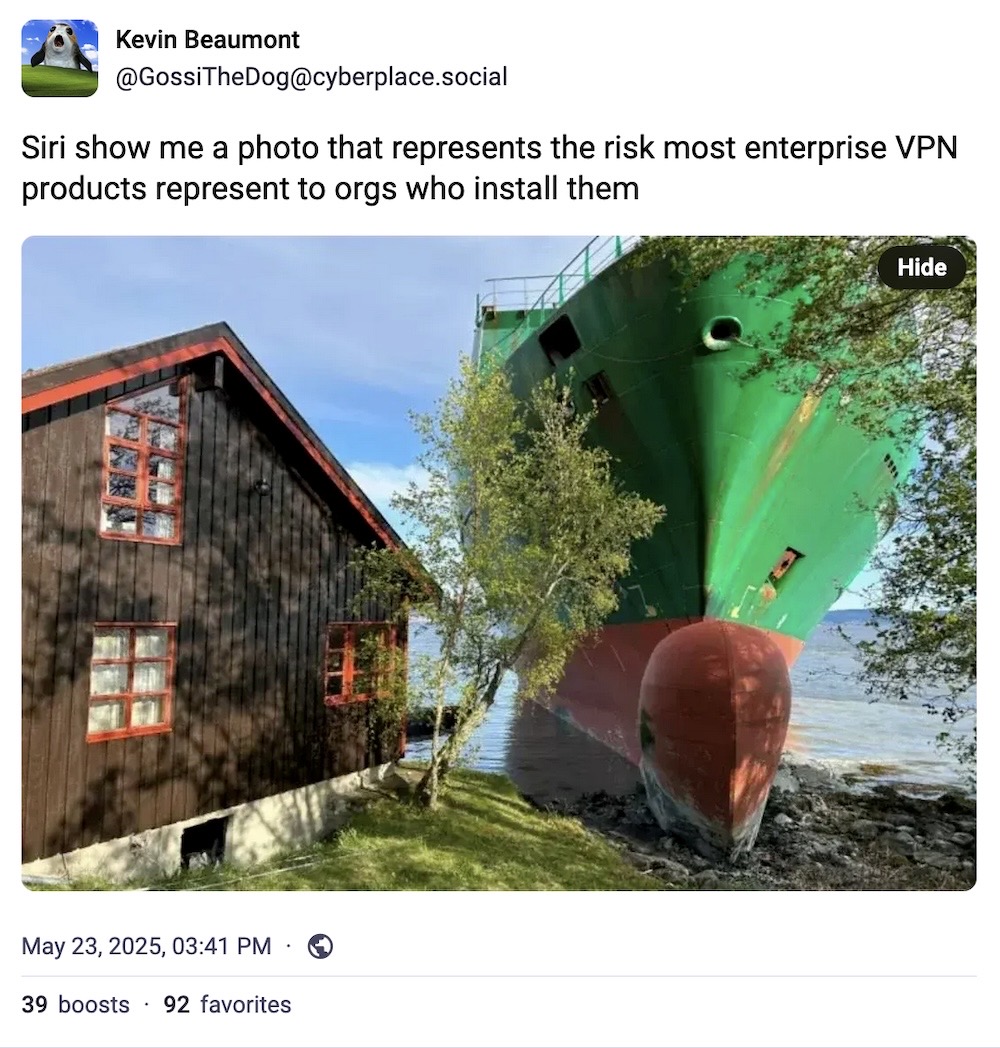
And... finally this week. Did you hear that story about that massive container ship that ran aground and got stuck just inches from someone's seafront house? Immediate alarms notwithstanding, we got some good memes out of it at least.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat box of light bulbs is Wilson, who is moonlighting as a physical pentester and can be seen here trying to sneak into a government complex in disguise. Trojan cat! Stay stealthy, Wilson. Thanks so much to Kyle B. for sending in!

Send in your cyber-cats (or a non-feline friend!) Drop a photo and name of your cyber-cat or friend by email, and they will be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's it for this week's cyber news. I hope you have a splendid rest of your weekend (and Memorial Day, for those in the United States).
I just want to say again, thanks so much for reading. It's really a joy to write this newsletter every week, and a true honor and privilege to reach so many people.
I'll be back next week with your usual roundup. As always, please do reach out if you want to share anything or just want to get in touch.
Until next,
@zackwhittaker