this week in security — may 26 edition
THIS WEEK, TL;DR
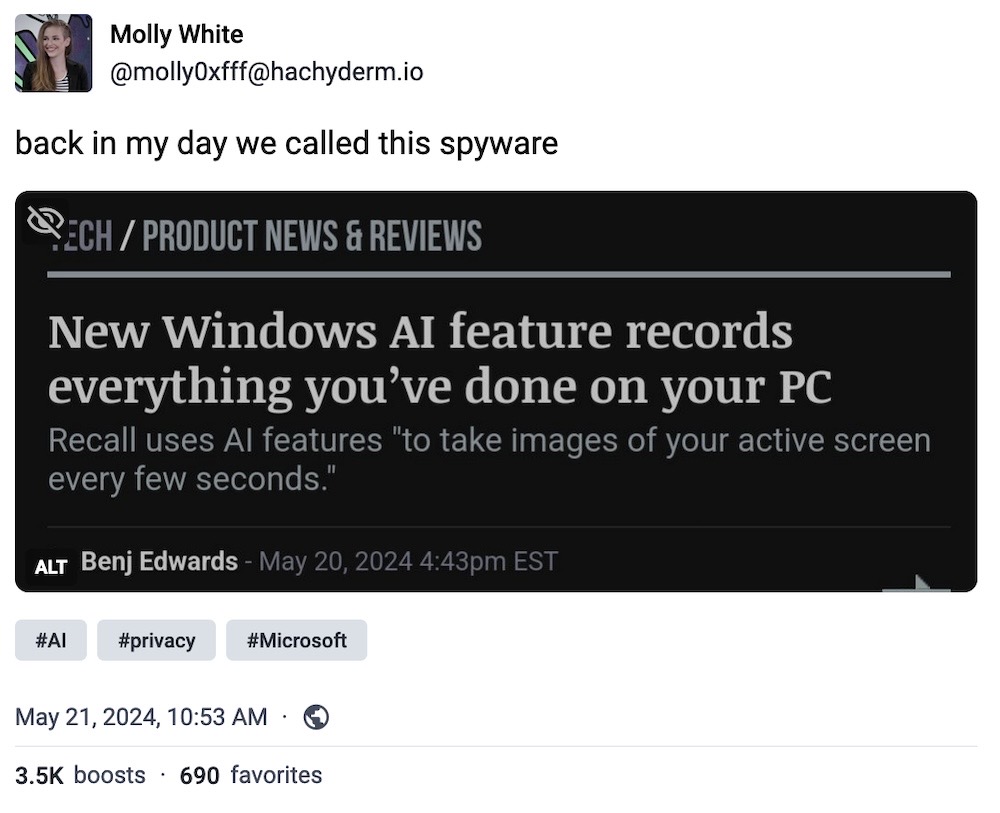
Microsoft's new Windows 11 Recall is a privacy nightmare
Bleeping Computer: Microsoft is rolling out a new spyware feature, I mean feature, called Recall, which saves a constant stream of snapshots and screenshots dating back three months — and it's all searchable through human language queries. Here's the big problem: The spyware *cough* feature (sorry) "performs no content moderation" so it won't mask your passwords or banking account numbers, or anything particularly sensitive. OK, what now?! At least the data is stored locally... so it's not safer, necessarily, but it won't be Microsoft's problem when someone's data will get stolen by a password stealer or worse. Look, there's a lot to say about Windows..pyw... Recall — and Bleeping does a great, if not the best job on explaining the pros and, well, many cons, so please read.
More: Microsoft | DoublePulsar ($) | BBC News | @molly0xfff
U.S. pharma giant Cencora says patients' health data stolen in cyberattack
TechCrunch: Pharma giant Cencora (which until 2023 was AmerisourceBergen), had a data breach in February affecting what's looking like a sizable number of patients' health data — including names, addresses, health diagnosis and medications. The company handles around 20% of the pharmaceuticals sold and distributed throughout the United States, and "served" at least 18 million patients to date, but has refused to say how many individuals its notified about the breach. (Disclosure: I wrote this story!) Cencora is the latest in a list of healthcare firms hacked in recent months, including Change Healthcare and more recently Ascension's hospital network, though Cencora said its cyber mess was unrelated to the two incidents. DataBreaches.net tallied up the number of those notified by Cencora so far, and counted over half a million. Expect that number to go far higher.
More: Cencora (Lash Group) | New York Times ($) | NPR | DataBreaches.net
Teslas can still be stolen with a cheap radio hack
Wired ($): Even more bad news, Tesla fans. Turns out that its new upgraded ultra-wideband keyless entry system isn't as secure as it's claimed. Researchers at the Beijing-based automotive cybersecurity firm GoGoByte demonstrated that they could carry out a radio relay attack that can unlock an affected Tesla. Since the keyless entry system also controls the car's immobilizer designed to prevent theft, the radio hacker can also start the car and drive off. The good news is that there's a fix, of sorts: Turn on Tesla's PIN-to-drive protection! "It's a warning for the mass public: Simply having ultra-wideband enabled doesn't mean your vehicle won't be stolen," said Jun Li, the car hacker behind the project.
More: @a_greenberg | @seldo

~ ~
THE STUFF YOU MIGHT'VE MISSED
pcTattletale leaked screenshots, was later hacked and defaced
TechCrunch: A spyware app called pcTattletale was found installed on the check-in computers at several hotels across the U.S., and we know this because the spyware app itself has a bug that's leaking screenshots from the device's it's planted on. Eric Daigle tried to report the bug to the spyware maker but was ignored. Since, an apparent vigilante hacker defaced pcTattletale's website and dumped its servers' contents on its own website, which included victims' data (which only causes further harm to victims) but also the customers who bought and planted it. The data is now in Have I Been Pwned, and @maia has analyzed the data dump.
'Re-appearing' iPhone photos sparks concerns, bug dissected
Synacktiv: Last week, Apple released iOS 17.5, which had a bug that multiple people reported seeing photos on their phone they had previously deleted. That sparked some concerns that Apple wasn't deleting photos properly when requested. But not so fast. Turns out a weird data corruption bug meant that "files on the devices themselves and not those that had been synced to iCloud," would seemingly return. Synacktiv's reverse engineering shows the bug fix sought to "prevent deleted photos stored outside of the photo library to re-appear." The Verge also explains more in less technical speak.
Redditors share their worst case of insider threat incidents
Reddit: Cyberfolks on Reddit's /r/cybersecurity took to a thread to discuss their worst cases of insider threats that they've seen (or heard about). Some employees got caught in the (digital) cookie jar, and one was a senior FBI agent that got busted for working for Russia's president Putin. But this thread gives some interesting insights into how some of these threats were identified, caught, and remediated. Take some with a pinch of salt, but good input from the wider cyber thought-cloud.
~ ~
OTHER NEWSY NUGGETS
EPA warns of more water cyberattacks: Cyberattacks against water utilities are on the rise, per the Environmental Protection Agency, which issued an alert urging water systems to take action to protect the nation's drinking water. Some 70% of inspected utilities during 2023 violated cyber standards, the agency told the AP. The usual suspects — Russia, China, and Iran — are blamed, but really, it's up to the U.S. industry to stop it, since a bunch of states (and the water lobby) back in 2023 sued the EPA claiming the federal agency didn't have the legal grounds to introduce cyber requirements. Yeah, that happened! (via Associated Press, The Record)
Hack, hack, who's there? A hacker has breached a scammer's call center, stolen its source code for the scammers' tools, and emailed its victims to tell them that they've been scammed. The company, Waredot, allegedly tried to get victims into installing junk software that costs money but doesn't work. Oh no, it's the consequences of their actions! (via 404 Media ($))
The Five Eyes of cyber: The Five Eyes intelligence alliance, made up of the U.K., U.S., Australia, Canada and New Zealand, collect much of the world's intelligence. Now, for the first time the five leaders of the Five Eyes agencies — the NSA, CSE, GCHQ, GCSB and the ASD (so many acronyms) — have been photographed together. Where was this photo taken? OSINT challengers, begin! (via @GCHQ)

Internet root server lags for days: Who hasn't just woken up one day and hated everything? That seems to be the best case scenario so far for what happened with one of the internet's core DNS servers — maintained by Cogent — which for more than four days fell out of sync with the other 12 root DNS servers. DNS basically makes web addresses work and load on your devices. It's still not clear why the root server fell behind the rest of the internet's core root servers, which could've caused internet instability, but it's worth asking why a private, for-profit company (that's said nothing so far about the incident) still runs one of the most important pieces of infrastructure in modern history. (via Ars Technica)
Nissan's cybersecurity incident call center... breached: The carmaker Nissan confirmed the call center it set up to handle customer inquiries after a data breach last year has itself been breached, per ITNews.com.au. The call center, provided by OracleCMS, confirmed that affected individuals had their names, contact details, dates of birth and a summary description of the information in the Nissan cyber incident notification letters stolen. Or, as @JP jokingly described, "We apologize again for the fault in the system. Those responsible for dealing with the people who have just been hacked... have been hacked." (via ITnews)
~ ~
THE HAPPY CORNER
Breathe? Breathe. Here's the happy corner.
Shout out to all the folks who were at Sleuthcon this year (I wish I could've gone!). The accidental renaissance photo looks great.

Congrats to area cyber reporter @bing_chris for obtaining further cybers. Very well deserved.
And, I'll leave you with this final, important thought for the week.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Toby, who has the smug look of someone who just changed all of your passwords because someone said he couldn't have any kitty treats. All the more reason to use a password manager! Many thanks to Steffany B., for sending in!

Send in your cyber cats! Feel free to drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
A little quieter-than-usual this week, in large part due to the Memorial Day weekend in the U.S. There just wasn't that much news. Still, thanks so much for reading this slightly abridged version, wherever you are in the world!
Please do to get in touch with any feedback you have (and cybercats, of course!).
All my best,
@zackwhittaker