this week in security — may 28 edition
THIS WEEK, TL;DR
Spain wants to ban end-to-end encryption in the EU
Wired ($): A bombshell this week: according to a leaked document, Spain advocated for banning encryption for hundreds of thousands of people across the European Union. It's in response to an EU proposal to compel tech companies to scan their platforms, including private messages, for CSAM — or child sexual abuse material. In a document with feedback from member states, Spain said the quiet part out loud, but it's a growing sentiment across the EU as democracies get increasingly hooked on the idea of even more surveillance. Poland also advocated for greater anti-encryption powers; not a surprise from two nations also known to be heavy users of spyware. What's worrying is just how on board most of the EU is with busting encryption and snooping on our messages. (Shoutout to Belgium for not realizing you can't retract an email.) Germany, at least, said the idea was crap and seems dead against it. Danke!
More: Techdirt | Statewatch | @mattburgess | @riana | @lhn

Chinese hackers targeted Kenyan government as debt strains grew
Reuters ($): Chinese hackers targeted Kenya's government in a widespread and years-long hacking campaign targeting key ministries and other institutions. Two sources tell Reuters that it's believed the hacks are aimed at — at least in part — gaining information related to debt the Kenyan government owes to Beijing. As Reuters notes: "Kenya's finances are being strained by the growing cost of servicing external debt — much of it owed to China." The growing theory — one that Beijing roundly rejected — is that China is willing to leverage its hacking ability to snoop on governments abroad to protect its economic interests abroad. Reuters reporter @pearswick has more in a tweet thread.
More: Nairobi News | @lukOlejnik
Microsoft says China hackers targeted Guam; is Taiwan the real target?
The New York Times ($): U.S. intelligence, the Five Eyes, and Microsoft say a Chinese hacking group they call "Volt Typhoon" planted malware in telco systems in Guam, a U.S. territory in the Pacific. Microsoft has all the details, but didn't keep it light for long. In its opener, Microsoft says the espionage campaign (think information gathering) across telcos could eventually be used to "disrupt critical communications infrastructure between the United States and Asia region during future crises." The fear is that the spies could knock out networks on Guam that could help the U.S. respond to a potential Chinese invasion of Taiwan. NSA's cybersecurity director @RGB_Lights told CNN that NSA agreed with Microsoft's assessment. Meanwhile, the Five Eyes governments dropped details of how to remediate the access, much of it centered on Fortinet networking gear.
More: Microsoft | CISA | CNN
U.K. data protection regulator receiving 'large number of reports' about Capita
The Record: Outsourcing catastrophe Capita had a second data breach after it left an Amazon S3 storage bucket exposed for years, on top of an earlier ransomware attack. Instead of owning it and helping customers, Capita responded by denying it. Now its porkies are catching up with it, after several U.K. local councils said that their data was caught up in the massive data exposure. And the U.K. data protection regulator is less than thrilled. In a spicy Twitter post, the ICO said it was "making enquiries" (which is British talk for scathing). Capita is a huge outsourcer for the U.K. government and handles a ton of pension schemes. You know, super sensitive data you don't want on the internet. DoublePulsar has the post-mortem of Capita's gross misrepresentations.
More: BankInfoSecurity | TechCrunch | @ICOnews
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Ethical hacker scams 60 Minutes staffer to show how easy digital theft is
CBS News: An excellent video report you can share with your friends and family on the new ways that scammers are using to trick folks into handing over money. In this case, hacker @racheltobac demonstrated how bad actors can use AI to mimic voices and trick people into turning over information. Really sage advice here: Scammers rely on urgency and fear! Don't let them trick you.
Here's how long it takes new BrutePrint attack to unlock 10 different smartphones
Ars Technica: Academic researchers have created a new low-cost smartphone attack that can crack the fingerprint authentication to unlock the screen and other features on a range of Android devices. The attack, dubbed BrutePrint, can be exploited in a few minutes using $15-worth of equipment and access to the device, but your mileage may vary by device. It's another classic @dangoodin deep-dive you can't miss.
Legitimate Android app iRecorder found with malicious code after launch
ESET: ESET researchers found a trojanized Android app on Google Play, the official app store, called "iRecorder - Screen Recorder." It appeared legitimate and had over 50,000 installs, but months after it first launched it received a malicious update that allowed it to extract microphone recordings and steal files. More from @LukasStefanko's findings on AhRat, the discovered Android remote access trojan.
A technical analysis of Intellexa's Predator spyware
Cisco Talos: Talos researchers dig deep into the technical workings of the Predator spyware, sold by the spyware firm Intellexa/Cytrox. The spyware has been widely reported to have been used in Greece, the ongoing government row dubbed Greek Watergate. It's a fascinating detailed walk through of the infection chain if you're wondering how the spyware works.
~ ~
OTHER NEWSY NUGGETS
PyPi was subpoenaed: The Python Software Foundation said it received three subpoenas from the U.S. Department of Justice for user data related to five PyPI usernames. It's not clear what investigation it relates to. Pretty transparent account here. (via PyPI, The Register)
Spyware in wartime: Digital rights group Access Now has a new report detailing new Pegasus spyware infections in the Azerbaijan-Armenia conflict — the first time that spyware is known to have been used in wartime. The report confirms 12 Armenian human rights officials, journalists, activists had their phones infected. The Azerbaijan government is likely behind the compromises. (via Access Now, The Guardian)
~ ~
THE HAPPY CORNER
Oh look where we are, it's the happy corner.
Bcrypt, the popular hashing algorithm, turns 25 this year. This mini-profile looks back at what made bcrypt so popular — it's open-source and has been implemented everywhere.
I don't know who needs to hear this but if you ever find a tracking device and need to build a makeshift Faraday cage to block its signals, maybe don't rely on a pressure cooker (per @mattblaze).
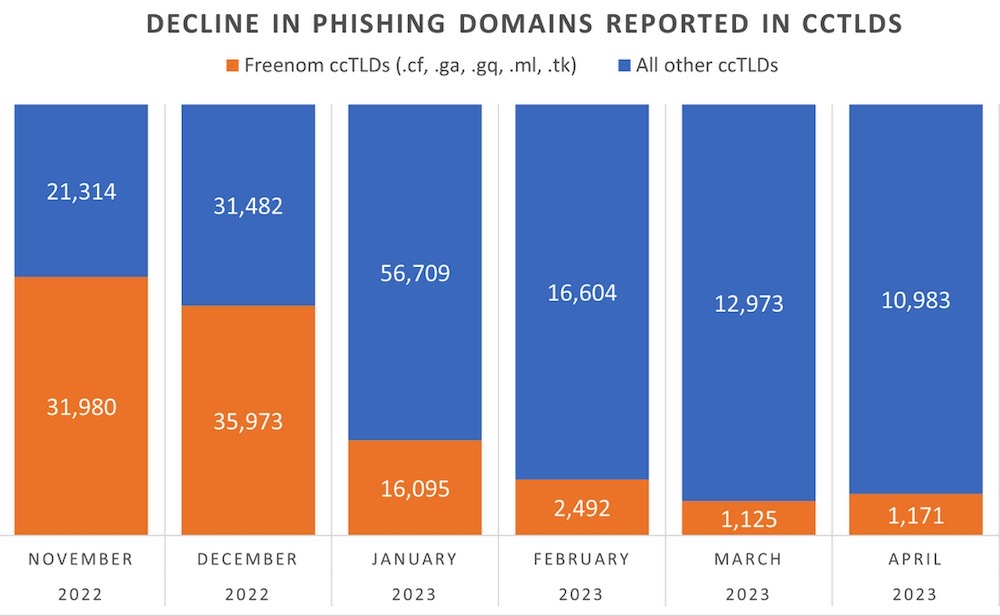
And a rare win: a lawsuit brought by Facebook parent Meta against domain name registrar Freenom appears to have resulted in a massive drop in phishing domains in recent months. Meta said it saw a huge amount of spam and phishing domains hosted on Freenom, and sued to stop it. Cause and effect? More from @securityskeptic.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Emma. Drop her a treat and she'll drop you a webshell. The other cybercats in the neighborhood don't stand a chance. Thanks to Pearson H. for sending in!

Please keep sending in your cyber cats! Send in a photo and their name, and they'll be featured in an upcoming newsletter. (Cyber cats and their non-feline friends are welcome!)
~ ~
SUGGESTION BOX
That's all for this week — a quieter week due to the Memorial Day long weekend here in the United States. Hope you have a good one. Let me know if you have any feedback. And please send in your cyber-cats (or their friends)!
Same time, next week?
—@zackwhittaker