this week in security — may 29 edition
THIS WEEK, TL;DR
Twitter will pay $150M fine over accusations it improperly sold user data
NPR: Twitter has agreed to pay $150 million in a settlement with the Justice Department and the FTC over historical accusations of illegally using people's personal data over six years for targeting advertising. Much of what was disclosed we knew in 2019 — that Twitter used phone numbers and email addresses given for 2FA or for account recovery for serving ads. That was in violation of a 2011 agreement with federal regulators. It's also ordered to no longer use the information that it "deceptively collected." One of the most recent examples of "explicitly using users' desire for better cybersecurity to exploit them."
More: FTC | Twitter | Washington Post ($)
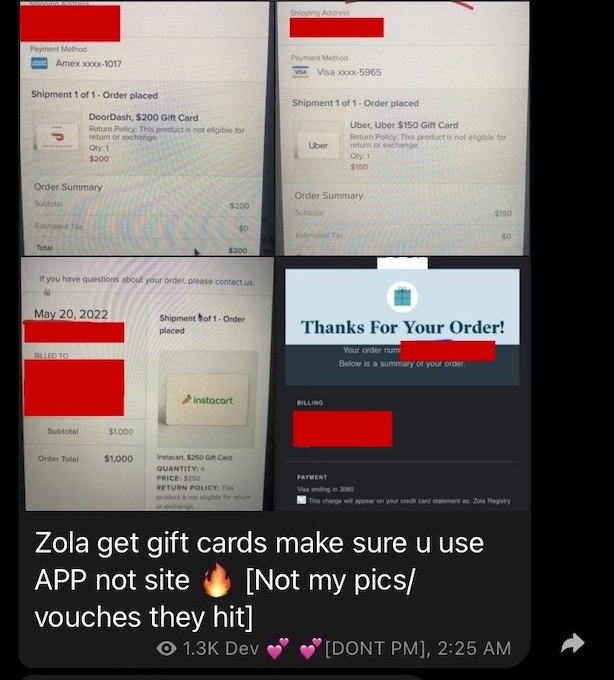
Scammers breach Zola wedding accounts and make fraudulent purchases
The Verge: Rough week for wedding-havers after hackers broke into hundreds of Zola accounts, an online wedding registry. Zola said it was a credential stuffing attack and 0.1% of its users were affected, with some of the hackers spending thousands of dollars using credit cards saved on file with Zola. The Verge first caught wind from Zola that the hackers were cashing in on gift cards. Later, my colleague @carlypage_ and I saw a private Telegram chat where hackers were discussing how they would order gift cards worth hundreds of dollars and ship them to email addresses they control (see below). Zola said it has blocked all transactions and refunding all balances.
More: Zola | Motherboard
Russian hackers are linked to new Brexit leak website, Google says
Reuters ($): Wild story from the Reuters cyber team. A website titled "Very English Coop d'Etat" published emails from former U.K. spymaster and leading pro-Brexit campaigners that claimed was part of a plot to secretly working to secretly call the shots in the U.K., such as allegedly trying to oust the former prime minister who negotiated the Brexit deal. Turns out it was a Russian hack-and-leak op, according to Google. Fascinating discovery here — and the tl;dr from Reuters reporter @razhael in his tweet thread. Admittedly I almost choked on my coffee with laughter when I saw who the Russians were referring to as a "sneaky strawhead"...
More: The Register | @billyleonard tweets
Hacker leaks police database files from inside Xinjiang camps
BBC News: Really vital and important reporting here. A massive cache of files obtained by someone hacking into "police/re-education camp computers" in Xinjiang — where millions of mostly Uyghurs are detained in highly surveilled camps. It's one of the most revealing and visual leaks from inside the camps, which China keeps shrouded in secrecy (and denial — in spite of the vast body of evidence) — though as Motherboard notes, the exact contours of the hack itself are unclear. This is really worth your time to read, plus bonus @hatr thread on how the files were authenticated and their OSINT findings.
More: Ars Technica | Tagesschau (German) | @ipvideo
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
We need to talk about sex toys and cyber security
Pen Test Partners: We don't talk about sex enough generally as a society even though it's an everywhere and everyone thing. We certainly don't talk enough about sex toys and cybersecurity, which can have some really damaging consequences. @TheKenMunroShow gave a TEDx talk recently about some of the great work that's been done in bringing awareness to poor security and data practices with connected sex toys and why as an industry we need to talk more about the risks and harms that can be literally deadly to some people.
Security flaw in Tor Browser, update today
Darknetlive: Update to the latest Tor Browser (version 11.0.13) as soon as possible to fix a security bug that affects all platforms, including Tails. The bug is in the JavaScript engine of Firefox, which is the base for the Tor Browser. "This vulnerability allows a malicious website to bypass some of the security built in Tor Browser and access information from other websites. For example, after you visit a malicious website, an attacker controlling this website might access the password or other sensitive information that you send to other websites afterwards during the same Tails session." It doesn't break the anonymity and encryption of Tor connections, however.
Critical Zoom vulnerabilities fixed last week required no user interaction
Ars Technica: Google Project Zero is back with a couple of vulnerabilities in Zoom that could have been exploited to launch zero-click attacks that could remotely run malicious code on devices running the Zoom software. Zoom fixed the bugs.
GitHub saved plaintext passwords of npm users in log files, post mortem reveals
The Register: GitHub said it inadvertently stored "number of plaintext user credentials for the npm registry," according to a company post-mortem, which discovered the issue as part of its investigation into April's unrelated OAuth token theft attack. The creds were stored in GitHub's internal logs, but still a pretty sizable mess-up. (Remember when Facebook did a similar thing?)
~ ~
OTHER NEWSY NUGGETS
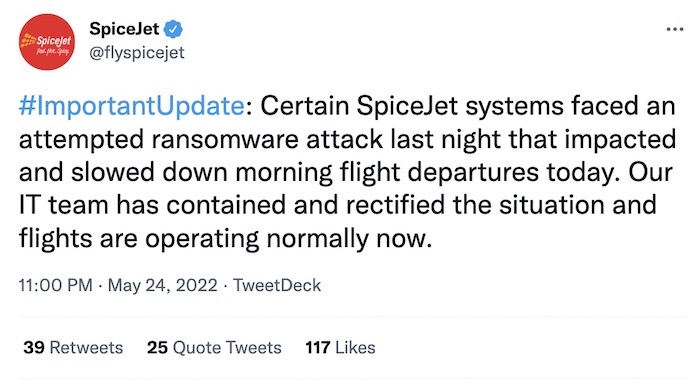
SpiceJet hit by ransomware attacks: BBC News reports that SpiceJet, one of India's biggest airlines, was battling a ransomware attack that left passengers stranded at airports and flights delayed. SpiceJet said things were "operating normally" while passengers took videos of them stuck on flights. Not the first time that an airline has been hit with ransomware: Bangkok Air was hit last year (via @uuallan) with passenger's personal information later published online.
Hacker steals database of Verizon employees: A hacker has obtained a database that includes the full name, email address, corporate ID numbers, and phone number of hundreds of Verizon employees, according to Motherboard, which verified a portion of the data set. "The anonymous hacker said they obtained the data by convincing a Verizon employee to give them remote access to their corporate computer. At that point the hacker said they gained access to a Verizon internal tool that shows employee’s information, and wrote a script to query and scrape the database."
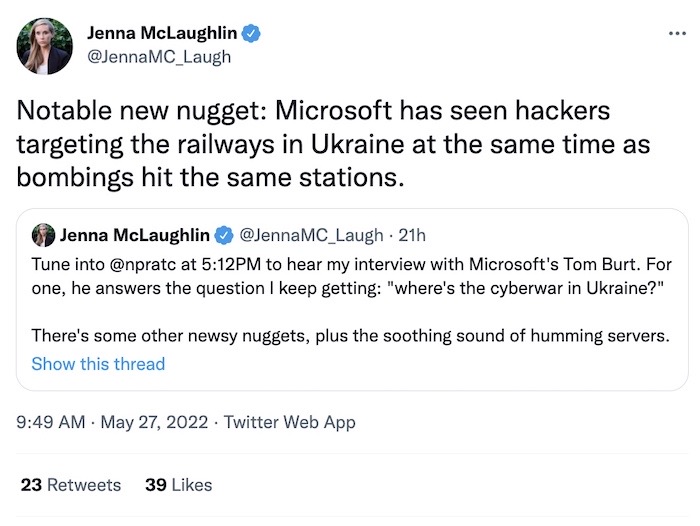
Cyberwar already underway in Ukraine: NPR cyber correspondent @JennaMC_Laugh was in Seattle to interview Microsoft's customer security chief Tom Burt, who gave the latest on what the company is seeing on the cyber front in Ukraine — including how Russian cyber operations are timed with its kinetic operations on the ground, including attacks on Ukraine's railways, which are a key method for transportation around the country. The transcript of the interview is here.
~ ~
THE HAPPY CORNER
Some good news this week as Otter, a popular transcription service, enabled two-factor authentication for all its plans. Previously it was just tied to enterprise accounts. The Freedom of the Press Foundation wrote about the security of transcription services earlier this year and noted that Otter didn't offer the security feature widely. As @runasand notes, "advocacy works."
And finally: here's a reason why you should never test in prod. Per the BBC, "behind the scenes, someone was training to learn how to use the ticker and to put text on the ticker, so they were just writing random things not in earnest and that comment appeared."

To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's very...strange-looking cyber cats...are Daisy (brown) and Bear (white). Four legs, two eyes, cute faces... yep, they certainly look like cyber cats to me. Many thanks to Omar for sending them in!

Send in your cyber-cats or their friends! Drop me an email here with their name and photo, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's it for me for now. No newsletter next week (sorry!) but back as usual on June 12. In the meantime, the suggestion box is always open or drop any feedback by email.
Take care, be well (and don't forget to send in your cyber cats!)
—@zackwhittaker