this week in security — may 4 2025 edition
~ ~
THIS WEEK, TL;DR
U.K. retail giants hacked by ransomware gang
BBC News: We start in the United Kingdom, aka my OG homeland, where retail giants Co-op and Marks & Spencer have reported intrusions and are trying to regain control of their networks. The situation is messy, but it looks like the DragonForce ransomware gang, potentially with the help of Scattered Spider — whose tactics involve initial access and social engineering — have taken credit for the attacks. The hacks are causing havoc and affecting grocery store shelves. News of the hacks started with M&S, which said it's experiencing ongoing internal disruption after it pulled much of its order systems offline. Then another major retailer, the Co-op, said everything was fine... until it wasn't, only confirming its cyberattack was in fact a data breach after the BBC reported that the DragonForce gang told its reporters that they stole customer data on some 20 million people. Harrods, another major U.K. store, was also targeted, but no word yet on any successful intrusions there. As @GossiTheDog writes in a blog post, while folks are at the RSA Conference thinking about "quantum AI cyber mega threats," big firms are ignoring the basics, and getting pwned by highly skilled and capable "advanced persistent teenagers."
More: Bloomberg ($) | Bleeping Computer | NPR | The Guardian | DoublePulsar ($) | @GossiTheDog posts
DHS' Noem at RSA: CISA needs to get back to 'core mission'
Cyberscoop: Speaking of the RSA Conference, that was a thing this week. U.S. Homeland Security Secretary Kristi Noem used her keynote at the industry-focused cyber-fest to urge Congress to reauthorize a law that encourages businesses to share cyber threats with the federal government. Not everyone is clearly thrilled about that, given DHS' role in rendering U.S. citizens to third-countries and huge cuts at cybersecurity agency CISA, which are still ongoing. This is in the same week that the Trump administration said it's planning to cut half a billion dollars from CISA's budget, weakening the agency even more than it's already has been, at a time when lawmakers' top committee officials aren't even sure that CISA can carry out its core mission in the face of so many layoffs. Noem faced a mild, tepid crowd, per @kevincollier and @gregotto, who live posted the keynote. As I posted this week, it's worth remembering that the cybersecurity industry is not the same as the cybersecurity community.
More: The Record | Fast Company | Cyberscoop
JPMorgan Chase CISO fires warning shot ahead of RSA Conference
SecurityWeek: It's worth noting this yarn from @ryanaraine, who blogged about JPMorgan Chase's top cyber chief basically calling out the horrid state of cybersecurity today ahead of the big annual RSA meet-up. A key line here: "Fierce competition among software providers has driven prioritization of rapid feature development over robust security." In short, cyber is moving at such a pace where profits are put ahead of quality control and security (a bit rich coming from JPMorgan, excuse the pun, but still), saying that the "pursuit of market share at the expense of security exposes entire customer ecosystems to significant risk and will result in an unsustainable situation" for the economy. All to say, AI-this and AI-that isn't going to save us from massive hacks, like the incidents we're seeing in the U.K. retail sector right now. Per Naraine, much of this fell on deaf ears at RSA where the "gravitational pull of AI-powered hype is unmistakable."
More: JPMorgan Chase | Risky.biz
TM SNGL, the obscure Signal knock-off used by Trump officials
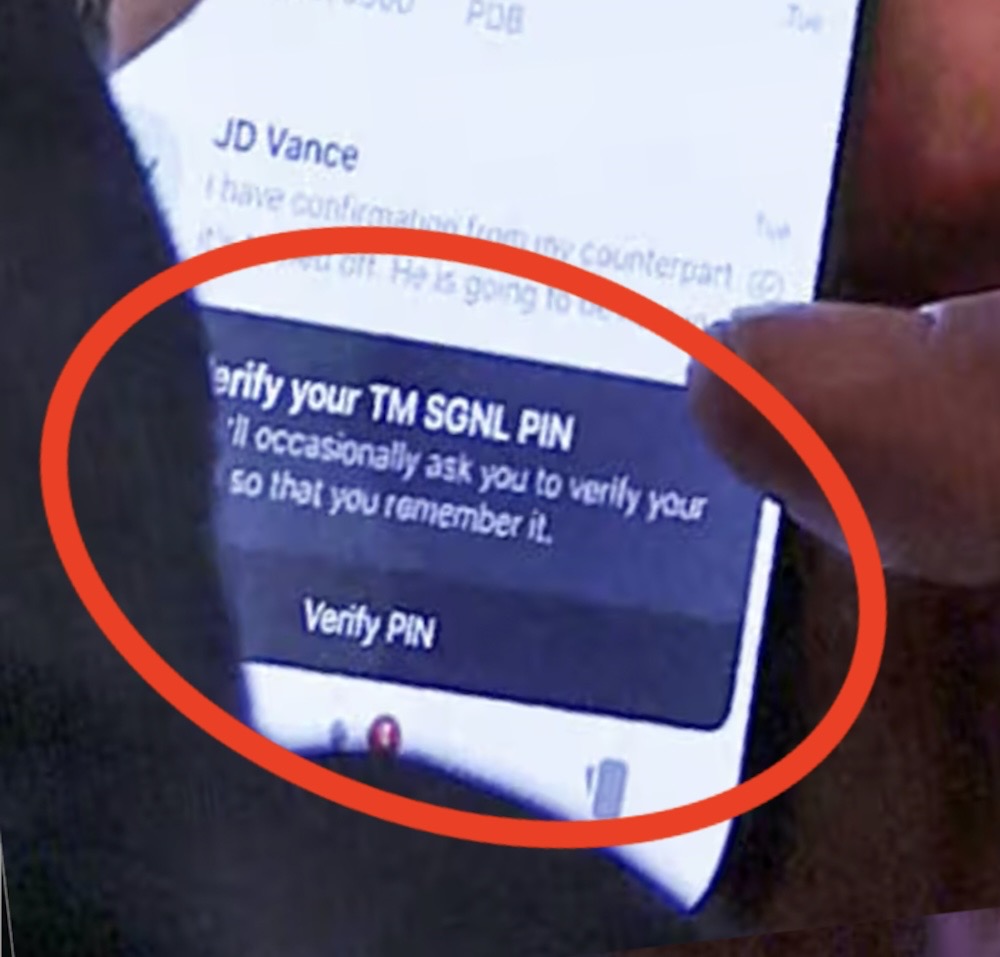
Micah Lee: Let's check in real quick on the state of cybersecurity in the Trump adminis... oh no. Can it get worse? Yes, yes, it actually can. As a reminder, Michael Waltz and other senior cabinet-level officials were said to be using Signal to share classified war plans... which, granted, Signal isn't cleared for government use but at least it's still Signal, right? Well, not quite, because it turns out a Reuters photographer snapped a photo of Waltz using his phone during a cabinet meeting and — sorry, I don't shout very often but... IT'S NOT EVEN SIGNAL... *sound of muffled screaming into a pillow*. In short, TM SGNL is an Israeli-developed unlicensed Signal rip-off with eye-wateringly bad security (including hardcoded credentials). The whole point of the app is to allow its users to save a copy of their messages to a central server... which... yes, defeats the very point of Signal. At least (he says, while evidently holding on to my last shred of sanity) this solution appears to be an attempt by the government to follow federal records-keeping laws, alas, these ostensibly encrypted messages are then archived in something like a Gmail account. (I can't even anymore.) Not to stress you out too much, but Tulsi Gabbard, Marco Rubio, and JD Vance are also seen in Waltz's Signal chats, per Reuters.
More: 404 Media ($) | Electrospaces | New York Times ($) | @kevincollier
~ ~
THE STUFF YOU MIGHT'VE MISSED
Can the U.S. government seize domain names?
Rob Ricci: Yes, in short, the U.S. can (and does) seize domain names on the semi-regular with court orders, especially for cybercrime operations. @ricci goes into how the process can work, albeit with caveats. It's worth thinking about from a threat model point-of-view, especially from a legal and jurisdictional perspective.
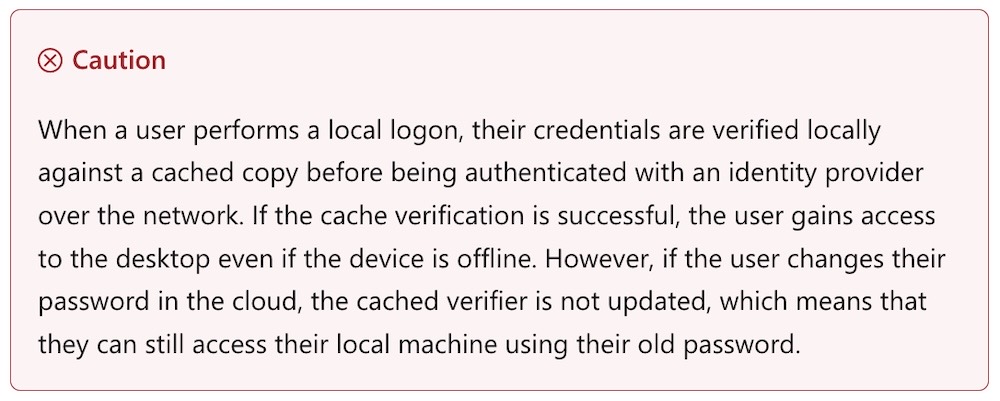
Microsoft: No plans to fix Windows bug allowing logins with revoked passwords
Ars Technica: Revoking a password is meant to be a surefire way of preventing access to a user's account when credentials are stolen. But a bug in how Windows handles remote desktop logins allows anyone to login using a since-revoked credential. Microsoft told Ars that it would "be in touch" if it had anything to share — so, no fix just yet. Instead, Microsoft updated its pages to caution, in red lettering, that if a user changes their password in the cloud and the cached verifier hasn't updated, this "means that they can still access their local machine using their old password." Cue area security buff @wdormann: "It doesn't make sense from a security perspective."
Developer leaked private API key for SpaceX, Tesla LLMs
KrebsOnSecurity: Huge facepalm here after an employee at Elon Musk's AI company, xAI, exposed a private key on GitHub that for the past two months could've allowed anyone to query private custom-made large-language models used for handling internal data at Musk's companies, including SpaceX, Tesla, and X. Researchers at GitGuardian found the exposed key and notified the employee and later xAI directly — but was told to report the exposure through HackerOne (yeah, that happened!). While many awe and ahh at AI, it's still unraveled by *checks notes* an exposed private key. This wouldn't be the worst breach in the world if Musk wasn't hellbent on feeding much of the U.S. government's stores of citizen data into his own AI systems.
How Riot Games is fighting the war against video game hackers
TechCrunch: Here's a really interesting long-read on how Riot Games, the company that makes Valorant and League of Legends, fights its war against cheaters and cheat developers. Video gaming is big business, and so is the game cheating industry that gives gamers an unfair advantage. Look, I'm no gamer, but I learned a ton in this @lorenzofb story about how cheaters actually hack games (including funneling in-game memory to an entirely separate computer) — but also how they can get caught.
Dating app Raw exposed users' location data and personal information
TechCrunch: Dating app Raw, which this week announced plans for a hardware wearable that claims (without evidence) to track a partner's emotions, claims to use end-to-end encryption. But when I ran the app through a network traffic analysis tool, there was no evidence of end-to-end encryption — but there was a leak exposing users' precise location data to the open web. The company fixed the bug soon after I contacted the company's co-founder. (Disclosure alert: I wrote this story.) My take is that if I could find this bug in less than 20 minutes and I'm a journalist for crying out loud, I dread to think who else could've found this before me.
Inside the efforts by North Korea to steal your job
Wired ($): An absolute belter of a story looking at how North Korean hackers and spies use AI and deepfakes to dupe unsuspecting companies into hiring them, thinking they're ordinary, non-sanctioned individuals. Although still crude for the most part, these techniques are getting better — and in any case, they're working now, even as the technology improves. This story gives a good fly-on-the-wall look at how the interview process works with some of these would-be North Korean hires. Remember: If you suspect a North Korean spy, ask them to say something rude or mean about Kim Jong Un... and see if you can count to three before they vanish and log off. Also: Sentinel Labs has a good report on what it's like to be targeted as a security company, and what to look out for.
Bots be warned of zip bombs
Ibrahim Diallo: Bots are everywhere, probing for flaws or scraping the internet and feeding them into AI systems. But Ibrahim Diallo has an idea: Zip-bombs, or highly compressed files that when opened can expand into a huge file that can overwhelm a bot's machine. When Diallo detects a bot, his website serves a small file that the bot is happy to accept and then... disappears off the web when the bot invariably crashes. Consider at your own risk, of course.
~ ~
~ ~
OTHER NEWSY NUGGETS
Governments lead the zero-day way: Google said that out of the attributable zero-days it's seen during 2024 (that is, the exploits it can definitively link back to certain threat actors), most of them are in use by governments and commercial surveillance vendors (which sell almost exclusively to governments). It's worth noting a fair percentage of zero-days are also actively used by cybercrims (think ransomware and extortion attacks). (via Google, TechCrunch)
Salut, l'unité 20728 du GRU: The French government confirmed this week (en français) that the Russian GRU's noisy hacking unit APT28 (aka Fancy Bear) were behind a series of cyberattacks targeting France — including the 2024 Paris Olympics. The French also name-dropped a new Russian GRU unit, 20728, linked to APT28. Wired ($) notes the newly disclosed unit is based in the southern Russian city of Rostov-on-Don and operates out of an "information research center." (via French government, @johnhultquist)
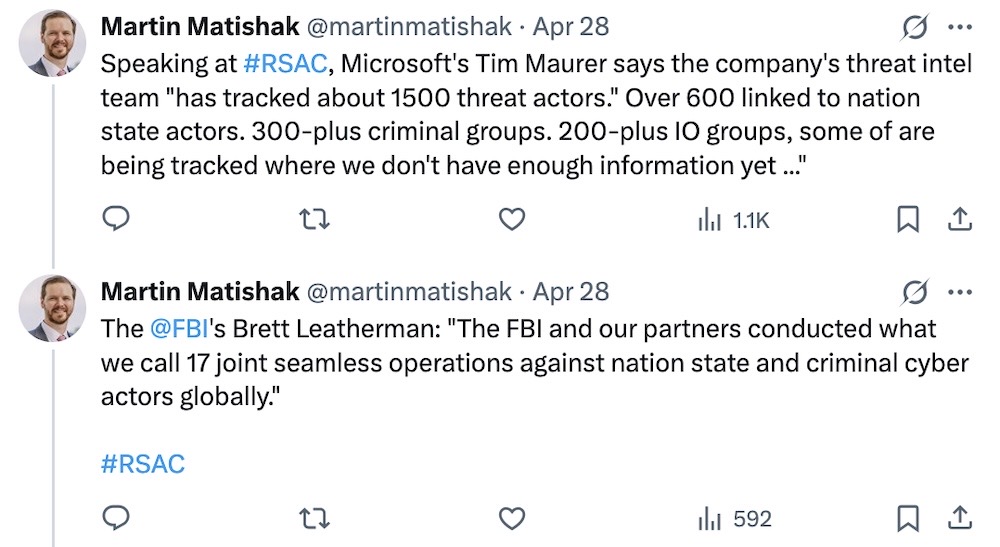
FBI conducts dozen-plus operations: At RSA, an interesting tidbit (albeit light on details): the FBI and its partners carried out 17 "joint seamless operations" against nation state actors and cybercriminals globally of late. To put that into context, Microsoft said at RSA that it's tracking about 1,500 major threat actors worldwide, including around 600 linked to nation states, 300-plus criminal groups, and about 200 groups related to information operations. (via @martinmatishak)
Car subscriptions raise your surveillance risk: Hands-free driving systems, heated seats, and car cameras: all of these technologies enable police to obtain gobs of information about you, where you go, and how you get there. Wired ($) found that cops are regularly tapping internet-connected cars that have subscription features, including through tower dumps. @dell has a handy chart that shows how much surveillance vs. what car. Remember, @kashhill also did some incredible reporting last year on how car makers are using and selling your vehicle data to raise your insurance rates. (via Wired ($), @couts)
Inside a credit card fraud ring: An investigation run by Norwegian outlet NRK, along with BR and Le Monde, included secretly monitoring a credit card fraud gang for a year to understand how they operate, including how the scammers stole more than 884,000 payment cards captured from unsuspecting people worldwide in a handful of months. This is a great story about sheer patience and incredible OSINT, and how they identified the scammer. (via NRK, @martingund tweets)
~ ~
THE HAPPY CORNER
Finally, we can leave all that hot mess of a week behind. This is the happy corner.
Firewall admin (aka "slayer of packets")? It's time to update your resume accordingly.
For those who're heading home after RSA, @wbm312 has your RSA buzzword bingo card ready to fill out.
And, lastly this week. Let's check in quickly with the good folks at the EFF, who have an open letter in support of former CISA director Chris Krebs, who faces a retaliatory federal investigation by the Trump administration. The letter was initially published with dozens of major names in security, and now has over 400 signatures.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cats are Charles and Ada, who can be seen here 'troubleshooting' the office printer... or hacking it, more like! Thanks so much to Becky for sending in!

I hate to ask even more of you but... ⚠️ please send in your cybercats ⚠️ or a non-feline friend! The bank of cybercats is running low! You can drop a photo and name of your cyber-cat or friend, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
This was... a very, very busy one! Thanks for reading all the way through. I'll be back next week as usual with everything you need to know.
Please do get in touch by email if you have anything to share with me for the newsletter, or just want to say hi. Also, please do drop your feedback in my survey if you can!
See you next,
@zackwhittaker