this week in security — may 8 edition
THIS WEEK, TL;DR
Data broker selling location of people who visit abortion clinics
Motherboard: This week saw the leak of a Supreme Court draft opinion that indicated that the court will soon overturn Roe v. Wade here in the U.S., ending guarantees that protect a person's constitutional right to have an abortion. Clearly this will have major ramifications, not least for human rights and healthcare — but also for privacy rights, especially for those who seek abortions or need to seek medical and reproductive services in places where procedures are banned. As @josephfcox reported this week it's incredibly easy to identify people who visit abortion clinics from the location data collected from the apps on people's phones. @alfredwkng also reported on another data broker that offered location insights on dozens of Planned Parenthood locations. My colleague @carlypage_ explored the not-unfounded fears that data collected from period trackers could be used in a post-Roe world to prosecute people seeking abortions. No matter which way you look at it, we're on the edge of a major human rights crisis in the U.S., and reporting this week shows just how easy it is for data to be used to identify people. As Recode says, "The pre-Roe world didn’t have data privacy laws. The post-Roe world needs them."
More: Motherboard | Wired ($) | BBC News | EFF | @melissagira
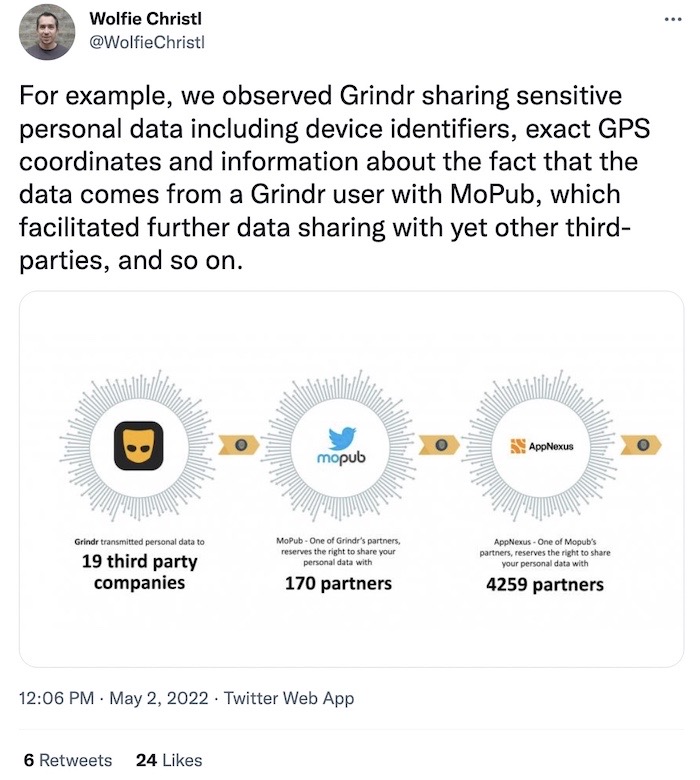
Grindr user data was sold through ad networks
Wall Street Journal ($): The precise movements of millions of users of the gay-dating app Grindr were collected from a digital ad network since at least 2017, according to sources speaking to the Journal. Grindr cut off the flow of location data two years ago. But for a time this commercially available data contained at-times intimate details about its users, like location data. It's the same kind of location data that allowed a publication to out a U.S. Catholic official last year as a Grindr user.
More: PinkNews | @wolfiechristl tweets
Over 200 Spanish mobile numbers 'possible targets of Pegasus spyware'
The Guardian: The Moroccan government is likely behind the mobile hacking of 200 Spanish phone numbers, including Spain's prime minister and defense minister, in mid-2021. The hacks happened at a turbulent time for Spanish politics, given the divisive pardons of nine Catalan independence leaders and a separate diplomatic spat with Morocco. Their numbers were on a leaked list of phone numbers said to be possible targets of NSO's Pegasus spyware, but also Candiru spyware, according to Citizen Lab's report last month. This week also saw a leading Catalan separatist politician say that Spain's spy chief "acknowledged" that her agency hacked into the phones of "some" of the Catalonian pro-independence party members. So, to recap: Morocco is likely hacking politicians in Spain, and Spain is likely hacking politicians in Catalonia.
Archive: Citizen Lab | More: Associated Press | The Guardian

Cyber Command did nine 'hunt forward' ops last year, including in Ukraine
Cyberscoop: U.S. Cyber Command, the offensive operations sister agency to the NSA, launched nine "hunt forward" operations last year, which is to say operations that have caused friction to the adversary in cyberspace. One of the operations was to help build resilience in Ukraine ahead of an anticipated (and eventual) Russian invasion. The unit's chief, Gen. Paul Nakasone, told the AP that some of these operations involved deploying defensive teams, including in Lithuania. As an aside, Nakasone — who heads both Cyber Command and the NSA under Trump and Biden administrations, has been asked to stay on for another year beyond his four-year posting.
More: Associated Press | The Record | Bloomberg ($)
Heroku resets user passwords weeks after GitHub OAuth token theft
ZDNet: Heroku has reset user passwords after sending out a last-minute alert warning users that their API access would also get wiped out and would need to be regenerated. It follows a security incident on April 12 that saw a theft of OAuth tokens — four tokens related to Heroku Dashboard and one from Travis CI. The OAuth token theft was detected by GitHub. The tokens were used to read and list all of the private repos they could access, and downloaded the contents of private repos from dozens of organizations. SecurityWeek explains more, too. People are rightfully not thrilled about Heroku's handling of all this.
More: GitHub | Heroku | @jacobian tweets
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
GitHub will require all code contributors to enable two-factor by 2023
TechCrunch: Speaking of GitHub, the coding platform giant will require all users who contribute code to enable two-factor authentication by the end of 2023. According to GitHub's own data, only about 16% of active GitHub users and 6% of npm users have 2FA enabled. Per @fredericl: "That is not a lot, and frankly fewer than I would have expected." Here's GitHub's explainer on the data.
Man convicted in phishing scam that cost Pentagon $23.5M
Decipher: A California man was convicted this week of launching a complex phishing attack that allowed him to steal the login credentials of a defense contractor employee, who was responsible for communicating with the Pentagon using a government system, to break in and redirect $23.5 million in federal funds to a bank account that he owned. The money was meant for supplying jet fuel to troops in southeast Asia. (So, did he not think the government wouldn't notice when their jet fuel didn't turn up?) Still, a good lesson for network defenders. More from Bleeping Computer, and the Justice Department's own presser.
India's new super app has a privacy problem
Wired ($): How much would it completely upend your day if you logged into a new app for the first time and all of your personal data was already there? That's what happened to many in India who signed up to Tata Neu, the country's latest do-everything app. The app is run by the Tata Group, one of India's largest conglomerates and a regular household name, which has amassed so much personal information — in large part because India has incredibly lax privacy rules.
~ ~
OTHER NEWSY NUGGETS
Google drops IOCs on threat activity in eastern Europe: Google's TAG has a new blog post with new indicators of compromise for a range of threat actors operating in Eastern Europe using the war in Ukraine as a lure. Russia's APT28 or Fancy Bear gets a mention, as does Turla and Ghostwriter, a Belarusian group with links to Moscow, as well as an espionage group operating out of China.
U.S. planning significant sanctions on Hikvision: According to the Financial Times ($), the U.S. is close to imposing new sanctions on Hikvision, the China-based video surveillance equipment maker accused of supplying its technology to detention camps in Xinjiang, which Beijing uses to oppress the largely-Uyghur population. The new sanctions would put Hikvision on the same "specially designated nationals" list as terrorists and drug traffickers and would make it near-impossible for U.S. and other Western countries to do business with Hikvision. Last month I spoke with a Kyrgyz man and a former Xinjiang prisoner, who gave a first-hand account of the use of Hikvision's technology in the camps. Washington is already in discussions about the sanctions with allies, per Reuters ($).
Big tech teams up on passwordless tech: Of the few things that Silicon Valley can get behind, a future without passwords is one of them. Google, Apple and Microsoft said this week (via ZDNet) that they will build passwordless support into their devices and platforms. "This means that, sooner or later, you won't need a password to log into devices, websites or applications. Instead, your phone will store a FIDO credential called a passkey, which is used to unlock your device — and your entire online account."
Ikea Canada hit by data breach, instructions unclear: An employee of Ikea Canada compromised a database of 95,000 Canadian customers, according to Dark Reading, by performing unsanctioned searches over a period of three days in early March. Ikea confirmed the breach and said that personally identifiable information was compromised — including names, email addresses, phone numbers and postal codes — but that banking information was not included.
~ ~
THE HAPPY CORNER
Welcome to the happy corner. For those considering a career move, @marciahofmann has you covered with a solid updating thread of internet-savvy legal jobs. Some great organizations in this list.
Meanwhile: May the Fourth be with you, and May the Fifth you have strong unique passwords at an absolute baseline minimum. Speaking of:
And finally. Spare a thought (or don't, I'm not your dad) for the hapless scammer who accidentally infected their own machine with spyware and doxxed themselves. According to Malwarebytes which did the research, "We don’t know exactly how, but the attacker managed to infect his own machine." Brilliant.
To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's cyber cat dog is Eddie. Some say the sand on his nose has such high entropy that it can produce truly random numbers, but Eddie doesn't mind so long as you boop his snoot. Many thanks to Ben F. for the submission!

Send in your cyber cats (and their friends)! Drop me an email here with their name and photo, and they'll be featured in an upcoming newsletter soon!
~ ~
SUGGESTION BOX
That's it from me this week. Thanks so much for reading. As always, the suggestion box is open or feel free to email me with any feedback you have. I'll be back next Sunday with the usual round-up from the week. Be good to yourself and to one another.
Until next week.
—@zackwhittaker