this week in security — november 10 2024 edition
THIS WEEK, TL;DR
Canada arrests man suspected of Snowflake data breaches
Bloomberg ($): We are starting this week in Canada, where authorities arrested a man of alleged involvement in the customer data breaches at cloud computing giant Snowflake. Much of the breaches rested on Snowflake's customers not using MFA — or Snowflake mandating its customers use MFA. That was a problem, because all the hacker (or hackers, plural) needed to steal huge amounts of a customer's data was through stolen employee passwords. Some 165 Snowflake customers — think corporate giants — were affected, including AT&T, Ticketmaster, and others. Much of the data was held for ransom, and some of the companies allegedly paid (again, AT&T). The arrested suspect is understood to be still in Canada under a provisional arrest warrant, and held in custody. Expect more to come on this in the coming week or so, as we'll likely understand more about the chief suspect and the wider group of cybercriminals behind these hacks.
More: 404 Media ($) | Wired ($) | Krebs on Security
Chinese 'Typhoon' hacking far more pervasive than previously thought, say sources
ABC News: Hold onto your hats, this one is getting messy. New reporting this week suggests the FBI is investigating whether China used its access to the wiretap systems of U.S. internet and phone providers to hack into the phones of high-profile Americans, including politicians, using malware (or spyware). Forbes ($) is also reporting similarly. If so, that's a major escalation of access to wiretap systems — so, unencrypted phone calls and text messages were stolen from the telcos themselves — but also that access was potentially used to directly compromise at least one iPhone belonging to a Trump-appointed lawyer. Exactly how remains unknown, but it's clear that this is a fast moving and developing story, linked to the "Typhoon" family of Chinese hackers. The Chinese access could easily affect at least thousands of people across the United States. Or, given that these wiretap systems have broad access to a vast amount of our personal communication records, potentially anyone in the United States. House lawmakers are now in the loop — at least until January, by which — well, pffft, anything could happen.
More: Wall Street Journal ($) | Cyberscoop | @dnvolz
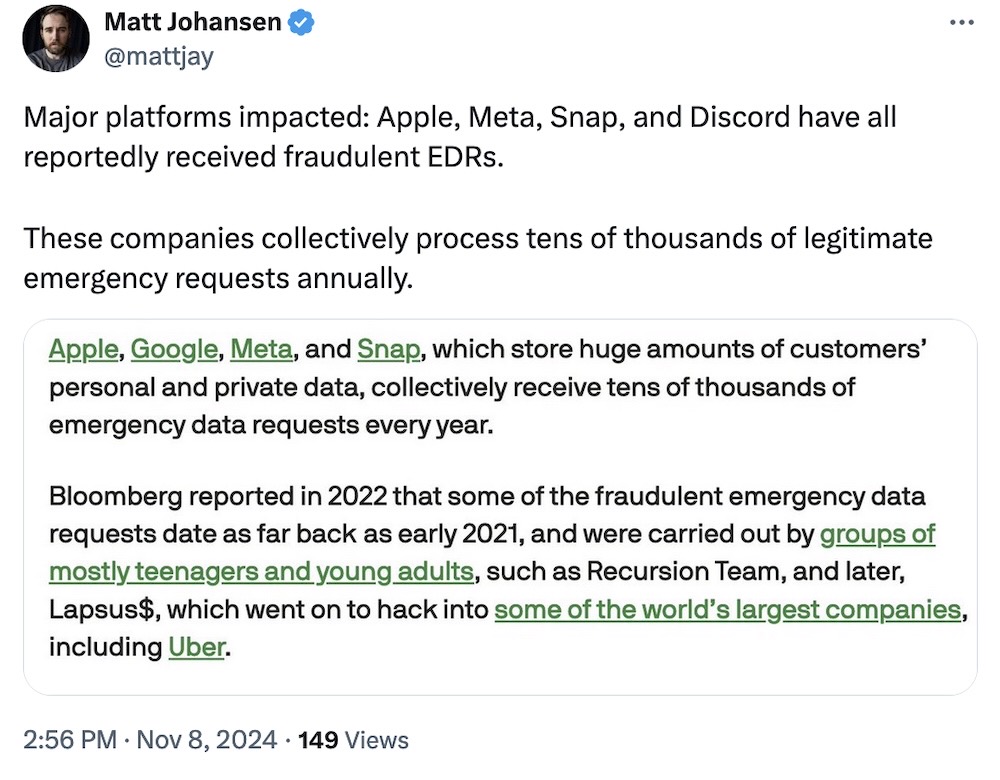
FBI warns of spike in hacked police emails used to send fake subpoenas
Krebs on Security: What's worse than being subpoenaed? Having a fake subpoena sent to a tech company for your personal data. But that's quite literally what's been happening with some crime groups, who have been publicly boasting about their ability to break into the email accounts of law enforcement, government agencies, and police departments (and popping webshells!) to send fraudulent "emergency data requests" (EDRs), which are meant to be used for obtaining user data in exigent circumstances only when there's no time to get a legal order. Equally bad, the tech companies have been tricked into turning over real people's data in response to some of these requests. @briankrebs has been on this story for years, and others, explaining how this scheme works. Now, the FBI has issued a rare admission that the EDR system is flawed and that, while companies must take better care of filtering out fraudulent requests, the police departments have to secure their systems far better as well. Who knew a backdoor could be used for abuse? It's not like the security community hasn't been warning about this for years...
More: TechCrunch | IC3 [DocumentCloud]
Google patches two Android vulnerabilities exploited in targeted attacks
SecurityWeek: Google is warning of "limited, targeted exploitation" of two vulnerabilities targeting Android. The two bugs are designated CVE-2024-43047 (found in Qualcomm chips, which I mentioned last month) and CVE-2024-43093 (an Android software bug in the Android's Framework component). Those fixes are now rolling out, so update as soon as you can. Details about the exploitation isn't yet public, but both Google's Threat Analysis Group and Amnesty International discovered the Qualcomm bug, so there's a greater than zero chance that a commercial spyware vendor may have been behind this exploitation.
More: Android Security | Bleeping Computer | Cyberscoop
~ ~
THE STUFF YOU MIGHT'VE MISSED
An exploration of new macOS sandbox escape vulnerabilities
Mickey Jin: A popular way that malware tries to slip into macOS is by abusing its sandbox escape, which allows the malware to break out of the operating system's protected sandbox to access the user's underlying system, software, and data. Thanks to @patch1t's "attack surface" cheat-sheet, we now have a comprehensive look at the weaknesses in macOS' sandbox protections.
Voted in America? This website doxxed you
404 Media ($): U.S. voter rolls are public, but still highly restricted at the states' level — though not impossible to obtain. One website called VoteRef, set up by a former Trump campaign official, is collating and publishing voters' registration data — including home addresses. This is (as of the time of writing this) entirely legal, because there are few restrictions on U.S. voters' data, and even fewer laws there to protect it. This is a major privacy and security threat, given there's been a rise in political violence of late... and yet just seems to be Yet Another Totally Normal Thing in America™. Politico wrote earlier this year about the states trying to fight against these sorts of sites, yet still failing in the courts.
Canada orders closure of TikTok Canada, citing national security
Government of Canada: The Canadian government has put the kibosh on TikTok Canada, the social media giant's operations in the country, which TikTok's parent, Bytedance — unsurprisingly — isn't happy about, and claims will destroy hundreds of jobs. This isn't a ban on Canadian users accessing TikTok, but the government said the decision to shutter the company's Canadian operations was based on national security. The specific reason wasn't given, because, guess what? National security, wink wink. @mattjay has a good thread on this.
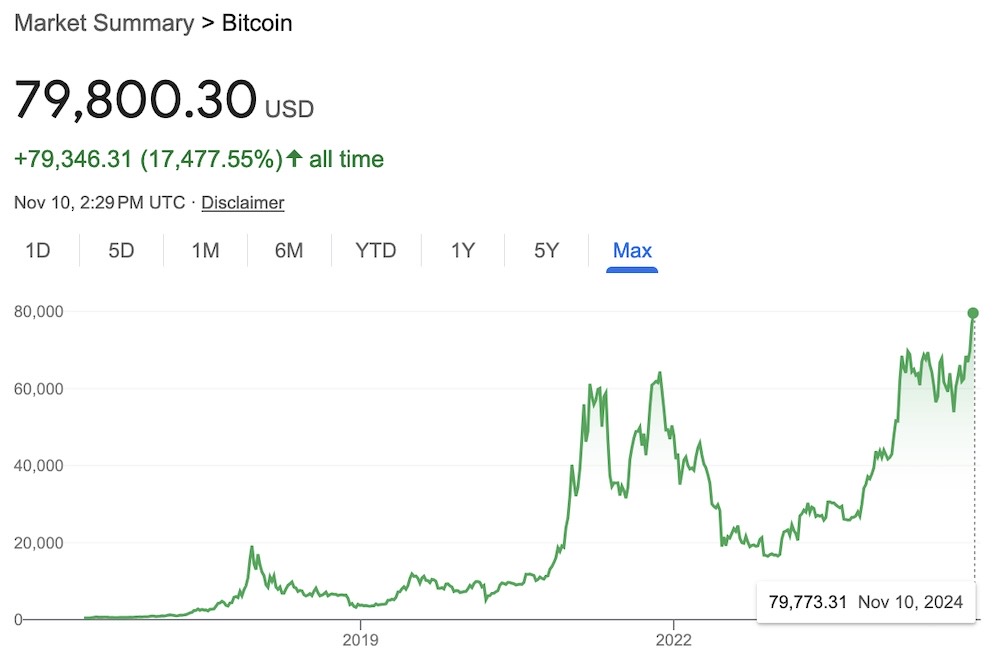
Crypto CEO kidnapped for $1M ransom
CBC: Sticking with Canada for a secon... and what now?! Who needs ransomware when you've just dragged the CEO of a crypto company off the street into your van, and threatened him into paying a $1 million ransom? That's exactly what happened in Toronto during rush hour this Wednesday. The CEO, who runs WonderFi, was released unhurt, and client funds weren't taken. But this is, alarmingly, one of many instances of suspects using physical violence against cryptocurrency owners. The rates of these kinds of incidents tend "to correlate with the exchange rate of bitcoin," per CBC. Huh, so let's go take a look at the price of bitcoi... ah, gotcha.
Cyberattack on Microlise disables prison van and courier vehicle tracking
SecurityWeek: Tracking systems and panic alarms in prison vans and courier vehicles were disabled this week after a cyberattack at Microlise, which provides car and vehicle tracking solutions for fleet operators. The company told the London Stock Exchange that it was making progress in its recovery, but that some employee data was stolen in the cyberattack. (According to London's FT, some prison van crews were "unaware that vehicles were still being used to transport prisoners for three days after the attack despite continuing software faults" — !!) Telematics and vehicle tracking systems — the technologies that tap into a car's data banks — can be a major weak-link in vehicle cybersecurity.
~ ~
OTHER NEWSY NUGGETS
Pirating software? That might be an infostealer: So, let's go back to Snowflake for a hot second. Remember what ultimately caused those massive data breaches? Stolen customer passwords. And how were those passwords stolen? Infostealing malware, or infostealers, which are often bundled in pirated or cracked software. Once installed on a user's computer, the infostealer can siphon and upload the contents of the user's browser password manager and more to the attacker's servers. In some cases, this type of malware can also steal session tokens, which allow hackers to log in as if they were you without needing your password or multi-factor code. @josephcox's reporting digs into the wider cybercriminal ecosystem of stealing and trading stolen credentials. (via Wired ($))
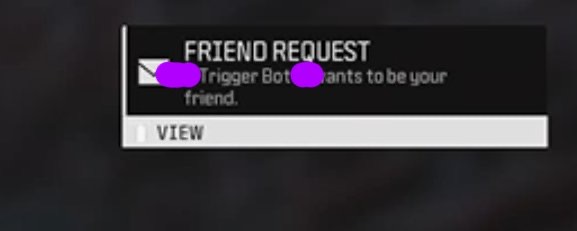
Hack, hack, ban, ban: Activision patched a bug in October that they said affected a "small number" of Call of Duty players who were getting banned seemingly at random. Turns out it was a video game hacker who found a bug in Activision's anti-cheat engine, Ricochet, which allowed the hacker to ban "thousands upon thousands" of players over the past few months by triggering banned keywords, such as those related to cheating (including "Trigger Bot," the name of a popular cheat). Here's a look at how the exploit went down, and a look at the back-and-forth race between game makers and game hackers. (via TechCrunch, @zebleerpo)
Aussie social media law prompts data alarm: Australia has proposed a new law effectively banning under 16s from accessing social media. The move is controversial for a lot of reasons. but from the security point-of-view it's worth noting that enforcement could easily result in age verification checks — and that means collecting lots of data. @ShaneHuntley, one of Google's top security researchers and Aussie native, explains the risks with age verification in the tweets. Collecting historically huge amounts of data hasn't worked out so well for Australia over the past year or so... considering huge data breaches at Medibank, MediSecure, Ticketek, and others... (via NPR, @ShaneHuntley)
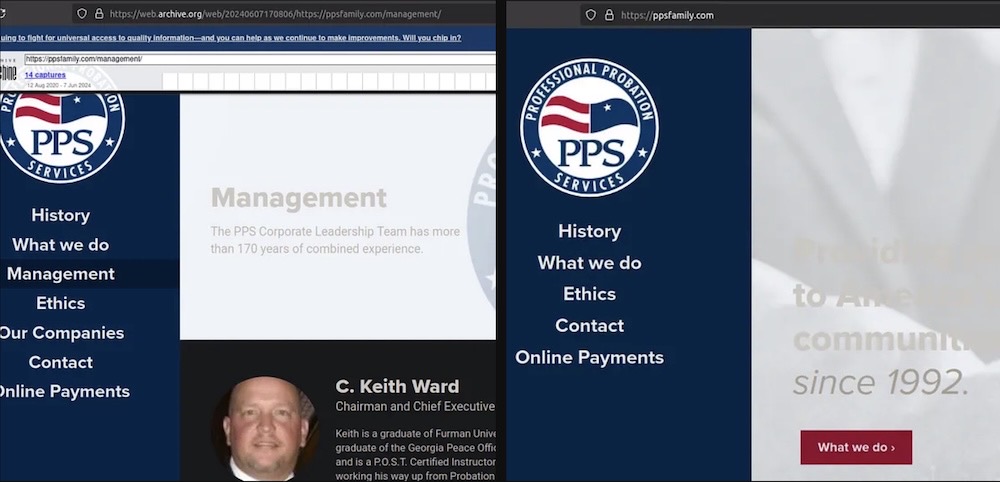
Thousands of probationers' data exposed: Data breach hunter @JayeLTee found a publicly exposed system spilling personal information on close to 500,000 U.S. probationers from a service called Professional Probation Services, a company that claims a "corporate culture of knowing right from wrong, and doing right — every time." The exposed data includes Social Security numbers, email addresses, and more. But, instead of "doing right" and disclosing the incident to those affected, the company appeared to go into "hiding mode," including by removing the CEO's name from the website. Ah, yes, the internet — where everything is forever. Good job there's a copy! (via @JayeLTee)
Soltani, signing off: Ashkan Soltani, the privacy buff who headed California's Privacy Protection Agency, the enforcement arm of California's groundbreaking privacy law, the CCPA, will leave the agency he founded after three years at the helm. Soltani, a former journalist and researcher who covered the Snowden files extensively, said the agency is "well-positioned" to continue leading the state of California — and the wider U.S. — in privacy and consumer protection. Congrats, and thanks, to Soltani. (via Politico Pro ($), @alng)
~ ~
~ ~
THE HAPPY CORNER
For those skipping straight to the happy corner this week, I saved you a spot. Come in. Welcome to everyone, and everyone is welcome.
Kids! If you ask your hacker parents how they spent their time online during the 80s and 90s, prepare for this Glomar response.
Some actionable advice for those on the social webs and wanting to keep your privacy and security in as best shape as you can: Block Party does good work to protect you against online harms before they can strike. The Washington Post ($) has some good yarn on the startup. (via @evacide)
If you, like me and — well, everyone, probably — is concerned about securing your digital data and communications in the wake of the China Typhoon-related hacks, former CISO @boblord has a beginner's guide on what you need to know about securing your phone, messaging and more. From passkeys to using a password manager, these are all good bits of security advice anyway. Encryption is the way to go. Encrypt all the things!
And, finally. I have some words on this to come next week, too, but wanted to share a note by The Verge about the PRESS Act, a press protections bill that was passed by the House in January and waiting for the Senate to take up a vote. The bill, if passed, enshrines federal and nationwide protections for journalists from having to give up their sources, and would replace a patchwork of different state laws across the United States. As someone who's literally had the FBI turn up at their house for doing this job, or for the journalists who had their phone records secretly seized to search for clues about their sources, it's intimidating as hell and all of this can have a real chilling effect on journalism and a free press — something that, as The Verge notes, will become increasingly relevant in a second Trump administration, during which all of the aforementioned happened. The bill has broad bipartisan support, but just needs a vote on the Senate floor. As someone who reads the news — you're reading this newsletter right now! — please, do everyone a huge favor and ask your senator (via the ACLU) to pass the PRESS Act today.
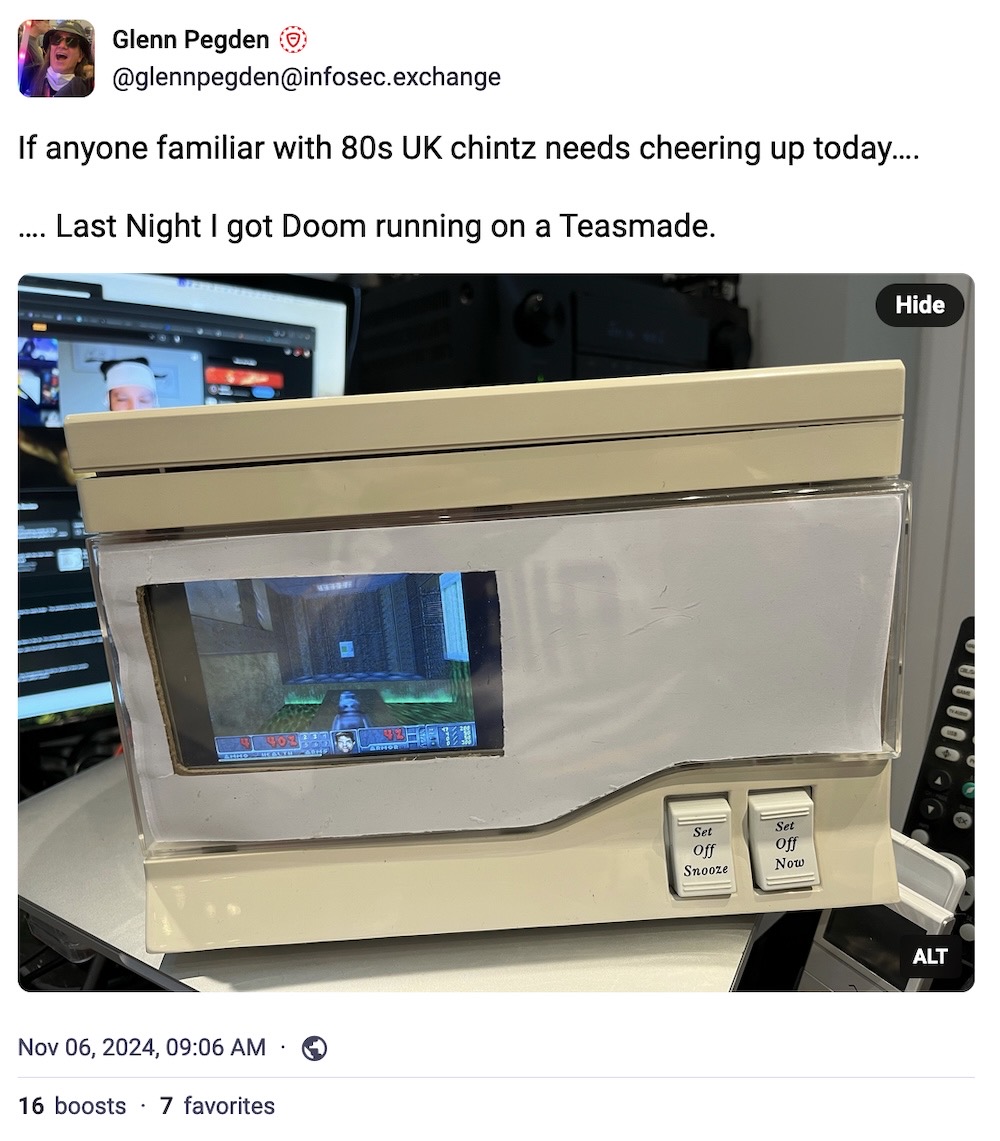
And, your final moment of zen this week. Can it make tea? Can it run Doom? Can it make tea and run Doom? Looks like you've got yourself a hackable teasmade.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat-and-friend special are Pepsi, a 14-year-old kitty (whose human tells me that she recently finished a six-month course of chemo, congrats!) and who occasionally tolerates her dog brother, Toby (who in my opinion is a very huggable and handsome pup). Well, you two are so adorable, and considerably warmed my heart this week. Thanks so much to Sebastian for sending in!

Send in your cyber cats! (or a non-feline friend). You can email any time with a photo with their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's all for this week. Thanks for reading, it really means a lot. I'm sending all my good vibes and love this week, wherever you read this newsletter.
As always, please do reach out if you have any feedback or want to drop anything in the newsletter for the following week. It's always lovely hearing from you, especially when it's a cyber cat (or friend).
Onwards,
@zackwhittaker