this week in security — november 12 edition
THIS WEEK, TL;DR
Lawmakers introduce bill to reauthorize and reform U.S. spy law
Sen. Ron Wyden: With just two months before the end of the year and the long anticipated expiry of a critical U.S. spy law, lawmakers are scrambling to fill the potential void with legislation that aims to reform the country's decades-old surveillance laws. Known under FISA as Section 702, these powers give the FBI, NSA and others access to huge databases of collected intelligence, including Americans, often without needing an individual warrant. Privacy hawk Sen. Ron Wyden (D-OR) and others signed on to a bipartisan and bicameral legislation that aims to reform the law so that U.S. spies can't access Americans' data without a warrant — as well as other reforms called on by privacy and civil liberties groups. The bill is long, but packs in a lot of new protections and is worth the read. The White House got ahead of the bill's introduction with, well, wrong information (whoops), since the bill enforces warrant requirements and nukes backdoor searches, which the U.S. intelligence community has been using (and abusing) over the years. Even though Section 702's powers expire at the end of the year, the FISA Court's year-long certification actually expires months later, so it's not like intelligence ops will immediately cease to function as we enter 2024. But just when we thought we saw progress, it looks like Senate leadership might just extend the damn thing anyway, according to the latest reporting by Wired ($) citing a congressional source.
More: Bloomberg Law ($) | Wired ($) | Roll Call | @johnnysaks130
U.S. service members' data is easy and cheap to buy online
NBC News: Another thing Wyden et al's bill will enforce is a warrant requirement for location data, which would prohibit the U.S. government from buying commercially available data from data brokers (which is already probably illegal). It's actually incredibly easy to buy some of this data online, given a paucity of data protection legislation aimed at preventing the sale of this kind of data. Duke University researchers found they could buy information on thousands of service people for as little as a few cents per person. Clearly this shows data brokers pose a national security threat, as well as a major privacy risk to millions of ordinary people. The U.S. government (and researchers — or anyone it seems) can buy this data and use it for any purpose. This lands in the same week that the FTC accused data broker Kochava of amassing a "staggering" amount of people's sensitive information.
More: Forbes ($) | Politico | @kevincollier | @jshermcyber
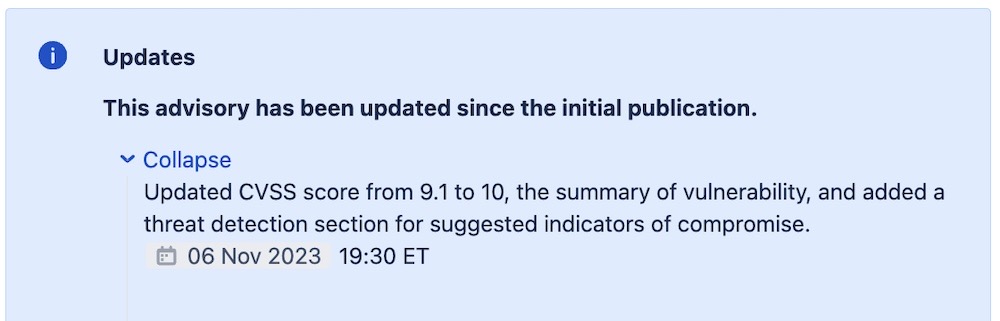
Critical vulnerability in Atlassian Confluence server is under 'mass exploitation'
Ars Technica: A critical improper authorization flaw in Atlassian Confluence is under mass exploitation, according to Rapid7, which has been investigating the bug. The bug, known as CVE-2023-22518, got a bump in vulnerability severity from a 9.1 to a maximum 10.0 after Atlassian realized a "change in the scope of attack." Customers who don't take immediate action could face "significant data loss," given that mass exploitation has begun, @shadowserver data shows.
More: Atlassian | The Register
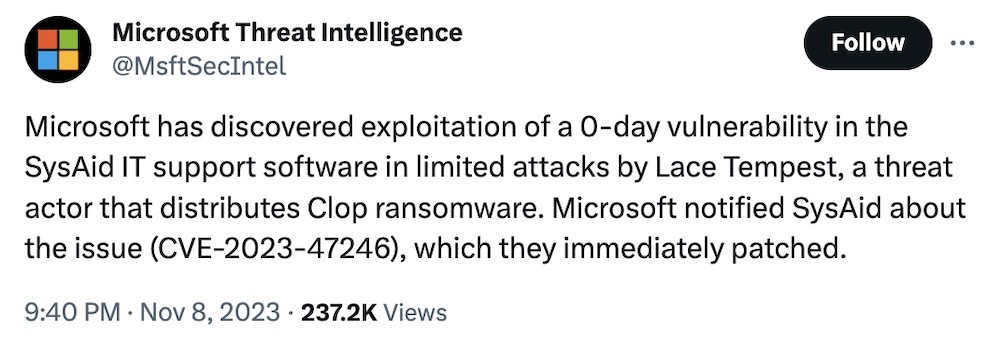
Microsoft says Clop exploiting SysAid zero-day
SysAid: Speaking of things under mass exploitation, customers running IT monitoring tech SysAid should take note. Microsoft's threat intelligence researchers tweeted this week that they've discovered exploitation of a zero-day (ie. no time to fix before it's exploited) in SysAid's software by attackers widely known as the Clop ransomware gang. SysAid published patches for the bug, known as CVE-2023-47246. Rapid7 says that while the company has some 5,000 customers, its searches show about 416 SysAid systems exposed to the internet (at the time of their publication), though it's unclear exactly how many customers are ultimately vulnerable. Clop has a history of mass-hacking and raiding data-heavy systems with zero-days (looking at you MOVEit, Accellion, and Fortra!).
More: Rapid7 | TechCrunch | @msftsecintel
Maine hit by data breach related to MOVEit
Associated Press: Speaking of MOVEit... the biggest mass-hack of the year got worse after the state government of Maine disclosed a breach of 1.3 million people's information. The state said on its incident page that the stolen data varied by individual, but could include names, driver's license numbers, Social Security numbers and some medical and health information. Progress Software, the company that makes the MOVEit file transfer software, disclosed a zero-day back in May, which the Clop ransomware group used to mass-exfiltrate data from thousands of organizations who used the software. Maine is the latest MOVEit customer to fall victim, though a Maine government spokesperson told me that the data was not a one-to-one match for the population (which is also 1.3 million people), given that about 60% of affected people live out of state. To date, the MOVEit breaches affect more than 70 million people, though the number is likely significantly higher as more victim organizations continue to come forward.
More: Maine.gov (incident page) | Emsisoft | Portland Press Herald | TechCrunch
~ ~
THE STUFF YOU MIGHT'VE MISSED
Experts say House speaker's use of porn-monitoring app presents security risks
Washington Post ($): The current speaker of the U.S. House of Representatives is Mike Johnson, whose use of a porn monitoring app (you know where this is going...) called Covenant Eyes is raising security fears. The app monitors' devices for porn and provides reports between "accountability partners," in this case his 17-year-old child. "It scans all the activity on your phone, or your devices, your laptop, tablet, what have you; we do all of it," Johnson said. That's a major problem (and national security headache) for someone who is third in line to the U.S. presidency and a member of the Gang of Eight, who is briefed on sensitive intelligence and national security issues. Last year, @dmehro took a deep dive look at Covenant Eyes and found (for many reasons) that these so-called "shameware" apps are not good. More also from Newsweek.
Sandworm hackers caused Ukraine power blackout during missile strike
Mandiant: Sandworm is back (not that the notorious Russia-backed hacking unit ever went away). Mandiant said in a blog post that Sandworm, known for launching destructive cyberattacks, targeted Ukrainian critical infrastructure in late-2022, which created an unplanned power outage that "coincided with mass missile strikes on critical infrastructure across Ukraine." It's not the first time Sandworm has caused cyber-related power outages, documents Wired ($), whose @agreenberg notes that this is the first combination of digital and physical attacks of this kind.
World's biggest bank traded by USB stick during ransomware attack
CNBC: The Industrial and Commercial Bank of China (ICBC) was hit by ransomware on Thursday ahead of the long weekend in the U.S. for Veterans Day. The New York-based banking giant was likely hit by CitrixBleed, an exploit targeting Citrix NetScaler devices vulnerable to CVE-2023-4966, which was disclosed on October 10. The Russian-linked ransomware gang LockBit was to blame, per Bloomberg ($), which reported that officials had to load trades onto a USB stick and send it through the streets of Manhattan by messenger (I'm not kidding!). It looks like the CitrixBleed bug might have been used to knock one of Australia's biggest port operators (and therefore several Australian ports!) offline. The Australian government's cyber coordinator said it was "responding" to the nationally significant cyber incident. LockBit is on a tear at the moment, targeting law firm Allen & Overy and Boeing.
U.K. may demand tech companies disclose upcoming security features
The Register: The U.K. government continues its anti-security warpath (facial recognition! anti-encryption!) by proposing new powers that would allow lawmakers to intervene and block the rollout of new privacy and security features for messaging apps. The move is thought to be aimed at preventing big tech companies from rolling out end-to-end encryption (which lawmakers wanted to effectively ban recently). The new powers were floated during the King's speech, the government's annual parade of policy ideas read out loud by a man with no role in forming them. The policy announcement naturally caused concern among technology companies. Signal, which repeatedly said it would leave the U.K. if the government compromised its security features, called the proposal "bellicose." So it looks like we're onto Crypto Wars 4: London Edition? I'm losing count.
How the GOP muzzled feds who fought foreign propaganda
NBC News: Filed under "why we can't have nice things," an alliance of federal agencies, tech companies, election officials and researchers that worked together to fight overseas propaganda and disinformation has largely crumbled after "years of sustained Republican attacks," per NBC News. Much of the symbiotic public-private collaboration fought election mis- and disinformation efforts aimed at undermining voting confidence. But since court rulings (which are now pending before the Supreme Court) brought by GOP-aligned attorneys general offices, much of those discussions and efforts have evaporated. The tl;dr from one of the reporters:
~ ~
OTHER NEWSY NUGGETS
Sumo Logic warns customers to rotate keys, doesn't say why: Cloud and IT monitoring giant Sumo Logic told customers in a notice to rotate their API keys after discovering evidence of a security incident. "The activity identified used a compromised credential to access a Sumo Logic AWS account," Sumo Logic says on its website, without saying more about the incident, instead offering more guidance here. (via Sumo Logic, Bleeping Computer)
Mr. Cooper says customer data 'exposed' during cyberattack: What's increasingly looking like ransomware (though the company refuses to comment outside of its boilerplate public statements), Mr. Cooper now says customer data was exposed during its October 31 cyberattack, though the loan and mortgage giant said it is "still investigating" what was taken. Mr. Cooper has more than four million customers. It's not clear if Mr. Cooper yet knows how many customers are affected. (Disclosure: I wrote this story!) (via TechCrunch, SEC)
Krebs + Stamos + SentinelOne = PinnacleOne: SentinelOne has acquired the Krebs Stamos Group, the cybersecurity consultancy firm set up by former CISA director Chris Krebs and veteran CSO Alex Stamos. The deal resulted in the group's new name, PinnacleOne, even if financial terms of the deal weren't disclosed. (via SentinelOne, @ryanaraine)
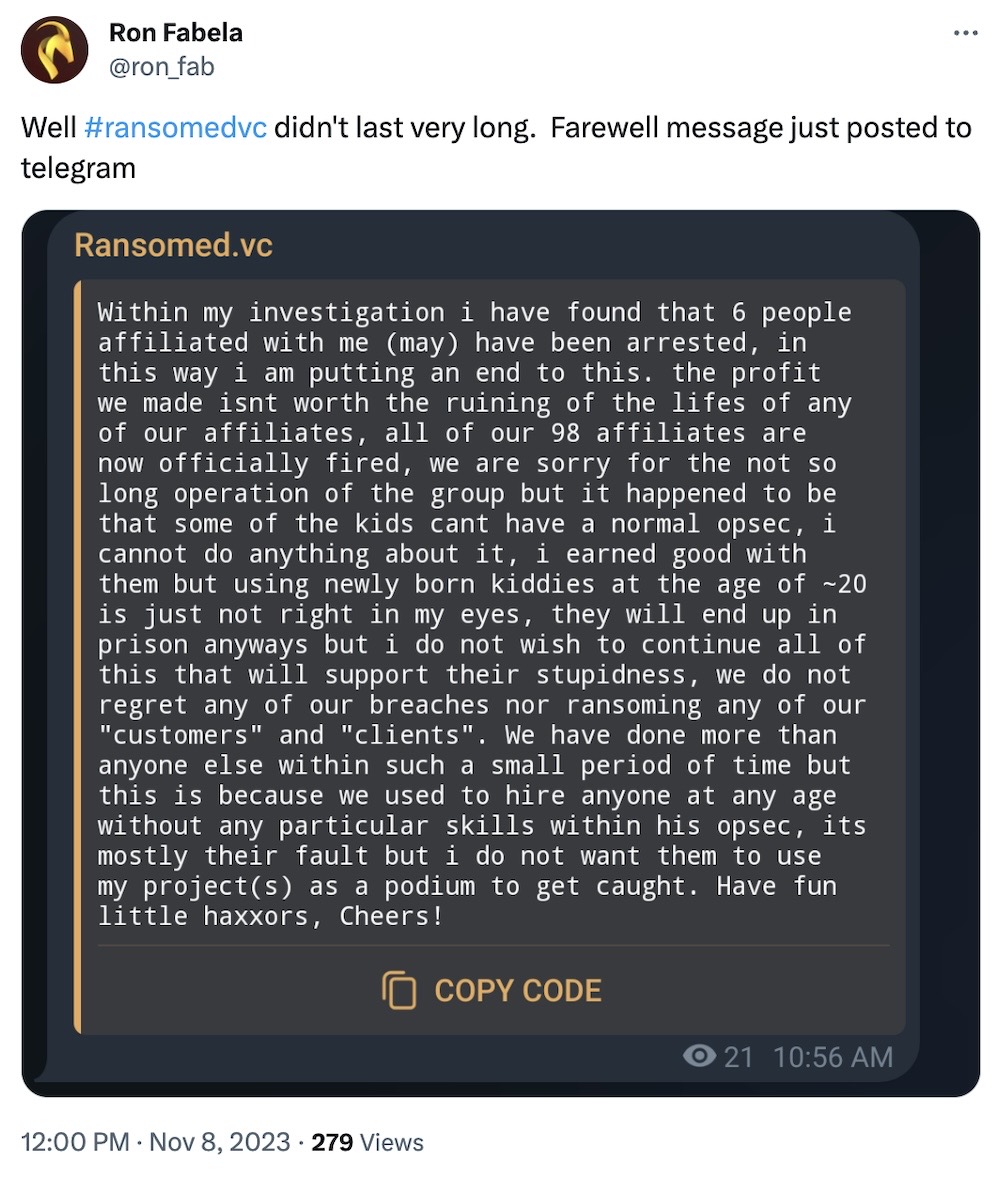
For sale: one shuttered ransomware gang: RansomedVC claimed it was offering itself up for sale, a decision apparently sparked by the arrest of six affiliates in recent weeks. In a since deleted note on Telegram, RansomedVC said it would sell the operation — including its ransomware builder, domain names, and alleged VPN access to 11 breached companies — for about $10 million. The group claimed to properly shut down after nobody bid, even after lowering its price by 20%. As The Register notes, no one wants to buy a ransomware group that has the cops' attention! Just weeks earlier, RansomedVC took credit for a breach of 600,000 lines of U.S. voter data. (via The Register, The Record)
~ ~
THE HAPPY CORNER
Enough news! It's time for the happy corner, and there's always space for everyone.
This week's cyber cat is coming up, but here's a bonus hacker cat, who allegedly* figured out they can knock the wall plug to their electric dry food dispenser and trick it into spitting out food on demand. (*I'm choosing to believe.)

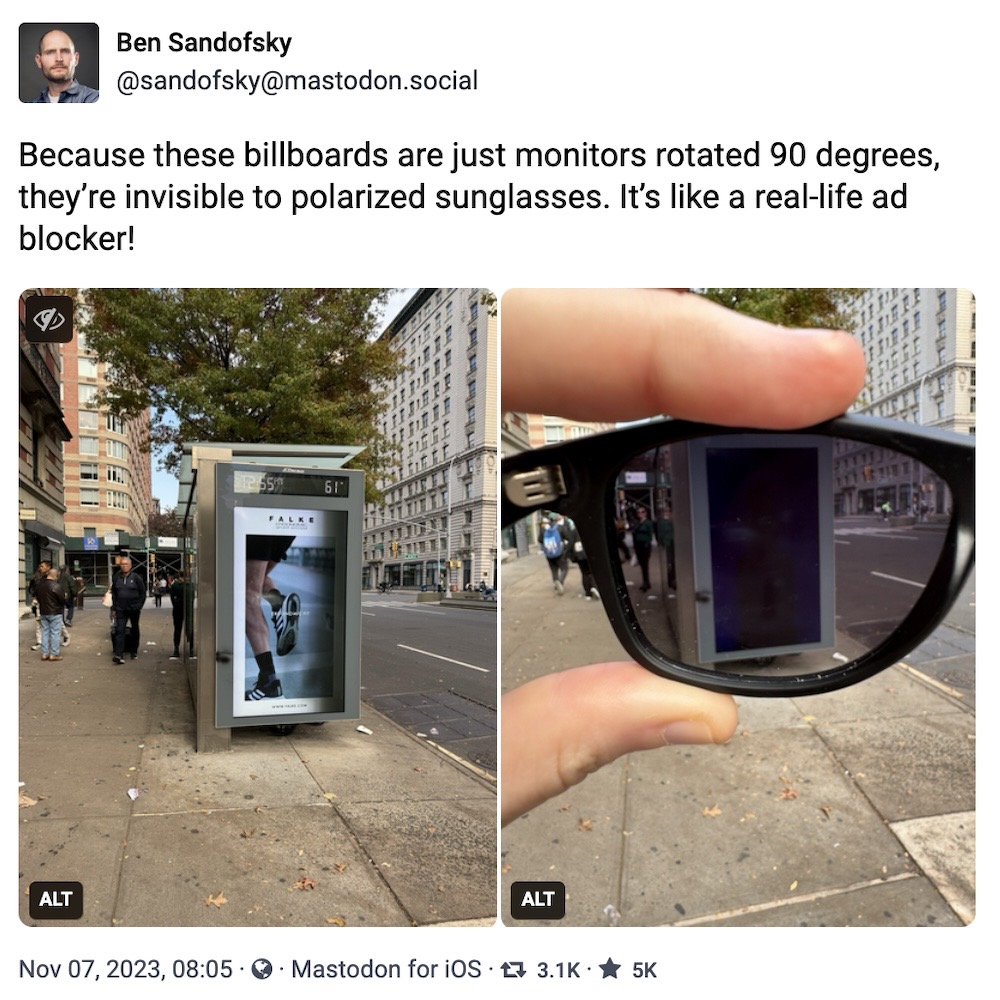
Meanwhile, check out these real-world ad blockers.
And finally this week, a small nugget of good news: Apple will soon introduce a new security feature in iMessage called contact key verification. It's a feature in many other messaging apps (including Signal and WhatsApp) that notifies users when they move or switch devices, which could indicate an adversary-in-the-middle situation. There's a more detailed blog by Tidbits, which is worth the read. One of the reasons why this is a good move is because Apple centralizes its iMessage key server, so users might never know if iMessage had been exploited (maliciously or via top secret court order), which Apple hints at in a blog post. The feature lands in iOS 17.2 and macOS 14.2, which'll be out later this year. (via @glennf)
![A screenshot of an iMessage conversation, which warns, "An unrecognized device may have been added to [recipient's] account."](https://this.weekinsecurity.com/content/images/scraped_images/b658f663-cb1f-e4a4-6a84-a0f474e98615.jpeg)
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~

~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Marsha, who keeps careful watch over the entire neighborhood and shares good security advice with everyone. Practice regular patching and multi-factor all the things! Many thanks to Leroy T. for sending in!

Keep sending in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with their name and photo and they'll feature in an upcoming newsletter.
~ ~
SUGGESTION BOX
An incredibly busy one, hope you enjoyed this week's super-packed newsletter! I'll be back as usual next Sunday with your usual roundup. And you can always drop me an email any time with any feedback (or cyber cats!).
Hope you have a peaceful Veterans Day weekend. And for those who celebrate, a happy Diwali to all.
Until next time,
@zackwhittaker