this week in security — november 17 2024 edition
THIS WEEK, TL;DR
U.S. unseals charges against hacker of Snowflake's customers
Krebs on Security: U.S. prosecutors have (finally) unsealed the charges against two hackers, John Erin Binns (in Turkey, so don't expect an extradition any time soon), and Connor Riley Moucka, in Canada. The duo are accused of carrying out some of the biggest data breaches of the past year by hacking into customer accounts of cloud giant Snowflake between November 2023 and October 2024. All of this was possible thanks to breached passwords and no MFA on the Snowflake accounts. Krebs, expectedly, has the full background on the hacking duo. Binns and Moucka allegedly extorted some of the companies they stole data from, including AT&T, which had an eye-watering 50 billion (yes, with a 'b') customer call and text records stolen. The hacks also affected Santander, Ticketmaster, and around 165 other companies — many of which haven't publicly disclosed their breaches (yet). This might be the end of the road for these hackers (for now), but there's likely a lot more to come from these mass-hacks.
More: 404 Media ($) | Bloomberg ($) | TechCrunch
Incoming Trump administration urged to focus on China, ransomware
Cyberscoop: There are a few updates to note in the world of politics as it pertains to cyber. Top White House official and U.S. cyber advisor Anne Neuberger urged the incoming Trump administration to keep focusing on China, amid the ongoing intrusions by Chinese hackers into U.S. phone and internet giants (more on that later), and, of course, ransomware. Cyberscoop looks ahead, and The Record also digs into what's to come. Ransomware is a major problem that's still getting worse, but relies largely on Russia finally deciding to do something about the problem within its own borders. (We can hope! But quick vibes check: probably not.) Meanwhile, we'll likely see cybersecurity deregulation — with CISA as a potential early casualty, despite the good it's done. And, expect to see the rolling back (or dwindling) of spyware proliferation efforts, per Wired ($). Oh, and Tulsi Gabbard may well be the next chief spy of the United States. Make of that what you will.
More: Wired ($) | TechCrunch | BankInfoSecurity | @kaitlancollins
How to protect yourself from government surveillance
Wired ($): Trump has promised to jail his enemies and deport millions of people, and Wired has published a detailed, thorough guide looking at the ways to protect yourself from ongoing (and future) government surveillance. All of this matters more than ever. Just this week, Trump's incoming border czar said he plans to use AI to aid deportations. Some supporters of this have suggested the government could "comb through millions of records of immigrants" to meet Trump's deportation goals. And given that the U.S. government can simply buy your location data without needing a warrant, it's going to be easier than ever for the government to identify people (either wrongly or arbitrarily) using the data that we all leave as a trail behind us. It's not too late to protect yourself, but like anything in cybersecurity, think of it as an investment in something you hope ultimately never happens.
More: 404 Media ($) | Politico Pro ($)
Palo Alto Networks confirms new zero-day under attack affects its firewalls
SecurityWeek: It's a day ending in "y," so of course there's a brand new zero-day under exploitation in *checks notes*... a cybersecurity company's own security product. Palo Alto initially said there was no evidence of exploitation of its firewall management software, only to about-face soon after. The security advisory confirmed it found hackers exploiting the "unauthenticated" bug (so no passwords or keys needed to take advantage). CISA added the bug to its running list of known-exploited bugs and ordered federal agencies to secure any systems within three weeks, but no details yet on exactly who's carrying out the attacks. These so-called "edge" devices are the bane of some network defenders' lives, and no wonder, when some of these products seem to cause more hassle than not.
More: Palo Alto Networks | Cyberscoop | Bleeping Computer
~ ~
THE STUFF YOU MIGHT'VE MISSED
Researchers warn of critical bug in Citrix Session Recording
watchTowr Labs: The folks at watchTowr Labs say they have found unauthenticated RCE bugs (think remotely running malicious code) in Citrix Session Recording, which captures all of the user's activity when using Citrix's products. Citrix has an advisory out, and disputes that no authentication is needed. But, security researchers called that out as bunk, since some organizations are still deploying their instances over the internet without authentication. The friendly folks at @Shadowserver urge folks to update as hackers attempt to exploit the bug. Some good yarn from Cybersecurity Dive, too.
North Korean-linked hackers caught experimenting with new macOS malware
Cyberscoop: Security researchers at Jamf [PDF] say they've found malware embedded in macOS applications using Flutter, which heavily obfuscates code, and that the malware appeared as clean when uploaded to mass anti-virus scanner, VirusTotal. It's not known if the malware was used in attacks, but was capable of bypassing Apple's notarization process, which checks if code is free from malware. Good intel to know if you're a Mac organization.
Hacking hackers with a fake ransomware builder
Cristian Cornea / Medium ($): ...and on that note, a good reminder that code on the internet is not always safe! One security researcher packaged up a fake ransomware builder as a secret honeypot and advertised the builder on a known cybercrime forum. The researcher found over 100 hackers used their ransomware builder, which allowed the researcher to identify what the hackers were doing and targeting.
~ ~
~ ~
OTHER NEWSY NUGGETS
T-Mobile's ninth recent hack: Pour one out for T-Mobile (or don't) for its ninth cyberattack since 2018. This time, the Chinese hackers known as Salt Typhoon, which've been breaking into phone and internet giants to target their wiretap systems, have also compromised T-Mobile. The telco didn't say much, only that its systems have "not been impacted in any significant way." (What does "significant" mean? I asked...) T-Mobile is the latest company affected; AT&T, Verizon and Lumen were also compromised, with the hackers targeting call and text logs of high-profile Americans, including U.S. presidential candidates. (via Wall Street Journal ($))
MOVEit like it's 2023: Remember the MOVEit data breaches from last year? A bug in Progress Software's file transfer tool allowed the Clop ransomware gang to mass-hack hundreds of companies that store gobs of data in their MOVEit servers. That includes Amazon, which this week confirmed — more than a year on — that the hackers stole employee information stored in Amazon's MOVEit instance. An individual on a known hacking forum claimed to have 2.8 million lines of Amazon employee data stolen in the breach. (Ah, it's the data breach gift that keeps on giving, I say with as much sarcasm as you'd expect from me). @vxunderground says no customer data seen just yet, but that may change. So far, it looks like it was mostly HR and other internal company information. HSBC and others also reportedly had data taken. (via TechCrunch, 404 Media ($))
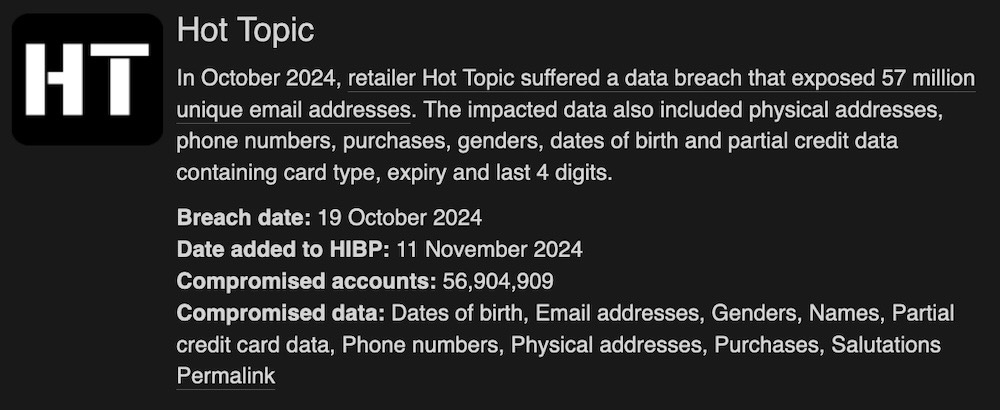
Hot Topic hacked: Data breach notification site Have I Been Pwned alerted some 57 million customers of clothing and merchandise site Hot Topic that they had data stolen in a recent data breach. It looks like its sister brands, Box Lunch and Torrid, may also be affected. The stolen data includes names, dates of birth, phone numbers, physical addresses, purchase history, and partial credit card data. Hot Topic hasn't commented on the breach. Let's hope it answers the regulators' questions, then. (via Bleeping Computer, @haveibeenpwned)
Discord leaker gets 15 years: Jack Teixeira, the former member of the Massachusetts Air National Guard, was sentenced to 15 years in prison for leaking and publishing several classified military documents about the war in Ukraine on Discord last year. The whole case of leaking classified documents had U.S. officials scrambling after learning that the files had been circulating online for several months before they were discovered. (via Associated Press)
November's Patch Tuesday fixes two zero-days: Microsoft has patched two actively exploited zero-days, including a bug in Windows Task Scheduler tracked as CVE-2024-49039, discovered by Google's Threat Analysis Group (which finds government-backed threats — so this could be an indicator of commercial spyware or the like). A separate spoofing bug tracked as CVE-2024-43451 can reveal NTLMv2 hashes, if exploited. More details from SANS' ISC. (via Krebs on Security)
NSO, not its customers, operated Pegasus: An ongoing legal case launched by WhatsApp, which sued Pegasus spyware maker NSO Group for deploying its spyware against thousands of WhatsApp users, saw a raft of sworn depositions unsealed this week. One revelation includes an NSO employee stating that NSO does in fact operate its spyware, not its government customers, despite the spyware maker long claiming it doesn't know who its clients are targeting. Another is that NSO cut off 10 government customers in recent years for abusing Pegasus (which, I know, seems like an entirely redundant statement, but alas, here we are). (via TechCrunch, The Guardian)
~ ~
THE HAPPY CORNER
And breeeeathe. This is the short-and-sweet happy corner.
There's not much this week. Top of mind was this novel way of reading the license terms that you'd otherwise never think about.

Let's check in with Inspirational Skeletor, who in times like these, still has our collective backs.

And, for a moment of peace: If you have decided to finally take the leap from The Site Formerly Known as Twitter™, load up this beautiful (and dare I say, relaxing) Bluesky data visualization and enjoy disassociating from reality for a few.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Kiki, who can be seen here brushing up on her chomping hacking techniques. Thanks so much to Alice B. for sending in!


Keep sending in your cyber cats (or a non-feline friend!). Feel free to email any time with a photo with their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's as much as I can find this week; there's a few things to keep an eye out for next week, including potentially more on the Snowflake indictment, and the ongoing fallout left behind by Salt Typhoon. We're also heading into the holiday season, and that's a busy time for network defenders...
In the meantime, please do reach out with anything if you ever want to get in touch about the newsletter. Sending good vibes to everyone.
Peace,
@zackwhittaker