this week in security — november 19 edition
THIS WEEK, TL;DR
LockBit ransomware gang using CitrixBleed to hack banks and governments
Double Pulsar ($): It feels like this week was a million years long, it's because it was! Welcome to the newsletter, it's a chunky one. Let's start with CitrixBleed, the bug in Cisco Netscaler appliances under active mass-exploitation — and wow, the number of hacked organizations keeps growing. Area security porg @GossiTheDog has a blog post tracking ransomware attacks by LockBit, who are exploiting the bug. "The cybersecurity reality we live in now is teenagers are running around in organised crime gangs with digital bazookas," writes Beaumont in the blog. Yes, teenagers, and some of you(!) are not taking them seriously. "They probably have a better asset inventory of your network than you, and they don’t have to wait four weeks for 38 people to approve a change request for patching one thing." It's pretty spot on, given some of the world's most powerful companies seemingly can't be bothered to patch. Boeing, an international law firm, the world's biggest bank ICBC, and several Australian ports were knocked offline in recent days, all linked to CitrixBleed, which was patched a month ago. Ars Technica has a good rundown of the blog for the paywalled. CitrixBleed is incredibly easy to exploit, and, of course, the victims are paying ransoms because it's the easiest thing for them to do.
More: CISA | Wall Street Journal ($) | Bleeping Computer | TechCrunch
FBI struggled to disrupt dangerous casino hacking gang, cyber responders say
Reuters ($): Speaking of teenagers... let's talk about the ones who recently hacked into MGM (and Caesars, which they've previously denied). The FBI reportedly has "known the identities of at least a dozen members" tied to the hacking group that broke into the Las Vegas casino giants. The group, called Scattered Spider (aka StarFraud), is believed to be in Western countries, including the United States, and typically use Discord and Telegram to coordinate their hacks. With links to a wider community dubbed "the Com," the group uses intimidation and threats of violence to get access to victim organizations' networks. Why the FBI haven't pounced remains an open question. "I would love for somebody to explain it to me," said Crowdstrike president Michael Sentonas, who described law enforcement's lack of response as a "failure" (welp). In a call with reporters this week, a FBI official said on background (which means they can be quoted but not named) said, stroppily, “Just because you don’t see actions being taken, it doesn’t mean there aren’t actions being taken”.
More: CISA | Cyberscoop | @Bing_Chris | @jkirk
Postmeds data breach affects millions of patients who used telehealth startups
TechCrunch: At least 2.3 million will receive notice that their personal and health information was stolen during a cyberattack earlier this year but only disclosed last week. Postmeds, the company doing business as online pharmacy unicorn Truepill, which fills prescriptions on behalf of other pharmacies and telehealth startups, confirmed a data breach affecting downstream customers. That includes people who used Folx for gender-affirming care, Hims, and other healthcare companies and startups. The data stolen is very sensitive and "presents a huge risk, especially for [the LGBTQIA+] community that stands to lose so much more by having that data compromised," one data breach victim told me. The reality is, a lot of people will be getting notices from Postmeds and have no idea how it got their data (or who shared it). Truepill earlier this month settled with the DEA and "accepted responsibility for operating an unregistered online pharmacy" as well as filling prescriptions written by providers, "who did not have the required licenses," all in violation of federal law. You can see a portion of the data breach letter below. (Disclosure: I co-bylined this story.)
More: TechCrunch | Drug Enforcement Administration | @zackwhittaker

Senate urged not to extend spy law in spending stopgap
Bloomberg Law ($): More than 30 civil liberties and other groups urged Senate majority leader Chuck Schumer to exclude language from a must-pass government spending bill that would have reauthorized the controversial Section 702 (FISA) spy law. The idea was to extend the powers, which are set to expire (for the most part) at the end of 2023. But by tacking on a reauthorization amendment to the must-pass government spending bill, lawmakers wanted to kick the can down the road for more discussions next year (which honestly seems like all they do these days). The pro-privacy crowd, like Sen. Ron Wyden, who introduced a bipartisan and bicameral bill to overhaul Section 702, said they would vote against it. In the end, the bill passed without (as far as I can tell) touching Section 702. The scramble to fix the bill before it expires at the end of the year continues...
More: Brennan Center | Wired ($) | @NoahChauvin
~ ~
THE STUFF YOU MIGHT'VE MISSED
How China targets civil society abroad
Glitch Cat: Digital security expert @runasand has a blog post exploring how China targets civil society overseas using cyber capabilities and intimidation tactics. It follows a 200-plus page Dept. of Defense document [PDF] published in October, which draws attention to China's extensive and growing use of cyber.
Children's tablet has malware and exposes kids’ data, researcher finds
TechCrunch: EFF security researcher Alexis Hancock found that an Android tablet for children — the Dragon Touch KidzPad — that someone bought for her daughter contained preloaded with malware and other sketchy "potentially unwanted programs." The Android tablet was sold on Amazon and had hundreds of reviews, but was subsequently pulled down. Walmart said it had removed the tablet from its shelves. Amazon and Google said they were investigating.
Three young hackers who built Mirai malware finally tell their story
Wired ($): Got a spare hour afternoon? Sit down with a big ol' pot of coffee and work your way through this ~22,000 story by @a_greenberg, who spent a year talking to the three young hackers behind the Mirai malware, which a few years ago briefly broke the internet. From @nixonnixoff, who investigated the hackers back when:
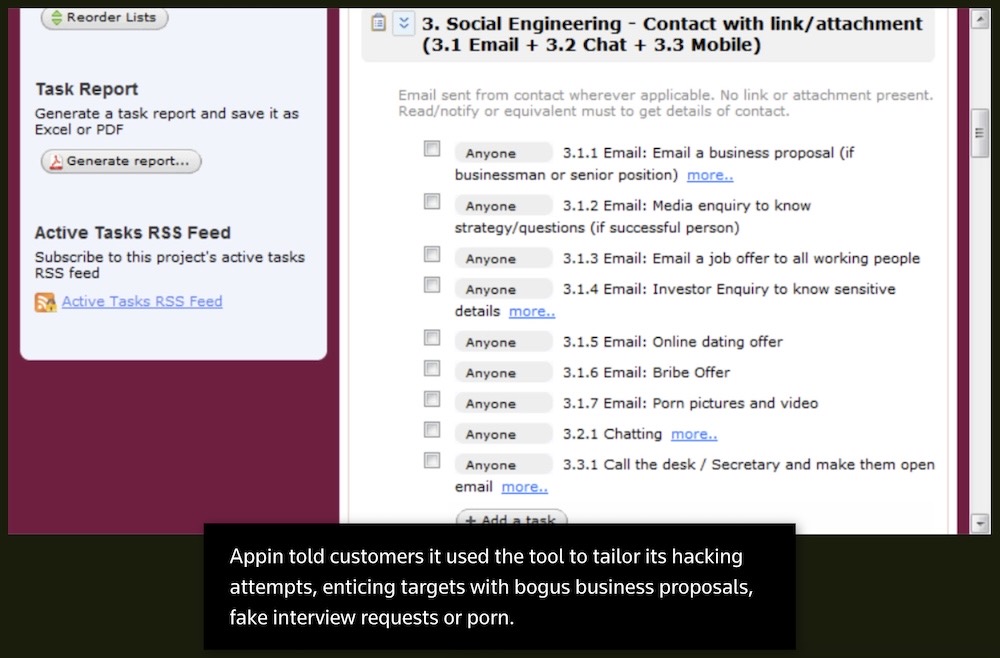
How an Indian startup hacked the world
Reuters ($): And while you're at it, take the time to read Reuters' deep dive into Appin, a notorious hacking-for-hire startup based in India, which was behind targeting some of the world's most powerful people. Just mind-blowingly good reporting here, and they brought receipts (see below). SentinelOne, which worked with Reuters on this story, also has a technical write-up on Appin.
European standards body votes to release secret TETRA algorithms
Zero Day: After the European standards body ETSI faced a barrage of criticism for keeping the decades-old TETRA radio algorithms secret after security researchers reverse-engineered the protocols and found an intentional backdoor, the algorithms will now soon be published. This is a huge win for security research.
Zimbra zero-day used to target international government organizations
Google Threat Analysis Group: Google's elite group of government hacker hunters say they've discovered a Zimbra zero-day in the wild (tracked as CVE-2023-37580) meaning Zimbra had no heads up to fix it. Hackers are actively exploiting the bug by targeting government organizations. The bug is a cross-site scripting (XSS) bug, which if crafted as a malicious link and clicked would allow hackers to extract users' mail data and attachments of a logged-in Zimbra user. The government-backed hackers — some are known and some are not — targeted victims in Greece, Vietnam, Pakistan, Moldova and Tunisia.
~ ~
OTHER NEWSY NUGGETS
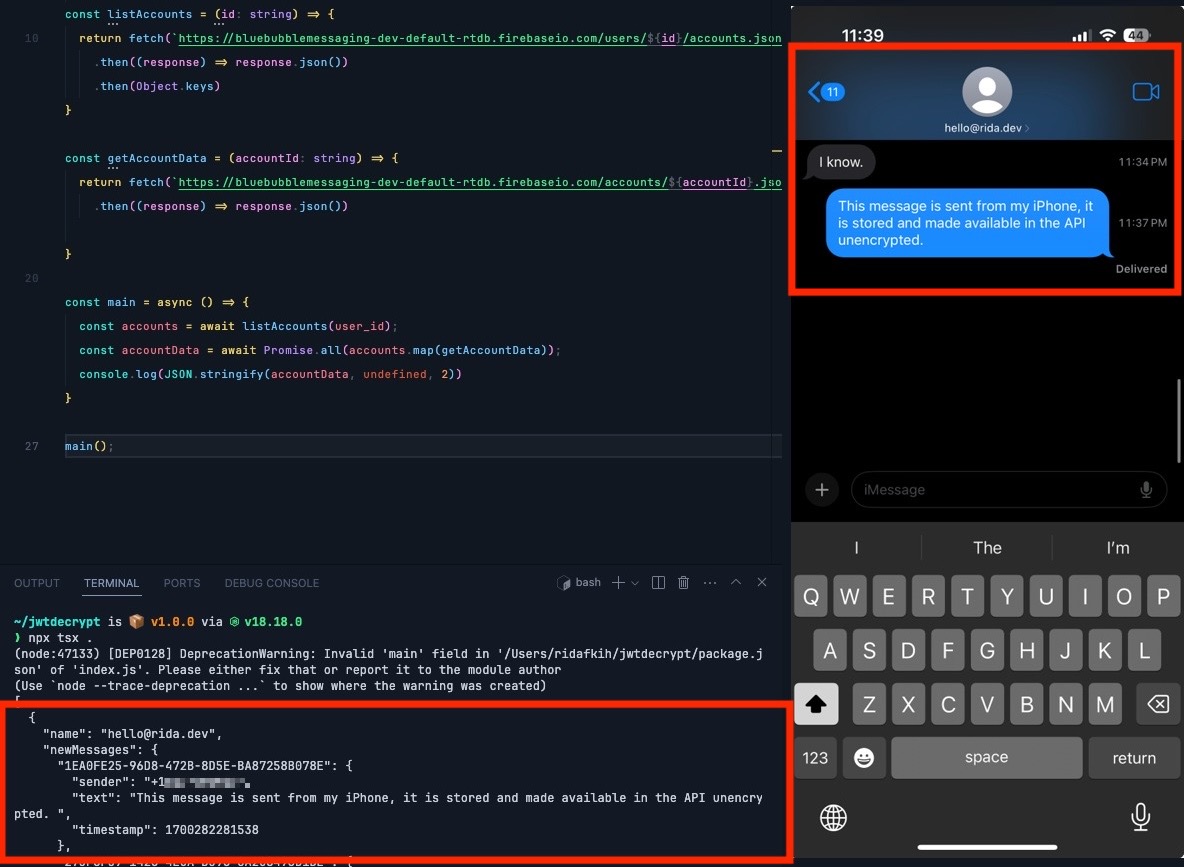
Nothing Chats is a 'privacy nightmare': Device maker Nothing announced this week its new messaging app that turns green bubbles (text messages) into blue bubbles (which implies the messages are end-to-end encrypted, like iMessage). Nothing said it relies on Sunbird, which has long promised iMessage support on Android, and Sunbird claims that its system keeps users' messages confidential and encrypted. Except that isn't true, with researchers finding that Sunbird is a "privacy nightmare" that sends and stores all data "unencrypted on Firebase." 9to5Google independently verified the researchers' findings. Remember, it's not end-to-end encryption if someone sits in the middle... More from Texts, a competitor to Sunbird. (via 9to5Google)
Pre-2016 bitcoin wallets may be at risk: A tech entrepreneur lost his bitcoin wallet password in 2016 and hired a team of hackers to try to break in. The hackers couldn't get the funds back, but did find a bug in the underlying code in BitcoinJS, which was used by a ton of companies to create wallets with random keys. Just one problem: the code wasn't sound and the random keys weren't always random enough. That means that many wallets created before 2016 are vulnerable to weak randomness. The bug is called Randstorm (because why not), and of course it has a fancy website and logo. You can use the Keybleed website to check your wallet's public key for known flaws. (via Washington Post)
Samsung hacked for third time in two years: Electronics giant Samsung admitted that the personal data of U.K.-based customers was taken during a year-long data breach between July 2019 and June 2020 — but was only discovered last week, more than three years later (whoops). Names, phone numbers, postal addresses and email addresses are affected. Samsung revealed it was hacked in 2022 but repeatedly refused to say how many customers were affected, and was hit by a source code data breach months earlier. (via TechCrunch, @troyhunt)
DOJ dismantles IPStorm botnet: Russian-Moldovan national Sergei Makinin pled guilty to three counts of computer hacking over charges he developed and deployed the IPStorm malware and botnet proxy service. Makinin made more than half a million in U.S. dollars from the scheme. The feds dismantled the botnet by disabling the defendant's infrastructure, rather than taking more aggressive steps (as the feds have done before) to mass-disinfect victims' computers. IPStorm infected tens of thousands of internet-connected devices around the world. the DOJ said. (via ABC)
CISA has a plan for weaponized AI: This week, U.S. cybersecurity agency CISA laid out its plans for implementing last month's beefy executive order that established new safety and security standards for generative AI. @CISAJen told Wired that the agency's plan focuses on using AI responsibly — but also aggressively in U.S. digital defense. (via Wired ($), Associated Press)
Reptar bug affects Intel CPUs: If anyone's been wondering what @taviso has been working on of late, he's been breaking most modern CPUs by the sounds of it. Details of the so-called "Reptar" bug (aka CVE-2023-23583) were finally released. The bug affects several Intel desktop, mobile, and server CPUs and can lead to information disclosure or privilege escalation. (via Reptar, Google)
Nine million hit by huge medical data breach: Somehow, the second biggest breach of U.S. medical data in recent years (since at least 2020) was revealed this week — albeit months after it happened — and barely anyone noticed. Some nine million patients had sensitive personal and health data stolen after a little-known U.S. medical transcription firm called Perry Johnson & Associates, or PJ&A, was hacked. Close to nine million patients are affected. That includes about four million patients at New York's largest healthcare system Northwell Health (with some data going back years), and about 1.2 million patients in Illinois' Cook County (which includes most of Chicago.). That leaves about the data of four million patients unaccounted for. Expect more to come on this. (Disclosure: I also wrote this story.) (via TechCrunch)
Medicare data stolen in MOVEit mass-hack: Speaking of major hacks... the biggest hack of this year (thanks to its mass-exploitability) affecting organizations who used MOVEit file transfer tools is now confirmed to affect at least 330,000 current people on Medicare. The Center for Medicare & Medicaid Services, the federal agency which administers the Medicare program, said a ton of sensitive health data was stolen in the breach, including names, Social Security numbers, and medical histories and notes. The Clop ransomware gang previously took credit for the MOVEit mass-hacks, but has long claimed (without evidence) that it deletes the government data it steals. (via CMS)
Another new acting cyber director: The U.S. has a new cyber czar, Drenan Dudley, who is now the new acting national cyber director, after Kemba Walden, the previous acting cyber director, departed the role on Friday. After Chris Inglis departed the role earlier this year, Walden was appointed acting national cyber director, but was passed over as Inglis' replacement in favor of Harry Coker, a former NSA executive whose nomination was approved by a Senate committee this week. A later full Senate vote could land next week. (via The Record)
~ ~
THE HAPPY CORNER
And that's enough news for now (and that was a lot!). Now, relax. It's the happy corner.
Here's some bonus @CISAJen meme game. Share the message, you might just help stop someone getting hacked. Also, always upvote Bob Ross.
And speaking of federal memelords... it's almost time. (If you know, you know.)

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~

~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Tennessee with a reminder that ad-blockers are a great security tool for blocking malvertising and help to protect your privacy online. Tennessee always has your back! Many thanks to Jeri D. for sending in.

Keep sending in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with their name and photo and they'll feature in an upcoming newsletter.
~ ~
SUGGESTION BOX
Well that was a wild one! I'm off to get some breakfast — this edition took a while to write. Next week is Thanksgiving in the U.S., so expect a slowdown in news... or not, who knows!
As always, you can email me any time with your feedback (and your cyber cats!). For those who celebrate, have a wonderful Thanksgiving.
Have a great week,
@zackwhittaker