this week in security — november 24 2024 edition
THIS WEEK, TL;DR
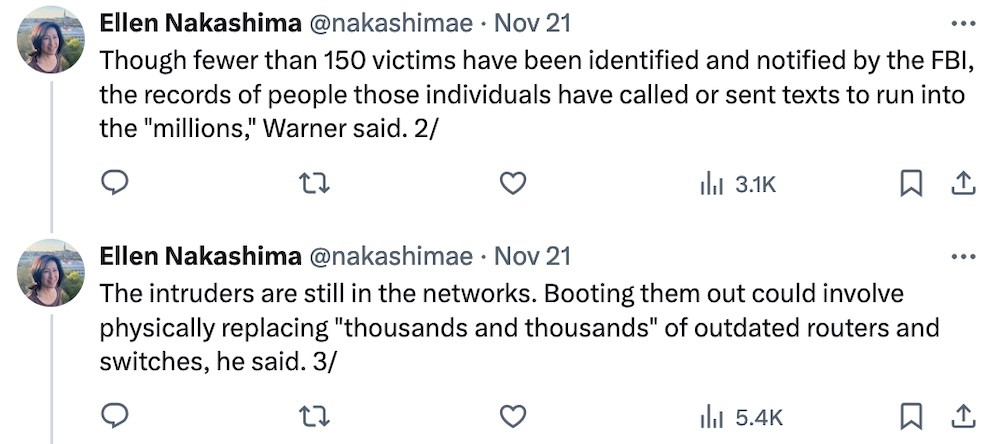
U.S. officials "increasingly concerned" about Chinese hacking U.S. telcos
Washington Post ($): As the U.S. continues to learn new details of the Salt Typhoon hacks targeting U.S. telecom and internet giants, the country's top telco chiefs were summoned to the White House to explain why Chinese hackers were running around their systems, fearing that they could access unencrypted calls and texts on American directly from the wire. Per @nakashimae, Senate intelligence chief Sen. Mark Warner says this is the "worst telecom hack in our nation’s history." The New York Times ($) that the feds were concerned the Chinese might use their access to identify people which authorities may have "repeatedly contacted," such as informants, from FBI phones. Meanwhile, Bloomberg ($) reports the NSA director wants to publicly disclose some of the details of the hacks to help other network giants defend, too. (Makes sense, right?) All the while, let's not forget about the threat from the other Typhoon groups... like Volt Typhoon, the Chinese hacking group that's still prepositioning themselves (per Reuters ($)) in U.S. critical infrastructure to strike in the event of a conflict with the United States over, say, Taiwan, for example. None of this is particularly good, but it's about to be a new administration's headache.
More: New York Times ($) | Reuters ($) | Bloomberg ($) | @nakashimae tweets
'Scattered Spider' hackers arrested by U.S. authorities
Justice Department: It's the end of an era for, well, at least some of the hackers known as "0ktapus," and later, "Scattered Spider," who were... mostly caught in recent months to face justice. The DOJ declared victory this week, claiming the arrests of five "advanced persistent teenagers" of mostly young adults (some of which were teens at the time of the hacks) who were caught mostly thanks to their bad opsec. Krebs on Security digs into the arrests and the hackers, who took credit for hacking DoorDash, LastPass, T-Mobile, Twilio (twice), and others. The hackers, for a time, were so prolific that the FBI and CISA put out a warning, urging corporate giants to shore up their security from these highly skilled social engineers.
More: Reuters ($) | Cyberscoop | TechCrunch | Bleeping Computer
Watchdog says many U.S. water systems exposed to high-risk flaws
The Record: Not great news for U.S. cyber resiliency, where close to a hundred drinking water supplies across the country, serving millions of residents, face "high-risk" vulnerabilities that could cause degradation or a loss in water supplies. A new report by the government watchdog GAO reveals some of the troubles in more detail, with the top-level highlight that absolutely more has to be done across the industry. And not just in the U.S., either. U.K.-based Thames Water, which supplies water across the British capital and further afield, is "falling apart" at the cyber-seams, according to one Thames Water insider speaking to The Guardian as part of a wider investigation into the company's apparently lackluster cybersecurity posture.
More: GAO | BBC News
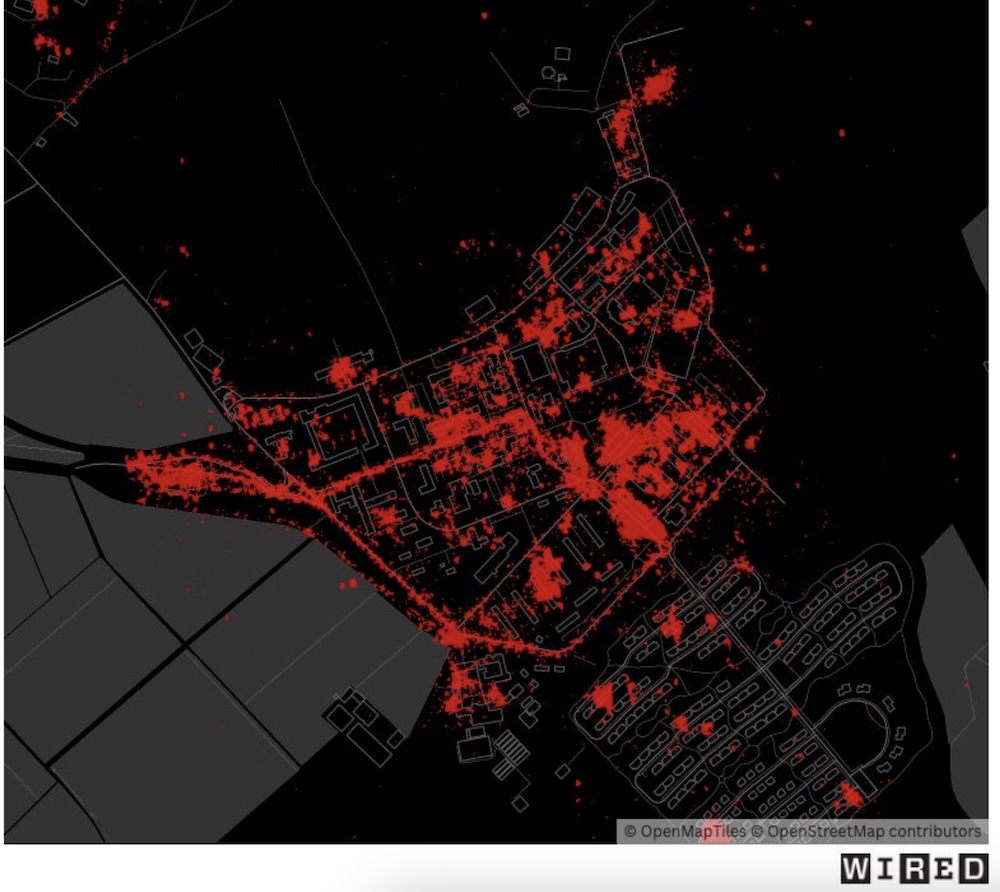
Anyone can buy data tracking U.S. soldiers near nuke vaults in Germany
Wired ($): There are billions (yes, with a "b") of location data points obtained by U.S.-based data brokers that hold huge amounts of sensitive data on where millions of people go at any given time, including who (and where) they interact with. Now, zoom into Wiesbaden, Germany, and you'll see a huge U.S. intelligence gathering hub and, with this location data, also see and track exactly where countless U.S. soldiers and military personnel go all over this base, including nearby to where part of America's nuclear arsenal is stored. Wired, working with a journalism reporting collective, again reveals the danger of data brokers around "sensitive locations," such as military bases. The FTC has long warned against U.S. companies gathering data around sensitive locations, but Wired reports the FTC is "on the verge" of changing its rules, per Ron Wyden's request.
More: Netzpolitik | Bayerischer Rundfunk | @dmehro
~ ~
THE STUFF YOU MIGHT'VE MISSED
Palo Alto Networks warns of firewall zero-days under attack (again)
Unit 42: Of course, there's a new zero-day (but actually two!) in a cybersecurity company's products. This time ...Again it's Palo Alto Networks, and these two bugs can be chained to get unauthenticated access to an affected customer's firewall — and the customer's wider network. The bugs, tracked as CVE-2024-0012 and CVE-2024-9474, are under active exploitation so you might want to patch sooner rather than later. Props to watchTorwr Labs for the great write-up (as usual), and more from TechCrunch.
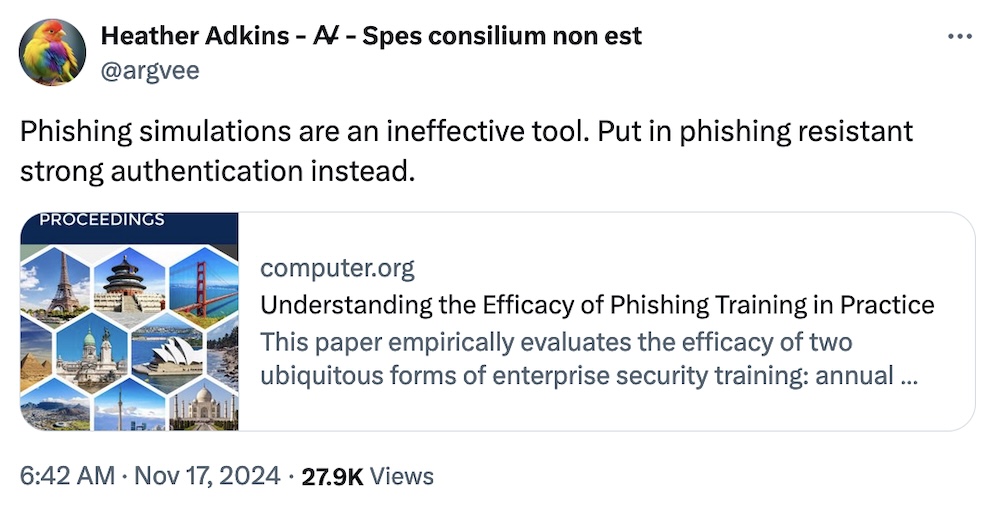
Phishing simulations aren't so effective, academics say
IEEE: Say what you will about email phishing simulations (and plenty of folks have opinions!). Now, academics say that phishing simulations aren't so effective in practice, according to their eight-month controlled experiment, now available to read. "We find no significant relationship between whether users have recently completed cybersecurity awareness training and their likelihood of failing a phishing simulation." The full results are worth reading, but also note that companies — with their resources and riches — should be the ones rolling out phishing-resistant authentication tech, not putting the responsibility on the users flagging could-be-malicious email themselves. Cue Google's top security veep, @argvee:
Leaked docs show what phones 'Graykey' can unlock
404 Media ($): Newly leaked documents show that Graykey, a forensic tool owned by Magnet Forensics that's designed for law enforcement to access locked electronics, can obtain partial data from most modern devices, including iPhones running iOS 18.0.1 and a range of Android devices, including Pixel phones. It comes soon after researchers reverse-engineered a new iPhone security feature that reboots inactive iOS devices after three days, putting it in a "Before First Unlock" state that's more difficult to password-crack.
'Every single person should be worried' about the risk from phone spyware
New Yorker ($): Speaking of spyware... @ronanfarrow has a new documentary and article out about how spyware proliferation (or lack of) will likely fare under the incoming Trump administration. Alarming headline, but interesting read — uncovering fresh details about spyware deals done with the U.S. government in recent years.
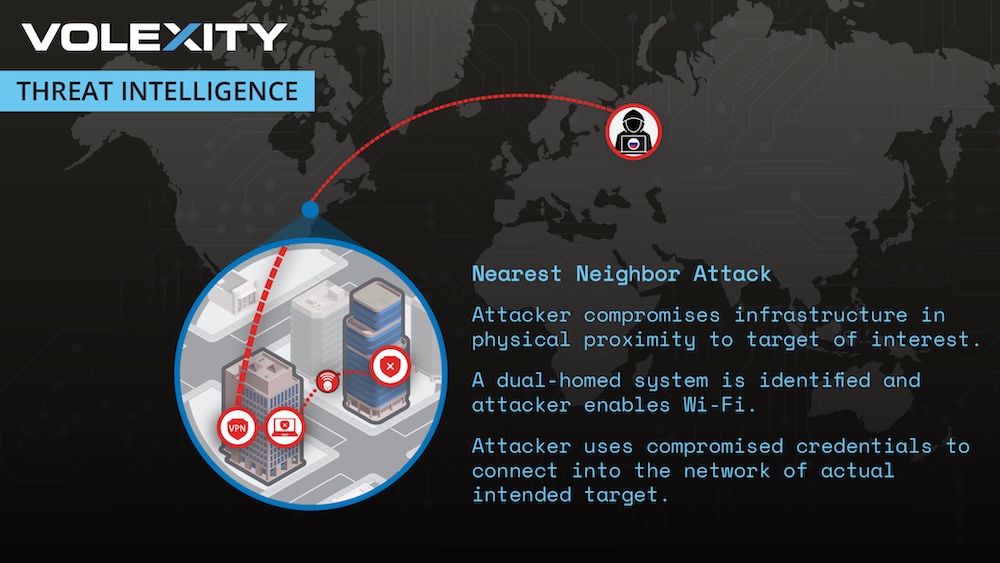
Russia caught hacking company via neighbor's nearby Wi-Fi
Volexity: A fresh new cyberattack hellscape just opened; turns out Russian hackers were tracked compromising one unlucky Washington DC-based organization by tapping into a nearby neighbor's network, then using the Wi-Fi to "hop" to the intended victim's network across the road. Wired ($) has some yarn on the story, which succinctly explains: "Instead of venturing into radio range of their target, they found another vulnerable network in a building across the street, remotely hacked into a laptop in that neighboring building, and used that computer's antenna to break into the Wi-Fi network of their intended victim — a radio-hacking trick that never even required leaving Russian soil.
~ ~
OTHER NEWSY NUGGETS
Apple warns of active Mac hacks: Fruit-themed device maker Apple has warned of active cyberattacks targeting Intel-based Mac users, and has rolled out patches to Mac users — as well as iPhone and iPad owners, fearing that the exploit could also target them. The bugs were discovered by Google's TAG, which investigates government-backed threats, so that gives some clues as to who's behind these Mac attacks. Update your devices today. (via Apple, TechCrunch)
The 'i' in CISO stands for 'insurance': A New Jersey-based insurance company is now offering professional liability insurance to top company cybersecurity officers, including CISOs, to shield from liability. CISOs are increasingly facing regulatory heat for security incidents and data breaches that, frankly, aren't always their fault (thanks to big companies withholding vital security funds from their CISOs!) but yet find these issues ultimately land on them. (via Cyberscoop)
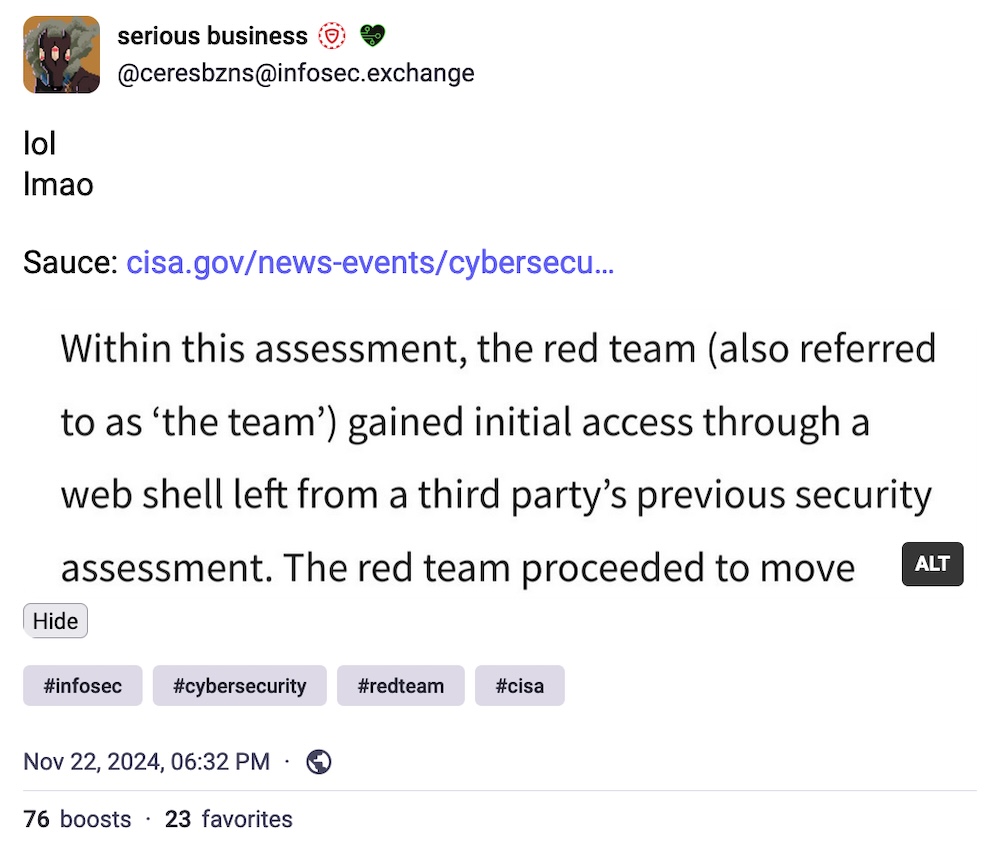
Pop, pop, who's there? CISA's red team: Once in a while, CISA's red team is tasked (with consent!) with breaking into a government agency, or, in this case, a critical infrastructure organization to find and shore up cyber weaknesses. No surprise that CISA's team of offensive hackers broke in with staggering results, but only the more alarming when you find out CISA initially gained access to their target's network because the organization failed to clean up a web shell left behind from a previous red-team engagement. (via CISA)
Finastra hacked: Global financial giant Finastra confirmed it was hacked, after hackers compromised its internal SFTP system using stolen credentials. (It's not clear yet if there was any MFA on this system, but certainly doesn't sound like it). A threat actor reportedly stole 400 gigabytes of data from the system, but Finastra won't say how many customers are affected. For background, Finastra serves 45 out of the world's top 50 banks, so... that's something for sure. Finastra was hit by ransomware in 2020, too, per Bloomberg ($). (via Krebs on Security)
Keep your medical imagery out of AI: I'll say this once in a while, but it's worth repeating. Please, please, please don't upload your medical imagery — X-rays, CAT and PET scans, etc. — to an AI model, even (especially) if a billionaire tells you to. In fact, probably just best to keep these off the internet if at all possible. With AI, what goes in will eventually come out again. (Disclosure: I wrote this!) (via TechCrunch)
~ ~
~ ~
THE HAPPY CORNER
Don't worry, there's plenty of space for everyone here in the happy corner. Welcome to all.
Scammers, beware. The next time you try to trick someone into handing over their passwords or sensitive information, you might be talking to a fake grandma. U.K. phone network O2 built an AI grandma designed to waste the time of scammers by keeping them on the phone for as long as possible. It's a beautifully evil trick. Excellent! (Thanks to Michael T. for sending in!)
Meanwhile, for those thinking of rolling their own crypto... just don't.
Here's a rare opportunity to look inside a roving SMS blaster operation, featuring a car trunk packed with equipment capable of sending a million phishing text messages per hour. Remember, SMS is insecure and should be used for authentication only as a last resort.

And finally, this week: A big thank you to @CISAJen, who is departing cybersecurity agency CISA on January 20 as part of the transfer of government power, after more than three years at the helm. CISA's continued to do incredible work under Easterly's directorship, and as a country the United States is better for it. A true hacker's hacker, all the best to Easterly and her future endeavors. 🫡 (via NextGov)

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This is Dirk who, according to her human, is very sweet and catches tons of mice. And, like a true cyber cat, I bet she snags in the occasional government-backed hacker, too. She's the sunshine to anyone's day. Thanks to Max B. for sending in!

Send in your cyber cats! (or a non-feline friend). You can email them in at any time with a photo, including their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's a bumper edition of the newsletter this week. Thanks for making it all the way through. Next week is Thanksgiving in the U.S. so expect a little lighter on the news... but who knows, we'll see. As for now, enjoy the rest of your Sunday.
As always, please do reach out with anything for the newsletter. It's lovely to hear from you!
'til next time,
@zackwhittaker