this week in security — november 26 edition
THIS WEEK, TL;DR
Secretive U.S. spy program gives cops access to trillions of U.S. phone records
Wired ($): A U.S. senator is demanding answers and challenging the legality of an ongoing and little-known Justice Department surveillance program that tracks over a trillion domestic U.S. phone calls every year. News of the program, dubbed Hemisphere, was first disclosed in 2013 by The New York Times in the midst of (and subsequently somewhat buried by) the Snowden leaks. The Hemisphere program runs largely in coordination with AT&T, which claims it's required by law to comply with a lawful subpoena — but Wired notes there's no law requiring AT&T to store decades' worth of Americans' call records for law enforcement purposes. Sen. Ron Wyden says that "troubling information" he has received about the program "would justifiably outrage many Americans and other members of Congress." As a member of the Senate Intelligence Committee, Wyden knows more than what he can publicly say (aka the Wyden siren). Good that this is being brought up again, and great reporting here. Always read @LizaGoitein on natsec legal matters.
Archive: The New York Times ($) | More: Ron Wyden | EPIC | EFF | @bretthaines
Ukraine fires top cybersecurity officials
TechCrunch: Two of the most senior cybersecurity officials in the Ukrainian government are accused of embezzlement and have been relieved of their positions. Yurii Shchyhol and Victor Zhora, respectively former head and former deputy head of SSSCIP, Ukraine's cybersecurity unit and home of CERT-UA, were dismissed Tuesday. Zhora, a close ally of U.S. cybersecurity agency CISA and known speaker on the cybersecurity circuit, told us in response to a request for comment: "I will defend my name and reputation in a court." CISA didn't say if it was given a heads up or any notice of the surprise firings. As Cyberscoop notes, "It is unclear what impact, if any, Shchyhol and Zhora's firing will have on Western cybersecurity aid to Kyiv," given the ongoing war. (Disclosure: I wrote this story.)
More: Reuters ($) | SSSCIP | Ukraine NABU
~ ~
THE STUFF YOU MIGHT'VE MISSED
Morgan Stanley fined $6.5M for exposing customer data during drive disposal
SecurityWeek: Banking giant Morgan Stanley will pay $6.5 million in a settlement with Florida's attorney general after the multinational exposed millions of customers' data after failing to properly wipe hardware it decommissioned in 2020. It's the latest in a string of actions by state AGs after some 15 million customers' information was found on 42 servers and hard drives, some of which later turned up on auction sites. Morgan Stanley paid $35 million to settle charges with the SEC last year over the same incident.
Microsoft's Windows Hello fingerprint authentication has been bypassed
Blackwing Intelligence: Security researchers say they have found flaws in how laptop manufacturers are implementing their fingerprint authentication technology, which affects how users log into their Windows machines. Laptops from Dell, Lenovo, and even Microsoft have vulnerabilities that were exploited to unlock computers under certain conditions. It's not clear if Microsoft can fix the flaws alone. More from The Verge and @rmhrisk, who was responsible for Windows Biometric Framework.

Tor removes risky relays linked to crypto scheme
Tor Project: The makers and maintainers of the Tor Browser and the Tor anonymity network said it's removed a "large number" of relays — the servers that bounce users' data anonymously around the world — that it says are associated with "high-risk, for-profit" cryptocurrency-related schemes. "We consider these relays to be harmful to the Tor network for a number of reasons, including that certain of the relays do not meet our requirements, and that such financial schemes present a significant threat to the network's integrity and the reputation of our project as they can attract individuals with malicious intent, put users at risk, or disrupt the volunteer-driven spirit that sustains the Tor Community," the project said.
Hundreds of U.K. law firms hit by cyberattack on upstream IT provider
The Record: Keep an eye on this one as we head into the new week: CTS, a managed service provider (MSPs) for law firms across the U.K., said it's "urgently investigating" a cyberattack that's knocked services offline — and left hundreds of British law firms unable to access their case files. It's believed the breach may be linked to the ongoing mega-fustercluck that is CitrixBleed. MSPs, like CTS, are often targets of hackers since they manage gob-loads of data and infrastructure for their clients and customers.
~ ~
OTHER NEWSY NUGGETS
New job, who dis? A North Korean spy? North Koreans are stealing our jobs! New findings by Palo Alto Networks detail the workings of North Korea's remote IT workforce. North Korea has been using its IT workers to get recruited for remote jobs in the U.S. to bring in fundings for its nuclear weapons program (as well as other means, such as crypto heists). Reuters reports that the IT workers use fake names, scripts and resumes to get jobs with Western firms. (via Reuters ($))
Fifth Amendment vs. passcodes: Lawyers at the EFF are asking the Supreme Court to overturn a ruling by the Illinois Supreme Court that they say erroneously ruled that the Fifth Amendment (which protects against self-incrimination) doesn't apply to the compelled entry of passcodes. That's a major problem, they say, because the Fifth can be used to compel the use of something you have (such as a fingerprint or a face scan) to unlock your phone, but can't be used to compel something you know (like a passcode in your head). As yet, there's no way to compel something from someone's head, hence the court's confusing ruling. "Only the Supreme Court can resolve this split," the EFF says. Keep a close eye on this one, as this could be the ruling that determines personal device protections. (via EFF)
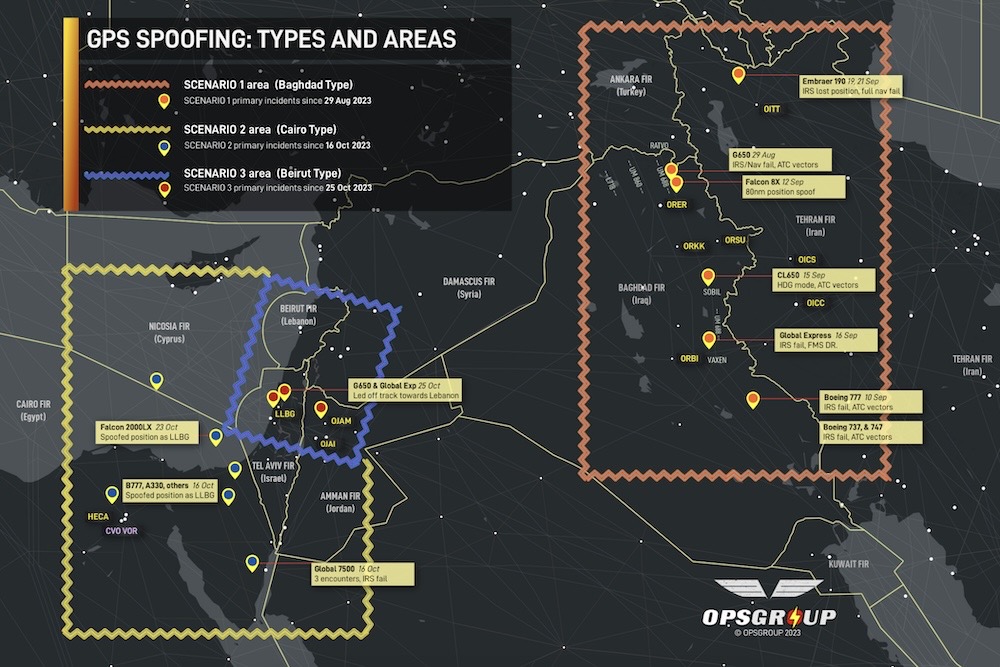
Commercial flights experiencing GPS spoofing attacks: Flights above the Middle East are experiencing "spoofing" attacks that muddle their GPS location, which are fooling planes into thinking they're flying miles away from their actual location. One aircraft almost flew into Iranian airspace without permission. There have been more than 50 incidents in the past few weeks. (via OpsGroup, Vice)
8 million Welltok patient records stolen: Welltok, the patient communication company acquired by Virgin Pulse, says more than 8 million patients had data stolen in a cyberattack earlier this year linked to a compromise of its MOVEit file transfer system. Welltok's data breach notice was buried out of sight and initially hidden from search engine results (tsk!). Welltok initially said a few million people were affected, but once victim organizations came forward with millions more affected, it quickly emerged that Welltok hadn't done its math properly. (via TechCrunch)
Fidelity insurance giant battles cyber incident: FNF, a Fortune 500 company that provides title insurance and settlement services for mortgage and real estate companies, said it shut down its network after a "cybersecurity incident" impacted its systems. What's looking like a CitrixBleed-related incident, per a screenshot of an unpatched Citrix gateway. The Alphv/BlackCat ransomware gang took credit, so that's another ransomware gang hitting victims on top of LockBit's spray-and-pay attacks... (via TechCrunch, Real Estate News)
'Gay furry hackers' breach U.S. nuclear lab: Well there's a sentence I didn't think I would write today but here we are. The self-described "gay furry hackers" of SiegedSec say they breached the Dept. of Energy's Idaho National Laboratory and stole Social Security numbers and other sensitive information of staff who work there. The lab, one of the most sensitive in the U.S., confirmed its HR systems were hit by a cyberattack. East Idaho News confirmed the stolen and subsequently leaked employee data was authentic. (via The Register, Cyberscoop)
~ ~
THE HAPPY CORNER
This week's happy corner is (not) sponsored by this perfectly timed Thanksgiving software update:
Happy 36th anniversary to the Max Headroom Signal Hijacking, one of the most high profile and elusive hacking incidents in living memory, which remains uncredited and unsolved to this day. More from PBS.
When I said last week, "it's almost time," I didn't mean still in November...(!) Anyway, here's this year's most secure light show in North America (probably).

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~

~ ~
CYBER CATS & FRIENDS
This week's cyber cats are Binx, Jasper and Sadie. Sure, they look cute and cuddly, but they're just plotting their next moves... like stealing your passwords. Many thanks to Dan S. for sending in!

Keep sending in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with their name and photo and they'll feature in an upcoming newsletter.
~ ~
SUGGESTION BOX
A short one this week... not a suprise given the quiter than usual Thanksgiving week. Although probably not such a bad thing — we all need a break once in a while!
Thanks for reading! As always, you can email me any time with your feedback, questions, comments — and, of course, your cyber cats.
Back next week — have a good one,
@zackwhittaker