this week in security — november 27 edition
THIS WEEK, TL;DR
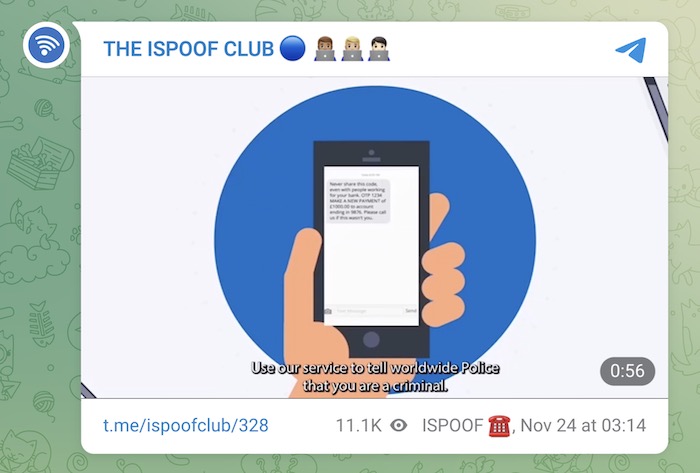
Police seize iSpoof call spoofing site, warns 70,000 victims by text message
BBC News: Baller week for international law enforcement who took down iSpoof, a notorious call spoofing site used by criminals to impersonate banks and other organizations. In iSpoof's place is now a seizure notice saying that U.S. and European police nabbed the site and its operators. Last year police said the site was used to make over 10 million fraudulent calls, making $58 million in damages at least. Police have made more than 100 arrests so far, including in Ireland, in connection with the seizure. Here's the twist: U.K. police said they are sending text messages to victims to alert them to the fraud and to help police build criminal cases on behalf of victims. Well, it was going well for the police, until the regular folk pointed out the obvious flaw in the plan: How will fraud victims know whether the police texts are legitimate? It's a nice idea in principle, but not one fully thought out. At least they redeemed themselves by posting a jaunty taxpayer-funded video to the seized site's Telegram channel telling everyone they were about to be arrested.
More: BBC News | RTE | The Record | @ispoofclub on Telegram
U.S., Britain take ban hammers to Huawei, ZTE, Hikvision
Associated Press, NPR: The U.S. government has finally banned Huawei and ZTE, two Chinese telecom equipment makers, preventing the sale and import of some of their technologies. It's been several years in the making. The FCC's ban means the U.S. can no longer buy or use new Huawei or ZTE equipment in critical infrastructure networks over fears it could be used for espionage (or worse), though existing tech may end up facing future bans (even if it's a far messier job to pull out equipment that's already there). The order also affects Hikvision and Dahua, two surveillance camera makers known for supplying technology to Chinese detention camps housing at least a million Uyghurs and other Muslim minorities, including interrogation devices. Hikvision and Dahua were subsequently banned by U.K. authorities this week from government buildings citing security fears. There's also a thread by former NSC staffer @joshuasteinman on the bans.
More: CNN | Reuters ($) | The Register | IPVM
A leak details Apple's secret dirt on security startup Corellium
Wired ($): Corellium, a cybersecurity startup that sells virtual iPhones and Android phones for app and pen-testing, offered or sold its tools to makers of government spyware and hacking tools, according to a leaked document prepared by Apple that contains internal Corellium communications. The document says Corellium offered iOS spyware maker NSO Group a trial, as well as offered to provide a quote to purchase its software to DarkMatter, a former cybersecurity company with close ties to the UAE. Corellium says it later denied NSO and DarkMatter requests to purchase the full version following its vetting process, which it explained more in a blog post after Wired's story went up. But Corellium didn't answer questions about why it allowed phone hacking companies Cellebrite or Elcomsoft to use its tech, or why Pwnzen was allowed to be a customer, despite helping to hack the phone of a suspected Chinese dissident back in 2019. More in the tweets from author @lorenzofb, and @dakotaindc on Pwnzen.
More: Washington Post ($) | Corellium | @lorenzofb tweets
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Need a laptop repair? Don't count on your privacy
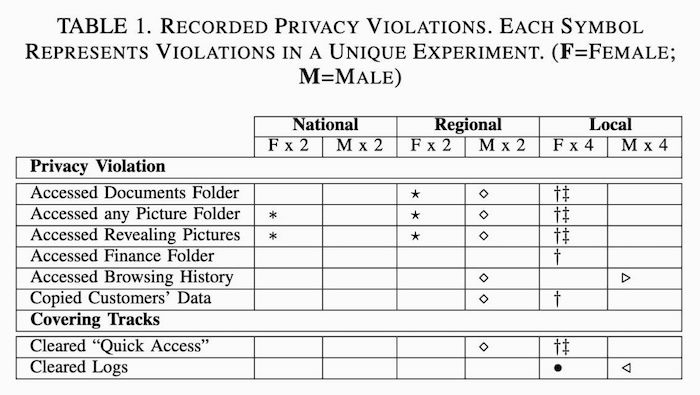
Ars Technica: A new study shows that laptop repairs often come hand in hand with privacy violations. When researchers recovered logs from 12 laptops that each went to a different repair shop, half came back with evidence that personal data from those laptops had been accessed. Unsurprisingly, female customers endure the most violations.
Indictments stand for French spyware maker
RFI: An appeals court in France upheld the indictment of the French company Amesys for complicity in acts of torture in the sale of spyware to the former Gaddafi-run authoritarian regime in Lybia, more than a decade after it happened, reports RFI (en français]. FDIH, a human rights organization, said the news was a "source of hope" that the company would face justice. You can read more background on the case via MIT Technology Review ($).
Meta links pro-U.S. influence campaign to U.S. military
SecurityWeek: Facebook owner Meta dropped the goods on a U.S.-run influence operation across YouTube, Twitter, and Facebook aimed at making the U.S. and its allies look great in the eyes of CIS and Middle Eastern countries, while making Russia and China look terrible. But according to Meta, the fake posts created for the operation had "little to no genuine engagement." To nobody's surprise, @WaPoEllen had the scoop back in September, reporting that the Pentagon began auditing its clandestine information warfare operations after they were, well, caught out doing exactly what other nations were doing. BBC News also has more.
~ ~
OTHER NEWSY NUGGETS
Tax filing sites sent your data to Facebook: H&R Block, TaxAct, and TaxSlayer were all sending sensitive financial information to Facebook when U.S. residents filed their taxes online, according to new findings. It's because Meta Pixels, the near-invisible website code that tracks website visitor activity, was transmitting back to the social giant things like names, email addresses, but also data on users' income, filing status, refund amounts, and dependents’ college scholarship amounts, regardless if a tax filer had a Facebook account or not. Ars Technica reports that H&R Block and TaxSlayer removed the pixel. (via The Markup)
FBI joins Continental ransomware probe: The FBI is helping German automotive supplier Continental investigate its recent cyberattack, blamed on the LockBit ransomware gang, after its leak page claimed to offer access to 40 terabytes of stolen data for $50 million. (via Handelsblatt)
~ ~
THE HAPPY CORNER
OK, a couple of good things from the week for the quiet post-Thanksgiving crowd.
This week I saw this brilliant YouTube video of lockpicking expert @deviantollam teaching a group of unsighted and blind folks the basics of lockpicking, in part by using 3D printed parts to help understand the mechanisms and parts of how locks work. I ended up watching the whole 50-minute episode last night because I was hooked from the start.
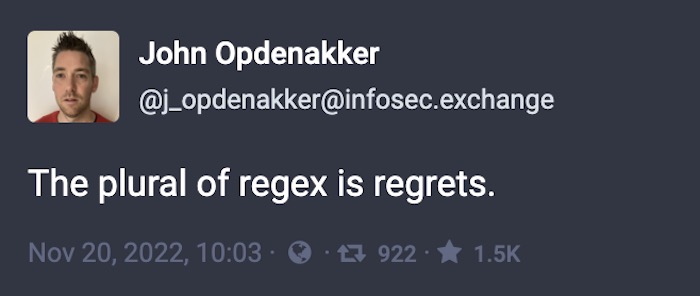
And finally, this week. For those, like me, who are still figuring out Mastodon:
If you have good news you want to share, get in touch at: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
Meet Jinx, this week's cyber cat, who speaks for how we all feel after this short holiday week, which is to say, sleepy. Many thanks to Collin L. for sending in!

Please send in your cyber cats (or their friends). Email me a photo and their name, and they'll be featured in an upcoming newsletter. Submitted before? Send an update!
~ ~
SUGGESTION BOX
That's it for now for this shorter-than-usual week (and newsletter). As always, feel free to drop any feedback in the suggestion box or email me. Have a great week as we head into the end-of-year home stretch.
See you next Sunday,
—@zackwhittaker