this week in security — november 5 edition
THIS WEEK, TL;DR
SEC charges SolarWinds and CISO with fraud and internal control failures
U.S. Securities and Exchange Commission: Months after SolarWinds warned of impending SEC enforcement action, the news dropped this week that the SEC was charging both SolarWinds and its CISO Timothy Brown with fraud and internal control failures. Key among the federal regulator's complaints include accusations that SolarWinds' CISO defrauded and misled investors by overstating the company's security practices and policies when he allegedly knew of "specific [cybersecurity] deficiencies" prior to a 2019 cyberattack. SolarWinds was hacked by Russian spies in 2019 with the goal of pushing out a Russian-planted backdoor via a SolarWinds software update to at least a hundred customer networks (including federal agencies). The whole complaint [PDF] is worth the read and it contains a lot. The SEC claims that while Brown allegedly knew of the risks, he failed to address them adequately. This puts (potentially) a lot of pressure on other companies (and CISOs) who could be faced with similar enforcement action in the future.
More: WSJ Pro ($) | SecurityWeek | BankInfoSecurity | @kimzetter

Four-dozen countries declare they won't pay ransomware ransoms
Cyberscoop: Some 48 countries (and the EU and Interpol) have pledged alongside the U.S. government to not pay ransom demands if they get hit by ransomware or other extortion event. The U.S. has long urged victims not to pay the ransom as this only perpetuates further cyberattacks (and it tells threat groups that you have cash and are willing to pay). This global pledge specifically notes that "relevant institutions under our national government authority should not pay ransomware extortion demands," so this only applies to governments and not organizations within those countries, and doesn't ban ransom payments outright. Costa Rica and Montenegro were hit by ransomware in recent years, as well as U.S. government systems and critical infrastructure (remember Colonial Pipeline?). It's a step in the right direction, granted, but while it sends a strong message, it's only going to matter if the majority of victims (who aren't government organizations) stop paying, too.
More: White House | Reuters ($) | TechCrunch | The Record
'Wholly ineffective and pretty obviously racist': Inside New Orleans' struggle with facial-recognition policing
Politico: Incredibly powerful reporting from Politico, looking at how the use of facial recognition by New Orleans' police department has resulted in few arrests and is disproportionately used against Black people. Politico obtained a ton of police reports via public information requests that shows that the police's use of facial recognition wasn't effective or even solving crime. Researchers have long argued that facial recognition is technologically biased against Black people because these systems are largely trained on white faces. This long-read is well worth your time, as are @alfredwkng's tweets on the story.
More: The Markup | BiometricUpdate | Brookings
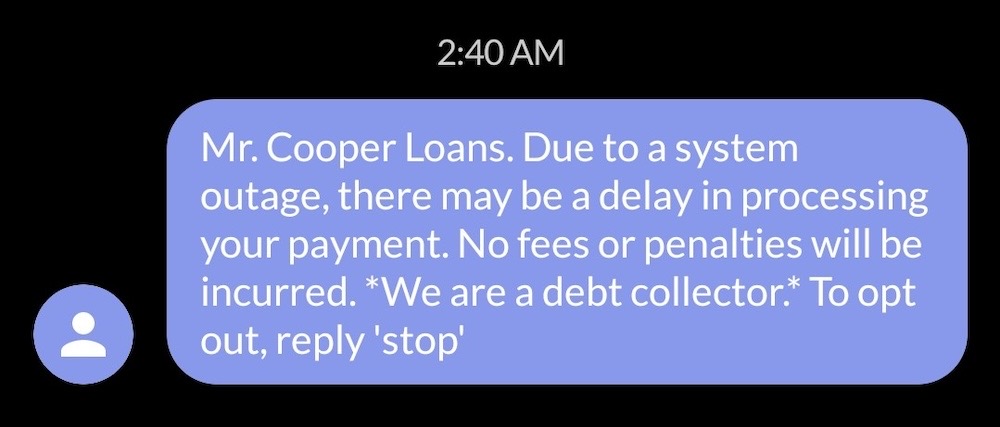
Mortgage and loan giant Mr. Cooper blames cyberattack for ongoing outage
TechCrunch: U.S. mortgage and loan giant Mr. Cooper said it's experiencing an ongoing "outage" caused by a cyberattack, which the company disclosed on a separate website (since most of the company's website is down). The company said it's investigating to determine if any data was exfiltrated (which doesn't instill much confidence). Folks have been in contact with me saying that they can't pay their loans or get access to their account information. Mr. Cooper said it's honoring rates and fees for the time being. With over four million customers, there's no clear timeline on when the company will get back online. (Disclosure alert: I wrote this!)
More: Mr. Cooper incident notice | MarketWatch | Dallas Morning News
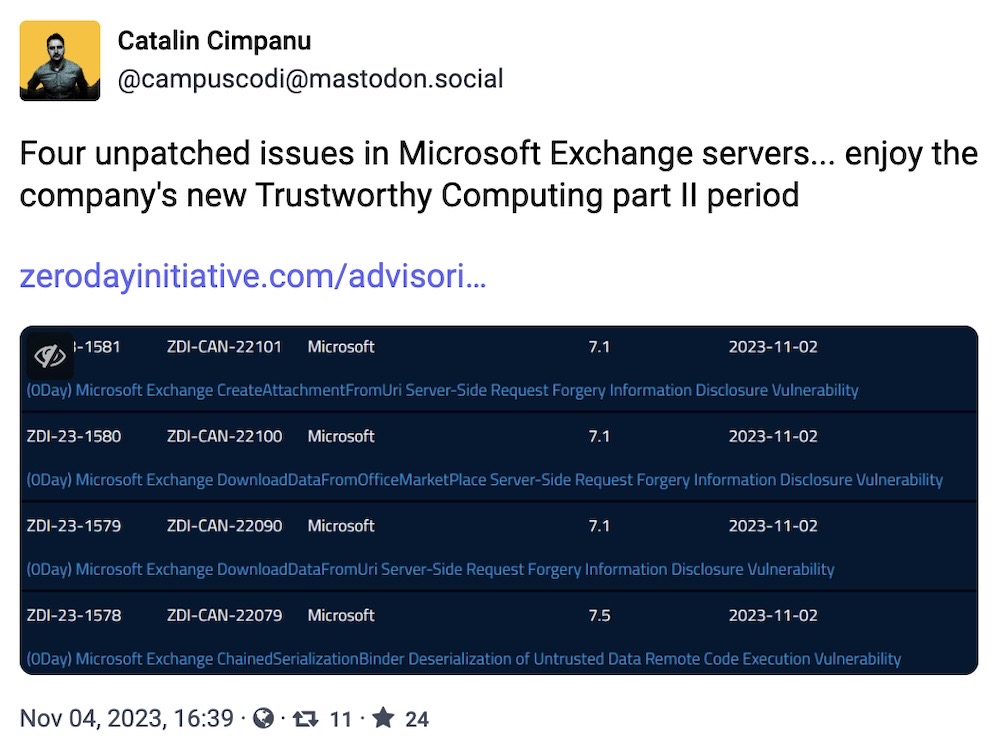
Microsoft is overhauling its software security after major Azure cloud attacks
The Verge: After a rough few months years, which The Verge starts out by noting in some detail, Microsoft announced it's overhauling its software security strategy, dubbing the new plan the Secure Future Initiative, which shakes up how the company designs, builds, tests, and operates its software and cloud services. Microsoft plans to use automation and AI during software develo... oh, come on, now that's where you're going to lose a lot of people! AI will only get you so far; having, listening to, and utilizing your best security talent will get you over the line. As Wired ($) notes, the initiative is Microsoft's damage control after a deluge of recent security incidents. The initiative also looks to speed up Microsoft's response to those incidents, as well as pushing for secure default security settings for its customers.
More: Microsoft | Wired ($) | Cyberscoop | Bleeping Computer
~ ~
THE STUFF YOU MIGHT'VE MISSED
Fujifilm and Xerox fix encryption bug in many of its branded printers
Pen Test Partners: Here's a great bit of research: Printer makers Fujifilm and Xerox have fixed a bug in their software that allowed an unauthenticated attacker (i.e. anyone) to retrieve and decrypt a printer's credentials from the web interface. Pen Test Partners found there were at least 1,900 affected printers connected to the internet, which if exploited, could allow access to the data stored within (which can be very sensitive!). Fujifilm and Xerox have both released advisories and patches.
Cyberattack dings Clorox earnings, but not as badly as expected
Marketwatch: Clorox, the consumer manufacturing giant behind popular cleaning brands and other household goods, reported its earnings this week for the first time since a cyberattack hobbled the company's operations. Clorox is cutting its full-year outlook, and its earnings were under what Wall Street expected, but not a huge surprise since its systems were walloped hard. Clorox's earnings are found here.
New details drop for mass-exploited CitrixBleed bug
Mandiant: In a new post, incident response Mandiant has published its notes on the CitrixBleed bug, also known as CVE-2023-4966, which affects Citrix's NetScaler and Gateway products. Mandiant says a big challenge for network defenders is that the web server running on the vulnerable appliances does "not record requests (or errors) to the vulnerable endpoint." That's a nice way of saying, "you're on your own folks!" There are some indicators you can look for, but Mandiant notes that identifying historical exploitation is "challenging." Lots of additional scribbles from @GossiTheDog.
Cloudflare dashboard, API service outage caused by power snafu
The Register: Somewhat ironically placed in "stuff you might've missed," but actually might have been very much impossible to avoid thanks to a day-long Cloudflare API and dashboard outage earlier this week. Cloudflare said the incident was caused by a regional power outage, compounded by a failure of backup generators. Whoops. Cloudflare also experienced an outage related to Pages and Workers KV earlier in the week, which it detailed in a post-mortem on its blog.
~ ~
OTHER NEWSY NUGGETS
Clop hackers accessed 632,000 email addresses during MOVEit mass-hack: According to the results of a Freedom of Information Act request, the Clop ransomware and extortion group obtained the email addresses of about 632,000 U.S. federal employees who work at the Departments of Defense and Justice. The Russian-speaking hacking group earlier this year mass-exploited a flaw in the MOVEit file transfer system software used by federal departments and thousands of other affected organizations. (via Bloomberg ($))
Mozi botnet bumped off, but by whom? The notorious Mozi botnet at its peak had ensnared more than 1.5 million infected Internet of Things devices, but suddenly dropped off the internet in August, according to security firm ESET. In a blog post, ESET believes the botnet largely disappeared following the use of a "kill switch," which effectively nuked the botnet and disinfected compromised devices, suggesting a deliberate takedown. But who was ultimately behind it? It was likely Mozi's original developers, but did law enforcement force their hand? (via SecurityWeek, ESET)
Okta drops breach post-mortem: Okta says its recent breach affected just shy of 1% of its customers, or 134 Okta customers. The identity and access giant said that the hackers used session tokens to hijack the legitimate Okta sessions of five customers. Three have already shared their own response to this event, including 1Password (which was first to notify Okta), BeyondTrust and Cloudflare. The two remaining hacked Okta customers have not yet publicly come forward. (via Okta)
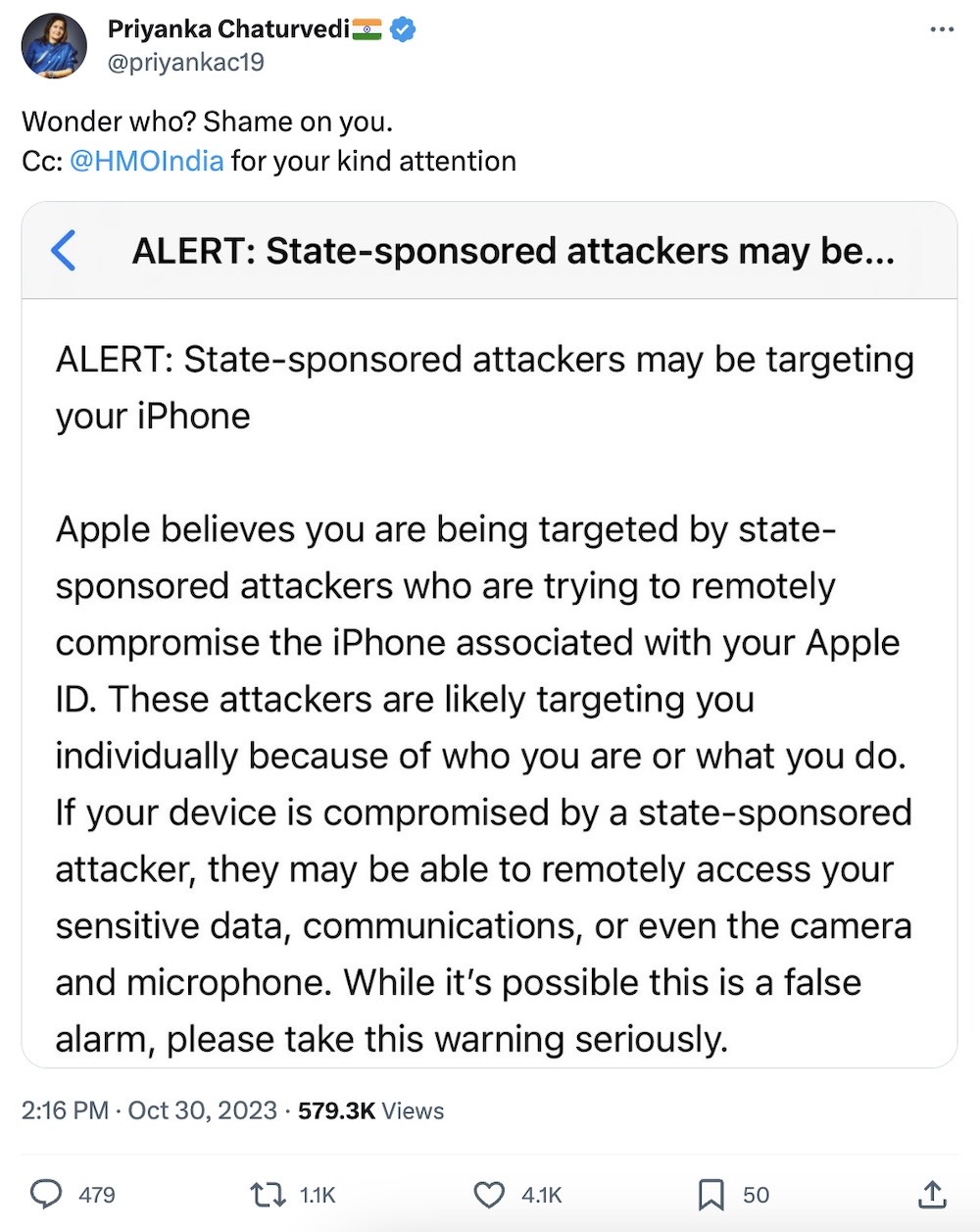
Indian opposition targeted with spyware: Apple sent out threat notification warnings to several members of India's opposition parties, saying "state sponsored attackers may be targeting your iPhone." These alerts are often sent out due to the discovery of indicators of compromise relating to spyware. The Indian government, which has been linked to previous Pegasus infections targeting activists and opposition leaders, downplayed the "vague" notifications. Meanwhile, Apple also warned people in Armenia, including high-ranking politicians and journalists, were also recently targeted with spyware, likely at the direction of the Azerbaijani government given the ongoing conflict between the two nations. Here's a primer on Lockdown Mode, the iOS feature that has successfully blocked some spyware attacks. (via TechCrunch, The Record)
~ ~
THE HAPPY CORNER
And breathe... that's the news, and this is the happy corner.
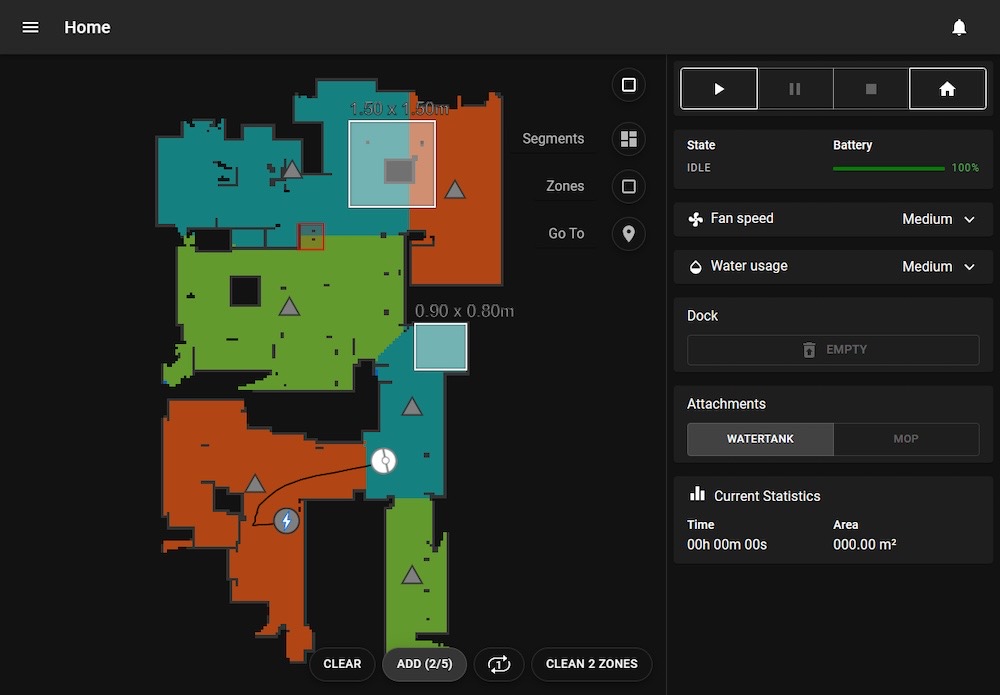
First up is this write-up from The Verge on self-hosting robot vacuums using a new system called Valetudo, a firmware replacement for robot vacs that acts as a cloud replacement, and includes room mapping(!). The project is by no means easy for the beginner crowd, but offers a really interesting insight into what it takes to run a local-only home robot vac. Don't go flashing your Roomba just yet, as iRobot products aren't yet compatible. Still, an awesome project nonetheless.
Halloween is over, but the Giant Sphere in Las Vegas is forever.

Great news out of California, whose attorney general Rob Bonta issued [PDF] a legal interpretation and guidance for state law enforcement that confirms it's illegal to share data collected from license plate readers with out-of-state law enforcement or federal agencies. License plate readers track cars around the country, and present a major privacy risk. Per the EFF, the legal guidance is good news for anyone who drives a car, since license plate readers can detail where people have been and what they've been doing.
And happy wormiversary to all those who celebrate. Here's a throwback to how the Morris worm — this week 35-years-young(!) — became the world's first botnet.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Arya, whose human can't get online today because of a significant business blocking event (aka very cute cat asleep on laptop). Many thanks to Emily for sending in!

Keep sending in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with their name and photo and they'll feature in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's it for this week's newsletter. Thanks so much for reading! I'll be back as usual next Sunday with all the news you need to know from the week. You can drop me an email any time if you have feedback, questions, comments or cyber-cat submissions
Have a great week,
@zackwhittaker