this week in security — october 1 edition
THIS WEEK, TL;DR
Ontario's BORN birth registry hack affects 3.4 million
Global News: Hello after a week away and we start with the incredibly depressing news (sorry) that Ontario's birth registry was stolen as part of the mass-hacks targeting MOVEit file transfer tools. Some 3.4 million people are affected by the incident at BORN, which records birth data for the Ontario government from hospitals and medical services. The incident affects those who sought pregnancy care and the data of newborns between January 2010 and May 2023. Yes, that's a decade's worth of highly personal data stored in a tool for temporary file transfers. How that was allowed to happen is anybody's guess. The incident page is here. Big questions remain for the Ontario Information and Privacy Commissioner, the province's data protection regulator, which oversees BORN. We're now at more than 62 million people affected — including children — by the MOVEit mass-hacks so far, claimed by the Clop ransomware and extortion group. But the number is likely significantly higher as new corporate victims continue to come forward.
More: BORN Incident | The Register | TechCrunch
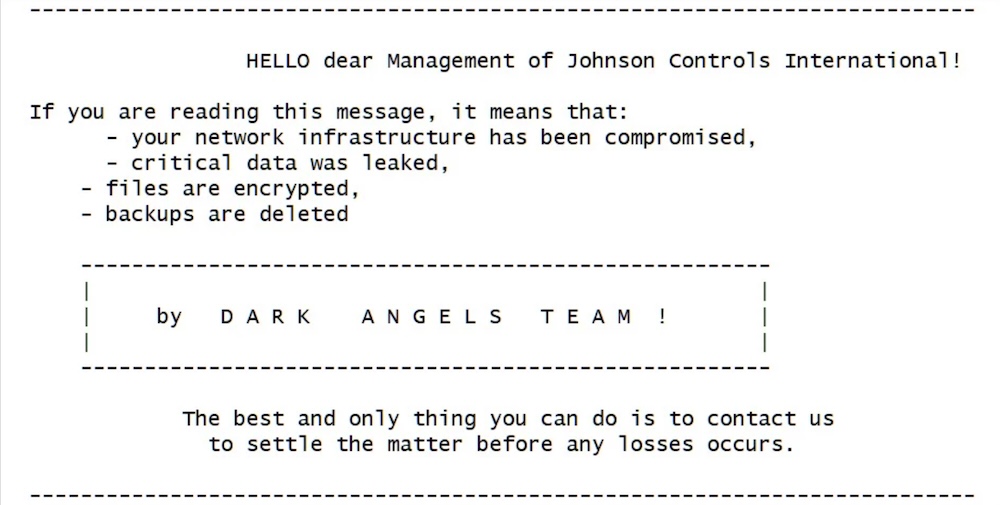
DHS investigating if floor plans were stolen from contractor in ransomware attack
CNN: Meanwhile, things aren't looking so hot over at Johnson Controls, a maker of alarm and building automation systems, which said in an SEC filing this week that it was hit by a cyberattack (read: ransomware) involving the theft of data. Homeland Security is said to be investigating, per CNN, fearing that the company holds classified or sensitive contracts for the department that "depict the physical security of many DHS facilities," per a DHS memo. Johnson Controls was hit last week, causing disruption to its IT systems and some websites. According to Bleeping Computer, the Dark Angels ransomware group took credit for the incident, claiming to have stolen 27 terabytes of data and scrambled the company's virtual machines.
More: Bleeping Computer | Dark Reading | Bloomberg ($)
U.S. spy law threatens privacy and needs restrictions, watchdog says
Wall Street Journal ($): PCLOB, the bipartisan privacy and civil liberties watchdog that examine U.S. surveillance laws like Section 702, which is up for expiry later this year, says in a new report [PDF] the surveillance law needs an overhaul and has recommended changes to the program that would improve oversight. Section 702 allows the NSA, CIA and FBI to access databases of raw collected intelligence (without a warrant) from non-Americans, even if those communications involve an American (in part why it's such a controversial law). It's complicated, to say the least. Feds want to keep these powers, fearing it could allow the next terrorist (or cyber) attack through, but privacy advocates say the law goes too far without much needed guardrails. It'll ultimately be up to lawmakers to decide how Section 702 survives, if at all (though it probably will in some form).
More: Cyberscoop | New York Times ($) | @JakeLaperruque tweets
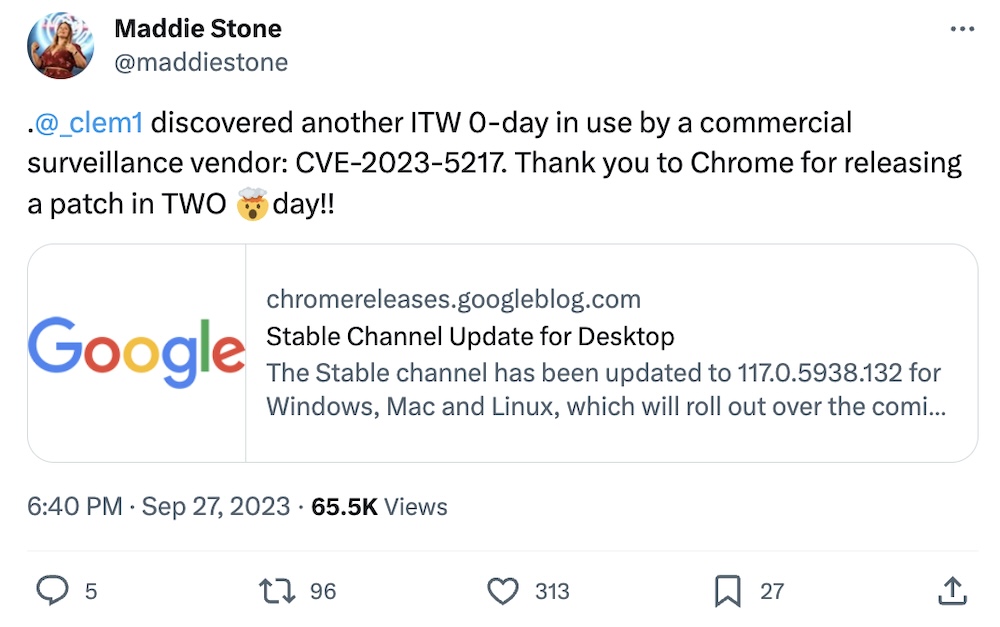
Google patches zero-day exploited by commercial spyware vendor
TechCrunch: Google has rushed to patch a zero-day flaw in Chrome that Google's own bug hunters say was used by a commercial spyware vendor. Google's TAG, which investigates nation-backed threats, discovered the bug tracked as CVE-2023-5217. Google fixed the bug in two days, but details of the bug weren't immediately available as patches rolled out. Firefox also got the same fix not so long later, per @campuscodi. It comes just a week after Google revealed three zero-days, recently patched by Apple, which were used to plant the notorious Predator spyware, developed by Cytrox. And, earlier in September, news of the libwebp bug came to light, which caused a stir at how it was handled, especially given this bug is in so many apps and web services. That libwebp bug was also used to plant the so-called BLASTPASS exploit used to deploy Pegasus. Patch all the things, literally!
More: Google | The Register | Isosceles | @benhawkes
~ ~
THE STUFF YOU MIGHT'VE MISSED
Who's behind the 8Base ransomware website?
Krebs on Security: 8Base is a prolific ransomware crew responsible for a ton of leaked and stolen data in recent months. Now, @briankrebs has found evidence linking the crime group to a 36-year-old programmer residing in Chisinau, the capital of Moldova. Krebs says 8Base was leaking its real-world IP address, which he linked to a GitLab account run by Andrei Kolev, who quickly began deleting screenshots he posted. A major opsec whoopsie here. 8Base apparently replied, claiming they have "nothing to say, we r a little busy," probably waiting for the feds to arrive.
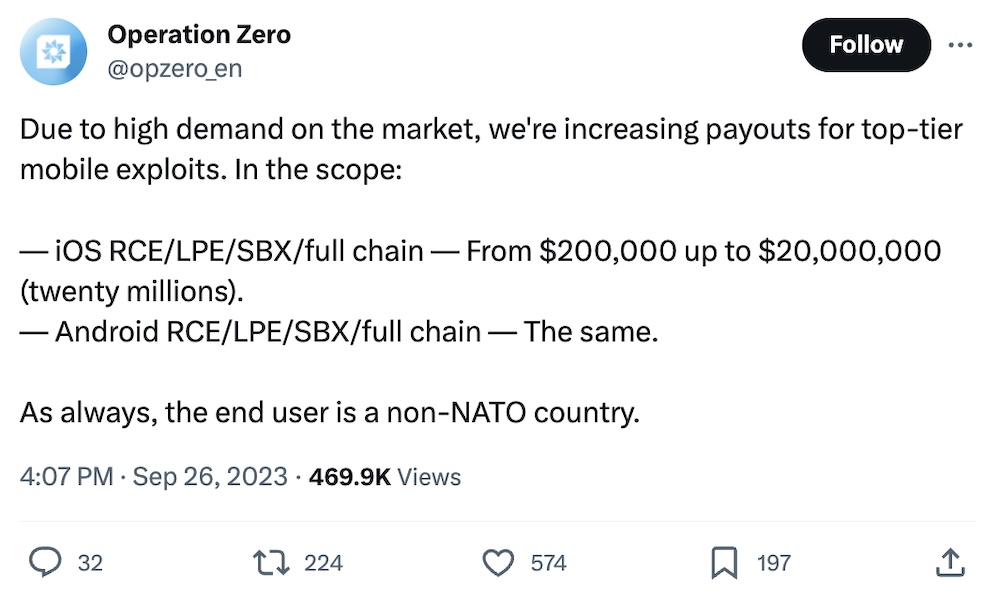
Russian zero-day seller offers $20M for hacking Android and iPhones
TechCrunch: An exploit seller in Russia is now offering to pay researchers $20 million (up from $200k) for tools and bug that can allow its customers to hack into iPhones and Android devices. The seller, a company called Operation Zero, said its clients are "Russian private and government organizations only," and that the exploit user is a non-NATO country. On the bright side, @shanehuntley says the rising prices are a "good sign" that zero-days are getting more difficult and expensive.
Kettering firm to lose 730 jobs after ransomware attack
BBC News: KNP Logistics, a trucking and training firm in Kettering, U.K., will shutter after 158 years following a ransomware attack in June. The incident was so bad that the company could not recover after reportedly paying the ransom. It's a really grim end for the business, especially for the hundreds now unemployed as a result.
Critical vulnerabilities in Exim threaten over 250k email servers worldwide
Ars Technica: More than 250,000 Exim-powered mail transfer servers worldwide are likely vulnerable to at least two outstanding remote code execution (RCE) bugs after three similar RCEs were fixed, according to a public mailing list. The situation is a bit of a mess and Ars explains this well. But the short version is, keep a close eye on this if you're an Exim user.
~ ~
OTHER NEWSY NUGGETS
Dallas publishes ransomware attack report: A hella-detailed report from the City of Dallas on its ransomware attack recovery efforts, including how much the restoration of its network cost. Credit to Dallas here, which published [PDF] its report into how the Royal ransomware gang broke in and what damage it did, which could help other victims (and would-be victims). (via SecurityWeek)
Chinese hackers stole 60k emails from State: State Department IT officials say that 60,000 unclassified emails were stolen from 10 State Department accounts, nine were working on East Asia and the Pacific, and one worked on Europe, following a breach at Microsoft, which hosts the government email inboxes. Those emails included travel itineraries and diplomatic deliberations, and some Social Security numbers. Microsoft was breached by Chinese state-backed hackers last year, said 25 organizations were affected, including the Departments of State and Commerce. The rest of the victims are not known. (via Reuters ($), Politico)
Government shutdown averted, for now: A U.S. government shutdown was narrowly averted this weekend after U.S. lawmakers eked through short-term legislation at the last minute, nudging another shutdown down the road for 45 days until the government's spending ability runs out again. A shutdown means some 80% staff at CISA could be sent home at a time when we really need our cyber defenders. NSA and other essential government services are largely exempt, and just in time for Cybersecurity Awareness Month. Phew. (via Federal News Network)
New Windows, new security features: Windows 11 update (23H2) will land with support for phishing-resistant passkeys and new security features, including Config Refresh, which lets admins revert to security policies in case of tampering. The firewall is also easier to manage. (via SecurityWeek)
Food delivery robot... spies? Those creepy food delivery robots are feeding their camera footage to the Los Angeles Police Department, according to emails seen by @jason_koebler. These robots are everywhere in LA, so it's not a surprise that the police are tapping them with department-issued subpoena powers. Again, folks, for those in the back who clearly aren't listening: If you collect data, it can be subpoenaed. Don't collect data to begin with, or at least make it unreadable. Speaking of, take a moment to read Bloomberg ($) on geofence warrants. "In law enforcement, as in life, sometimes it’s easier to ask Google for the answer," which should never, ever be possible. Alas, here we are. (via 404 Media, @kashhill)
~ ~
THE HAPPY CORNER
Welcome back to the happy corner.
It's October so it's *breathes in* extreme fall foliage season, and it's also Cybersecurity Awareness Month, so you know what that means:
And now you are too. So, please stop sending those silly PR emails. Don't make me tap the sign, because it's just the same Rob Joyce meme.
This week's bonus cybercat with a retro twist. (And bonus mental nostalgia for those old enough to remember the static smell of an old cathode ray monitor.)
Next up. @SwiftOnSecurity has a point:
And finally, if you were wondering where I was last week, you can find out more in my mega-long Mastodon thread.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Moe, who according to his human fell asleep on the job while guarding the network. Moe cannot be faulted, as his advanced age of 16 years old means he needs his rest. Totally agree, you're still doing a great job, Moe. Many thanks to his human, Rosa U. for sending in!

Thanks for sending in your cyber cats! Keep 'em coming. Send in your cyber cats! Drop me an email with your cyber cat (or non-feline friend!) with their name and photo, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's all there is for this week. Thanks for making it through! I'll be back next week with the usual roundup of news and more. As always, you can send any feedback you have to my email.
Have a wonderful week, back next!
—@zackwhittaker