this week in security — october 13 2024 edition
THIS WEEK, TL;DR
U.S. officials race to understand severity of China's recent hacks
Wall Street Journal ($): Let's start this week with the "Typhoon" family of Chinese hackers gearing up for war. Over the past few months, (at least) three distinct China-backed hacking groups — Volt Typhoon, Flax Typhoon, and now Salt Typhoon — have been caught laying the groundwork for a future conflict with the U.S., such as over Taiwan. Salt Typhoon is the latest group to catch the eyes of U.S. authorities, after breaking into several major ISPs' wiretap systems (think AT&T, Lumen, and Verizon) in an effort to snoop on U.S. internet traffic and, potentially, access information on subjects of U.S. surveillance. U.S. officials don't yet seem to know how far and wide the intrusions go — some as recently as "within the last week"(!) — but now the ISPs are under the spotlight for how they implemented a government-mandated backdoor law from some 30 years ago. Lawmakers are asking questions [PDF], including some scathing words for the FCC and the DOJ for not doing anything about this sooner when previously warned.
More: CBS News | TechCrunch | EFF | @riana
Internet Archive hacked, 31 million user records stolen
Bleeping Computer: A seemingly random popup on the Internet Archive's website alerted visitors that the non-profit's internet's online backup engine was "on the verge of suffering a catastrophic security breach." Turns out that's exactly what happened. Some 31 million user records were stolen from the Internet Archive and provided to Have I Been Pwned. HIBP owner Troy Hunt contacted the Internet Archive (as detailed in his disclosure timeline), but the non-profit's site was DDoS'd and defaced with the popup warning of the breach at around the same time. The stolen passwords in the data set are bcrypt-encrypted but email addresses were exposed in plaintext. The Internet Archive said it was working on rebuilding the site after scrubbing its systems and upgrading its security. As an aside, attacking the Internet Archive has widely been considered a really, really sh*tty thing to do, akin to hacking hospitals or other public services.
More: The Verge | SecurityWeek | @troyhunt tweets | @brewster_kahle tweets
Hackers targeted Android users by exploiting Qualcomm chip zero-day
TechCrunch: Qualcomm confirmed this week that unknown hackers were exploiting a zero-day bug in its widely used chipsets, used by dozens of popular Samsung, Motorola and ZTE-made phones. Details of the bug aren't yet known, but who found it is the most telling. Google's Threat Analysis Group, which investigates government hacking threats, found evidence of "in the wild" exploitation — meaning the bug is actively being used to hack people — and Amnesty confirmed the report, suggesting activists (or other members of civil society) may have been targeted. Could this be another spyware attack? Possibly. But more to come in the next few weeks, likely, when patches are rolled out and the risk to customers lowers.
More: Qualcomm | @__sethJenkins | @mattjay | @evacide
Microsoft's Patch Tuesday fixes two actively exploited zero-days
CSO Online: It's that monthly roundup of Patch Tuesday updates, landing with fixes for two zero-days exploited in the wild and another three publicly disclosed zero-days. One of the exploited bugs is a remote code execution flaw in Microsoft Management Console, which can trigger when a user is tricked into opening a malicious saved console file (though Microsoft was light on details around who was exploiting it). Bleeping Computer also has a list of recent security updates from other companies, from Cisco (plenty) to Ivanti (including zero-days, again).
More: The Register | @wdormann
~ ~
THE STUFF YOU MIGHT'VE MISSED
Hacked 'AI girlfriend' data shows CSAM prompts
404 Media ($): An 'AI girlfriend' site that lets its users create an "uncensored" chatbot was hacked and its contents leaked, including users' specific chatbot prompts — some of which described CSAM-related prompts. @Laughing_Mantis has heard of two extortion attempts linked to this breach, opening up a new fresh wave of hell for network defenders.
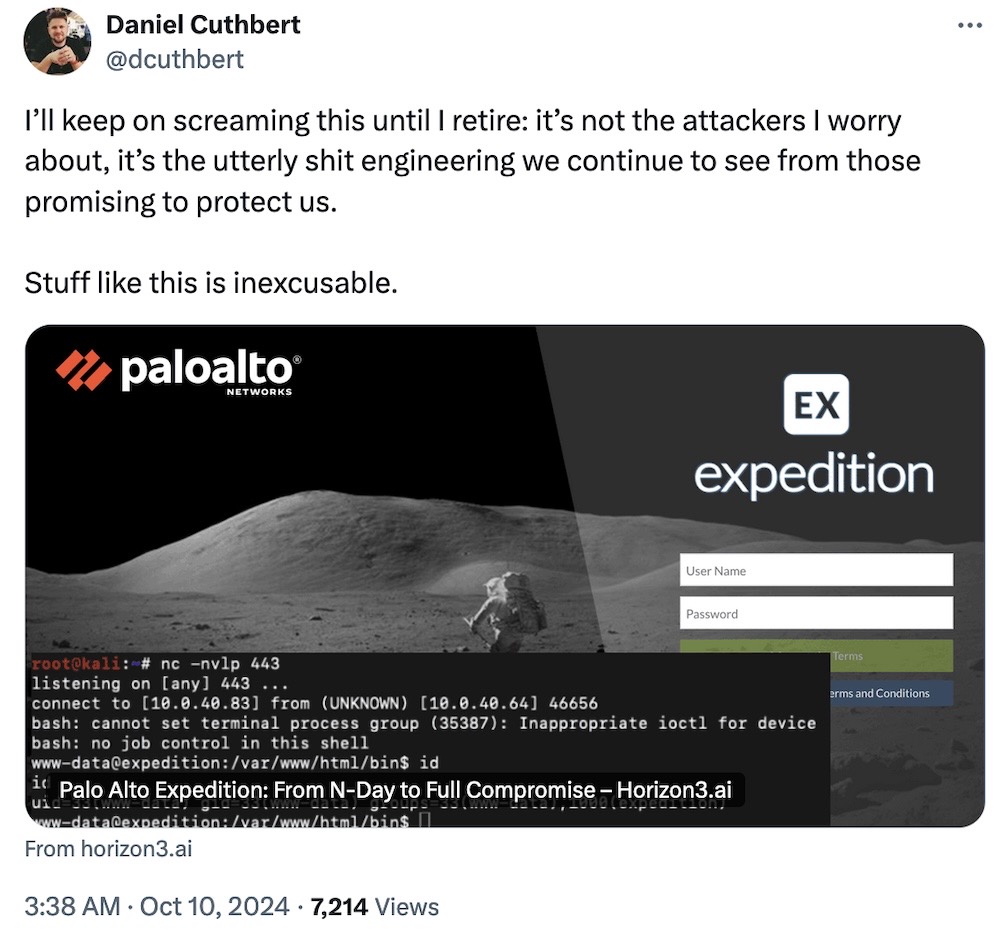
Palo Alto fixes bug that allowed remote admin takeover
Horizon3.ai: Researchers disclosed a series of bugs in a Palo Alto product called Expedition, including an unauthenticated SQL injection bug that allowed the exfiltration of database data. Cybersecurity is difficult, and so is software, but this isn't what you'd expect in a product from a security company. @dcuthbert, preach!
14,000 medical devices are online, unsecured and vulnerable
Cyberscoop: Nearly half of the 14,000 IP addresses of exposed and vulnerable medical devices as surveyed by Censys are located in the United States. Blame in part the decentralized nature of the U.S. healthcare system, compared to the U.K., which only has a handful of exposed devices online.
Meet the team paid to break into top-secret bases
BBC News: The BBC has a good story on red teaming, the groups of physical hackers and social engineers tasked with breaking into military bases or corporate headquarters upon their request. As the BBC goes, it's a pretty vanilla take on red teaming, but a nonetheless good read for anyone who wants a surface level view of how a physical pen test can go down.
~ ~
OTHER NEWSY NUGGETS
Alright, buckle up. We've got some hacks to blast through.
MoneyGram 'fesses up to data breach: Money transfer giant MoneyGram confirmed a data breach, after last month experiencing a cyberattack caused a week-long outage. The company, which serves more than 50 million people a year, wouldn't share how many customers are affected. (Disclosure: I wrote this story!) The data includes personal information — and transaction data — including dates and amounts. Bleeping Computer has more reporting on the incident itself, and more from @TonyaJoRiley in the tweets. (via TechCrunch)
Someone scraped thousands of Fidelity customer docs: Fidelity, one of the world's largest asset managers, said 77,000 customers had personal information scraped (seemingly) from a Fidelity customer document storage server. Someone created two new user accounts on Fidelity that allowed some kind of access to the document storage, so certainly a breach but not quite a hack. A strange case, compounded by the fact that Fidelity wouldn't answer any questions — but other data breach notices confirmed the accessed data included Social Security numbers and driver's licenses. (via TechCrunch)

FTC slaps Marriott and Starwood over breaches: The Federal Trade Commission told the hotel giant Marriott (including Starwood, which Marriott owns) that it must pay $52 million and improve their cybersecurity postures after several data breaches between them, including three incidents between 2014 to 2020 affecting more than 344 million customers worldwide. Glad to see the FTC act... several years after the fact. Better late than never, eh. (via FTC)
IronNet settles class action lawsuit: IronNet, the company set up by former NSA director Keith Alexander that was left to crumble under its management (check out this AP yarn from last week's newsletter), will pay $6.6 million to settle a class-action lawsuit that accused the company of making false and misleading statements to plump up its stock price. It's a huge fall from grace for a company that claimed – crucially(!) — a lot but allegedly provided little substance. (via DataBreachToday)
Aussie big firms made to report ransom payments: Some interesting news out of Australia; larger businesses (some 6.5% of all businesses in the country) that make $3 million (AUD) in annual turnover or more will soon have to report ransom payments to the Australian government. That's a start, given that banning ransom payments outright probably isn't going to happen — at least in the U.S., which would make the whole international side of enforcing the ban far trickier. (via The Record)
Firefox flaw, fast fix: The folks at Mozilla have updated Firefox to fix a zero-day bug under active attack within 25 hours of receiving its initial bug report. Per @campuscodi, the zero-day was used to target users of Tor Browser, which relies on Firefox. That's a fast fix, for sure — update today! (via Mozilla)
~ ~
~ ~
THE HAPPY CORNER
Not a moment too soon... welcome back to the happy corner. Just a couple of things from the barrel this week:
First up, here's one way to never fail the phishing test.

And... finally. A hacking group this week took out some of Russia's top state media outlets as well as several court and judicial websites on Putin's 72nd birthday, per Cyberscoop. The hackers left a message: “Happy birthday, d–khead," presumably about the deathly-looking aging autocrat (but actually...). The Russian authorities weren't thrilled, but maybe that's what you get when you illegally invade your neighbor twice in a decade?
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Princess Buttercup, who can be seen here conducting an adversary-in-the-middle attack on their human's computer. Very stealthy indeed... thanks so much to Sean K. for sending in!

Send in your cyber cats! (or a non-feline friend). You can email any time with a photo with their name, and they'll be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
And that's all there is!. Back next with the usual round-up from the week, and hopefully more on those China-backed hacking groups that seem to have the U.S. on edge. We will see!
As usual, feel free to reach out with any feedback, or anything you want to share for an upcoming newsletter.
I'm off to enjoy some autumnal nature and changing leaves.
Catch you next Sunday!
@zackwhittaker