this week in security — october 15 edition
THIS WEEK, TL;DR
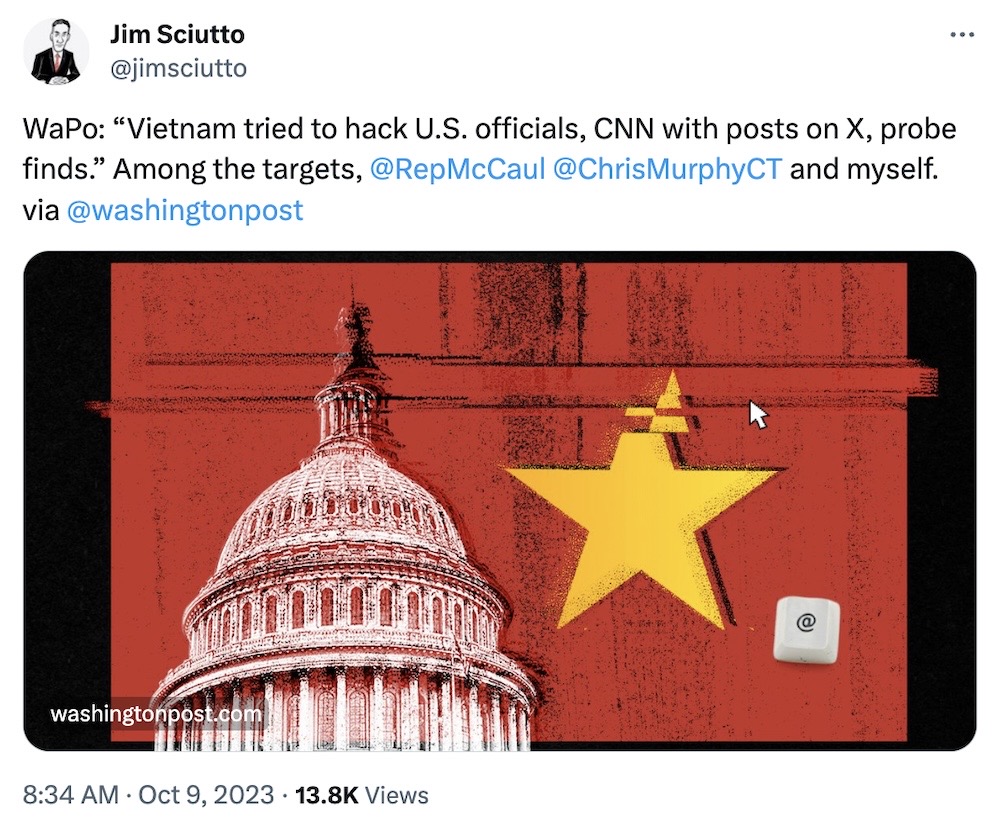
Vietnam tried to hack U.S. officials and journalists with posts on X
Washington Post ($): Vietnamese government agents tried to plant the Predator spyware on the phones of members of Congress and journalists, including CNN, during negotiations between Vietnam and the U.S. to counter Chinese influence in the region. Instead of sending malicious links to specific targets by text message, the agents sent them via tweet (or X'es?) replies or mentioning their would-be victim by tagging them from an account "@Joseph_Gordon16". One expert called the incident "reckless," since anyone could have tapped a malicious link (even if their phone data wasn't ultimately exfiltrated). Predator is made by North Macedonian company Cytrox and sold by Greek company Intellexa, two companies on America's so-called Entity List, which bans U.S. organizations from doing business with them — and yet here we are. Much of the information comes from a new series of stories looking at the Predator spyware. Amnesty has more in a detailed technical report. Clearly there are a lot of questions for EU and state officials, which allowed the export of European-made spyware to Vietnam.
More: CNN | @donnchac | @jimsciutto | @SophieintVeld
Hacktivist attacks erupt in Middle East following Hamas assault on Israel
The Register: The events in Israel-Gaza this past week are horrific, with thousands dead following an attack by Hamas. There's been immediate scrutiny about how the attack was possible and how the intelligence missed the planning, given the technology and defenses in place on the border with Gaza. Some wonder if the attack was largely planned offline, since resources in Gaza (like power and internet) are limited. Following the initial attack, U.S. intelligence said there was little known state-backed cyber component to the conflict. Instead, much of the visible cyber activity was carried out by hacktivists with allegiances to both sides, including DDoS attacks and website defacements. There was some good coverage of this story, including from Wired ($) and Data Breach Today with more context. The cyber component hardly seems relevant when people are dying needlessly.
More: Wall Street Journal ($) | SecurityWeek | TechCrunch
![A snippet of a WSJ report with the headline: "U.S.: No Major Cyber Attacks in Israel-Gaza Conflict, Yet" followed by the block of text: U.S. intelligence hasn't seen major cyber campaigns in the conflict between Israel and Hamas, but such attacks may yet be on the way, Rob Joyce, director of cybersecurity at the National Security Agency said Monday. Joyce said there have been minor assaults, including denial of service attacks and defacement of websites, by actors he didn't identify. “But we’re not yet seeing real [nation] state malicious actors,” Joyce said at the Cipher Brief Threat Conference in Sea Island, Ga."](https://this.weekinsecurity.com/content/images/scraped_images/86193a8d-d722-79aa-d3c1-44541a333eca.jpeg)
Hackers advertised 23andMe stolen data two months ago
TechCrunch: A batch of data stolen from individual 23andMe accounts during a credential stuffing attack (think password reuse) appeared online months earlier than first reported, suggesting the genetic testing company could have known about this incident as early as August. In case you missed it, a hacker is selling access to millions of 23andMe account holders' data, including genetic information, many of which were scraped from user accounts of Jewish Ashkenazi descent and Chinese users. @lorenzofb and I (disclosure alert) found that the stolen data is likely genuine, since we verified that some of the stolen data matches existing known genetic data that had been previously published online by genealogists. 23andMe still hasn't commented beyond a blog post it published a week ago, which largely blames users for not using multi-factor authentication. Blaming users for this (which some have done!) seems shortsighted, since it's 23andMe's job to ultimately keep your data safe — and enforce MFA, like others have done (yes, even surveillance giants like Ring).
More: 23andMe | Bleeping Computer
Massive DDoS attacks caused by HTTP protocol bug
Wired ($): Google, Amazon, Microsoft and Cloudflare said one by one this week that they had battled huge, record-setting DDoS attacks that pummel victims' web-facing systems with junk traffic, knocking those victims offline. A new protocol bug dubbed HTTP/2 Rapid Reset is to blame. The bug doesn't hijack systems or steal data, but can knock services offline for those who really need them. The bug is in the HTTP/2 network protocol itself, which has been around for almost a decade and widely used, and most web servers are likely affected, so expect this to be a thing for a while.
More: Cyberscoop | Cloudflare | Amazon AWS | @tdp_org | @Tarah
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
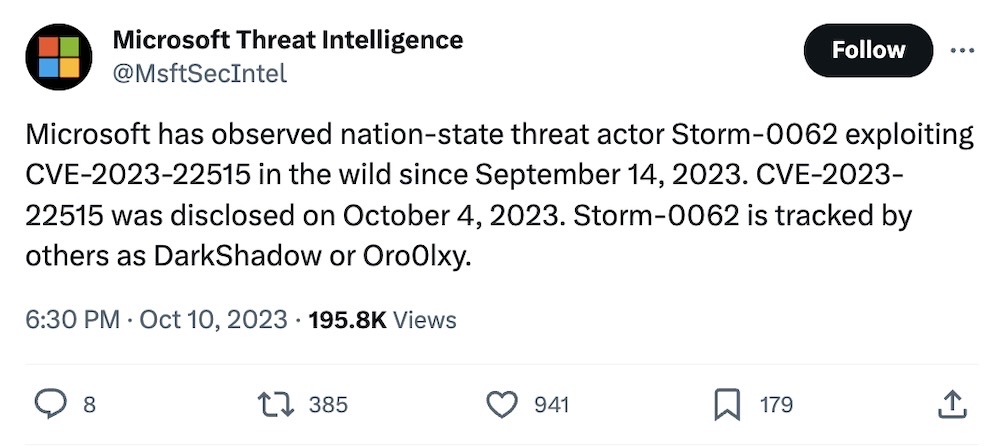
State hackers exploiting Confluence zero-day
Microsoft, Positive Technologies: In a set of tweets (because writing a blog post is too difficult?), Microsoft said that the recently discovered zero-day bug (aka CVE-2023-22515) in Confluence, which Atlassian disclosed on October 4, was under active exploitation since at least September 14. Meanwhile, @ptswarm, Positive's offensive security team (rings a bell) reproduced the bug, which allows attackers to create administrator accounts on an affected system.
Microsoft fixes exploited zero-days in WordPad, Skype for Business
SecurityWeek: Speaking of zero days, Microsoft said it patched more than 100 vulnerabilities in its products as part of its monthly release of patches, including two other actively exploited zero days bugs. One of which is found in WordPad (that note-taking app you used once in 1998 and not since). Microsoft said the bug allows the disclosure of Windows password (NTLM) hashes via maliciously crafted URLs or files. WordPad is like Windows' appendix; occasionally it'll malfunction and try to ruin your day. There's also another zero-day in Skype for Business that can disclose IP addresses and is under active exploitation, so update today if you haven't already. Sounds kinda similar to this...
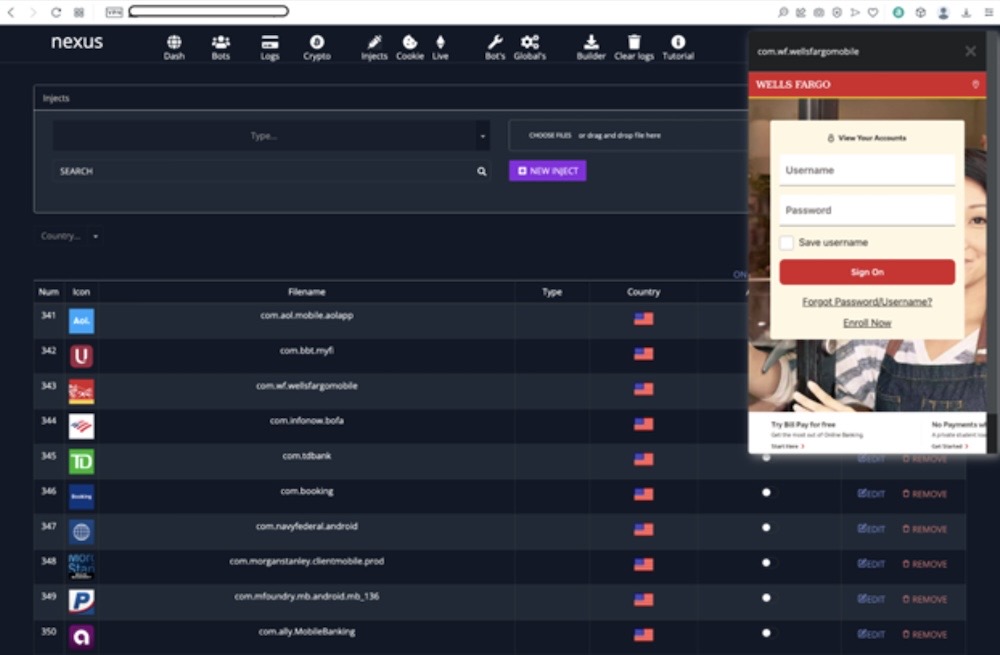
Researchers compromise Android banking botnet Nexus' admin dashboard
Virus Bulletin: Security researchers found a common security vulnerability (an SQL injection) in the command-and-control server used by the Nexus Android botnet and exploited it to gather information on how the operation works. Nexus has been rented as an Android malware-as-a-service in the past, and used to carry out data theft, spam campaigns, DDoS attacks and espionage. "For penetration testers and security researchers, it is important to find security vulnerabilities in the C&C panels of botnets in order to obtain access and gain intelligence to help combat botnet infections," writes researcher Rohit Bansal. Great work here. It reminds me of a recent excellent DEFCON talk by @evstykas (and now on YouTube) on the art of compromising malware C2 servers.
Heap overflow bug found in curl
Daniel Stenberg: A vulnerability in curl, the command line tool for getting or sending data, was patched this week. The bug, CVE-2023-38545, aka "apocurlypse" (maybe, anyway) was widely hyped, and while an impressive bug, it's not believed to be a widespread security threat. After all, curl is found on many, many modern operating systems (Macs and Linux especially). The bug works in cases where curl clients are configured to use a SOCKS5 proxy with remote DNS enabled, per @malwaretech.
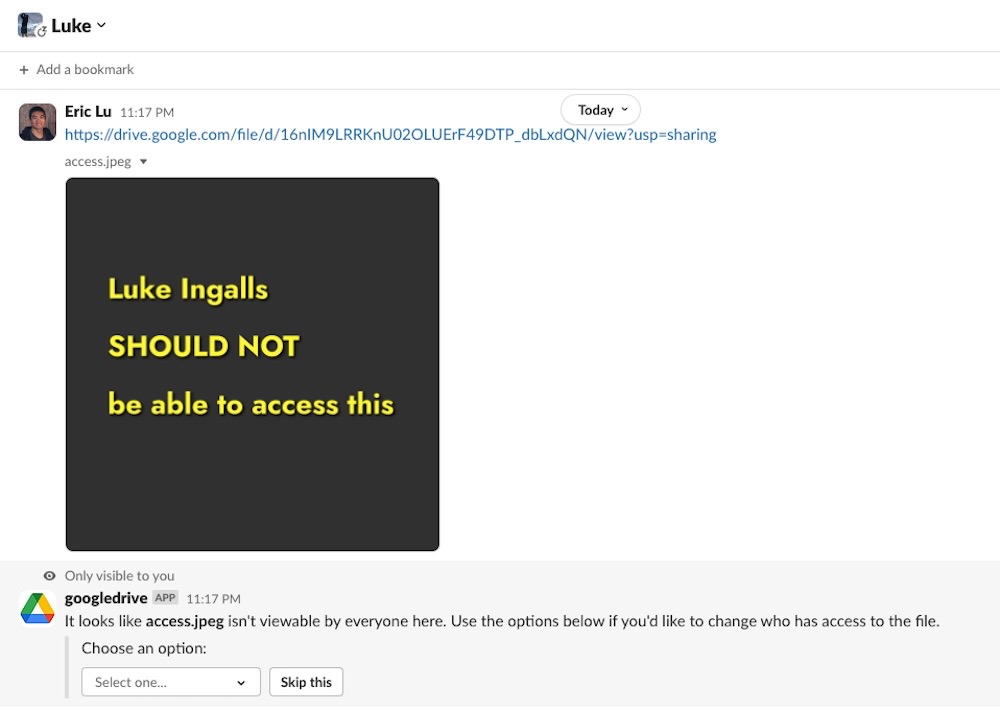
Slack's Google Drive App can share your private Docs and Drive files
Kapwing: Turns out that Slack's access to Google Drive seems... wider than necessary. According to Eric Lu, Slack's Google Drive integration uses a feature called File Preview, which shares a small preview of the document's text when a Google Doc link is shared over Slack. But that also reveals the contents of documents that were set to private. Whoops. Here you can see how this works:
~ ~
OTHER NEWSY NUGGETS
Mercenary hackers stole data used by Exxon in court: An Israeli private investigator allegedly used hackers to steal emails from activists that were later cited by Exxon's lawyers in court, as part of an effort to parry an investigation involving state attorneys general and backed by environmental activists. That's according to a sentencing memo by U.S. Attorney Damian Williams for the SDNY, who stopped short of stating a link or connection between the private eye and Exxon. But it's important that a U.S. prosecutor noted this particular tactic, as the use of hacked materials are increasingly used in legal proceedings to gain an upper hand; case in point, this blockbuster Reuters story last year. (via Reuters ($), @JosephMenn)
Blackbaud's massive data breach cost it $50M: The software maker company whose web-based software is used by schools, charities and other organizations to manage donor outreach, has settled with all 50 state attorneys general over the company's poor data security and terrible response to its 2020 ransomware attack. More than 13,000 organizations were affected, and countless individuals' data. Blackbaud settled for $50 million in the end, on top of another $3 million to settle separate SEC charges. (via Bloomberg Law ($))
MGM says it didn't pay hackers' ransom after huge breach: Hotel and casino giant MGM said it chose not to pay a ransom to the hackers who broke in or even respond to them, because the attack was so far along and the company had already begun responding to the incident. "We're not paying these bastards," said MGM CEO Bill Hornbuckle in an interview with Bloomberg. "The reality is because we caught this so early and we were on them." As huge as the breach is — and likely to cost the company at least $100 million, on top of dealing with the theft of millions of people's data — MGM seems to have come out largely looking like it handled its scandal. Its rival, Caesars, however... ehhhhh. (via Bloomberg ($))
EU body considers revealing TETRA code: ETSI, the European standards body which landed in hot water earlier this year after the encryption algorithms it used to secure TETRA radio comms was found to be buggy as hell, is now debating whether to make the algorithms public so security researchers can examine them for (further) flaws. Earlier this year, Zetter reported in Wired ($) that security researchers who reverse-engineered the algorithms said the standards body purposely weakened the algorithm to allow the decryption of radio communications. (via Zero Day)
~ ~
THE HAPPY CORNER
Welcome back to the happy corner. Only good vibes in here, some might even say the best.
Google made passkeys, the phishing-proof passwordless sign in method, the default way for Google users to log in to their accounts. Passkeys are great, easy to use, and can replace passwords in a jiffy. Users will be prompted to switch to a passkey when they log in. That's a pretty good move for Google's several-ish-billion users.
If you, like me, want to take a trip down memory lane, @shellsharks has a running list of Designer Vulnerabilities, aka vulnerabilities with custom names, logos and websites. Special shout out to CVE-2023-39848 for (not) making the list.
Shout out to California for passing the Delete Act, which allows residents to request all data brokers in the state remove their personal information. The bill reinforces that all data brokers have to register with the state's privacy regulator, the CPPA, where California residents already have GDPR-style "right to be forgotten." The law "requires the CPPA to establish an easy and free way for Californians to request that all data brokers in the state delete their data through a single page, regardless of how they acquired that information." I mean, that's pretty toasty, right? Now any one of California's 40 million residents can contribute to burning the data broker industry to the ground one click at a time.
Veilid (created by the Cult of the Dead Cow), the open-source, peer-to-peer protocol that makes surveillance so much more difficult, found a bug and disclosed it with a proof-of-concept code, because... why not? This is how it should be done!
And finally, this week: @TonyaJoRiley has an appropriately seasonal update on where we are with U.S. privacy legislati...

Maybe next year, huh?
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Miffy, who since becoming an inside cat has taken her role in physical security very seriously — and Miffy is doing an excellent job. Many thanks to her human Luke A. for sending in!

Please send in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with their name and photo and they'll feature in an upcoming newsletter.
~ ~
SUGGESTION BOX
Aaaaand I'm out for now. Hope you enjoyed this week's newsletter. Same time next week? In the meantime, if you have any feedback, feel free to drop me an email.
Have a good week,
—@zackwhittaker