this week in security — october 20 2024 edition
THIS WEEK, TL;DR
U.S. charges Sudanese men with running powerful DDoS-for-hire gang
Washington Post ($): Finally, the long-running DDoS-for-hire gang called Anonymous Sudan is done, after its members — two brothers from Sudan (quelle surprise) — were arrested earlier this year and charged with computer hacking and a range of other crimes. Anonymous Sudan was also charged with "knowingly and recklessly causing serious bodily injury or death" in its cyberattacks targeting hospitals, which went on to cause real-world downtime and harm to patient care. The group was certainly powerful for its size, briefly taking down Microsoft and PayPal's services, but was known for consistently hitting targets with DDoS that would favor or benefit Russia. U.S. prosecutors denied a link between Anonymous Sudan and Russia, but others aren't so sure about that.
More: U.S. DOJ | Europol | Wired($)) | Risky.Biz | @jkirk
U.S. charge Alabama man with SEC's X account hijack
Ars Technica: Busy week for the DOJ... after a U.S. man was charged with participating in the hack earlier this year that saw the SEC's X account hijacked and posted false information causing the price of bitcoin to rocket. The Alabama man was charged with SIM swapping the account belonging to a SEC staffer's phone, which ultimately allowed access to the X account (since it had been MFA'd up to its eyeballs). The Alabama man printed a fake ID, claimed to be an FBI agent, and secured the SIM swap in-store. What caught the hapless hacker? Was it reams of CCTV or a ton of evidence from the store and logs? Or maybe it was the accused Googling, "What are the signs that you are under investigation by law enforcement or the FBI even if you have not been contacted by them?" Yeah, no kidding! The indictment is a real hoot.
More: U.S. DOJ | TechCrunch | The Record | BBC News
Microsoft tells customers it lost log data for key security products
Business Insider ($): OK, apologies as this is... two weeks late(!) but wanted to flag this one as it's pretty important. A year after Microsoft begrudgingly agreed to open up the security logs for its customers' cloud products... Microsoft has now conceded that it lost weeks worth of those logs. The technology giant told some customers (the notice is now public) that the logs had failed to save between September 2 and September 19. It wasn't a cyberattack, but "a bug in one of Microsoft's internal monitoring agents resulted in a malfunction in some of the agents when uploading log data to our internal logging platform." The issue affects logs from Entra (which, y'know, important), Sentinel, Defender for Cloud, and Purview... so all fairly critical! Welp. Microsoft's handling of this is classic Microsoft, in that its top PR people stuck their fingers in their ears in the hope that this'll all go away. It won't. Instead, Microsoft continues to flush its customers' trust down the toilet.
More: TechCrunch | Bleeping Computer | @GossiTheDog
~ ~
THE STUFF YOU MIGHT'VE MISSED
How Apple Passwords generates strong passwords
Ricky Mondello: See that new Passwords app on your iPhone and ever wondered how it generates seemingly random phrases that aren't actual words but aren't gibberish either, like hupvEw-fodne1-qabjyg? Good news! Apple's @rmondello has your back with a great explainer of how Apple Passwords generates two-syllable "words." All for the sake of passwords that are briefly memorable but not memorizable; got it!
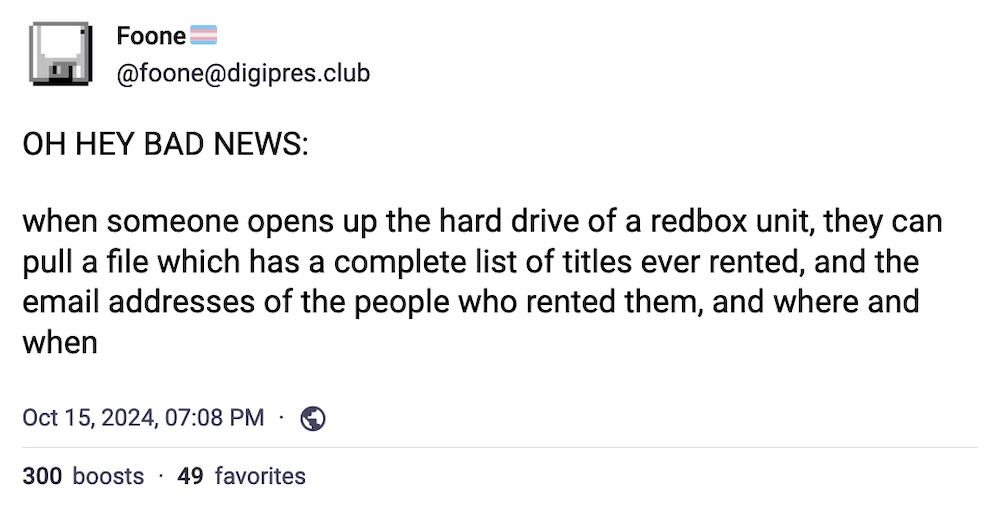
Taking apart an old Redbox kiosk for fun, data, and Doom
404 Media ($): Those aging Redbox DVD rental kiosks are no more, but not to a community of hackers and tinkerers, who are more than happy to take these defunct devices home to play. Turns out these once-helpful DVD rental machines are still loaded with data, including partial credit card numbers and transaction details. Although the devices can't "phone home" to their official servers, the tinkerers have still managed to repurpose the machines for their own uses... like running Doom. Solid @foone thread to check out, too.
Nah, Chinese researchers didn't break RSA encryption, but nice try
Rob Joyce: A story went around this week claiming that Chinese researchers broke the widely used RSA encryption using a quantum computer. Ehh, not so much, and ex-NSA's @RGB_Lights dispels the claim, as the attack targeted only a 22-bit key (which isn't very complex) and the computer itself wasn't actually quantum-based. All to say, make a mental note — bad actors will still collect encrypted data today for future decryption, but we're just not at the decrypt-later stage yet.
Some 87,000+ Fortinet devices still open to exploitation
Help Net Security: I know you're just as frustrated as I am having to read this what feels like on repeat every week, but here we are again. There's yet another security bug in a modern-day security appliance, this time it's Fortinet's FortiGate firewalls. The bug, known as CVE-2024-23113 (also see watchTowr Labs), is actively being used in hacking campaigns. According to the Shadowserver Foundation, more than 87,000 exposed Fortinet devices are connected to the internet. On the bright side, the meme game has been excellent.

Critical hardcoded SolarWinds credential now exploited in the wild
The Register: Surely we can't get any worse than tha.... oh, COME ON. Stand up, SolarWinds. Not like you haven't had enough attention already this decade, but here we are again with *checks notes* hardcoded credentials? The latest SolarWinds bug, aka CVE-2024-28987 has to be manually patched, or it can allow an unauthenticated user to access and modify internal data. Not at all an ideal situation, so patch (manually) today.
~ ~
OTHER NEWSY NUGGETS
Pixel gets security feature updates: Google rolled out Android 15 to its flagship Pixel devices this week, adding a ton of new features and functionality, including theft protection measures that require additional authentication if someone tries to alter key account or device details (similar to iOS 17.3). (via TechCrunch)
Pokemon maker hacked: The long-time gamemaker behind Pokemon, Game Freak, confirmed it was hacked, with decades of data stolen, including more than 2,600 items containing the names and email addresses of former and contract employees. Apparently the breach contains a fair bit of scrapped lore and unused concept art (and some of it quite odd). Not clear if this is some kind of hack-and-leak, or what the motivations are. (via Forbes ($), BBC News)
Kroger Face/Off: Add Kroger to the list of grocery stores that aren't worth your patronage, given the company's efforts to blanket its stores with facial recognition tech. Yes, the face-scanning technology used under the guise of preventing shoplifting but all too often gets things wrong (and people put in jail). Kroger made $3.1 billion in profit last year, so it's clearly not about its bottom line, but most likely about data, the other currency of the United States. (via The Record)
ESET's partner in Israel hacked: Hackers somehow breached ESET's exclusive partner in Israel to send phishing emails to businesses that pushed destructive data wipers under the guise of trying to protect the user against a state-backed threat. The company, ComSecure, hasn't commented on the incident, but ESET proper says it was "aware of a security incident which affected our partner company in Israel last week." ESET itself was not compromised, it said. (via Bleeping Computer, The Register)
Hacker still inside the Internet Archive: In not-so-great, late-breaking news (as in, just before this newsletter went out), the threat actor behind the breach of the Internet Archive has now auto-responded to every one of the non-profit's Zendesk tickets, clearly as a way to show they still have access to its systems. (The online archive remains in read-only mode for now.) @troyhunt, who initially disclosed the incident to the Internet Archive, posted the response from the hacker in a tweet, claiming the site hasn't yet reset its API keys. Suffice to say, this cyberattack is clearly ongoing. You can donate to the Internet Archive as it continues to rebuild. (via Washington Post ($), @troyhunt)
~ ~
~ ~
THE HAPPY CORNER
Welcome to the happy corner — the more the merrier this week, and not a moment too soon.
It's Hallowe'en season, and so don't forget to check your kids' candy for malware, USB sticks laced with Stuxnet, homebrew auth, and errant large language models. Let the Hallowe'en memes begin! (And please do send in your favorite.)
In excellent news, Hack To The Future, a deep-dive non-fiction by @hexadecim8, which follows the history of the critical and often-fraught relationship between the U.S. government and the hacker community, has gone to print! I'm super excited for this book, and it's out in December — just in time for the holidays. Pre-order today!
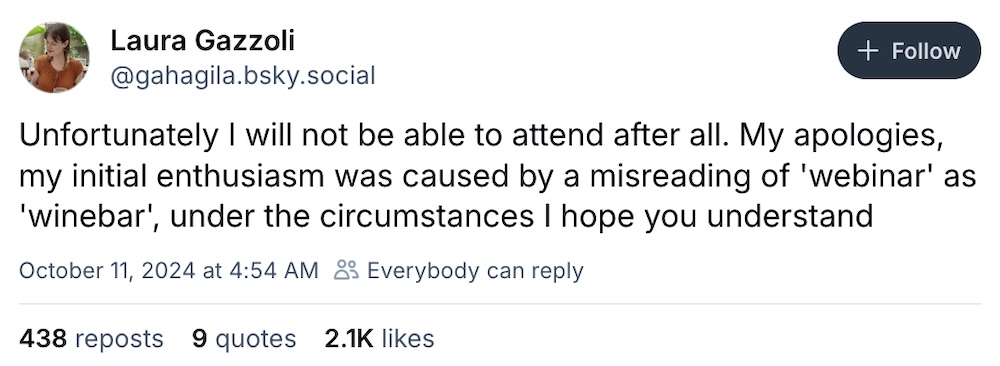
Meanwhile, over on Bluesky, we have your latest get-out-of-webinar excuse:
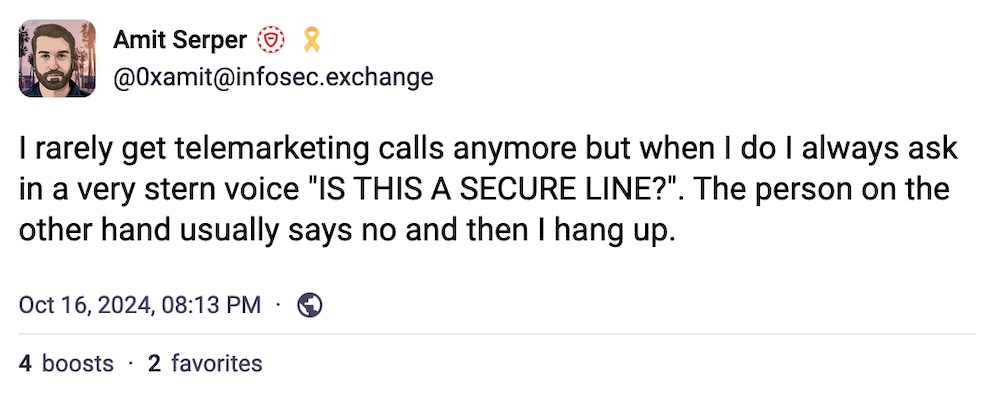
...and speaking of solid advice: If, by chance, you do pick up the phone these days, here's an easy way to handle pesky callers.
And, before you go, check out @morgan_sung's new podcast series called Close All Tabs on KQED, exploring the incredible and often weird world of internet culture and politics. Available on Spotify and your usual podcast places. Plus, bonus cybercat!
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet this week's cyber cat, Storm, who can be seen... Zzzz... Zzz... *snoozing* after a long day hacking... ssshh..... Zzzz..zz..zzz... thanks to Paul W. for sending in!

Send in your cyber cats! (or a non-feline friend). You can email any time with a photo with their name, and they'll be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
That's it for this week... and next... so this newsletter will return in a fortnight on November 3. Thanks for tuning in and reading, it's hugely appreciated! In the meantime, please do reach out if you have any feedback.
Gone phishin'...
@zackwhittaker