this week in security — october 22 edition
THIS WEEK, TL;DR
Thousands of Cisco devices backdoored through unpatched zero-day
Ars Technica: Not a fun week if you're a Cisco administrator, after the company dropped details of a new zero-day under active exploitation. A critical bug in the IOS XE software running on internet-facing Cisco devices can be exploited to create a new administrator account, granting near-unfettered access to a device and its network. At least 10,000 devices are vulnerable, but the number could be in the tens of thousands, per Censys, which says exploitation began as early as September 18 (at least). Most of the affected devices are in the United States. Patches are out today, October 22, so get patching if you haven't already.
More: Cisco | Cisco Talos | Dark Reading | @dangoodin | @shadowserver
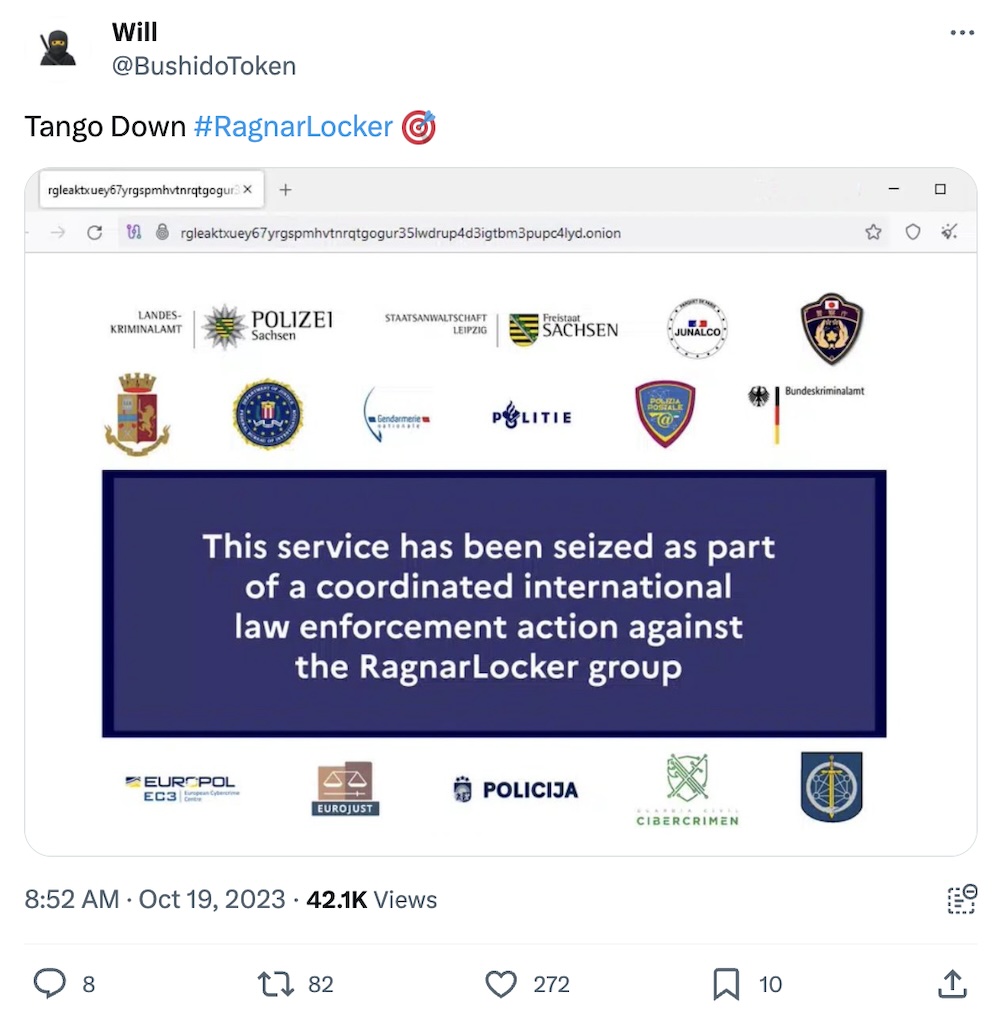
Authorities confirm take-down of RagnarLocker ransomware
TechCrunch: Another ransomware gang bites the dust — at least for now — after the alleged main perpetrator of the RagnarLocker gang, a 35-year-old developer, was arrested in Paris and his home in the Czech Republic searched by European police led by Europol. Servers, digital equipment, and a ton of cryptocurrency were seized. News of the takedown began on Thursday after RagnarLocker's dark web site was taken over by authorities and replaced with a website seizure notice. Confirmation of the raid finally landed on Friday, presumably once the operation was over. RagnarLocker started targeted victims in 2020, and targeted critical infrastructure and organizations, including in the United States.
More: Europol | Bleeping Computer | @BushidoToken | @lorenzofb
No known zero-day affecting Signal, despite rumors
Signal: There were rumors and rumblings of a bug affecting Signal last week, which some of you may have heard about, some of you have not. Signal said it's seen the "vague viral reports" but has said there's "no evidence that suggests this vulnerability is real." Signal president @mer__edith said the rumors, which claimed to come from a U.S. government source, "has the hallmarks of a disinfo campaign." Secure messaging apps are targets for disinformation as perceived or unsubstantiated flaws can nudge people into using less secure messaging apps that can be abused, per @jsrailton. Remember folks, stay cautious but like you would with anything else, trust but verify. While you're here though, Signal's president chats with Rest of World about how the non-profit resists government threats to privacy and encryption around the world. It's a great read, and all the more reason to support the non-profit.
More: @signalapp | Security Week | Rest of World
North Korean workers tricked U.S. companies into hiring them
Zero Day: It's a bold strategy, and one that apparently worked quite well, until the meddling kids at the Justice Department figured it out: North Korean workers would trick U.S. companies into hiring them remotely by using false identities to get the job, then funnel the earnings back to Pyongyang so the money can be laundered for its sanctioned weapons program. The workers used a ton of techniques to create an air of U.S. presence, such as paying Americans to use their home internet connections to tunnel their internet traffic. The workers made millions of dollars — which is obviously bad for world security, first and foremost, but also, as if the job market couldn't get any worse... and then you find out a North Korean scammer might've taken a job from right under your nose.
More: Justice Department | Associated Press | The Register | @kimzetter
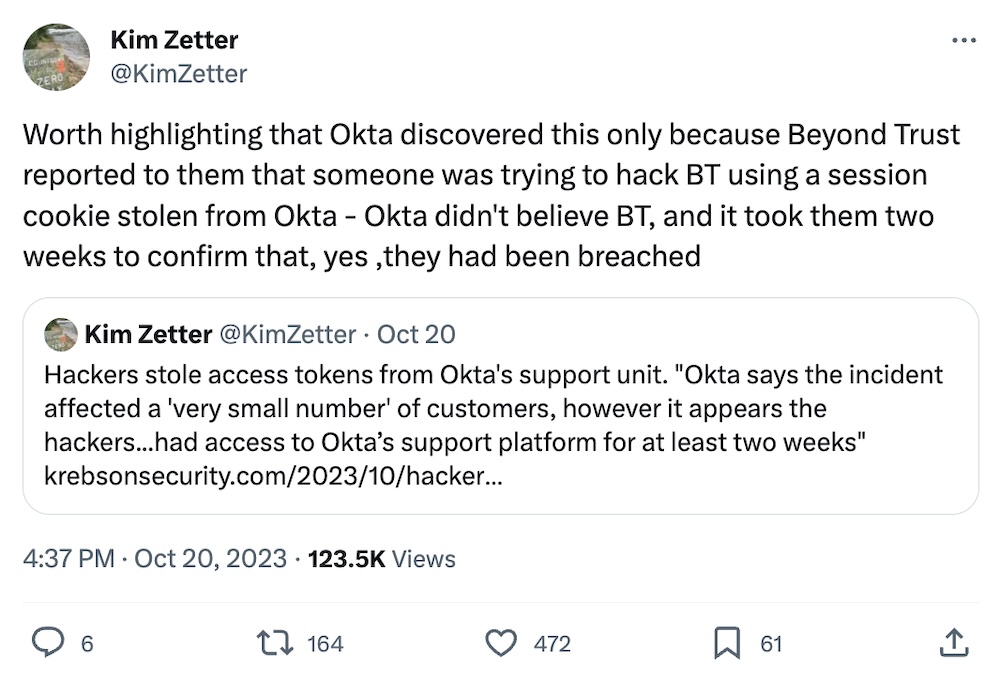
Okta hacked, and customer session tokens stolen
Krebs on Security: Identity and access giant Okta, which you probably know best from your workplace single sign-on experience, said a hacker broke into its support case management system, which Okta uses for customer support, and stole sensitive files uploaded by customers — including HAR files for diagnosing browsing session issues. HAR files can contain sensitive secrets, such as session tokens and cookies, which if stolen can be used to impersonate a real person. @briankrebs had the scoop, and Okta followed with a blog post shortly after, claiming it "identified adversarial activity" — except, it didn't, because BeyondTrust did, some two weeks earlier, long before Okta went public. Okta didn't say how the hackers broke in, saying only that a "stolen credential" was leveraged. I think what everyone is wondering is how exactly did the hackers break in? That is assuming Okta knows, of course. When I asked Okta, a spokesperson said around 1% of customers were affected (Okta has 17,000 customers). More from Cloudflare, which also published a blog post clubbing Okta over the head.
More: Okta | BeyondTrust | Reuters ($)
~ ~
THE STUFF YOU MIGHT'VE MISSED
Orbital Insight makes money from tracking West Papuan cellphones
All-Source Intelligence Fusion: Geospatial analytics startup Orbital Insight derives most of its revenue from a "wiretapping partnership supporting the Indonesian government," reports investigative reporter Jack Poulson. The partnership, dubbed Project Alpha, allows "full access, full untethered access" to the cellphones of Indonesian citizens, particularly those in the contested region of West Papua. Fascinating reporting here.
Prompt injection for your resume
Kai Greshake: The job market sucks right now, despite layoffs and companies still pushing growth and driving profitability at everyone else's expense. Just getting your resume through the door is a challenge, given how many (lazy) recruiters think using AI to filter out candidates is going to get you the right candidate. Prompt injection adds keywords into your resume near-invisibly, giving AI what it wants, and hopefully getting you to the front of the stack. Use this tool with caution! (via @mhoye)
Switzerland's e-voting system has predictable implementation blunder
Freedom to Tinker: Voting over the internet is always going to be less secure than a paper verified ballot, but that hasn't stopped states like Switzerland from pushing ahead with e-voting. And predictably, that's led to flaws, such as the "implementation blunder" as described by Andreas Kuster, which means that if a voter's computer is hacked, malware can redirect a voter to a spoofed website. Freedom to Tinker breaks down the blunder, with more from Bruce Schneier.
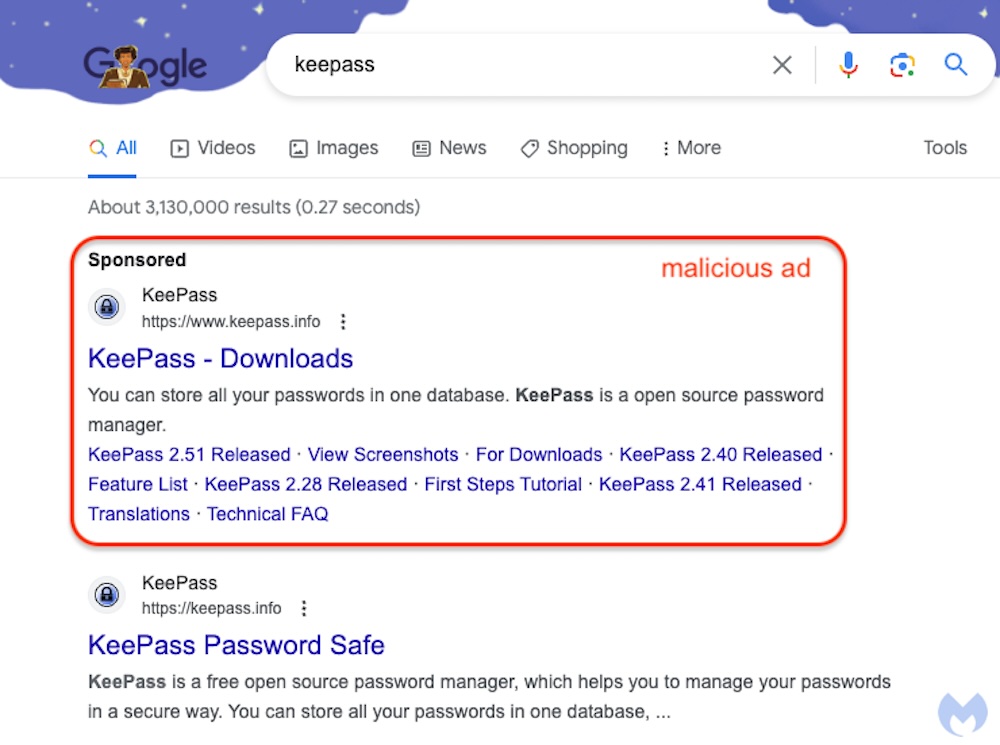
Google-hosted malvertising leads to fake Keepass site that looks genuine
Ars Technica: Speaking of malware... Google's continued declining search quality (we all see it) is at it again by displaying sponsored ads to malicious sites aimed at trying to trick users into downloading a malware-laden version of the KeePass password manager. Malwarebytes discovered the malicious site, which used a punycode domain name to look near-identical to the real KeePass website. Again, this wouldn't be an issue if Google kept its search results clean and free from malware. Alas, ads are how Google makes most of its money.
Jabber.ru likely wiretapped by German police, researcher says
ValdikSS: Russia's Jabber service (jabber.ru and xmpp.ru) "should be assumed compromised" after a researcher discovered that the TLS-encrypted connections were being wiretapped for around six months. It looks like what could be a lawful intercept, given that "the traffic redirection has been configured on the hosting provider network," in this case Hetzner and Linode servers in Germany. The intercept was only discovered after a TLS certificate expired and wasn't renewed (whoops). "We believe this is lawful interception Hetzner and Linode were forced to setup," likely at the request of German police. More discussion on Hacker News.
Surveillance tower in Mexico becomes unsettling landmark for privacy advocates
The Record: A building in Chihuahua, a Mexican state running along the U.S. border, will reach 20-stories in size, and feature 1,791 automated license plate readers, more than 3,000 pan-tilt-zoom cameras, and 74 drones, including live feeds from cameras owned by neighborhood businesses and residents. This building, known as Torre Centinela (or Sentinel Tower), is part of a deal between the Mexican authorities and the state of Texas, whose involvement isn't fully known (yet). The surveillance building — there's no other way of putting it — is already alarming local activists, fearing that the data (or surveillance) will track entirely innocent people.
~ ~
~ ~
OTHER NEWSY NUGGETS
Tech repair support snoop on personal devices: If you take your personal devices for repair to places like Best Buy, Mobile Klinik, and Canada Computers, expect to have your data raided and snooped on by technicians, because that's exactly what reporters at CBC discovered. Its reporters recorded technicians accessing personal device data unrelated to repairs in more than half of its cases. One technician copied data to a personal USB device. Great investigative work here, adjust your threat models accordingly. (via CBC)
Clearview AI lands rare win against U.K. sanction: Gross facial recognition company Clearview AI has scored a rare win against U.K. data protection authorities after it was found that the U.K. ICO, which in 2022 issued a $10 million fine for Clearview committing a string of breaches of local privacy law, was... technically wrong, because it wasn't a violation of the U.K.'s implementation of GDPR after Brexit (confusing, yes?). Clearview appealed the fine on the grounds that the ICO lost on jurisdiction grounds. As Privacy International explained in a tweet: "Clearview would have been subject to GDPR if it sold its services to U.K. police or government authorities or commercial entities, but because it doesn't, it can do whatever the hell it wants with U.K. people's data — this is at best puzzling, at worst nonsensical." Another bizarre consequence of Brexit. (via TechCrunch, @privacyint)
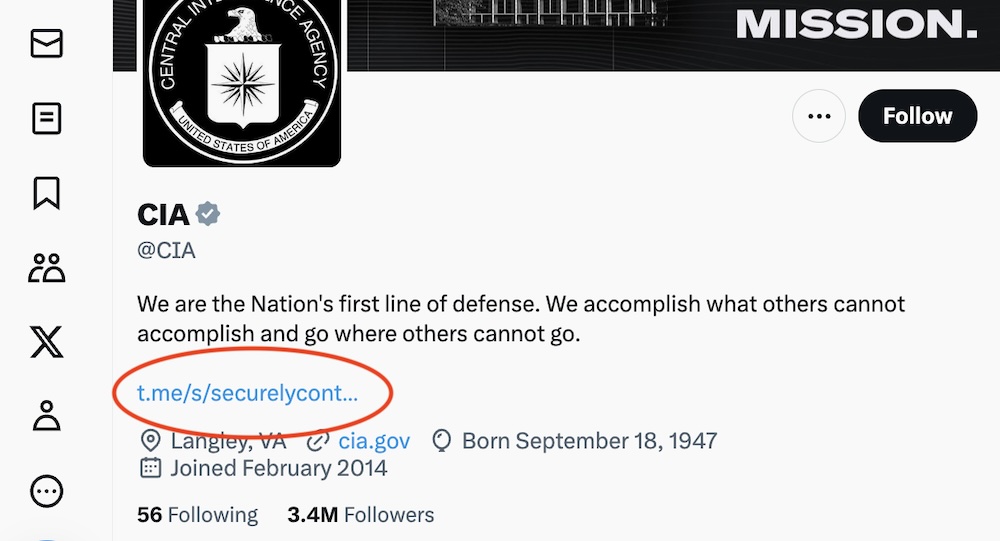
CIA 'really dropped the ball' after X/Twitter gaffe: The CIA's account on X (formerly Twitter, RIP) displays a link to a Telegram channel for informants, but cybersecurity researcher Kevin McSheehan found that the link in the CIA's profile was truncated slightly, and McSheehan was able to register that Telegram channel instead. "My immediate thought was panic," he told the BBC News. Yeah, it would probably be mine, too. "The CIA really dropped the ball," he added. (via BBC News)
Russia, China hacking WinRAR users: Earlier this year, researchers discovered a zero-day in the popular Windows archive file tool WinRAR that can be used to drop malware disguised as a legitimate file. Patches were rolled out quickly, but not everyone has updated. Google said this week that the hackers backed by Russia (Sandworm, the destructive hackers, and Fancy Bear of DNC hacking fame) and China (aka APT40) jumped on the exploitation bandwagon and abused the bug to hack their targets. (via Google Threat Analysis Group)
Hacker targets company that vets police data requests: Kodex acts as a buffer between law enforcement and tech giants to verify requests for customer data, but hackers apparently have access to Kodex's dashboard. Kodex helps companies verify law enforcement requests, and screenshots show it supports companies including Binance, Coinbase, Pinterest, Discord, and Snapchat. Hackers have previously exploited law enforcement request portals to retrieve sensitive data on individuals. (via 404 Media ($))
23andMe data leak gets millions times worse: Hackers who drained a ton of user data from 23andMe accounts largely consisting of Ashkenazi Jews and Chinese users are back with a new set of leaked data, this time a huge data set of some four million records of users in the United Kingdom. The new data matches known and public 23andMe user and genetic information, suggesting it came from 23andMe's servers. A spokesperson for 23andMe said the company is working to verify the data. 23andMe said the data was taken by way of credential stuffing — in other words, 23andMe is blaming users for password reuse. But just numbers-wise, that's a lot of data to have been exfiltrated allegedly from password reuse, no? Something doesn't seem right here, and 23andMe still hasn't said anything of substance. The EFF has a guide for folks who are concerned about the leak. (via TechCrunch)
~ ~
THE HAPPY CORNER
This is the happy corner, where you're cornered with goodness. It's like being lightly threatened with nice things.
With pumpkin season in full swing, please make sure you check your kids' Halloween candy for malware, exploits, and stolen session tokens.
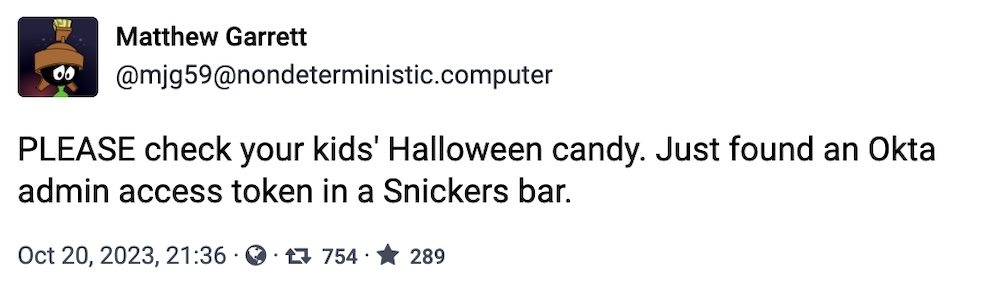
And happy Halloween to all the SOC managers out there in particular.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Hoa, whose human tells me that he keeps an eye out for physical security threats, particularly from winged attackers of the bird variety. Many thanks to Kenneth I. for sending in!

Please send in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with their name and photo and they'll feature in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's as much as I can humanely fit in one newsletter for this week. Thanks so much for making it through this far. As always, if you have any feedback, questions, comments or submissions, please drop me an email.
Patch all the things!
—@zackwhittaker