this week in security — october 29 edition
THIS WEEK, TL;DR
1Password detects 'suspicious activity' after Okta support unit hack
1Password: Password manager giant 1Password said its internal Okta account was briefly compromised after an earlier hack at Okta's support unit. As first reported by Ars Technica, 1Password said in an email to customers (and a subsequent blog post) that there was "no compromise of user data or other sensitive systems, either employee-facing or user-facing," which is good news. So far the breach of 1Password's outer layer leaves customers unaffected, but questions about Okta's response continue to be raised about why it took Okta three weeks to investigate and lock down its own systems. Last week, Okta confirmed its support unit was hacked, allowing hackers to obtain browser recording session files (and sensitive credentials within) that customers had uploaded to Okta's support system. "Our bar is as high as it can be," Okta CEO Todd McKinnon was quoted by Axios the same day as its breach. Some of Okta's customers disagree.
More: Ars Technica | TechCrunch | The Register | Axios
Hackers that breached Las Vegas casinos rely on violent threats, research shows
Cyberscoop: The hacking group known as Scattered Spider (aka UNC3944 or Okto Tempest), which earlier this year allegedly targeted MGM and Caesars (though the latter was denied by the group), uses SIM swapping and other social engineering techniques — including violence and threats — to break into high-profile targets. Researchers say the hackers connected to a wider community of SIM swappers called "The Comm" will use physical threats to get their way. 404 Media ($) reports that these SIM swappers are also working with ransomware gangs, like ALPHV.
More: Microsoft | 404 Media ($)
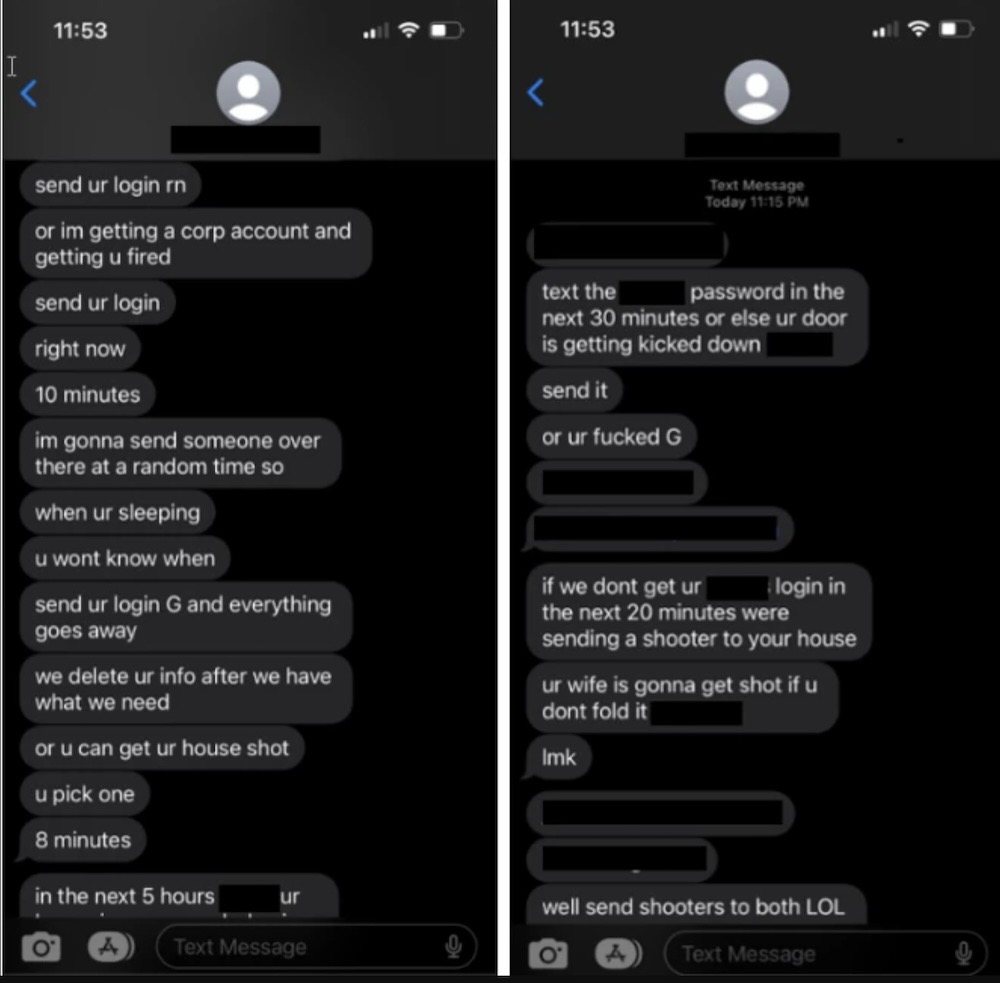
Grammarly says it corrected sign-in vulnerabilities after researchers' alert
The Record: Grammarly, a popular real-time grammar tool, has fixed flaws in its OAuth implementation, a common protocol for users logging in, which researchers said allowed bad actors to gain unauthorized access to users' accounts. The bugs were discovered by Salt Security, which found that Booking.com, Expo, and Vidio were vulnerable to the flaws. The bugs come from a lack of token verification, which, as you can imagine, is a very important process for ensuring those logging in are who they say they are. Without properly verifying tokens, hackers can steal credentials from the website's systems.
More: Salt Security | HackRead | BankInfoSecurity
Citrix warns admins to patch NetScaler 'CitrixBleed' bug immediately
Bleeping Computer: And as if you don't have enough to think about already this week, enter "CitrixBleed," a new bug that allows hackers to steal authentication session cookies from affected NetScaler appliances. The bug, tracked as CVE-2023-4966, was found to be exploited as a zero-day since late-August. Compromised accounts can retain persistence even after patches are applied, so don't forget to nuke all active and persistent sessions.
More: NetScaler | Rapid7
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
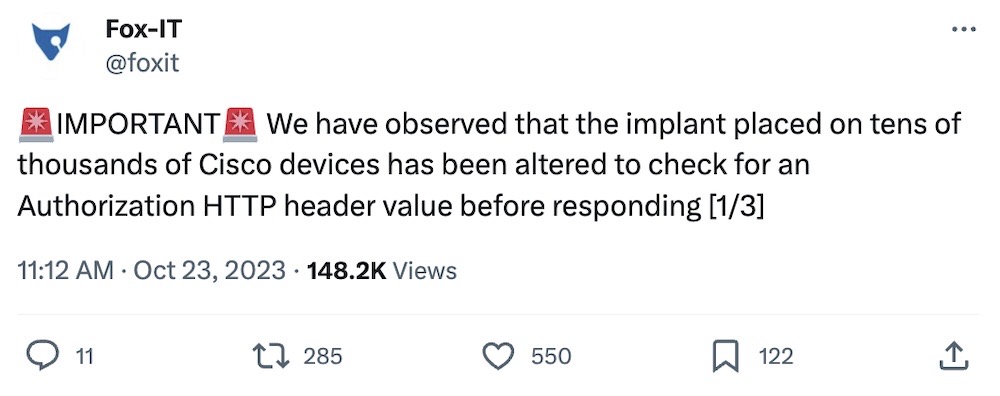
Cisco IOS XE devices still mass-hacked, but now hidden
Fox-IT: Meanwhile... remember those major bugs in Cisco networking appliance software IOS XE that are being actively exploited? Hackers compromised at least 50,000 Cisco devices to create privileged user accounts and plant backdoors. But then suddenly the number dropped out of nowhere. It turns out those devices haven't suddenly disappeared off the web, Fox-IT reports that the hackers modified the implant to effectively hide it from watchful researchers. This means those 50,000+ devices are still compromised — and not a valiant effort by good-faith researchers to mass-uninstall the implant as first thought.
DC voter roll was stolen in hack
DC Board of Elections: The U.S. District of Columbia's Board of Elections says its entire voter roll was stolen in a data breach affecting DataNet Systems, a third-party company. While voter roll records are generally public, not all of the data is. In an update, the local government agency said the breached database server also contained 600,000 lines of voter's personal information (which isn't public), including partial Social Security numbers, driver's license numbers, dates of birth and contact information. RansomedVC, a known extortion gang, took credit for the breach, which the DC Board of Elections initially said did not include voter information... welp.
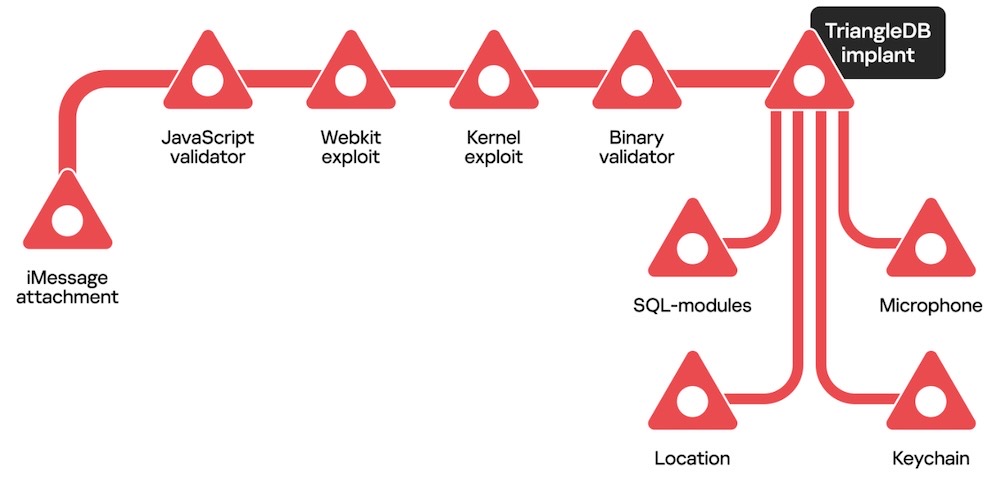
Kaspersky researchers explain how they obtained iPhone zero-day implant
Securelist: Kaspersky researchers take a long-dive into Operation Triangulation, the name of their project identifying a zero-day exploit targeting its researchers' own iPhones. The researchers obtained the implant, delivered over iMessage via two exploits, which contained several modules aimed at grabbing a device's location, passwords and microphone access. "We were able to eavesdrop on all communications performed by the implant, as well as obtain the module binaries," the researchers wrote. Pretty interesting finds, and Apple has fixed the bugs.
Australian spy org hit 'tens' of targets in the last year
iTnews AU: Late on Wednesday, the Australian Signals Directorate — aka its spy agency — confirmed in parliamentary testimony [PDF] that it had conducted "tens" of offensive operations, or some 30-50 individual actions, against cybercriminals (including ransomware actors), but that the figure did not extend to offensive activity against state actors. The ASD's director said that the spy agency had a "spectrum" of results, such as gangs losing reputation or being unable to trust the infrastructure they're using. (via @jkirk)
~ ~
OTHER NEWSY NUGGETS
Hackers pilfered Philly inboxes: For at least three months, hackers dug around inboxes run by the City of Philadelphia, which contained a wide variety of sensitive information, including some health data. The intrusions happened between May 26 and July 28, according to a PDF notice on its site. It isn't known how many people had data compromised as a result of this incident. (via City of Philadelphia [PDF])
VMware patches critical vCenter bug, including end-of-life: An out-of-bounds write issue with a critical-rated severity score of 9.8 out of 10 allows attackers to remotely run malicious code on VMware vCenter Server and Cloud Foundation products. Given the severity of the bug, VMware also rolled out patches for customers running products that were past end-of-life, briefly reviving security updates for its zombie product versions. (via SecurityWeek)
CISA releases nine ICS advisories: U.S. cybersecurity agency CISA dropped nine advisories for ICS products — the industrial controlling devices that keep the lights on and ensure the water supply is running. CISA said the advisories contain details about actively exploited security issues. Take note if you manage Dingtian, Centralite, Rockwell and Sielco products — and more. (via CISA)
23andMe slowly notifies customers of data breach: DNA and genetics tech company 23andMe is gradually notifying those whose information was compromised earlier this year following an incident of sorts that 23andMe has yet to adequately ascertain or confirm. What started as a credential stuffing attack now has the hallmarks of maybe that with a hint of an API data scrape. 23andMe has since switched off its DNA Relatives tool, per a blog post. Either way, hackers are still advertising millions of people's data, and 23andMe is still (publicly at least) none the wiser about how the incident went down. (via Reuters ($))
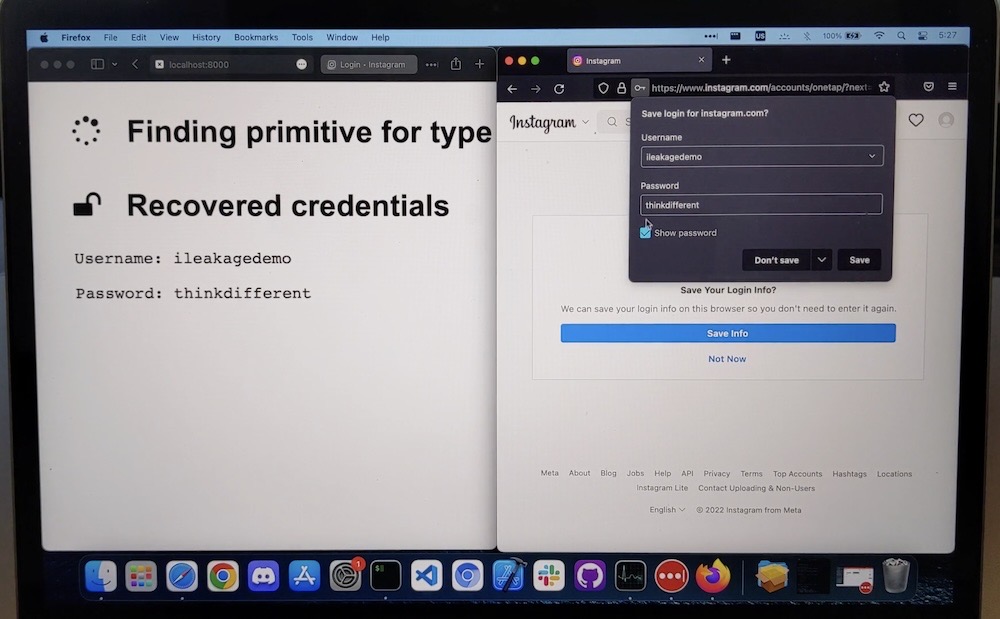
Malicious web pages can pinch Safari passwords: iLeakage, the latest exploit with a fancy name, can trick Apple's Safari browser into divulging passwords, Gmail message content, and other secrets by exploiting a side-channel flaw in A- and M-series chips in iOS and macOS devices (most modern iPhones and Macs). Researchers spent considerable time reverse-engineering Apple's hardware, and subsequently implemented iLeakage as a locally-run website, which when visited uses JavaScript to recover secrets, the researchers noted on their website (which will not exploit your device). (via iLeakage, Ars Technica)
Non-bank financial institutions must soon report breaches: The FTC said it's amending the Safeguards Rule that will require non-banking institutions (think mortgage brokers, motor vehicle dealers, and payday lenders) to report data breaches and other security events to the agency. The rule, which "requires financial institutions to notify the FTC as soon as possible, and no later than 30 days after discovery, of a security breach involving the information of at least 500 consumers," such as if unencrypted customer information was taken without authorization, should go into effect around April 2024. (via Federal Trade Commission)
CCleaner customer data stolen in MOVEit mass-hack: The company behind the popular optimization app CCleaner said an unspecified number of paid customers' personal information — including names, billing addresses, and phone numbers — was stolen in May. CCleaner's parent company Gen Digital said the breach happened as a result of the MOVEit mass-hacks, for which the Clop ransomware gang have taken credit. CCleaner has millions of customers, but a spokesperson refused to say what number of customers are affected — only that it's around 2%. That's still likely to account for millions of customers. (Disclosure alert: I wrote this story!) (via TechCrunch, @troyhunt)
~ ~
THE HAPPY CORNER
At last, it's the happy corner. Like a gentle breeze of good news on a warm day.
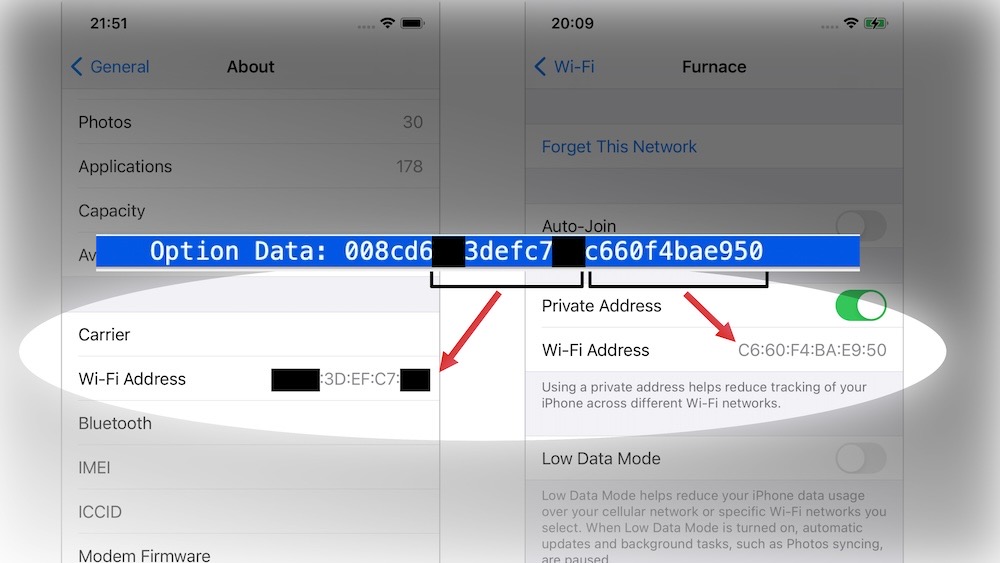
iOS 14 introduced private Wi-Fi (MAC) addresses, which prevented tracking device owners across networks, a new privacy feature that... never actually worked, according to researchers. Worse, the bug also exposed IP addresses when Lockdown Mode was enabled. But(!) here's the good news: now it's fixed in iOS and iPadOS 17.1. The bug is tracked as CVE-2023-42846, and here's more about how the bug worked. Update today if you haven't already.
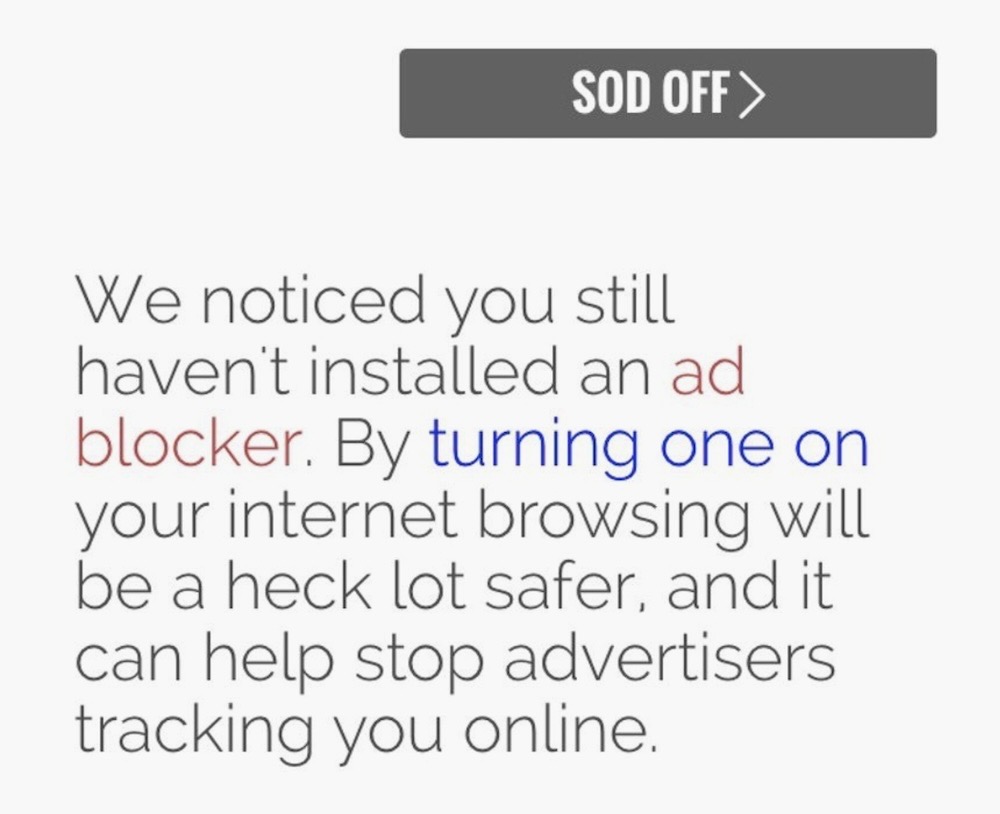
Hats off to @gcluley for considering taking the novel approach by telling his website visitors who don't use an ad-blocker to sod off and get one. Of course, using an ad-blocker is a good thing and we should all do it, not least to piss off the data brokers that perpetually vacuum up our browsing data, but also because it makes the internet look so much better. Wirecutter has a great list of best ad-blockers (it's written by @thorin so you know it's legit).
And finally. If you, like me (always and forever) are wondering what CVEs are being discussed on Mastodon, @kpwn has you covered. Enter cvecrowd.com, which has all the CVE chatter you need to know. Absolutely fantastic stuff; added to bookmarks!
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet this week's cyber cat, Vino, a three year old American shorthair tuxedo tabby rescue adopted in Sonoma, who as you can see here has a particular knack for threat detection... there's one! Just out of shot! A very good boy doing a very important job. Many thanks to his human Tanya L. for sending in!

Please send in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with their name and photo and they'll feature in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that is it for this week! Have a fantastic Halloween (if that's your jazz) 🎃 And don't forget to update your things and patch your devices or you'll be in for a real fright.
As always, if you have any feedback, questions, comments or submissions, please drop me an email. I'll be back same time next week with the usual round-up from the past seven days.
~disappears while making scary ghost-like 'whooo-ing' sounds~
@zackwhittaker