this week in security — october 6 2024 edition
THIS WEEK, TL;DR
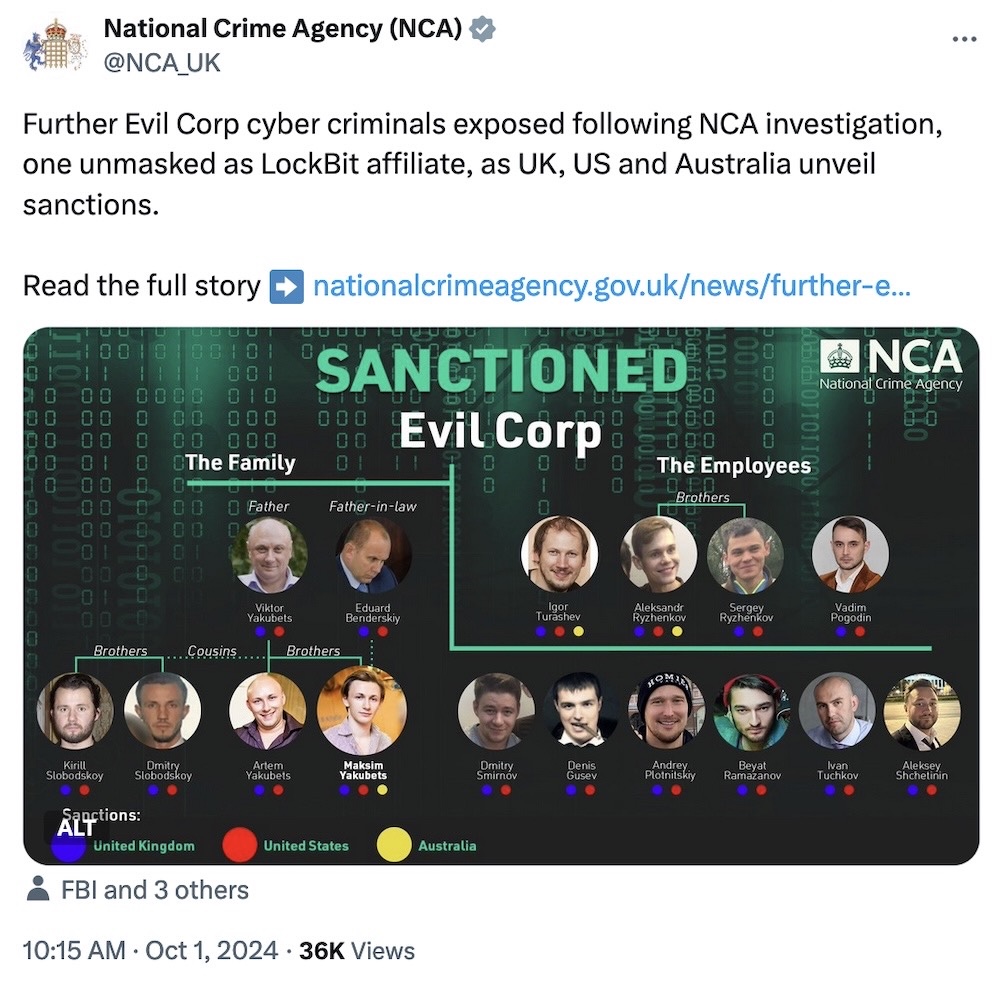
U.K. says LockBit worked with Russia-linked hackers
National Crime Agency: Let's start this week in London, where U.K. officials revived LockBit's previously seized dark web leak site to announce the revealing of a LockBit ransomware affiliate as also a high-ranking member of Evil Corp, a Russian cybercrime gang with links to the Russian government, thanks in part to his dad, a former FSB official. Along with the unmasking, the U.S. issued fresh sanctions and an indictment. The fresh links between the two groups are interesting as U.K. authorities say Evil Corp provided "direct assistance" to the Russian state, in part by targeting NATO countries with hacks, though the details weren't immediately known. It's the latest round of activity from the U.K. and U.S. authorities attempting to take down LockBit for good.
More: Justice Dept. | U.S. Treasury | Bloomberg ($) | TechCrunch | BBC News
Hackers put facial recognition on Meta's smart glasses to dox strangers instantly
404 Media ($): Well this is probably one of the most terrifying things I've seen in a while... A pair of Harvard students hacked Meta's new smart Ray Ban glasses (which have a camera in them — it's Meta, what do you expect?) to feed in raw camera data to a facial recognition service, allowing them to identify people in real-time. Here's the video. Using a large language model (LLM), the students are able to walk up to someone and identify them from their photo — using public data pulled from the internet. It's remarkable and concerning how fast this insta-dox works. One of Meta's not-so-smart spokespeople clapped back that this "could be used with ANY camera, correct?" But it wasn't; it was done using Meta's camera-enabled glasses that look like any regular pair of non-intrusive glasses, which is the point. Genuinely frightening concept brought to life by two incredibly smart students. It is, ultimately, Meta's fault for enabling this project. If you don't like the bad press, maybe don't build things that could be used for abus... oh wait, right, because it's Meta.
More: Ars Technica | I-XRAY [Google Docs] | @AnhPhuNguyen1
How a 'serial hacker' who tried to fake his own death got caught
TechCrunch: Jesse Kipf was a prolific hacker who brokered access to systems he hacked to other cybercriminals. Then in early 2023, Kipf tried to fake his own death by breaking into a U.S. state government's death registry. But Kipf made a couple of critical errors that led FBI agents right to Kipf's front door. Here's the wild inside story of how Kipf got caught, and ultimately sentenced to seven years in prison.
Archive: Justice Dept. | More: @lorenzofb
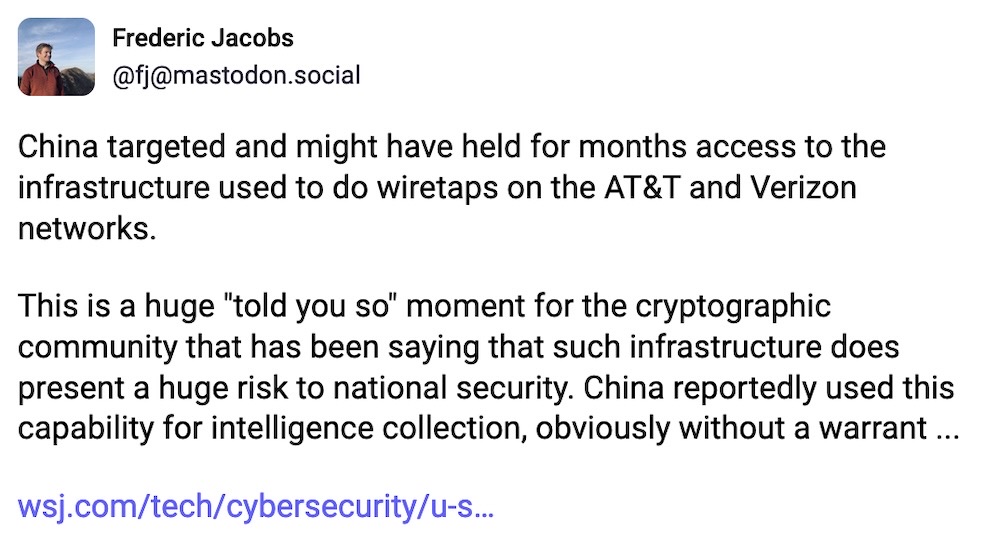
China hackers targeted U.S. wiretap systems
Wall Street Journal ($): What is old is new again. Young'uns, gather round. Back in the '90s when cell phones were becoming a thing and the internet was still in its early days, the U.S. government decided to pass a law called CALEA that added a legal backdoor every phone company and ISP so that the feds could wiretap phone and internet traffic at will (with a warrant... sometimes!) Sounds bad, right? The OG crypto folks (aka cryptographers) warned for years that there's no such thing as a secure backdoor (and subsequently went on to make this point several times during the "Crypto Wars" of the 2010s, too). Skip to 2024, and now we have Chinese-backed hackers — aka Salt Typhoon (more on this here) targeting these very wiretap portals at phone companies and ISPs, such as AT&T, Lumen (previously CenturyLink), and Verizon at least. According to the WSJ, the hackers engaged in a "vast collection of internet traffic" that these portals allow access to. Thanks so much to the Congress of 1994 for screwing up 30 years later. What's weirdly just as depressing is that some of these very same lawmakers are still in office...
More: @dnvolz | @mattblaze
~ ~
THE STUFF YOU MIGHT'VE MISSED
Collapse of national security elites' cyber firm leaves bitter wake
Associated Press: Remember IronNet? You probably do, even if the company didn't really get up to much, let alone make money. Founded by former NSA director Keith Alexander, after he was shot out of the government's retirement cannon after losing a huge cache of highly classified documents stolen by a former NSA contractor... I digress... IronNet eventually collapsed after years of mismanagement by top leadership and allegedly engaging in "questionable business practices" and "produced subpar products and services." Actually, it sounds like most of the cybersecurity product world, except, IronNet failed to keep up appearances, and left a trail of unemployment — and anger — in its wake.
Zimbra bug exploited by cc'ing email addresses
Ars Technica: Attackers are actively exploiting a critical-rated vulnerability in mail servers sold by Zimbra in an effort to plant backdoors, per researchers. Zimbra says the bug, CVE-2024-45519, is now fixed but for a time allowed unauthenticated attackers to plant a backdoor on an affected server by sending an email to the target, with a ton of obfuscated code in the cc: field, which when opened by the server plants the backdoor. The folks at @Shadowserver have data, and more from Proofpoint's @justicerage and the excellent @wdormann.
![Ivan Kwiatkowski toot: "If you're using @zimbra, mass-exploitation of CVE-2024-45519 has begun. Patch yesterday. Malicious emails are coming from 79.124.49[.]86 and attempting to curl a file from that IP," followed by a screenshot of the cc: field in a Zimbra email showing obfuscated shellcode.](https://this.weekinsecurity.com/content/images/scraped_images/31e4d533-1d78-71fa-2e4a-f29a7273ec5a.jpeg)
As 23andMe circles the drain, what happens to the DNA data?
NPR: If you haven't already asked to delete your data from 23andMe, the sinking DNA genetic testing company that last year had a catastrophic data breach, now would be a good time. Here's where and how you can delete your data. 23andMe faces removal from public markets and the company's board members recently resigned en masse. If 23andMe goes private or gets sold, so does your private DNA data. Don't give people grief for using a service that ultimately let down its customers (in a multitude of ways) — just go and delete your data while you can.
~ ~
OTHER NEWSY NUGGETS
Crikey, mate! Another major Aussie data breach: G'day to everyone except I-MED, Australia's biggest medical imaging provider, which left "swaths of sensitive health and personal information" at risk because several company passwords were left online for a year. It looks like there wasn't a huge breach of data, but that the access itself is pretty telling. Big companies are still dealing with the same basic security issues from yesteryear, it's quite embarrassing. (via Crikey)
Cambodia arrests cyber journalist: Award-winning Cambodian freelance journalist Mech Dara, whose work has been vital in exposing cyber scams and human rights violations, has been arrested by Cambodian officials, leading to resounding criticism by rights and journalism groups. Repression against journalists in Cambodia is not unusual. Here's hoping for Dara's speedy and safe release. (via The Record)
Domains seized, ColdRiver disrupted: Those pesky ColdRiver hackers, who researchers have attributed to Russia's FSB, are back with a series of cyberattacks aimed at targeting civil society an...d it's gone again, after Microsoft asked a court to seize the hackers' domains. More than 100 websites were seized in this latest round targeting the group. Will it be enough to knock ColdRiver off the map for good? Probably not, as is the nature of advanced persistent groups. (via Justice Dept., Citizen Lab)
Mysterious zero-day hits Rackspace: Rackspace took its monitoring dashboards offline after a zero-day was exploited in one of its applications provided by ScienceLogic. Details remain a mystery, however. ScienceLogic won't say what or where the affected issue is, so now we have an actively exploited zero-day and practically nothing to work with. (via The Register)
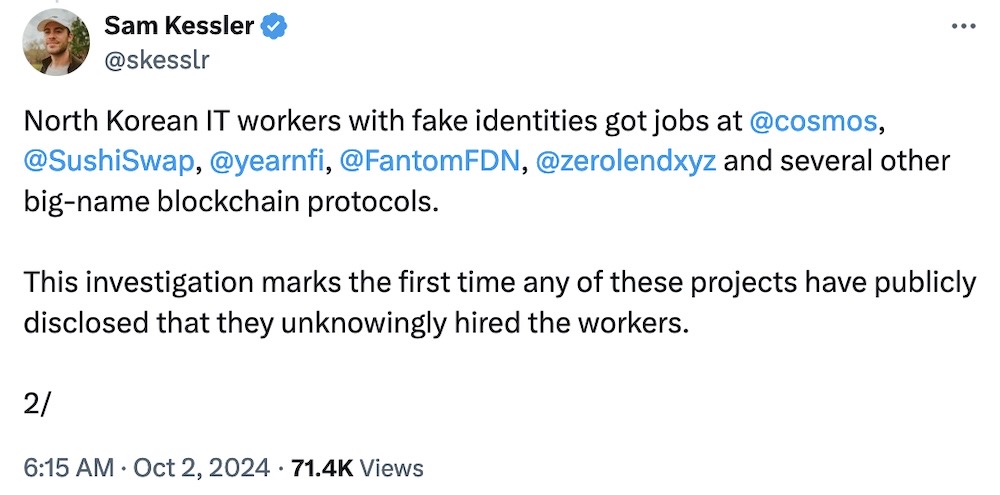
North Koreans infiltrating U.S. crypto industry: More than a dozen blockchain firms inadvertently hired undercover IT workers (read: spies) from North Korea, presenting a major cybersecurity (and sanctions!) risk. The workers used fake ID documents, successfully navigated interviews, passed reference checks and presented genuine work histories. What do they want? Crypto! What do they want it for? Nuclear weapons! More from @skesslr in the tweets, and @SwiftOnSecurity, because this could well affect you. (via Coindesk)
~ ~
~ ~
THE HAPPY CORNER
Finally, and not a moment too soon. Here's the happy corner.
We're long overdue on our long-running series of What Can Doom Run On? This week, it's the turn of quantum computers. As @Lumorti notes, there has yet to be a single practical use for quantum computers. "This changes today, with the release of Quandoom, a port of the first level of DOOM designed for a quantum computer." *audible gasps* — and it (kinda) works! If you're wondering how it functions, PC Gamer has you covered — also, this might be the best news headline of the week.
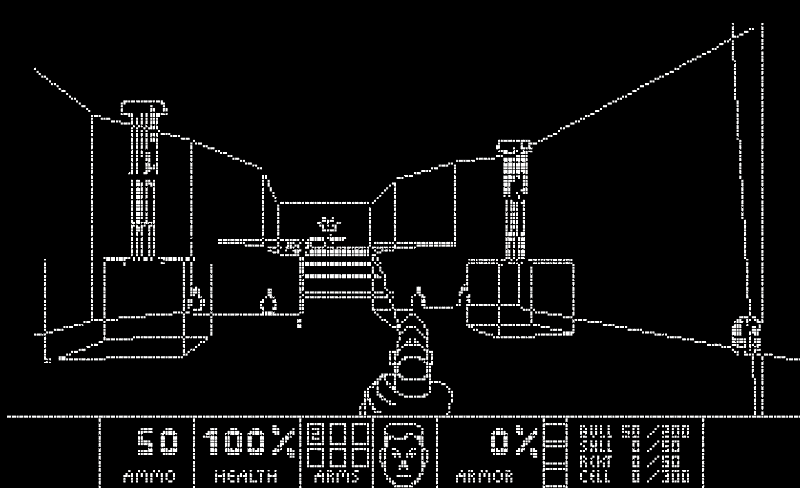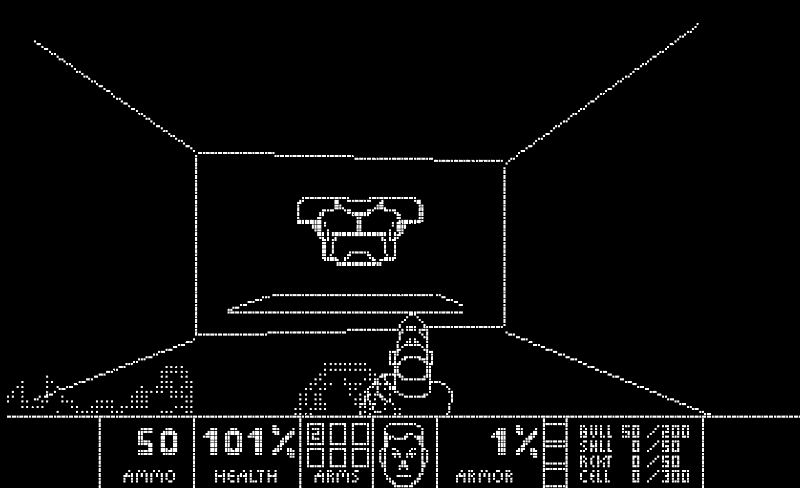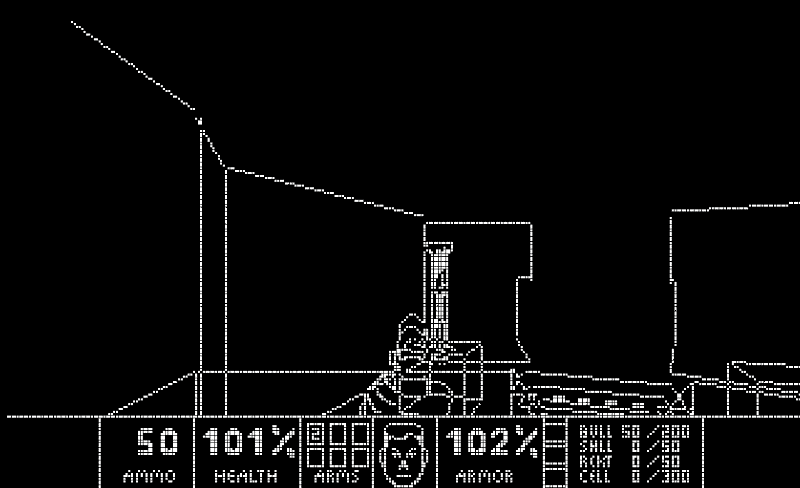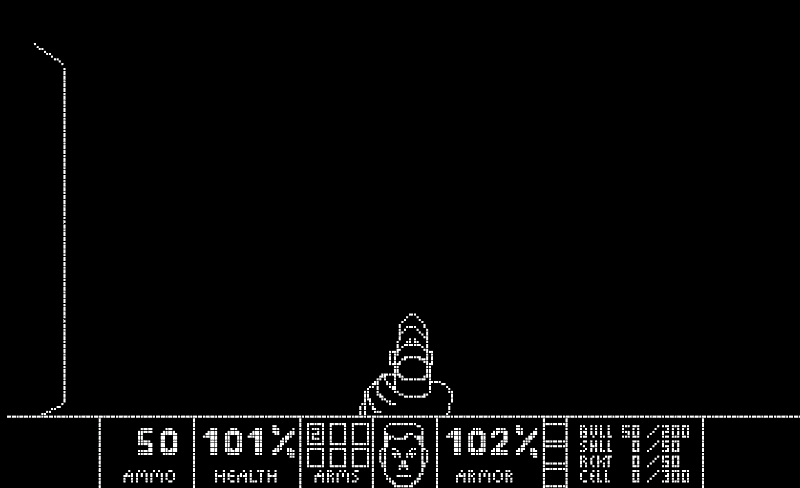
In excellent news, @CISAJen has spoken: the U.S. election is secure and there's no chance that a foreign adversary can change the election results. That's right, not Iran, nor Russia or China can alter the final vote count. But there are plenty of things to keep a close eye out for, like misinformation, disinformation and undue influence (yes, even from bad actors here in the United States — you know who!). Remember to check your voter registration (and actually register — go to vote.gov!). We got this, America. More from the Associated Press on Easterly's comments.
Psssst — hey kids: While you're here, here's some very simple advice on how to stop apps and ads tracking you on your iPhone and Android devices. Thank the folks at the EFF!
Happy Cybersecurity Awareness Mo... oh..., turns out it was all just a lobbying effort to prevent actual cybersecurity regulation. Look, Cybersecurity Awareness Month happens every year and while some appreciate the general sentiments, in reality, we should be cybersecurity aware every day, not just for a month. Maybe if companies stopped laying off huge swathes of their staff and stopped approving exorbitant bonuses and compensation for their executives, maybe we wouldn't have some of the biggest data breaches in living history still happening because of fundamental and basic cybersecurity measures, like password reuse and lacking MFA.
OK, fine. I concede that there's one good thing that comes out of Cybersecurity Awareness Month, and that's @RGB_Lights' excellent meme game. And on that note, next time a company says there's "no evidence" of a data breach, well, here's your final thought for the week.
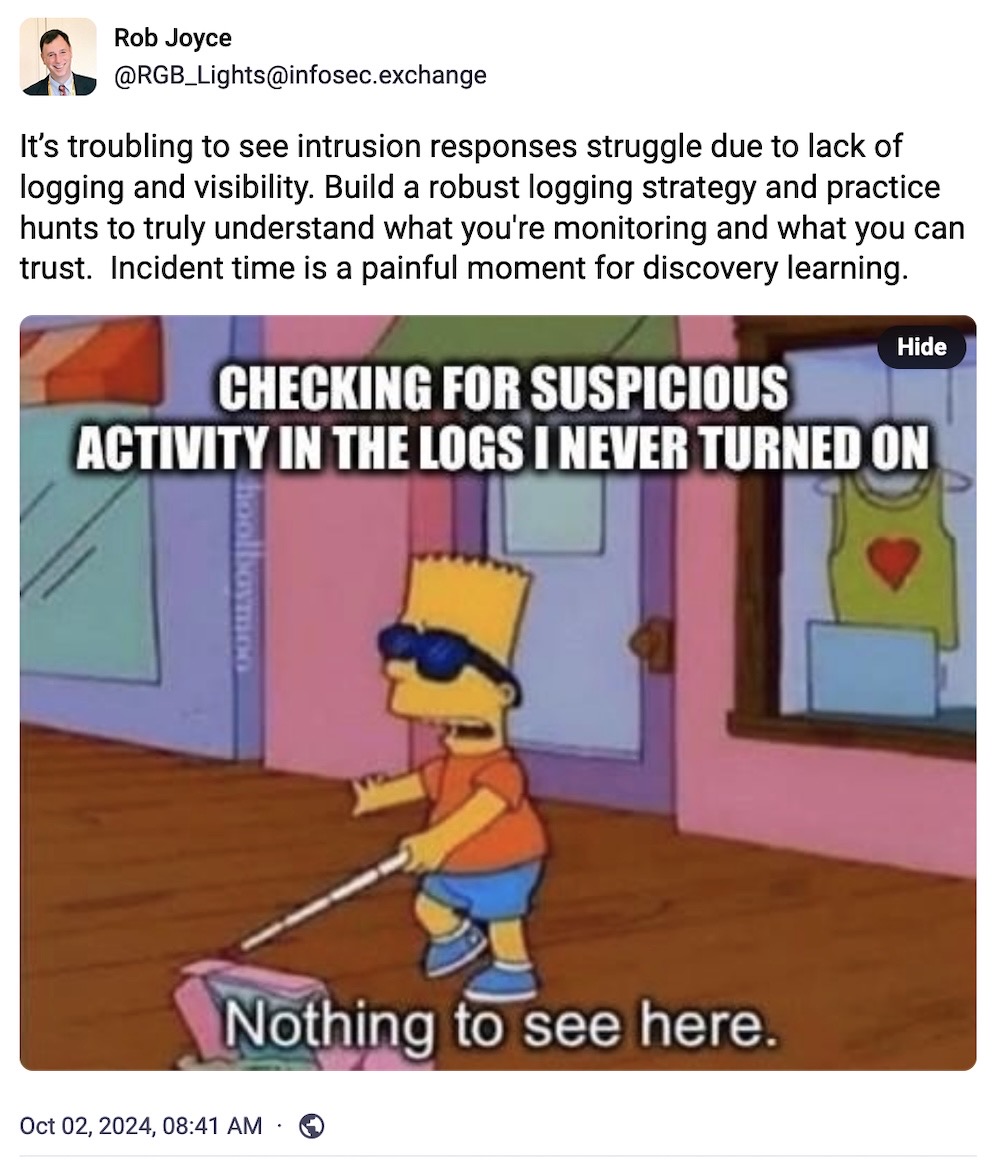
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week we have a ... two-for-one cyber-dog special (an extremely rare event). Here we can see Daisy (the brown pup) and Bear (the white pup with brown ears), caught by their human plotting their next red team engagement. Many thanks to Omar S. for sending in!

Send in your cyber cats! (or a non-feline friend). You can email any time with a photo with their name, and they'll be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
And that's all the news for now. Same time next week? I'll be back at the usual time with your rundown of the week's big news — bring your strongest coffee. I bet we'll hear more on those ISP breaches, too.
As always, you can reach out at any time by email with anything for the newsletter, or just to get in touch!
Take it easy,
@zackwhittaker