this week in security — october 8 edition
THIS WEEK, TL;DR
European spyware consortium supplied despots and dictators
Spiegel International ($): Meet the Intellexa Alliance, the name of a shadowy group of European companies that supplied authoritarian regimes with powerful spyware. Much of the reporting comes from the Predator Files, an investigation named after the spyware that's developed by North Macedonian startup Cytrox and sold by Intellexa. Both companies are part of the secretive group, which you can visualize here; it's messy! The Predator spyware has been used to spy on journalists — including the main subject in the Spiegel piece — as well as politicians in what was dubbed "Greek Watergate." The spyware has also been sold to Egypt, Malaysia, Indonesia, and a Libyan warlord. Amnesty International has its own analysis of the files, which includes never-before-seen screenshots of the Predator spyware dashboard. Expect more reporting to come out of this investigation.
More: Washington Post ($) | Haaretz ($) | Amnesty International | @RonDeibert
Clorox breach linked to group behind casino hacks
Bloomberg ($): The group called Scattered Spider, known for its recent social engineering-led cyberattacks targeting hotel and casino giants MGM and Caesars, is also said to be behind a cyberattack at consumer products maker Clorox. The company has said little about the incident, which began in August, except that it's likely to take a financial hit following the incident, which continues to experience hobbled operations. Somewhat separately, MGM said this week that the hacking group stole customers' information, including government-issued IDs and Social Security numbers. The breach is expected to cost MGM at least $100 million, which so many news sites led with, but the real impact is to the customers whose information was compromised.
More: Reuters ($) | TechCrunch ($)
Microsoft patches spyware zero-day bugs, but won't say if products were exploited
Microsoft: The mess left behind by two recently discovered zero-days in popular open-source libraries webp and libvpx has been far and wide. So far, the bugs have affected Apple and Android devices, browsers, email clients, and more. These two bugs have been used to plant spyware, according to researchers, and Apple, Google, and others have released patches to block those spyware attacks. Microsoft said several of its products were also affected by the bugs, but declined to say if Microsoft's own products were exploited, or even if the company has the ability to know. Cool, cool. If you haven't updated your apps, devices, browsers or anything in between any time recently, this weekend would be a great time to do that.
More: TechCrunch | Bleeping Computer | Ars Technica
ICE, CBP, Secret Service all illegally used smartphone location data
404 Media ($): Bombshell reporting from 404 Media again — this time, a report from the DHS's inspector general watchdog said several DHS agencies that relied on buying commercially available smartphone location data without a warrant broke the law. The report also recommends ceasing the use of location data until it can receive the necessary approvals, which ICE refused to do. CBP has since discontinued accessing location data, but not before a CBP official was caught using this kind of data to spy on coworkers. Clearly this data can't be trusted in anyone's hands.
More: OIG Report (DocumentCloud) | @josephfcox
~ ~
THE STUFF YOU MIGHT'VE MISSED
23andMe user data stolen in targeted attack on Ashkenazi Jews
Wired ($): Wired is reporting that DNA genetic testing company 23andMe confirmed that some of its users' data was compromised in what looks like a credential stuffing attack. 23andMe hasn't yet verified that the data is genuine, so clearly a fluid situation. Much of the data was published online to a known hacking forum, which included broad genetic ancestry results, and not raw genetic data. The stolen data includes information on Ashkenazi Jews and thousands of users of Chinese descent. 23andMe's communications have been a hot mess about this incident. Keep a close eye on this story; we're likely to learn more.
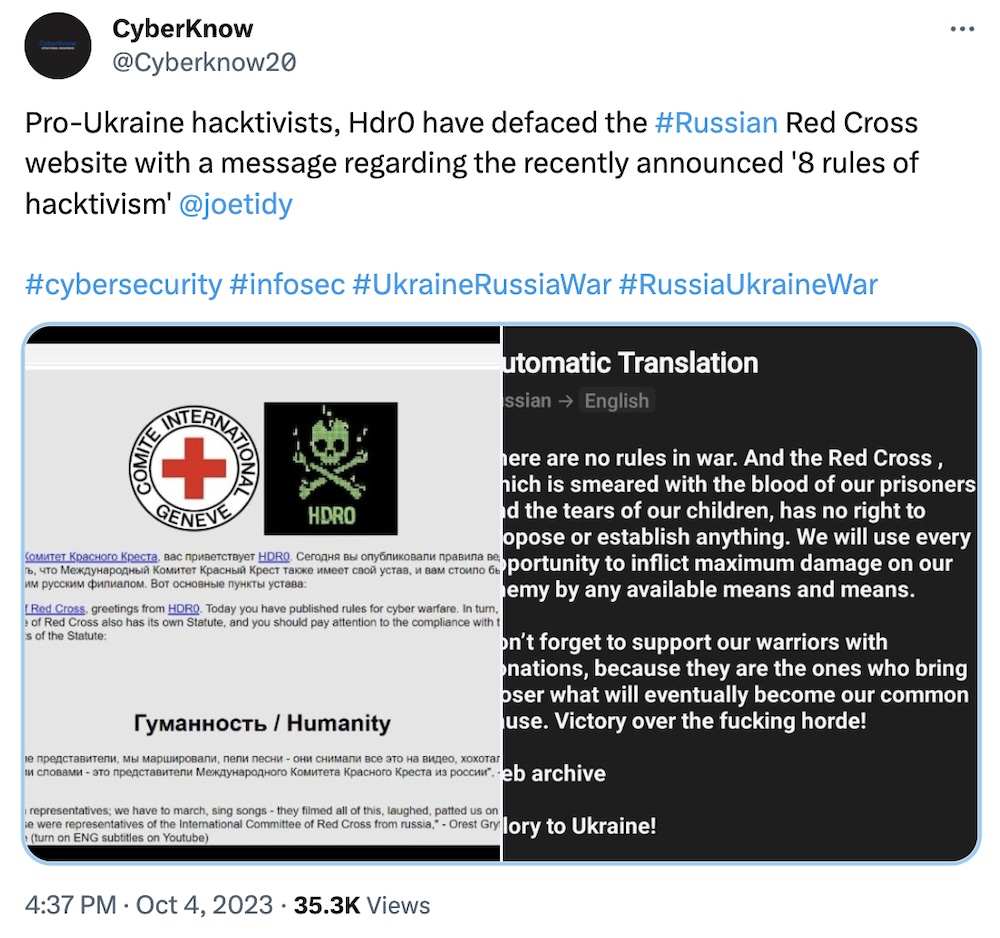
Rules of engagement issued to hacktivists after chaos
BBC News: The International Committee of the Red Cross published for the first time rules of engagement of how hackers and hacktivists should operate during conflicts, especially with the Russia-Ukraine war ongoing but also with further conflicts around the world. Ukraine said it's going to make best efforts to follow the rules, while Russia-linked operations like Killnet said they are ignoring the advice. "Why should I listen to the Red Cross?" said Killnet's leader. Hacktivists took the news well by defacing Russia's Red Cross website with a reminder that the Russian government was the one that started all this.
An analysis of Exim bugs now that patches are out
watchTowr Labs: Last week we brought you news of Exim bugs. Some bugs were fixed, but two of the outstanding bugs allowed for remote code execution. Those fixes were released this week. A blog post by watchTowr Labs broke down the bugs in more detail. The good news: "This one is more of a damp squib than a world-ending catastrophe."
EU Parliament wants journalists to have better protections from spyware
The Record: Lawmakers in the European Parliament want a full blanket ban against spyware on the bloc, saying it should "under no circumstance be considered necessary and proportionate under Union law." It comes as lawmakers continue to debate whether spyware can ever be used to target journalists. The journalist writing this newsletter would say no, but the draft also says that spyware could be planted on journalists' phones "on a case-by-case basis." It seems like lawmakers are still hashing out details. Given so many journalists have already had their devices hacked by spyware, maybe the only way out of this is by banning spyware!
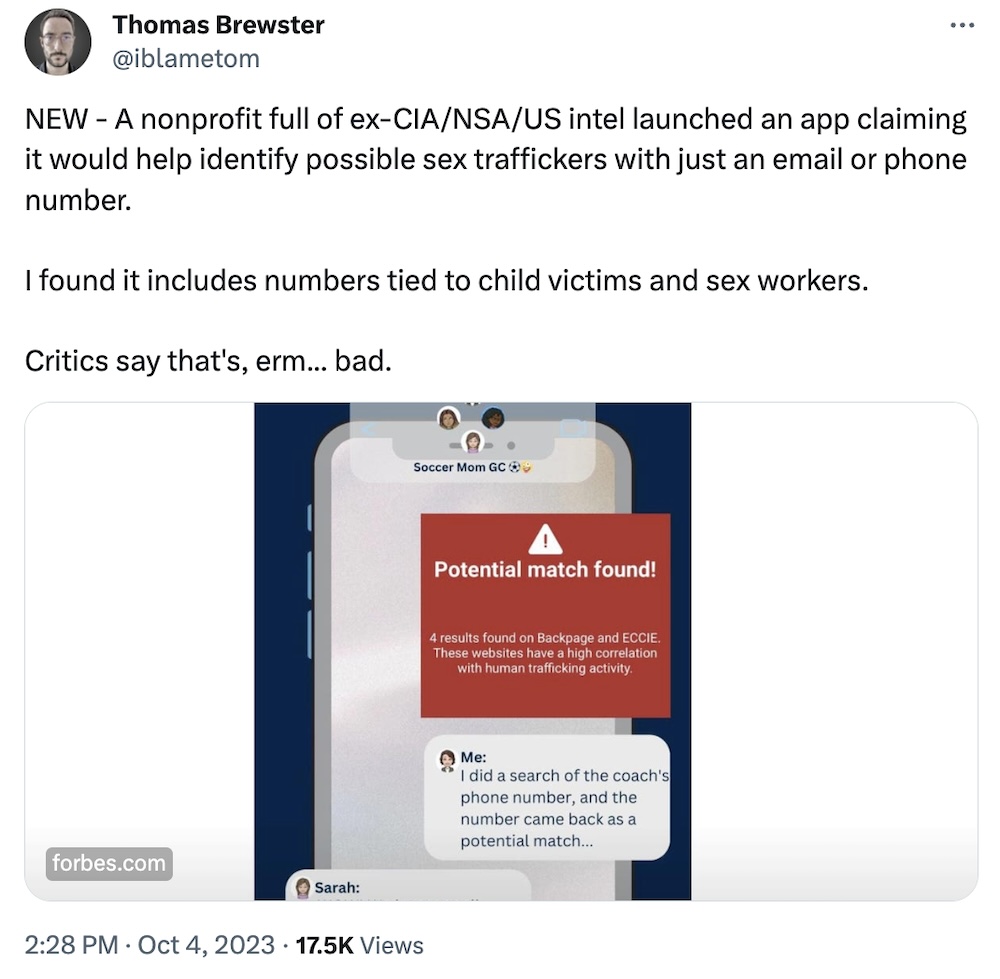
Non-profit's app promises to identify sex traffickers. Critics say it endangers survivors
Forbes ($): Anti-human trafficking nonprofit called DeliverFund built an app called HT Safeguard, a consumer-facing app designed to help protect kids from human trafficking. But Forbes found that the app's database also includes phone numbers tied to sex workers and minors who are trafficking victims, "potentially implicating innocent people in illegal activity." The EFF called this app "clumsy." That's one word to describe it. DeliverFund didn't comment, but by the looks of it, the ongoing legal spats between the founders seem to be taking up most of their time and energy. Great work here by @iblametom. Meanwhile, Wired ($) has a mini-profile of Emma Pickering, works at Refuge, the U.K.'s largest domestic abuse organization, where Pickering heads a team that helps women secure their devices.
Rapid7 says new Atlassian zero-day is 'trivially exploitable'
Rapid7: Atlassian has confirmed a maximum vulnerability severity score of 10.0 for a new bug in Confluence Data Center and Confluence Server that could allow malicious hackers to create unauthorized admin accounts. The bug is being exploited in the wild. Not great! Rapid7 details the bug. But questions remain as to whether Atlassian's own systems were affected by the same bug, and if not, why?
~ ~
OTHER NEWSY NUGGETS
Prospect hack 'far more debilitating' than acknowledged: The hack at Prospect Medical Holdings, a company that operates 16 hospitals and dozens of outpatient facilities, was hacked — badly — earlier this year. New reporting by local press, citing Freedom of Information requests, found that the hack was a lot worse than the company let on. The incident was so bad that Yale executives, which were set to acquire the beleaguered Prospect, "have begun to question whether acquiring Manchester and Waterbury hospitals remains a prudent business decision." If the sale doesn't go through, three hospitals "may no longer be financially viable." Forget the company for a second; think about its employees and the local residents who will suffer because of all this — some of it brought on by Prospect's own executives, clearly. (via Connecticut Mirror)
Tricking Bing Chat into solving CAPTCHAs: Not to alarm anyone but it turns out robots can understand CAPTCHAs. You just have to ask the right way. Just like you could with previous chatbot jailbreaks, sometimes all you need to do is ask the same question you want the answer to but as if the request came from your phantom deceased grandparent. This so-called "grandma exploit" meant that it was possible to trick Bing Chat into unscrambling a CAPTCHA by asking it to read the CAPTCHA as if it was engraved on a non-existent grandmother's necklace. Jailbreaks crack me up, but please don't ever use them to make actual napalm... (via Ars Technica)

IronNet, founded by ex-NSA director, shutters: In an SEC filing, IronNet said it has ceased operations, let go of its remaining staff, and shut down. The collapse of IronNet, once a promising cybersecurity startup, comes soon after its main investor, C5 Capital, dropped a final million to keep it afloat in recent weeks. IronNet was founded by former NSA director Keith Alexander, who mic-dropped out of the company he founded earlier this year and was replaced with C5 Capital's chairperson. Alexander still serves on several other companies' boards, if you were wondering so I'm sure Alexander is going to be just fine. But spare a thought for the dozens of employees who are now out of a job because of crappy corporate management. (Disclosure: I wrote this story.) (via TechCrunch)
U.K. to use passport database for facial recognition: The U.K. takes one step deeper into authoritarianism by announcing plans to use the U.K.'s passport database to identify criminal suspects using CCTV, doorbell cameras, and dashcams. Yes, nothing quite says forcing the population into mass-contributing to the facial recognition surveillance state by... getting a passport. This is the brainless idea from U.K. junior government minister Chris Philp, who said he wanted a system that would enable officers to "press one button" and "search it all." (via The Record, BBC News)
Lyca Mobile was hacked, causing network disruption: U.K.-based mobile virtual cell network Lyca Mobile experienced a major outage following a cyberattack (that smells like ransomware). Lyca deliberately hid its security notice from search engines (using "noindex" code), making it more difficult for customers to find, and botched its notice by exposing its back-end CMS (containing the security notice post!) to the internet without a password. And then Lyca confirmed customer data was stolen, though it doesn't yet know how much or exactly what, but likely to include customers' personal information, ID cards, passports and more. (via Lyca Mobile)
~ ~
~ ~
THE HAPPY CORNER
This is the happy corner. Nothing but good things from here — and there's a lot.
This week, the friendly folks at Consumer Reports released Permission Slip, a new app for iOS and Android that lets you verify your identity and process a ton of opt-out and deletion requests to data brokers and consumer companies on your behalf. It's a pretty great app for those who want to blast through a ton of data brokers at once. Of course, there's a full FAQ and details about how the app treats your data.
Mastodon's favorite infosec hub, infosec.exchange, has crossed the two million post mark this week. Donate today to support the instance!
Amazon said that beginning 2024, all root users signing in to AWS must use multi-factor authentication, which is probably the least evil thing Amazon has done in recent years. Speaking of "do no evil," Google said it'll give Pixel 8 (and Pixel 8 Pro) customers seven years of security updates. Good!
Moving on. Anyone seen the giant sphere in Las Vegas recentl... oh.

And finally, this week, since we're rapidly approaching the season, please send in your best scary security-themed pumpkins. I'd love to put the best ones in a newsletter before Halloween.

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet Nymeria, this week's cyber cat. This is simply titled, "gone phishing." No notes, perfect job. Many thanks to Julian N. for sending in!

Keep sending in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with their name and photo and they'll feature in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's all for this week's very busy newsletter. I'm off to have some breakfast and top up my coffee. Have a good week, and see you next. If you have any feedback, feel free to drop me an email.
All my best,
—@zackwhittaker