this week in security — september 1 2024 edition
THIS WEEK, TL;DR
China linked to targeted attacks on ISP software
Black Lotus Labs: Security researchers at Lumen's Black Lotus Labs found evidence that Volt Typhoon, the China-backed hackers that have burrowed into tons of U.S. critical infrastructure in the event of a future conflict with China (think Taiwan), are also targeting U.S. internet providers — specifically software they run for managing network configurations. The Chinese hackers are targeting Versa Director, notably a bug that allows the planting of web shell code on the server, as part of efforts to target downstream would-be victims. The zero-day bug — which dates back to mid-June — is now fixed, but Versa blamed its customers for not patching sooner. Uh-huh, well that's certainly a choice. As you'd expect, the Post ($) story has a solid run-down of the situation.
More: CISA | Ars Technica | KrebsonSecurity | TechCrunch | The Record
Google says Russia reusing exploits made by spyware makers
Google TAG: Google's Threat Analysis Group, the security researchers focused on government-backed threats, said this week that cyber-spies working for Russia's foreign intelligence service (aka, APT29, or the FSB) were caught reusing iOS and Android-targeting exploits developed earlier by spyware makers Intellexa and NSO Group. The exploits were found buried in hidden code on Mongolian government websites and designed to steal credentials from what looks like Mongolian government employee email accounts — so, understandable that Google might think Mongolian civil servants were likely the target. How did the FSB get the exploits, you might be thinking? Google said it isn't sure, but didn't rule out the FSB buying the exploits once they are no longer zero-days (ie. since the exploits can still be useful for hacking unpatched devices). But Google said that this is what happens when spyware makers develop exploits that proliferate to "dangerous" threat actors like the Russian government.
More: Wired ($) | TechCrunch | Cyberscoop | @mattjay tweets
Iran caught using 'Tickler' malware to target governments and satellites
Microsoft: Iran, not content with trying to faff with the U.S. presidential election, is now trying to score a big win in space — targeting satellite communications. The Iran-backed hackers, known as APT33 (or Peach Sandstorm), are using password spraying attacks (which by all accounts seem to be pretty effective, going to show simple security protections can help!) and deploying malware that Microsoft calls Tickler — (why?!) — as a custom multi-stage backdoor. Wired ($) breaks down Microsoft's research in more detail, as does a Microsoft tweet thread. All in the same week that CISA confirmed another Iran-backed group, this one called Pioneer Kitten (again, these names??) that apparently moonlights with a ransomware gang, likely in support of Iran's goals but "not sanctioned" by the regime.
More: CISA | The Register | @snlyngaas
North Korean hackers exploited Chromium zero-day to steal crypto
TechCrunch: So, that's China, Russia, Iran... now let's wedge in North Korea to complete our quad of naughty hackers. Yes, North Korea has been found exploiting a Chromium zero-day (read: exploited before it was patched) to steal — yes, you guessed it — crypto, all so the country can build up its sanctioned nuclear weapons program. This is the tenth zero-day in Chrome this year, reports Bleeping Computer. Google patched the Chromium bug on August 21, two days after Microsoft first spotted the North Korean hackers exploiting the bug. Since it's a bug in Chromium, any browser that relies on it — Google Chrome through Microsoft Edge — were affected. Microsoft added that the group it calls Citrine Sleet (seriously, none of these names make sense!) deploys fake cryptocurrency trading sites that can plant a custom Windows kernel rootkit(!) on a targeted computer, which means it's absolutely game over for the victim's device data.
More: Microsoft | SecurityWeek
~ ~
THE STUFF YOU MIGHT'VE MISSED
Texas to spend millions on warrantless snoop tech
Texas Observer: Police in Texas will spend close to $5.3 million on a contract with a company called Cobwebs, which makes a tool called Tangles that can allow police and investigators to geofence over an area and track mobile movements without needing a warrant. The tool relies on data gathered from smartphones, such as location data, which is collected from apps and shared with others. Good thread by @FrancescaDnunz. There has never been a better time to yeet your phone into the nearest large body of water.
U.S. Marshals concedes data was stolen in earlier ransomware attack
The Record: Meanwhile, speaking of law enforcement, the U.S. Marshals said it was aware of a claim by a ransomware gang that it has close to 400 gigabytes of stolen data, but that the incident was not a "new or undisclosed incident." What it looks like is a ransomware attack from February 2023 has come back to bite the Marshals in the behind. The federal law enforcement agency has no idea how the Hunters ransomware gang got the stolen data — but doesn't change the fact that it did — and that it appears to contain sensitive law enforcement materials, including apparent details of electronic surveillance.
Google uncovers Iranian counter-intel operation, two years after reporter
Google Cloud: A new blog post by Google looks at an Iranian counter-intelligence operation involving dozens of fake recruiting sites aimed at trying to hook Iranian citizens into working for overseas governments. The operation dates back to at least 2017, and was initially discovered back in 2022 by former journalist @arawnsley (whose tweets on this are great). Excellent research and findings here.
Bypassing airport security via SQL injection
Ian Carroll: Excellent research here by way of @iangcarroll and @samwcyo, who found a simple SQL injection bug in a TSA program called Known Crewmember, which, as you might guess, is a system at airport security for allowing pre-cleared pilots and cabin crew to skip security screening checks. TSA sought to fix the bugs, but did an absolutely awful job of trying to cover the fact that the agency had royally messed up. The full blog post is worth the read. Meanwhile, in other news: Seattle's hacked airport is still largely offline, even if planes are still landing and taking off. Here's what it's like to fly through the hacked airport.
City of Columbus sues man after he discloses severity of ransomware attack
Ars Technica: Prepare to get extremely cross. The mayor of the city of Columbus in Ohio said that data stolen in a recent ransomware attack targeting the city was "unusable" by the attackers. Turns out that was blatantly wrong, and a security researcher proved it by showing local reporters how easy it is to access the stolen files. (That's kinda the point of these ransomware and extortion tactics; these gangs publish the data so it's easier to extort the victims.) Instead of accepting that the city has a bigger problem than it clearly realizes, the city took the researcher to court and secured a restraining order. So, to be clear, the mayor's response is to blame other people rather than handle its scandal. Good luck finding help going forwards. Clearly the city of Columbus in Ohio is hostile to security researchers.
~ ~
OTHER NEWSY NUGGETS
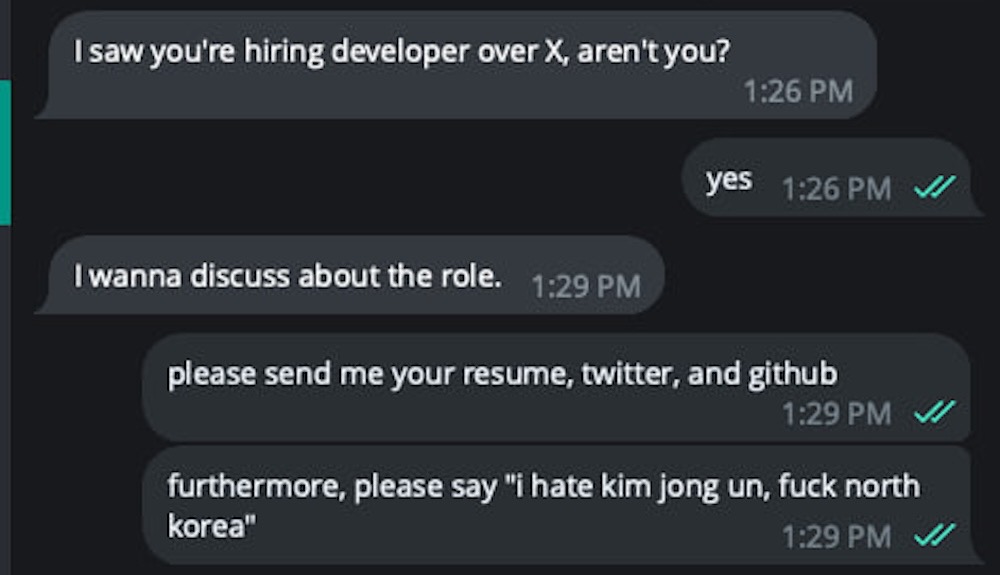
North Korean spies hate this one weird trick: Here's a novel... if not somewhat unorthodox technique for trying to weed out suspected North Korean spies trying to earn a place at your company so they can steal your secrets. (It's a real problem!) When asked by one recruiter to send their resume, Twitter, Github, and a short note saying, "I hate Kim Jong Un, f**k North Korea," the applicant immediately vanished. Extraordinary problems require extraordinary solutions. But maybe check with your folks in HR, first... (via @PopPunkOnChain)
Telegram boss' phone hacked: Pavel Durov, the CEO of Telegram bailed by French prosecutors who was told he can't leave the country amid a raft of criminal charges against him, had his phone hacked in 2017 by a joint French and UAE operation. According to the WSJ, French authorities were "acutely concerned about Islamic State’s use of Telegram to recruit operatives and plan attacks." Durov is a high-profile target: perhaps it's worth wondering how many other tech executives have had their phones hacked? Remember Jeff Bezos? (via Wall Street Journal ($))
Mirai's back, baby: Not that it ever really went away, the Mirai botnet — which was open-sourced so anyone can cause chaos with the power of enough hacked devices — is now drawing power from an unpatchable zero-day vulnerability in the AVM1203 widely used surveillance camera made by Taiwan-based firm AVTECH, which has no plans to fix. By exploiting the bug, known as CVE-2024-7029 — per Akamai — the Mirai botnet can break in and harness the many, many hacked devices' bandwidth to collectively pummel targets with floods of junk internet traffic. (via Ars Technica)
~ ~
THE HAPPY CORNER
It's the happy corner. Rejoice!
Remember the One Million Checkboxes website? As the name suggests, it was a collection of one million checkboxes that went viral overnight. Check a box, and it's checked for everyone. Uncheck a box, and it's unchecked for everyone. But, for a brief moment a few days in the site's infancy, its owner thought the site had been hacked. Well, it turns out a friendly Discord group figured out a way to hack it (in the nicest way) to stress-test the site with as much as it can handle. Turns out, quite a lot — and the friendly hackers were able to write messages, draw images, and animate a GIF. The full blog post is worth your time. Of all the creative people I've met in my time, hackers have to be way, way up there.
Moving on. Error 502: very bad gateway.
Here's a blast from the past. The National Security Agency finally released (in response to a FOIA — thank you, MuckRock!) a 1982 lecture by Admiral Grace Hopper, widely known as a pioneer in early computing. The full YouTube video is online, and it's amazing to see how much stands up today. Cyberscoop looks at the video and what Hopper predicted – and how far we've come.
Signal, the world's favorite end-to-end encrypted messaging app, recently turned ten. Incredible to think that Signal started out as the janky apps RedPhone and TextSecure — but have gone on to secure much of the world's communications. Wired ($)'s @agreenberg sat down with Signal president Meredith Whittaker to talk shop, surveillance, AI and more. It's also worth noting, Signal is free but it's not cheap to run, and it needs our help and support to keep protecting millions who rely on it. By the end of reading this interview, you'll feel the jolt of energy you need to take on the world.
And, on this final jaunty note, your weekend moment of clarity.

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
~ ~
CYBER CATS & FRIENDS
Meet Murphy, this week's cybercat. That's the face of a cat whose canarytoken on an airgapped system just triggered. Thanks so much to Matt S. for sending in!

Send in your cyber cats (or a non-feline friend!). Drop me a quick email any time with a photo with their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
Thanks so much for reading this packed edition! For those in the United States, enjoy your Labor Day weekend. I'll be back next Sunday as usual with your roundup from the week. As always, please drop me an email any time with anything you think would be good for the newsletter. Weid, wonderful, cats, and good news galore.
Back next week,
@zackwhittaker