this week in security — september 29 2024 edition
THIS WEEK, TL;DR
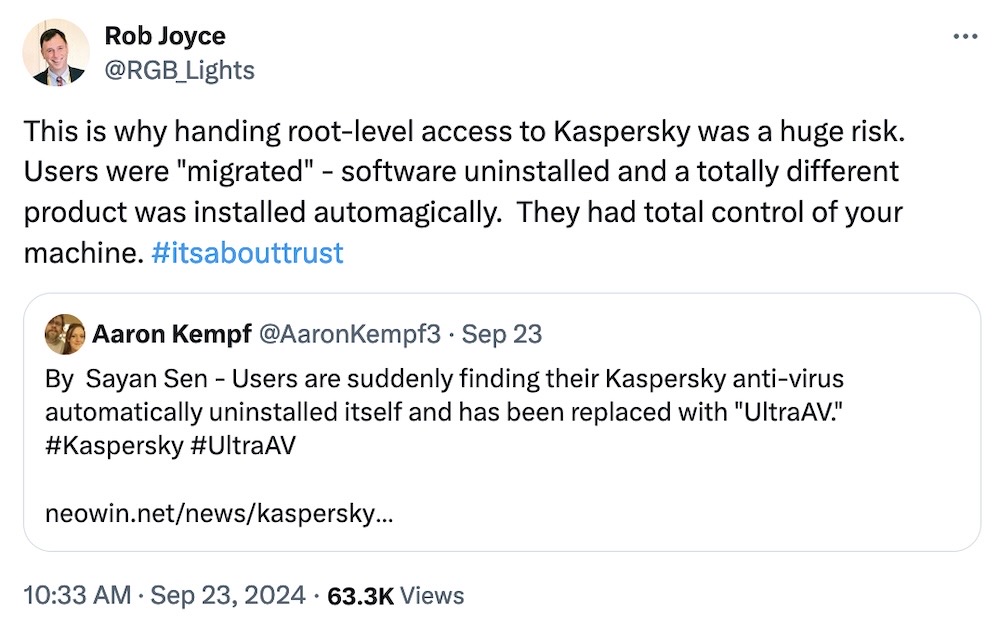
Kaspersky deletes itself, installs UltraAV antivirus without warning
Bleeping Computer: You know what they say, "In Russia, antivirus uninstalls self." Or something like that, but that's exactly what happened this week when Kaspersky force-replaced its antivirus software quite literally overnight with... a completely brand new antivirus called UltraAV, which nobody's heard of and has absolutely no track record. Kaspersky and Pango, the maker of UltraAV, said to the effect of, "everything is fine, trust us!" But a lot of folks don't, and understandably! Kaspersky had until this week to figure out a replacement software for its one million or so customers before a U.S. sales ban comes into effect, preventing Kaspersky from selling or updating its software. This was about trust. Kaspersky could've asked for consent, but it didn't.
More: TechCrunch | Axios | The Register
U.S. charges three Iranians with hacking Trump campaign
BBC News: New week, new indictment. This time it's the Iranian hackers targeting the Trump campaign, because Iran has been on an absolute tear since the killing of Qasem Soleimani in 2020 and vowed revenge, even if that means trying to take out former government officials in the process. That's why Iran hacked the Trump campaign and tried (badly) to leak the stolen files. Turns out the hackers had access even as recently as last week. Three Iranians were charged with the operation; per the DOJ. It's not just the Iranians, but also the Chinese and the Russians working to influence the election. And please, do not forget to register to vote!
More: Justice Department | NCSC | NBC News | TechCrunch | @bing_chris
Millions of cars could be tracked thanks to a simple website bug
Wired ($): Back in the day it took months or years to figure out ways to hack into a car and take over its controls. Nowadays, thanks to the ubiquitous connectivity of practically every car on the road, it's as simple as scanning a car's license plate and... boom, that's it. At least with most Kia vehicles, or dozens of models that represent millions of cars on the road. That's because of a flaw in a Kia web portal that allowed a team of security researchers to essentially use the portal's unprotected API to interact with cars as if they had the keys in person. Tracking a car's location, unlocking the car, honking its horn, and starting its ignition at will. Just normal, normal stuff. Genuinely brilliant findings here. I wish, wish, wish car makers would stop connecting cars to the internet.
More: Sam Curry | @samwcyo

~ ~
THE STUFF YOU MIGHT'VE MISSED
Newly released investigations toolkit helps open source research
Bellingcat: The folks at open source reporting outfit Bellingcat have a new online toolkit aimed at helping folks find the right investigative tool for the job you need. Much of the web's top investigative folks rely on open source intelligence (what's out there in the open already) and this new toolkit is a great place to start, from analyzing satellite imagery and maps, social media posts, transportation data, and archiving. Plus, most of the tools are free. More from @Bellingcat.
Eric Adams told the FBI he forgot his phone's passcode
404 Media ($): Have you ever been indicted so hard that you forgot your own phone's passcode? That's what seemed to happen to New York Mayor (still, at the time of writing, but I had to check) Eric Adams, whose multiple phones were seized by the FBI last November. It's unclear if the feds got access to his phones, because Adams reportedly changed his password from four digits to six and... subsequently "forgot" (heavy wink) the passcode. Uh-huh. Adams was charged with a litany of federal corruption charges this week. New York, where dreams are made and its officials are (allegedly) corrupt.
MoneyGram files data breach notice with U.K. authorities
TechCrunch: MoneyGram, the second largest money transfer service in the world (after Western Union, apparently), was hacked and its website and backend infrastructure nuked during a days-long outage. Its website was down, its app wasn't working, and its spokespeople couldn't respond because their email was down. (That said, MoneyGram's website and email came back and they still ignored us; quite rude!) But MoneyGram didn't ignore their U.K. legal obligations, filing a data breach notice within the mandated 72-hour window as required by U.K. law. That's to say, MoneyGram is saying it had a data breach, but details remain scarce. MoneyGram serves over 50 million people each year... so that could be a spicy one.
~ ~
OTHER NEWSY NUGGETS
"For FEC's sake! Hacked again": Well, hopefully not going forwards, because the FEC, the U.S. government body that oversees federal election finance laws, will now allow U.S. political campaigns to spend campaign funds on physical and cybersecurity purchases. That's a good move, especially since hacking (or at least targeting) political campaigns seems to be the norm these days. Staff and even family members can be a major weak link in the cyber-chain. (via Cyberscoop)
Tor + Tails = ❤️: The Tor Project is merging operations with Tails, the portable Linux-based operating system that's focused on preserving user privacy and anonymity. Tails will be incorporated "into the Tor Project’s structure," allowing Tails to focus more on the product itself while using Tor's resources for easier collaboration and better long-term sustainability. Big fan of the Tor Project, donate today! (via The Tor Project, TechCrunch)
Volt? Flax? OK, now, Salt Typhoon(?!): Looks like we have our third member of the China-backed "Typhoon" family of cyberattackers; Salt Typhoon is the latest disclosed hacking group working for China, allegedly geared towards collection of intelligence from hacked U.S. internet providers, per the WSJ ($) this week... and as somewhat previously reported by the Washington Post ($). That's as well as Volt Typhoon, which is laying the groundwork for disrupting U.S. military operations in the event of a conflict with China (over Taiwan, for example); and Flax Typhoon, a private company based in China that last week was caught by prosecutors operating a botnet on behalf of the Chinese government. Salt, Flax, and Volt Typhoon. Got it? (via Wall Street Journal ($))
The CUPS uproar that wasn't: A series of flaws in many Linux distributions became the talk of the town this week, but the hype (that wasn't) fell short of expectations. Plus, the bugs can be fixed with simple remediation. The bugs are in CUPS, which has to be manually enabled and requires some work to exploit. (via Cyberscoop)
~ ~
~ ~
THE HAPPY CORNER
I'm here again after a week away! Welcome back to the happy corner.
First up, it's time to let go of the mandatory password reset. That's right, the U.S. government's standards body is finally proposing to do away with its long-held view that passwords should be reset after 60 or 90 days. Or, as @dangoodin says, NIST is proposing to no longer recommend some of the "most nonsensical password rules." Huzzah!
Also in excellent news, Semiphemeral is back! (Well, almost). The app, which once allowed you to download and delete your entire Twitter stream until Elon Musk threw a world-class strop and cut off all API access, will soon be back with a brand new version capable of automatically removing your data from the former birdsite. Developer Micah Lee explains his reasoning and efforts behind the new app, and how Semiphemeral will allow you to rid your posts from the hellsite.
And finally, this week. A bonus cybercat meets caption contest. That's the U.K.'s prime minister, by the way, and his family's new kitty (where's Larry, you ask? He's still there!). But who needs the nuclear codes when you've got the spiciest kitten?

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's two-for-one cyber-cats special are Kirby (the beautiful void floof) and Kodo (the handsome gray kitty). I'm told that they can be seen here, taking a quick break from their ever vigilant surveillance efforts. Always monitoring for threats (and treats). Thanks so much to Andy T. for sending in!

Send in your cyber cats! (or a non-feline friend). You can email any time with a photo with their name, and they'll be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
That's it for this week; all the news that you need to know! It's good to be back after a week away, and as usual I'll be back next Sunday with your newsy roundup from the week. In the meantime, you can reach out at any time by email if you see anything fun for the newsletter. It's always great to hear from you (and your cyber-cats!)
All my best,
@zackwhittaker