this week in security — september 3 edition
THIS WEEK, TL;DR
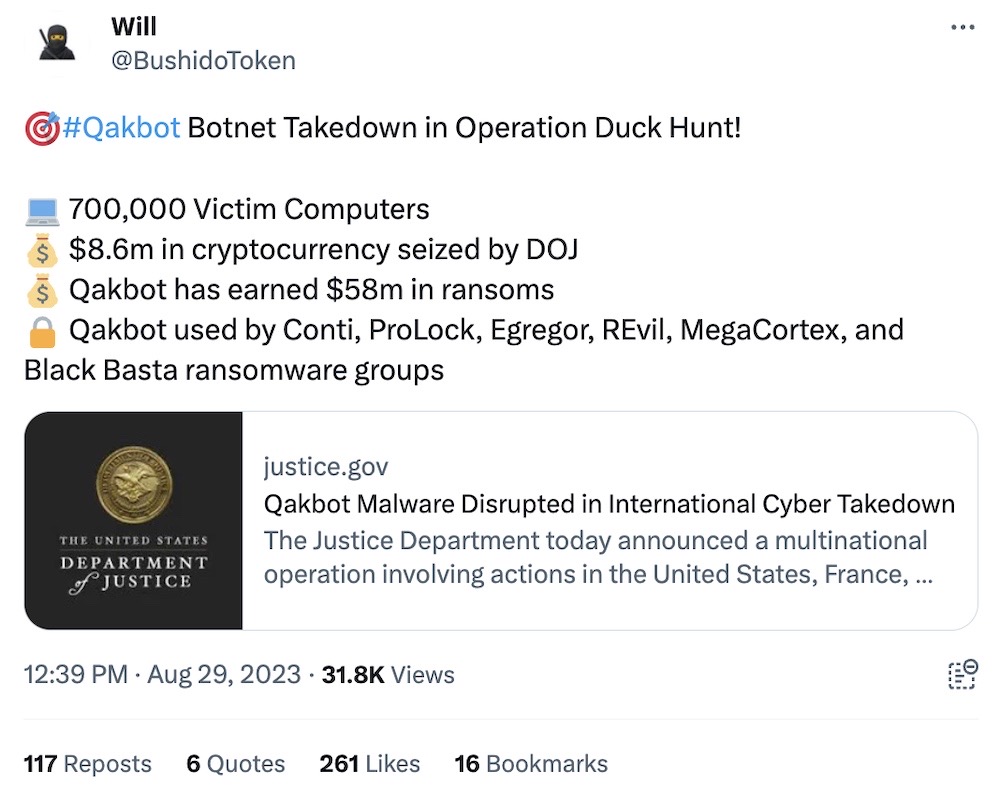
Qakbot malware disrupted in international cyber operation
U.S. Justice Department: And that was that for the Qakbot botnet after an FBI operation this week disrupted and largely neutralized the long-running malware. U.S. feds, prosecutors, and international partners launched an operation to trick core botnet machines into downloading an uninstaller from an FBI-controlled server, which rid the malware from infected machines and locked the Qakbot administrators out of their own infrastructure. Qakbot had at least 700k machines infected with some 200k in the U.S. alone, but that the true figure was likely in the millions. FBI said its Qakbot-controlling servers will be a "dead end" and used solely for the purpose of dismantling the botnet. (If you're interested in how the operation went down, I have an explainer.) Some 6.43 million impacted emails were siphoned out and given to Have I Been Pwned so you can check if you are affected. In case you were wondering, the operation was called Operation Duck Hunt. Try not to laugh.
More: CISA | Krebs on Security | Troy Hunt | TechCrunch | @andrewbrandt
Unmasking Trickbot, one of the world's top cybercrime gangs
Wired ($): From one malware network to another: this time it's Trickbot. Trickbot is, much like Qakbot, a malware delivery system that allows other threat groups to steal data or deploy ransomware. But data leaked by an apparent insider allowed Wired to link Bentley, a senior Trickbot boss, to a Russian national called Maksim Sergeevich Galochkin. Brilliant reporting here. Nisos, the cybersecurity company asked by Wired to investigate the leaks, wrote a blog post linking Trickbot to Russian intelligence.
More: @lhn | @campuscodi
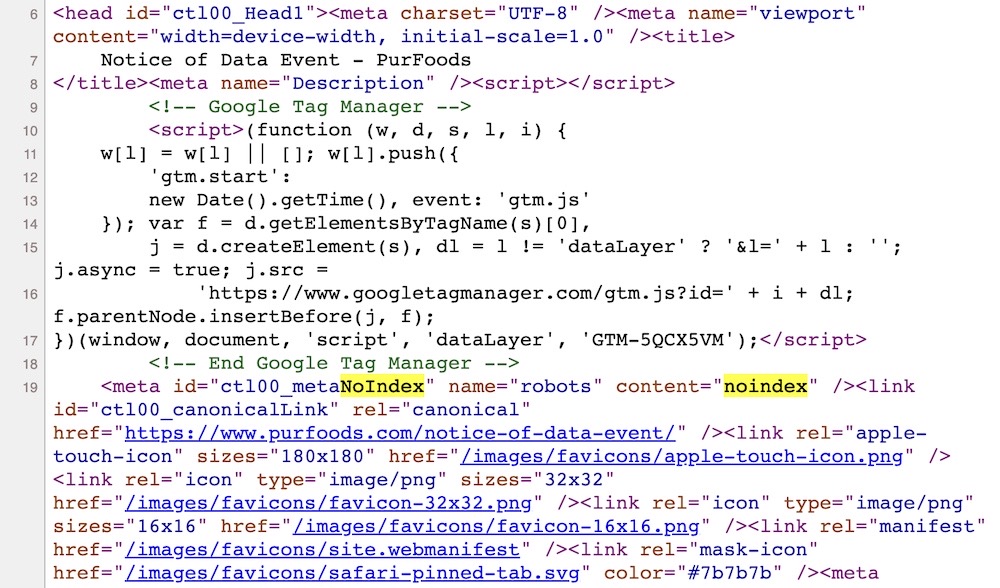
Mom's Meals discloses (but tries to hide) huge data breach
TechCrunch: PurFoods, the parent company of Mom's Meals, a maker of meals for folks with chronic health conditions, had a huge data breach affecting 1.2 million people. The company said affected data includes protected health information and Social Security numbers, according to a data breach notice filed in Maine, which described a situation that sounds like ransomware. The news comes months after an employee raised concerns about a massive outage reported in March, which led to staff being told to "take paid time off or not be fully paid for some days." If that wasn't gross enough, the company added a "noindex" flag to its data breach notice, ensuring that almost nobody can find the page in search engine results unless they have the direct web address.
More: KCCI | Maine Attorney General
BadBazaar malware targets Android users via fake messaging apps in Google Play
ESET: Security firm ESET found evidence of the BadBazaar malware in two trojanized messaging apps designed to spoof Signal and Telegram. The major issue here is that the apps were found listed in Google Play. It's really not a good look for Google when you have two of the most ubiquitous messaging apps spoofed in Android's official app store. BadBazaar has been used to target Uyghurs and other Turkic ethnic minorities. Google removed the apps, but Samsung — which was notified about malicious apps in its app store — hasn't taken any action.
More: Forbes ($) | Bleeping Computer
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Hacker gains admin control of Sourcegraph and gives away free access
Ars Technica: Sourcegraph said in a blog post this week that a hacker may have accessed customer information after an employee accidentally published an authentication key to a public Sourcegraph instance. The hacker abused the key to provide free accounts to other users.
The cheap radio 'hack' that disrupted Poland's railways
Wired ($): Last week, I noted that Poland's railway was briefly disrupted by what appeared to be pro-Russian hackers. Wired ($) looked further and found that the sabotage of more than 20 trains was carried out by broadcasting a "radio stop" command on a certain frequency using $30 worth of equipment.
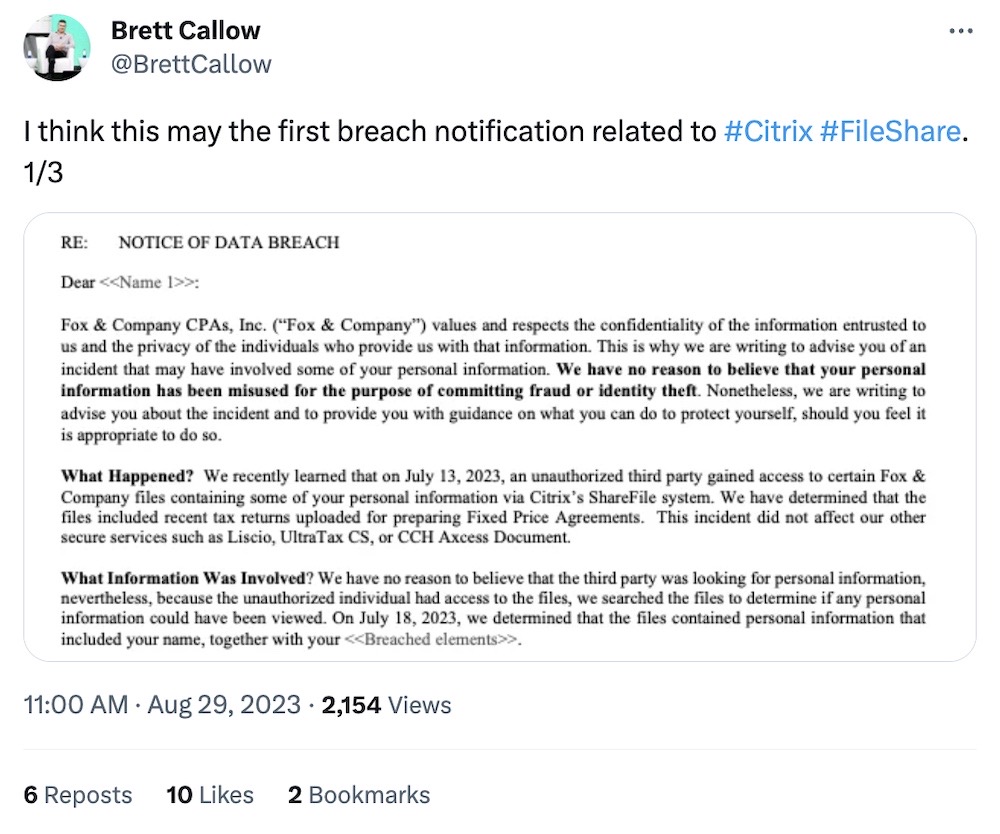
Breach notices involving Citrix ShareFile exploitation rolling in
Brett Callow: An accounting firm in Kentucky may be the first organization affected by a recently discovered zero-day in Citrix ShareFile, a file-transfer tool used by companies to share big sets of data over the internet. According to ransomware expert @BrettCallow, this may be the first notice seen so far linking a data breach to the ShareFile vulnerability. There are fears that the bug (CVE-2023-24489) could be the next in a recent list of corporate file transfer tools hacked by a ransomware and extortion group.
Chinese hackers accused of using Barracuda bug against U.S. agencies
The Record: Chinese hackers are exploiting a somewhat-patched vulnerability in Barracuda tech, according to Mandiant, which says the hackers have been abusing the bugs for the past eight months against a wide range of victims. Barracuda released a not-quite-fix that resulted in the company having to tell customers to physically replace affected devices.
Microsoft won't fix bug that exposes Skype users' IP addresses
404 Media ($): Back in 2016, Microsoft released an update for Skype that would hide user IP addresses by default, citing an uptick in incidents targeting users. The fix took Microsoft four years from when it said it was first looking into the issue. Fast-forward to 2023, and Skype is still exposing customer IP addresses. An independent researcher discovered the latest flaw and showed it was possible to access @josephfcox's IP address in real-time.
~ ~
OTHER NEWSY NUGGETS
Apple killed its CSAM detection tech, fearing the worst: Last year, Apple killed an effort to include an on-device CSAM detection technology from its iOS and macOS devices that was designed to curb the spread of child abuse imagery. The feedback was largely negative over fears that the technology could be misused to scan for other content. Now we know why Apple killed the project. In a letter to one child safety group, Apple said that after consulting with human rights experts and security and privacy technologists, Apple "concluded it was not practically possible to implement without ultimately imperiling the security and privacy of our users." Now, if Apple — with near infinite money and resources — can't figure out how to build a CSAM-scanning solution, or any "secure backdoor," then for the love of all that is holy take the hint that it cannot — repeat, cannot — be done. Hopefully this nugget of clarity isn't too late for the U.K., which continues to push an anti-encryption bill. (via Wired ($), DocumentCloud)
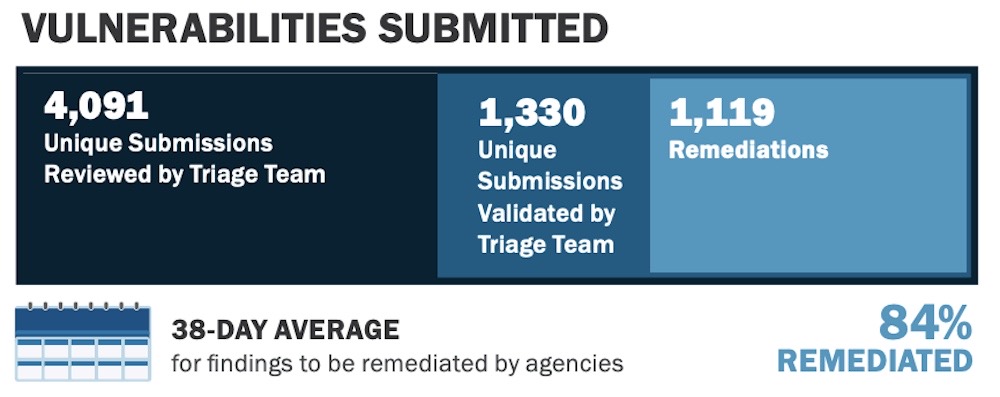
CISA VDP A-OK : U.S. cybersecurity agency CISA said its shared vulnerability disclosure policy (VDP), which launched in July 2021, has helped catch more than 1,300 "validated" bug submissions through December 2022. Of the 40 agency programs, 84% of reported bugs were fixed with an average timeline of 38 days. That's not bad! That's better than some Fortune 100 companies. (via Federal News Network ($), CISA [PDF])
LogicMonitor customers hacked with default passwords: Customers of the network security company LogicMonitor have been hacked. A LogicMonitor spokesperson confirmed the "security incident," which is due to how LogicMonitor was issuing customers with weak and easily guessable default passwords. At least one LogicMonitor customer was hit by ransomware following an intrusion. (via TechCrunch, Bleeping Computer)
~ ~
THE HAPPY CORNER
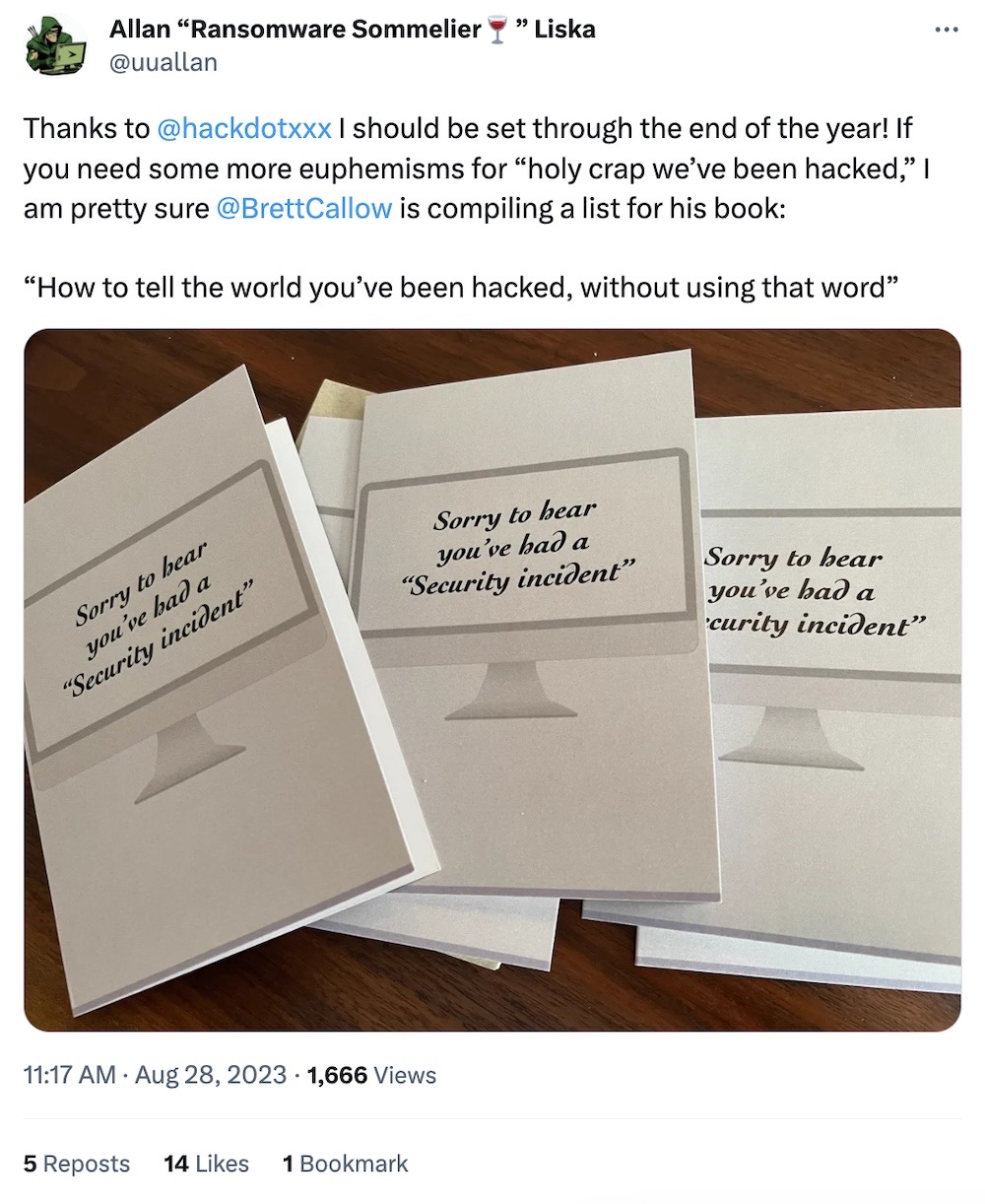
Welcome to the happy corner. Starting off strong with these incredible sympathy cards. "Sorry to hear you've had a 'security incident'." Exquisite, no notes
One of my favorite web tools, Backlight, has new features, including the ability to scan desktop sites for web trackers.
This week's bonus cybercats.
And finally, some early internet nostalgia for anyone over the age of 30.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Ollie, who as you can see is taking notes for his human doing a security review. Document all the things! Many thanks to Michael & Pamela for sending in!

Please send in your cyber cats! The more the merrier. Send me an email with your cyber cat (or non-feline friend!) with a photo and their name, and they will be featured in an upcoming newsletter. Repeat submissions are welcome!
~ ~
SUGGESTION BOX
An unexpectedly busy week, thanks for tuning in! If you have any feedback, thoughts or comments, as always please drop me an email. And do send in your cyber cats, we're running low!
Take care, be well and happy,
—@zackwhittaker