this week in security — september 5 edition
THIS WEEK, TL;DR
Apple cares about privacy, unless you work at Apple
The Verge: Apple seems to care about its customers' privacy (at least ostensibly, just don't mistake it for altruism), but there is no expectation of privacy when it comes to its own employees. Sure, you know a lot of companies monitor their employee communications, but Apple is actively pushing its employees to link their personal Apple accounts with their work Apple accounts. In fact, it's encouraged in large part to test internal features. But in doing so that exposes personal information of employees to Apple. But don't think you can just wipe your devices at the end of your employment... Excellent reporting by @ZoeSchiffer.
More: CNBC | @ZoeSchiffer tweets
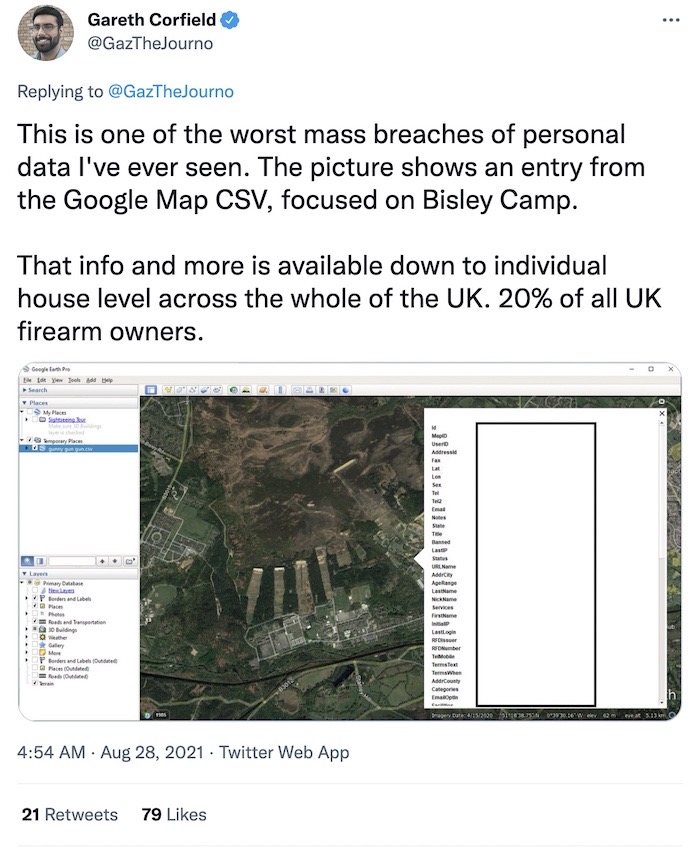
Leaked Guntrader firearms data file shared in 'worst case scenario'
The Register: A few weeks ago The Register reported on a U.K.-based gun trading forum that was hacked. Some 110,000 entries were stolen, amounting to some five years of data. (Don't forget, the U.K. is a country where guns are not readily available and require licenses and permits.) Now that data has spilled online. The Register says the data — which included gun owners' names and addresses — has been published in a CSV file that can be imported into Google Earth. Yes, now you can see where thousands of U.K. gun owners are registered. No doubt this is the worst case scenario for victims of this breach. "Guntrader has not explained why it was collecting location coordinates down to six decimal places." Yeah, start with that.
Background: The Register | More: BBC News | @GazTheJourno tweets
FTC proposes first stalkerware ban, compels SpyFone to notify victims
Cyberscoop: In a first-of-its-kind order, the FTC unanimously voted to ban spyware maker SpyFone and its CEO from the surveillance industry. Practically that means SpyFone, a known "stalkerware" (which is often used by spouses to spy on their partners under the guise of using it for parental control) cannot offer, sell or advertise any spyware again. The ban, which goes into effect after 30 days, comes after the spyware maker exposed thousands of victims' data due to an exposed Amazon S3 bucket two years ago (and it's not the first spyware maker to have done this). SpyFone is also obligated to inform victims that their phone data was hacked and stolen — suggesting this may be another line of relief for victims in the future. But even the FTC's own Rohit Chopra said the FTC's power alone isn't enough and criminal sanctions are needed.
More: FTC | Reuters ($) | TechCrunch
US Cyber Command says mass exploitation of Atlassian Confluence vulnerability 'ongoing'
ZDNet: In the run-up to the long weekend in the U.S. (which is why this week's newsletter is so short — sorry!), the White House was gearing up for another high-profile ransomware attack, since ransomware groups love holiday weekends like the rest of us — just for different reasons. This holiday weekend seems to be Atlassian's turn, after U.S. Cyber Command warned of mass exploitation of CVE-2021-26084 — a bug that can allow unauthenticated users the ability to execute arbitrary code on a Confluence server. Cloud customers are not affected by the vulnerability. But whether or not ransomware is ultimately the end goal in this case, Cybercom said "this cannot wait until after the weekend." Go patch!
More: Atlassian | @bad_packets
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Lawyers, bugs and money: When bug bounties went boom
Decipher: Here's a historical look back at the conception and rise of bug bounty programs, which really kicked off in the early-00's when Mozilla unveiled its first security bug bounty program. This piece is one of three that digs into the important history of bug bounties.
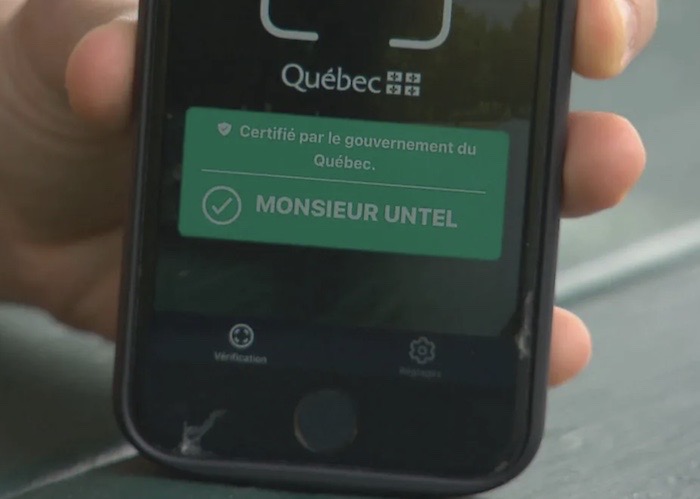
Flaws in Quebec's vaccine passport lead to police investigation of bug finder
CBC: Within six hours, a security researcher was able to create a fake vaccine passport for a person — Monsieur Untel ("Mr. So-and-So") who doesn't exist. Others have also obtained the QR codes of senior politicians, including the digital transformation minister overseeing Quebec's vaccine passport security. Clearly things aren't going well for Quebec's digital vaccine passport. The politicians defended the system — though they weren't committed to a fix — but were pretty keen on asking the police to investigate "if criminal charges have to be laid." Ah, this again. The "we can't take responsibility for our own mistakes so we're going to blame it on the people who embarrassed us instead" approach. Don't forget this when you're next at the ballot box.
A replay bug affects Honda and Acura keyfobs
GitHub: A radio replay bug in wireless keys of Honda and Acura cars can be easily replayed to lock and unlock a car, control its windows and start its engine. That's because the keyfob doesn't encrypt (or rotate) the radio signal, allowing anyone to essentially capture it and replay it as if it was the real owner.
FBI warns Beijing is targeting U.S.-based Uyghurs
IPVM: An unclassified bulletin issued by the FBI this week warns U.S.-based Uyghurs are being targeted by Chinese authorities through both "in person and digital" attacks. This is part of China's ongoing efforts to "silence dissent, issue instructions, collect information, and compel compliance," even outside of its own borders, according to the FBI. It's not the first time that Uyghurs — of which at least a million have been detained in camps by Chinese authorities — have been targeted by digital attacks.
~ ~
OTHER NEWSY NUGGETS
WhatsApp issued second-largest GDPR fine of €225m
BBC News: WhatsApp has been fined about $267 million, which is about 0.9% of Facebook's global income for 2020, for violating Europe's GDPR, the second largest fine issued by the bloc under its privacy rules. Ireland's regulator, which issued the fine because it oversees Facebook's EU operations based in Ireland, said WhatsApp had not supplied enough information as to how users' data is processed.
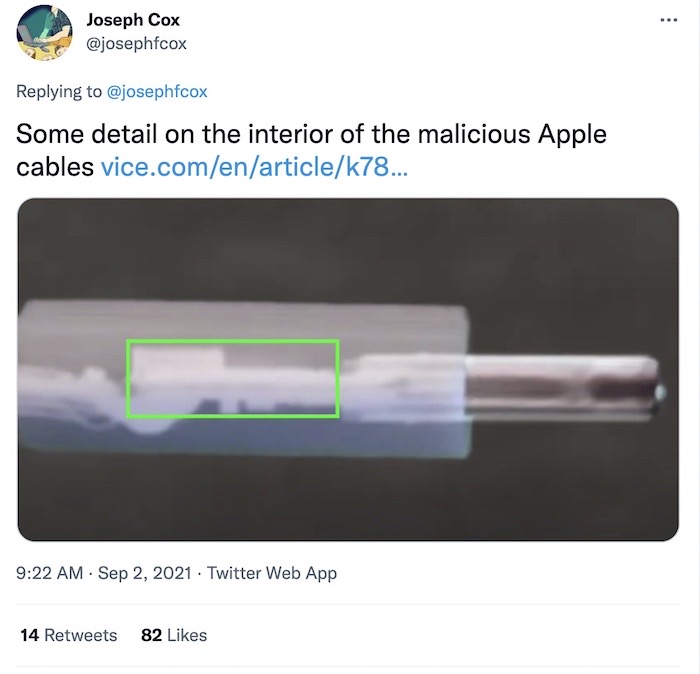
This seemingly normal Lightning cable will leak everything you type
Motherboard: It looks and works like a Lightning cable, but this isn't a Lightning cable — it's an OMG Cable, which contains an implant that creates a Wi-Fi hotspot that allows a hacker to intercept everything that a person types. The cable was created by @_MG_, who builds these keyloggers such as for red team engagements. Here's a video of one of the newer OMG cables working in action. A good tweet thread from @josephfcox, who tested the cable.
Apple delays plans to roll out CSAM detection in iOS 15 after privacy backlash
TechCrunch: Apple has delayed — not cancelled — its client-side child sexual abuse materials (CSAM) detection technology, which was slated to be baked into iOS 15. But the "screeching voices of the minority" said that the system could be abused by authoritarian governments (which already exploit known vulnerabilities in iOS 14, which Apple refuses to patch, leaving thousands of human rights defenders vulnerable to both digital and real-world attacks). Apple faced a ton of criticism for the technology, but decided to wait until Friday before a holiday weekend to say it was pulling the plug — for now. Companies only do that when they have something they really don't want to announce. (Disclosure: I wrote this story.)
Autodesk confirms it was hit as part of the SolarWinds espionage campaign
Cyberscoop: It's been about a year since Russia's SolarWinds hacking and espionage campaign began and victims are still coming forward. In a government filing this week, software house Autodesk said it was also a victim of the SolarWinds hack. "While we believe that no customer operations or Autodesk products were disrupted as a result of this attack, other, similar attacks could have a significant negative impact on our systems and operations," Autodesk said.
~ ~
THE HAPPY CORNER
Little in the way of happy news this week. It is a quiet, shorter week than usual...
For anyone going away any time soon, @malwaretech has a short TikTok video on how to detect hidden cameras in your hotel room. Some of this might be known but this walks you through exactly where to look and what to look for. Now I'm just replaying in my head every hotel room I've ever been in...

If you want to nominate some good news from the week, feel free to reach out.
~ ~
CYBER CATS & FRIENDS
Meet Rory, who is this week's cyber cat. His human tells me that Rory loves watching paper emerge from a printer and comes running when he hears a print job. Cats and paper is a messy combination! Many thanks to Eric for the submission!

Keep sending in your cyber cats (or their friends)! Email with their name and photo here!
~ ~
SUGGESTION BOX
That's all for this week's shorter-than-usual Labor Day special. As always, feel free to drop any feedback in the suggestion box or reach out directly at this@weekinsecurity.com. Have a great week and see you next Sunday.