this week in security — september 8 2024 edition
THIS WEEK, TL;DR
Five Russian GRU officers charged with targeting the Ukrainian government with destructive malware
Justice Department: Let's start this week in Maryland, of all places, where U.S. prosecutors returned charges against five Russian intelligence officers (*cough* hackers *cough*) working for the GRU, who are accused of launching destructive "wiper" malware against the Ukrainian government in the run-up to Russia's full-scale invasion in 2022. It follows an earlier indictment that included the involvement of a civilian in the scheme. The so-called "WhisperGate" malware attack looked like ransomware hitting the Ukrainian government's systems, but was deliberately unrecoverable. The attack launched around the same time as the Viasat hack, also designed to target Ukraine. The DOJ lifted the lid more on the GRU's hacking unit, aka Unit 29155, which Wired ($) digs deeper into the notorious special forces unit that is "now doing cyber things from behind a keyboard." Great...
More: U.K. NCSC | Reuters ($) | NYT ($) | Nextgov | Security Conversations
Spyware vendors thwart restrictions with new names and locations
Washington Post ($): The effort to curb the proliferation of commercial (think government-used) spyware appears to be failing, as spyware makers sanctioned by Western governments manage to skirt many of those restrictions on selling their surveillance products. That includes Predator (developed by Intellexa) and Pegasus (developed by NSO), both firms that have been effectively told they can't have dealings with the United States. The emergence of spyware exploits making their way into Russian government hacking campaigns also raised questions about, well, how that was possible, all the while Predator's infrastructure appears to be returning despite recent sanctions levied against its spyware maker, Intellexa. Clearly more has to be done, but the U.S. is limited and Europe hasn't done nearly enough on its side (per European Parliamentarian @sophieintveld).
More: Recorded Future | DFRLab | The Record | DarkReading | @josephmenn
Ransomware Roundup: Seattle Public Library, Microchip, and Halliburton
Geekwire: Let's start this roundup with the Seattle Public Library, whose 27 branches across the city have returned following a ransomware attack that has knocked the library offline since May. A public assessment of the cyberattack is forthcoming. Meanwhile... It looks like U.S.-based chip supplier Microchip is back on its proverbial feet after crims stole employee data during a ransomware attack disclosed in August, per SecurityWeek. And lastly... oil and fracking giant Halliburton remains mum on its "ongoing" cyberattack, but that Bleeping Computer has linked to RansomHub, the same hackers behind the Change Healthcare breach. Halliburton says some data was stolen, but details remain scarce. Remember, folks: Ransomware is an ecosystem, not a collection of threat groups, per threat intel wizard @sherrod_im.
More: TechCrunch | KIRO 7 Seattle
~ ~
THE STUFF YOU MIGHT'VE MISSED
The U.S. isn’t ready for cyber chaos in the food and agriculture sector
The Record: The Dept. of Agriculture is meant to help prevent farmland disasters and meatpacking plant failures, but the department is "woefully unprepared" to play that role, per policymakers and other experts, and that leaves the agriculture and food sector — some 10% of U.S. jobs! — at risk of cyber threats. A ransomware attack in 2021 on JBS, a major meat producer, was a taste (inadvertent pun) of things to come.
London transit network avoids delays despite cyberattack
BBC News: The U.K. capital's transport network, including buses, trams and — of course, the world famous London Tube, is running largely alright despite a cyberattack targeting the local government organization's corporate offices. The "ongoing" incident has resulted in online outages for the most part, but The Guardian ($) reports that the incident is "not believed to be a ransomware attack, and no ransom demand had been made." Well, that sounds promising, but sounds like we really need to get that claim attributed to a named spokesperson before we can trust it completely.
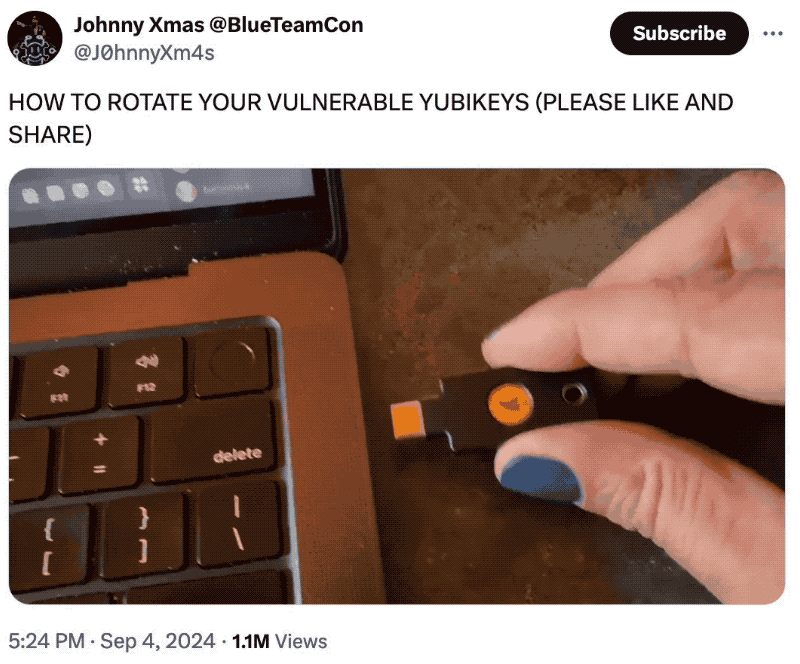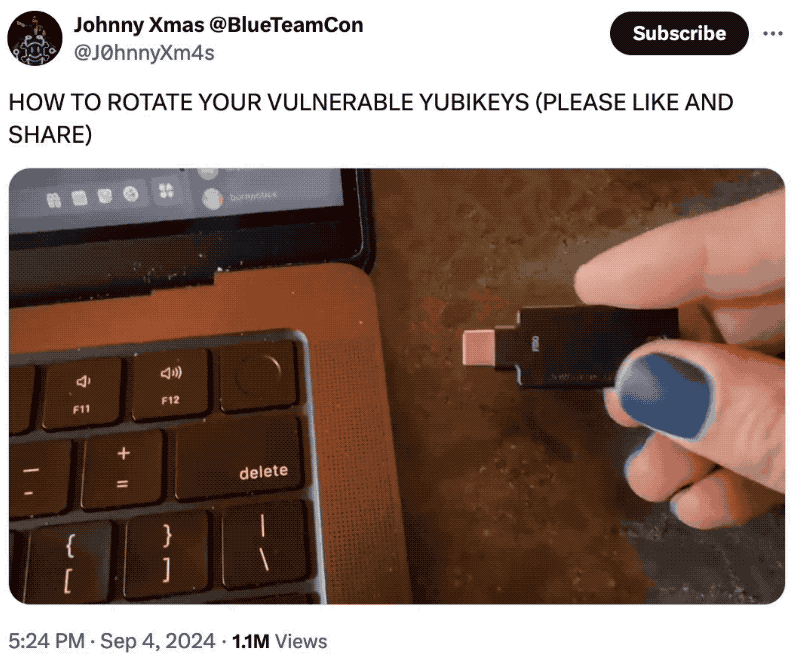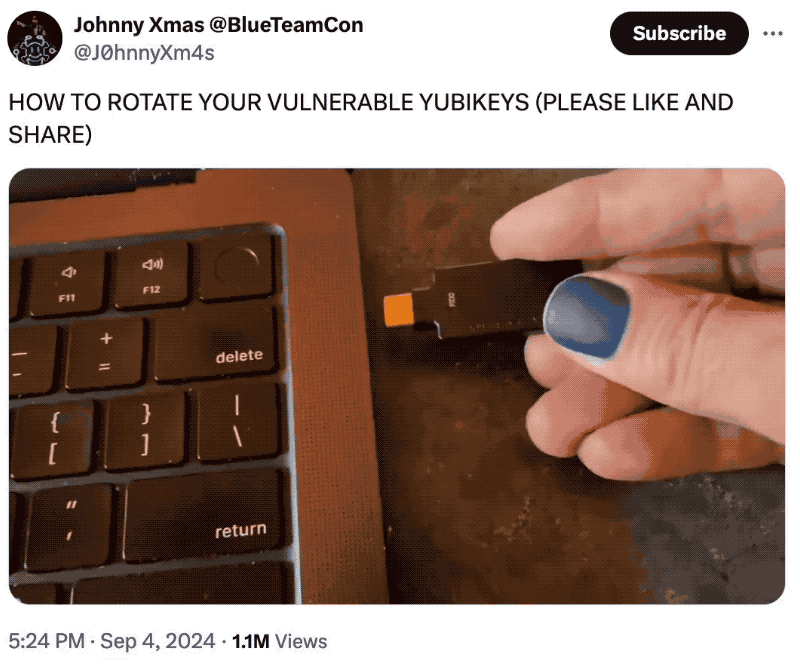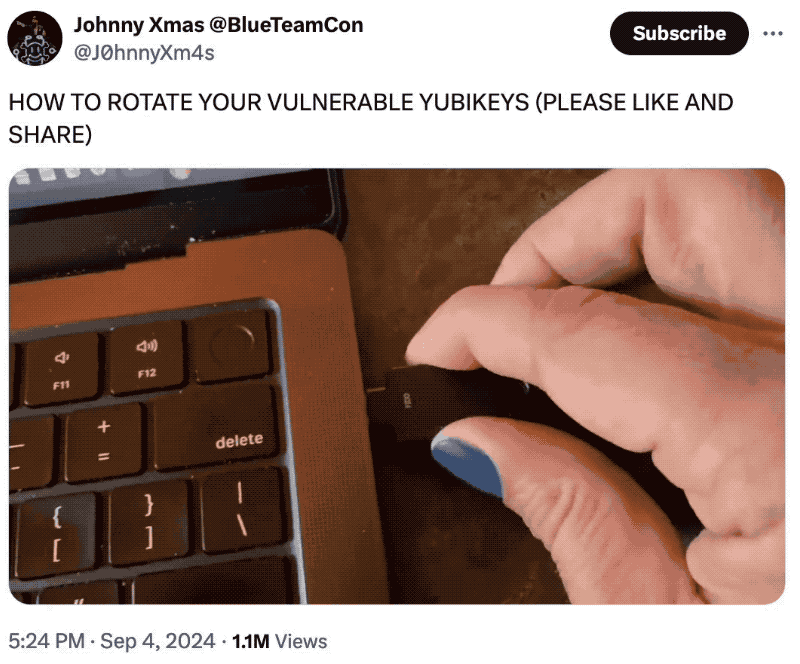
Side-channel hack affects older YubiKeys, but no need to panic
Ars Technica: A very sophisticated (read: complicated and laborious) side-channel attack targeting the popular physical security keys, YubiKeys, allows for an in-person attacker to clone a YubiKey and extract the secret key from within. Clearly not great, but practically speaking, it's near-impossible to carry out an attack like this secretly or covertly. Everyone's favorite former CISO @jerry has some grounding words of clarity, but, tl;dr: unless you're a nuclear scientist or an actual spy, you probably don't have much to worry about, and using a YubiKey is still far, far better than not. Still, for those considering rotating their YubiKeys, @J0hnnyXm4s shows you how (🚨 terrible joke incoming 🚨):
Gone in 60 seconds: The worst places to leave your secrets
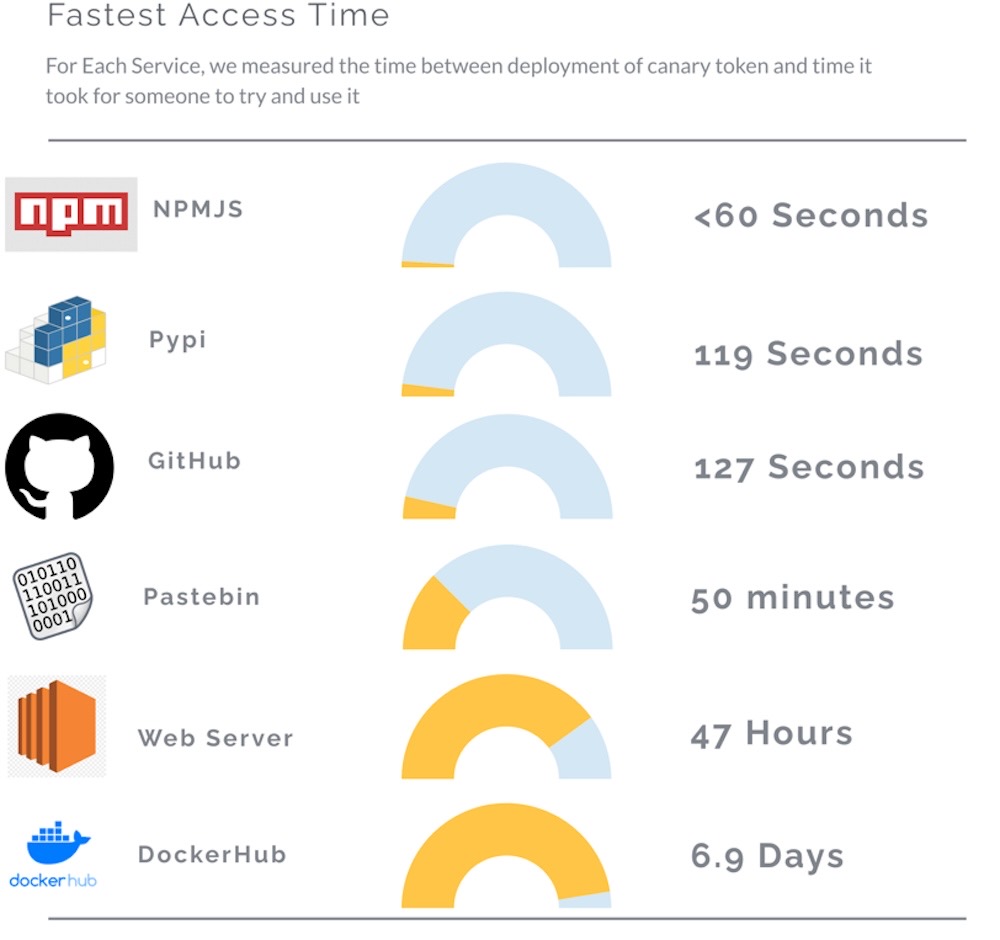
Cybenari: I missed this research the first time around, but it's brilliant and worth re-sharing. In short, if you accidentally expose your private keys (or any other secret), bad actors can detect and steal those keys in as little as 60 seconds, which means you really, really need to get on top of (actually!) rotating those secrets as soon as possible. Which is all to say, have a detection and remediation plan in place.
Over one-third of CISOs report flat or falling budgets
The Register: Do you hear that? That's the sound of corporate executives declaring "cyber is over," and that the world is secure at last, clearly, because why else would these million-dollar bonus-making fatcats allow flat or declining budgets for cybersecurity? Have they looked around recently? No, there isn't a talent shortage — with layoff after layoff, despite record corporate profits — it's greedy executives who hoard their wealth, and face practically no repercussions when their companies get hacked. They destroyed the world, but at least they created incredible value for shareholders (and at the expense of everyone else).
Would you trust AI to scan your genitals for STIs?
The 19th: I don't know who needs to hear this, but you really, really shouldn't upload photos of your genitals to the internet, let alone to an AI model.
~ ~
OTHER NEWSY NUGGETS
White House wants to secure BGP: The Biden administration said this week it wants federal agencies to boost their internet routing security on their networks in the face of rising threats targeting an underlying internet protocol, called Border Gateway Protocol, or BGP. In short, whenever there's a major internet outage not caused by either DNS or a squirrel nibbling through a fiber cable, it's almost always caused by BGP. The fact that the federal government is taking it on sets a good example to the rest of the industry. (via White House, Reuters ($))
Credit cards stolen from Cisco swag store: Network security giant Cisco, whose CEO Chuck Robbins (if you recall) made $31.8 million during 2023 and who recently made the decision to cut several thousand staff from its headcount following an earlier layoff in February, isn't having a very good security week. That's because Cisco's online store for selling swag and other corporate-branded tat (quite frankly) was hacked to include hidden JavaScript code that scraped credit card numbers of customers at the online checkout. I wonder how many of the "limited number" of users had their credit cards stolen as a result? Guess we'll have to wait to find out... (via Bleeping Computer)
Hunting hidden police signals at the DNC: A project by Wired's @dmehro (+ bonus tweet thread) used open-source software developed by the Electronic Frontier Foundation that can detect cell-site simulators (used by police to locate devices nearby) to detect hidden police signals while fellow reporters walked around at the high security, locked-down Democratic National Convention. Really great journalism here. (via Wired ($))
Kaspersky offloads customers to Pango: Following the U.S. government's decision to effectively ban Kaspersky from selling its products to U.S. customers citing the Moscow-headquartered company's links to the Russian government, Kaspersky has offloaded its customer base to the Pango Group. Kaspersky was given until September 29 to offload its one million or so customers before its antivirus updates stopped, putting its customers at risk. (via Axios)
Confidant Health exposed therapy sessions: Thousands of people had highly sensitive health information, including audio and video of therapy sessions, exposed to the internet because virtual medical provider Confidant Health left an unsecured database on the internet — no password required — containing, in part, transcripts and other medical note of its patients, according to a security researcher. Confidant CEO Jon Read chided the "sensational nature" of the findings. Perhaps if Confidant didn't have such a colossal and negligent security lapse to begin with, none of this would've happened. You've nobody to blame but yourself there, Jon. (via Wired ($))
~ ~
THE HAPPY CORNER
And breathe... (paper bags upon request). This is the happy corner.
First up, this toot speaks for itself.
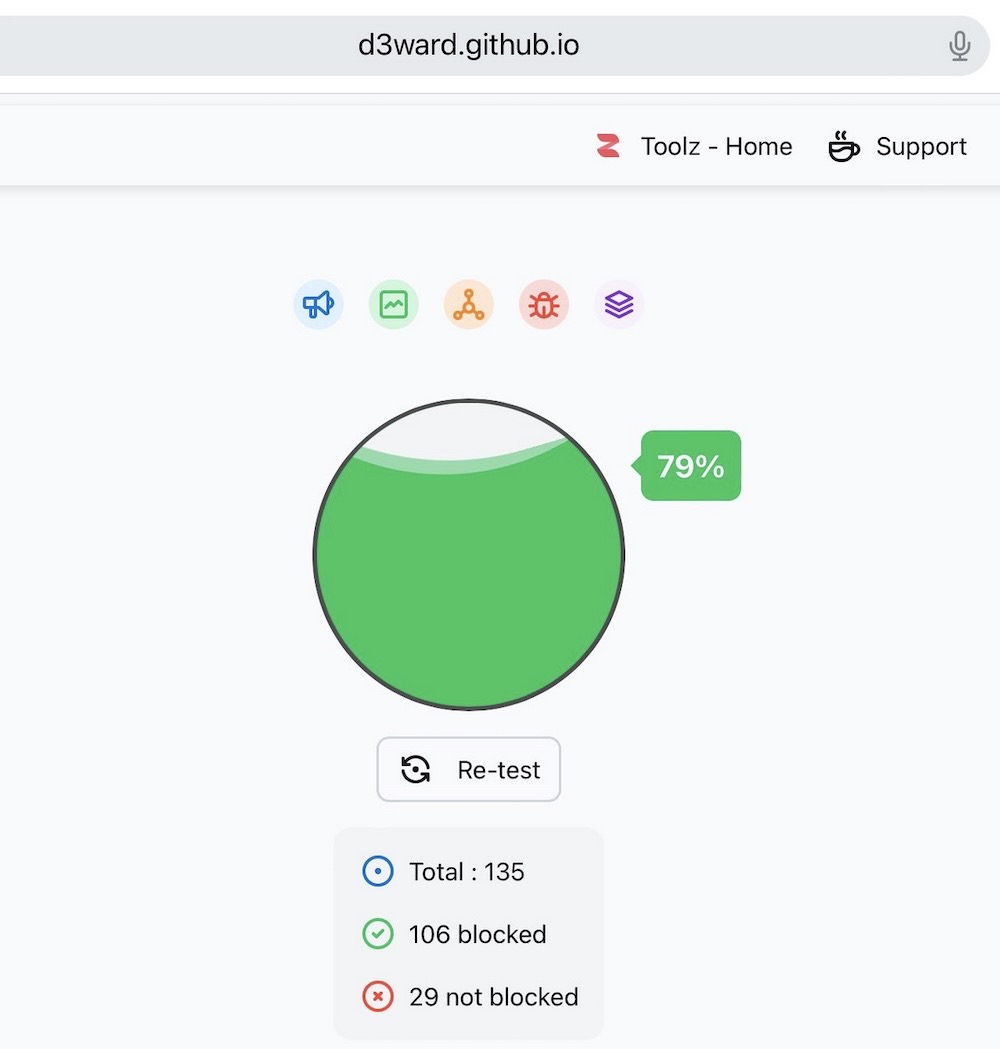
Per @troyhunt, there's a cool project on GitHub that allows you to determine the percentage of ads that your device is blocking (or allowing through). This project is a good way to stress-test your ad-blocker — and you should absolutely use one, because they're good for both privacy and security.
In other good news, the White House has launched a cybersecurity hiring sprint to try to fill some 500,000 job openings across the cybersecurity sector. (More from Cybersecurity Dive). A key thing here from National Cyber Director Harry Coker is that, "many Americans do not realize that a cyber career is available to them," and that there's a "perception" that you need a computer science degree and a deeply technical background to get a job in cyber. Nope! Per the top U.S. government cyber official: "The truth is, cyber jobs are available to anyone who wants to pursue them. Cyber professionals are part of a dynamic and diverse modern workforce and individuals from all backgrounds and disciplines have a place." Hell yeah, and diversity is absolutely key.
And finally, this week. A friendly reminder (via @Em0nM4stodon) that Inspirational Skeletor always has wise words to share. Speaking of...

And, a friendly reminder! If you are eligible to vote in the U.S. but haven't registered yet, take a few minutes to check at Vote.gov.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Fluffy, who is fluffy by name, cyber-secure by nature. That's because Fluffy multi-factors all the things, so Fluffy can spend their time thinking about literally anything else... mice, treats, threat hunting... Many thanks to Mikael F. for sending in!

Send in your cyber cats (or a non-feline friend!). Drop me a quick email any time with a photo with their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's it for this bumper newsletter this week! Thanks so much for taking the time to read. See something cool, send it in! You can drop me an email any time with research, news stories and other fun things you see from around the web. Enjoy your week and we'll catch up next.
All my best,
@zackwhittaker