this week in security — august 24 2025 edition
THIS WEEK, TL;DR
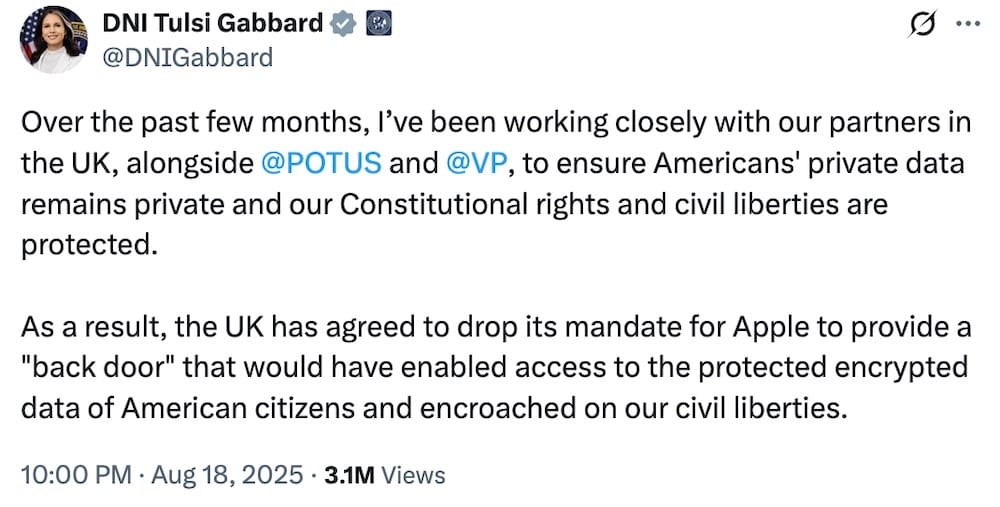
U.S. spy chief says U.K. drops demand for Apple backdoor access
Washington Post ($): The latest round of Crypto Wars came to a somewhat bureaucratic end this week when the U.S. spy chief Tulsi Gabbard tweeted that the U.K. had "agreed to drop" its secret legal order demanding an encryption backdoor to Apple's cloud. You'd be right to be cautious and somewhat skeptical of the announcement, given that the U.K. hasn't commented yet (only to say it doesn't comment on these matters), and neither has Apple, which remains technically subject to the U.K.'s secret backdoor demand until we hear otherwise. In short, the U.K. government sought secret access to any Apple-held customer data in its encrypted cloud, but that drew ire from the U.S., and the White House reportedly threatened ending its data-sharing agreement as a result. Yes, this a win for common sense, but these laws exist for the sole purposes of surveillance and they're unlikely to go away. Even though Google and Meta say they haven't been ordered to backdoor their systems for U.K. access, the risk remains in the future. In any case, it's unlikely that Apple's top cloud security feature, ADP, will ever return to the U.K.
More: Reuters ($) | BBC News | The Times ($) | @DNIGabbard
Man charged with running Rapper Bot, a DDoS service that targeted the Pentagon
KrebsOnSecurity: A 22-year-old man from Oregon has been arrested and charged with running a massive DDoS-as-a-service that was capable of knocking entire websites offline. Ethan Foltz allegedly ran the "Rapper Bot" botnet made up of some 65k-90k hacked internet-connected devices around the world, clocking traffic-flooding attacks in the range of 2 terabits per second, making it one of the largest known "booters" today. According to the criminal complaint, Foltz tried to stay off the feds' radar by ensuring the botnet never pointed at Brian Krebs' website, fearing an attention-grabbing attack would get the botnet caught. This strategy seemed to be largely working, with the botnet growing in size. In May 2025, KrebsOnSecurity was hit by an unrelated 6.3 terabit DDoS attack (the largest Google, which protects the site, had ever defended). It was this attack that caught the attention of Rapper Bot, saying "going against Krebs isn’t a good move" (fact check: accurate). Still, targeting the Pentagon also wasn't a good idea, and ultimately got the operator caught.
More: Justice Department | DefenseScoop | Cyberscoop | @briankrebs
First member of 'Scattered Spider' sentenced to 10 years
Bloomberg ($): After a few years of high-profile hacks and a blitz of data breaches, the first member of the notorious Scattered Spider hacking group has been jailed for his role in the gang's cyberattacks. Noah Urban, 20, got 10 years in prison for wire fraud and aggravated identity theft, for his role as a "caller," a skilled social engineering who calls up IT helpdesks or phone companies and tricks employees into handing over access to an employee or customer's accounts (though, these skills were allegedly not always necessary...). These attacks worked incredibly well at times, allowing the hackers to break into some of the biggest tech companies, like LastPass, DoorDash, Mailchimp, and others. The gang went quiet for a bit after Urban's arrest, but came back with a vengeance, attacking retail, insurance and transportation sectors. To note just how brazen these hackers are: One suspected group member "hacked a Florida-based magistrate judge to see whether a defendant had provided information about his co-conspirators" 👀... The hacker "accessed a copy of Urban's sealed indictment" before their access was shut down.
More: Justice Department | Daytona Beach News-Journal | KrebsOnSecurity | DataBreaches.net
Workday says personal data stolen from its Salesforce database
TechCrunch: Workday had a data breach of one of its Salesforce databases, exposing the contact (read: personal) information of an unspecified number of individuals. Workday, which is the world's largest HR tech giant with data of more than 11,000 corporate customers (and millions of their employees), said it had "no indication" of access to customer tenants or their data. Not the strongest statement in the world, as regular readers will know. A spokesperson wouldn't budge on disclosing the number of those affected or if the company has logs to detect any access to customer data. (Disclosure: I wrote this story!) Workday is the latest firm to have its Salesforce data swiped in recent months; Cisco, Qantas, and Google are also affected; Google attributed these hacks to ShinyHunters, which is said to be preparing a leak site. (Also, good grace points deducted from Workday for using "noindex" code on your site — don't hide your data breach notices from search!)
More: Workday | Bleeping Computer | Cybersecurity Dive | Archive: CISA
THE STUFF YOU MIGHT'VE MISSED
Age verification is breaking the internet
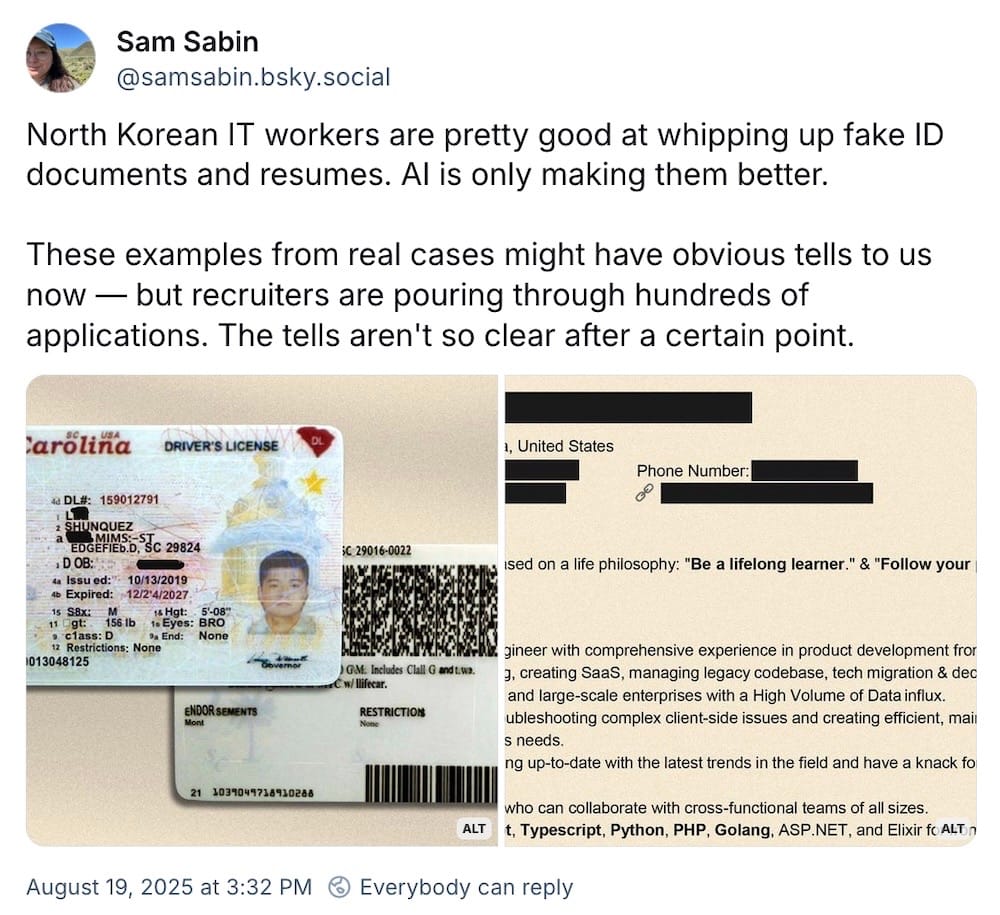
Mashable: Solid reporting from Mashable looking at age verification, an emerging but ongoing threat to the open internet. Just this week, Bluesky pulled its service from users in Mississippi after an age-checking law took effect. By siloing users or regions that require age checks before users can get access to websites is creating a fragmented, broken internet that's also fueling the massive surveillance of collecting people's identity documents (related: Wired ($)'s story from late July is also a great read.). Protect the children, sure, but not at the expense of everyone losing their privacy. This isn't a zero-sum game; governments, do better! At a time when North Koreans are spitting out fake IDs a dime a dozen to gain fraudulent employment, the very process of checking IDs doesn't even work.
Lumma password-stealing malware bounced back after FBI takedown
Recorded Future: New research shows the world's largest password-stealing malware, Lumma, has bounced back following a law enforcement takedown operation earlier this year. The malware, which is often found buried in normal-looking but malicious apps, continues to pose a "significant threat, actively exfiltrating data from individuals, organizations, and governments." More from @julianferdinand in a Bluesky thread.
New zero-day startup offers $20 million for tools that can hack any phone
TechCrunch: A startup called Advanced Security Solutions (yes, that acronym) is offering a $20 million bounty for anyone who can hack any phone with a text message. Shady companies like this exist effectively as brokers of zero-day bugs to anyone who will pay full price — typically governments — but realistically anyone with enough money can buy phone-busting exploits despite little regulation. A source familiar with the zero-day market told TechCrunch that the $20M price-tag was about right, if not on the lighter side, depending on "how unscrupulous you are."
Proton says it's moving out of Switzerland amid surveillance law
Proton: The maker of privacy focused apps, Proton, says it's moving its physical infrastructure out of Switzerland as the country's lawmakers are planning to pass a surveillance law, which would effectively undermine the company's privacy promises. Alas, many folks are increasingly realizing that ostensibly private borders like Switzerland actually never really were, and can (and do) change over time. The best way to secure data from prying eyes is by not having access to it, or simply not collecting it to begin with.
Telco giant Colt cyberattack likely stems from SharePoint flaw
Double Pulsar ($): It looks like the cyberattack on U.K. telco giant Colt was ransomware, as taken credit by the Warlock gang. Trend Micro has a good blog on Warlock, which targets unpatched SharePoint servers to gain access to a victim's network. Per @GossiTheDog, aka Kevin Beaumont, Colt had an on-premise SharePoint server that had already been backdoored (via CVE-2025-53770) in the recent mass-hack wave by the time it was patched. AAs usual, this was a really good blog by Beaumont, providing a run down on how the Colt attack went down, but with sage advice and learnings peppered in. Also, again on the noindex nonsense...
Home Depot sued for allegedly secretly using facial recognition
PetaPixel: Looks like Home Depot is in hot water (yes, that's a home improvement pun) for allegedly using facial recognition at its checkout cameras. One shopper saw himself with a green box around his face appear on a checkout screen, and later launched a class action suit [PDF]. Look, I'm no genius but, please, do judge for yourself. Good luck (/sarcasm) to the Home Depot lawyers on this one.

Microsoft curbs early access for Chinese firms to cyber flaws
Bloomberg ($): Microsoft won't provide companies in China (or any other country where companies have to report flaws to their governments) with access to advance notifications about bugs in its technologies through its program called MAPP. Previously, the aim was to provide details of flaws so security vendors can roll out fixes faster, but after the recent SharePoint-related mass-hacks, there were fears (though no evidence yet) that MAPP could've given the hackers a heads-up.
FBI warns Russian gov't hackers are exploiting bug in end-of-life Cisco routers
FBI IC3: Hackers linked to the Russian government are exploiting a 7-year-old unpatched flaw in end-of-life Cisco routers, aka CVE-2018-0171. Cisco updated its advisory following an FBI alert this week to warn about the flaw being used to target critical infrastructure.
OTHER NEWSY NUGGETS
Oracle chief security officer suddenly departs: The surprise departure of Oracle's long-time security chief Mary Ann Davidson, who joined the company in 1988, took plenty by surprise. The departure — the specific reason as yet unknown — comes after Oracle announced job cuts as it ramps up on AI. Davidson's departure also comes after a massive data breach of its Oracle Health (Cerner) division, as fresh breach notifications continue to roll in. (via Bloomberg ($), CSO Online)
The week where weed deets leaked: Not a great week for weed users in Ohio and the U.K., where two unrelated companies apparently exposed their customers' private information. Per Website Planet, which first reported the incident, the Ohio case saw close to a million customer records — including Social Security numbers, government IDs, and health conditions, exposed to the internet. (via Cannabis Health, Wired ($))

Orange Belgium breach hit 850,000 customers: At the end of July, Orange Belgium was hit by a hack that compromised the personal data, phone number, SIM card number and corresponding PUK codes of 850,000 customers, per the phone giant's latest statement. The breach is separate from a hack affecting Orange Group customers in France, which resulted in gigabytes of data stolen in a ransomware attack attributed to Warlock, per Bloomberg ($). (via Orange Belgium)
German top court overturns ad-blocker ruling: For more than a decade, a legal case brought by German publishing giant Axel Springer involving Eyeo, the maker of Adblock Plus, has been winding its way through the German legal system. While Eyeo has largely prevailed and the legality of ad-blockers remains untouched, Germany's top federal court has now partially overturned an earlier decision and remanded the case for further proceedings. Mozilla has a good post on this messy situation. The implications of this ruling aren't clear, and may not be for some time, but consider this a matter placed very much on your radar. (via @jsrailton)
Zscaler CEO says company using customer logs to train AI: The CEO of enterprise security giant Zscaler said this week that the company is using half-a-trillion daily "complete logs" to train its AI models. (This was first covered by The Stack last year with more details.) As SDX Central noted: "In practice, this means a substantial volume of data – traffic that enterprises typically regard as encrypted and protected – is being intercepted, processed, and effectively ingested into Zscaler’s systems." (via Steven Swift (LinkedIn), @vxunderground)
New Apple zero-day drops: Update your iPhones, iPads and Macs for the second time this week, a new zero-day just dropped. The bug can be triggered by way of a malicious image file, so that's... broad. Apple says it has a report that the bug may've been exploited in an "extremely sophisticated attack against specific targeted individuals" (its standard language these days). Don't delay! (via @zackwhittaker, @ryanaraine)
U.K. criminal background checker breached: Keep an eye on this major breach: A leading U.K. provider of criminal records checks for employers, Access Personal Checking Services (APCS), which runs background checks for 19,000 organizations, has confirmed a data breach. The hack initially stems from a software development company called Intradev. (via The Register)
THE HAPPY CORNER
What's that sound? It's peaceful, quiet and calm in the happy corner.
When the world is spinning out of control and everything seems to be breaking, remember that this is the true way:
Browsers are a personal choice, and not all are created equally. (I stopped using Chrome as Google began phasing out support for popular ad-blockers.) Firefox seems better, but even then it's getting bogged down by AI junk. Thanks to @gaytabase, there are a few settings that you can change to switch it off.
And lastly, this week, a bonus cybercat, because why not? (As someone who has two cats who regularly "help" edit this newsletter, I certainly empathise with this.)
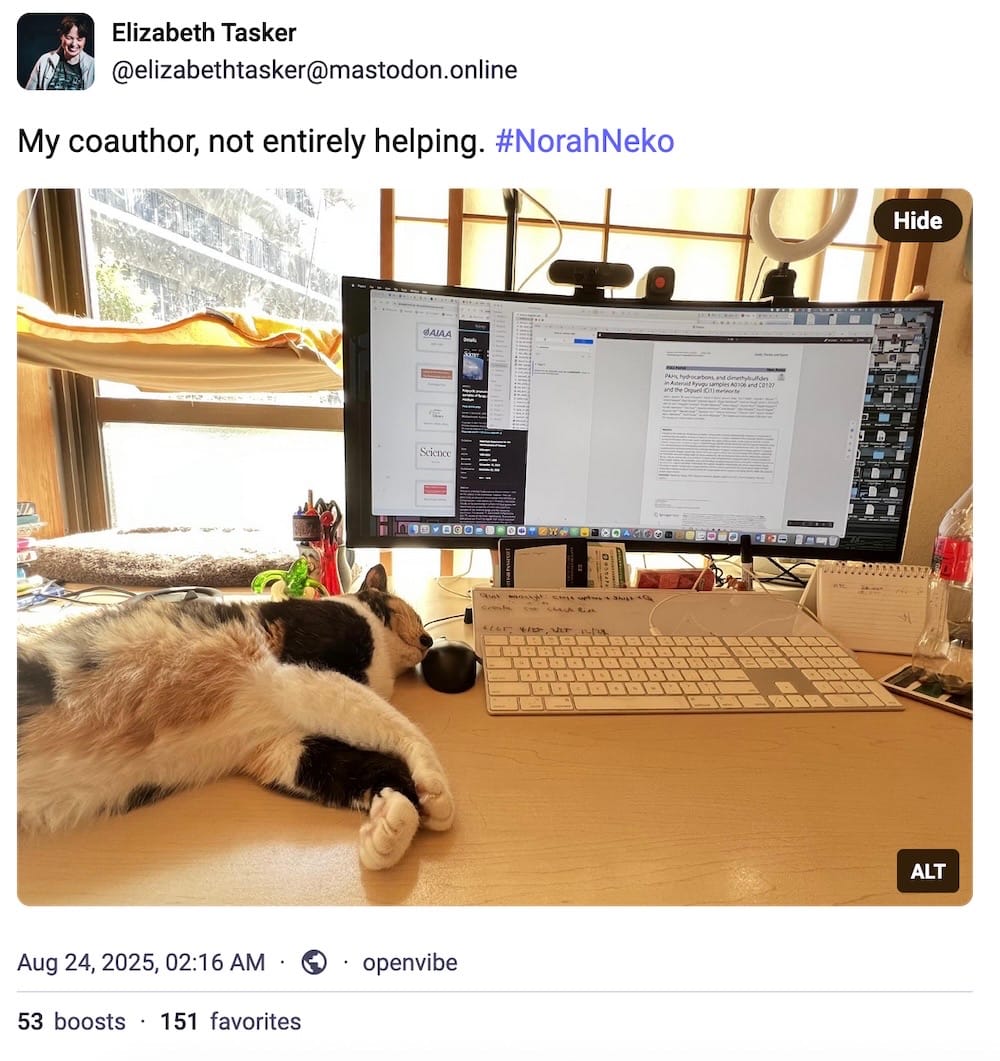
CYBER CATS & FRIENDS
This week's cyber cat is CISO Storm, who can be seen here supervising active defense from the cyber-security team. You're doing the absolute best work, Storm, keep it up. Thanks so much to Paul W. for sending in!

🐈⬛ Send in your cyber cats! 🐈⬛ Got a cyber-cat or a non-feline friend? Send me an email with their photo and name and they will be featured in a future newsletter!
SUGGESTION BOX
That's it for a very busy week in security. I'll be back as you'd expect next week with your usual round-up from the week, and more!
Thanks so much for reading and supporting this newsletter. It really means the world. As always, please get in touch if you have anything you want to share with me for the newsletter.
Catch you later,
@zackwhittaker