this week in security — august 31 2025 edition
THIS WEEK, TL;DR
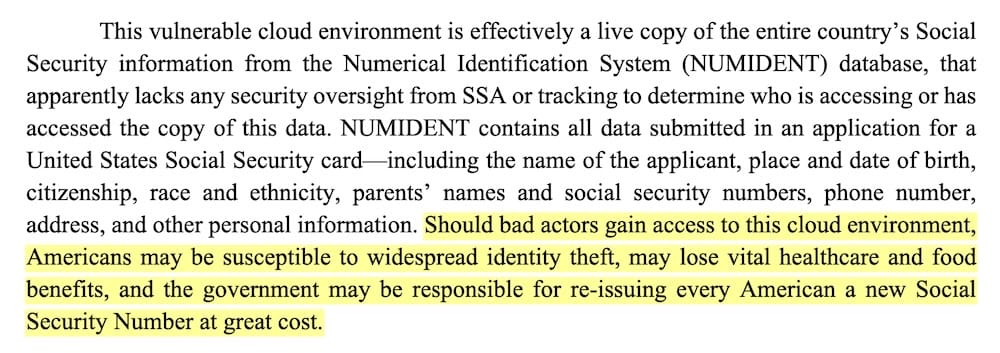
Whistleblower says DOGE put copy of Social Security database on 'vulnerable' cloud
NPR: We start this week with the absolutely stunning revelation from the now-former chief data officer Charles Borges at the Social Security Administration, who blew the whistle claiming DOGE copied the live U.S. Social Security database, known as Numident, onto an AWS cloud server run by the agency that lacked proper logging or access controls. This database of some 300 million Americans contains all the information submitted as part of a Social Security application, so if this information leaks or is breached, it's game over — everyone would need a new number, per Borges. The whistleblower said DOGE went around him and others to copy the data. By putting the data in an AWS cloud, the DOGE operatives could potentially make the data "publicly accessible" (even by mistake). Anyone who's heard of an open AWS S3 bucket (and there have been plenty over the years) will know the risk here. The whistleblower's complaint is very detailed and worth the read. Borges resigned Friday following his public disclosure. Wired ($) reported that his resignation email later vanished from staff inboxes. @Emptywheel has a very good short video explaining the entire saga, and there's also a good thread to check out by former 18F staffer @skiles.
More: DocumentCloud | Government Accountability Project | New York Times ($) | TechCrunch | @makenakelly | @emptywheel
Salt Typhoon hacked hundreds of companies, stole data on 'nearly every' American
Washington Post ($), The Register: The FBI's top cyber cops did the media rounds this week as a coalition of U.S. and international partners dropped new details [PDF] on China's Salt Typhoon hacking campaign by naming three new China-based companies involved in the hacks targeting critical infrastructure around the world. Per the FBI, the hackers have hit more than 600 companies in 80 countries (including the Dutch), 200 of which are American, including telcos and other tech giants. This access allowed the hackers to vacuum up call records and other data on "nearly every American," but specifically the calls and text messages of at least 100 high-ranking U.S. officials. Describing it as one of the "more consequential cyber espionage breaches" in U.S. history, the FBI said the hackers aren't done yet. With the new guidance, the U.S. and its partners hope to help mitigate the broad threat from this ongoing hacking campaign.
More: WSJ ($) | The Record | TechCrunch | UK NCSC
Salesloft cyberattack affects all Drift customers with data integrations
Google: Google sounded the alarm on a new hacking campaign targeting Salesloft customers who use its Drift AI product. Drift, which integrates with a bunch of cloud data services (like Salesforce), was somehow compromised and customer OAuth-connected integrations accessed, allowing the hackers to steal huge amounts of data from customers' connected cloud instances. Salesloft has an incident page, but Google isn't mucking around: "Treat any and all authentication tokens" connected to Drift as potentially compromised. This is likely part of a wider campaign targeting Salesforce and other cloud data, but Google said it's not yet clear on the hacking group's motivations, but it screams of ShinyHunters but a direct link hasn't been fully confirmed yet.
More: ~this week in security~ ($) | Cyberscoop | Ars Technica
TransUnion says hackers stole 4.4 million customer Social Security numbers
TechCrunch: Credit reporting giant TransUnion said in a filing with Maine's attorney general this week that more than 4.4 million customers had data stolen in a recent data breach affecting a "third-party application," which the company wouldn't name, describe, or comment about in general, or provide anything of substance regarding the breach. The company claims (without saying how it knows) that "no credit information" was breached, but later reported to Texas' attorney general's office that Social Security numbers were included in the stolen data. (Disclosure: I wrote this story!) Was this, then, another ShinyHunters breach? Likely, it seems, with DataBreaches.net reporting that the hacking group took credit for the theft of TransUnion's Salesforce instance (surprise, surprise) but that the 4.4 million number allegedly relates only to Social Security numbers and that the total number of affected individuals is likely far higher to the tune of 13 million. Meanwhile: Farmers' Insurance said a million customers had data stolen from an unspecified cloud vendor that ShinyHunters also took credit for.
More: DataBreaches.net | Bleeping Computer | PCMag
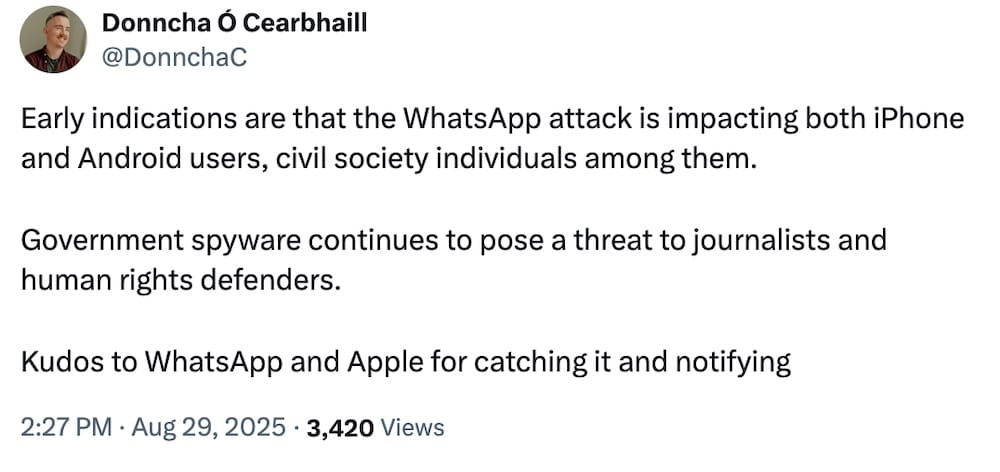
WhatsApp fixes 'zero-click' bug used to hack phones with spyware
TechCrunch: We now have more information about that Apple zero-day from last week… turns out the bug Apple fixed was used in conjunction with another vulnerability in WhatsApp to hack into the phones of Apple users and steal their data. Amnesty's security lab chief @DonnchaC said this was a spyware campaign that also targeted some Android devices. WhatsApp said the bug was fixed some weeks ago, and a spokesperson told me that the company sent out fewer than 200 threat notifications alerting users they may've been hacked. (Disclosure alert: I wrote this, too; busy week!) It's not clear who was behind the campaign (yet) but these things have a habit of coming to light in the weeks that follow, thanks to the tireless work by the folks at Amnesty, Citizen Lab, and Access Now, among others, who investigate surveillance abuses.
More: Reuters ($) | Bleeping Computer | 9to5Mac | @jsrailton thread | @techlore
THE STUFF YOU MIGHT'VE MISSED
Agentic AI browsers tricked into performing malicious actions
Guardio, Brave: Back to our regular feature, Misbehaving AI Corner™ (I still have no better name for this). Agentic browsers, aka web browsers with AI agents baked in that can perform actions on your data and browsing sessions, can be tricked just like regular AI agents. Case in point: Perplexity Comet, one of the most well-known agentic browsers today, can be duped with hidden prompt or instruction injections (such as hidden in source code on a website) into running malicious tasks. Both Guardio and Brave had research published this week detailing the risk.
Phishing emails caught abusing AI defenses
Malwr-Analysis.com: Ditto the above, but email as well. New research also shows some malicious emails now contain instructions designed to manipulate AI-based email defenses (see below). There are helpful IOCs in this blog so you can identify and block these attacks; plus, @neurovagrant collected a list of domains connected to the scam campaign that admins can use to block en masse.
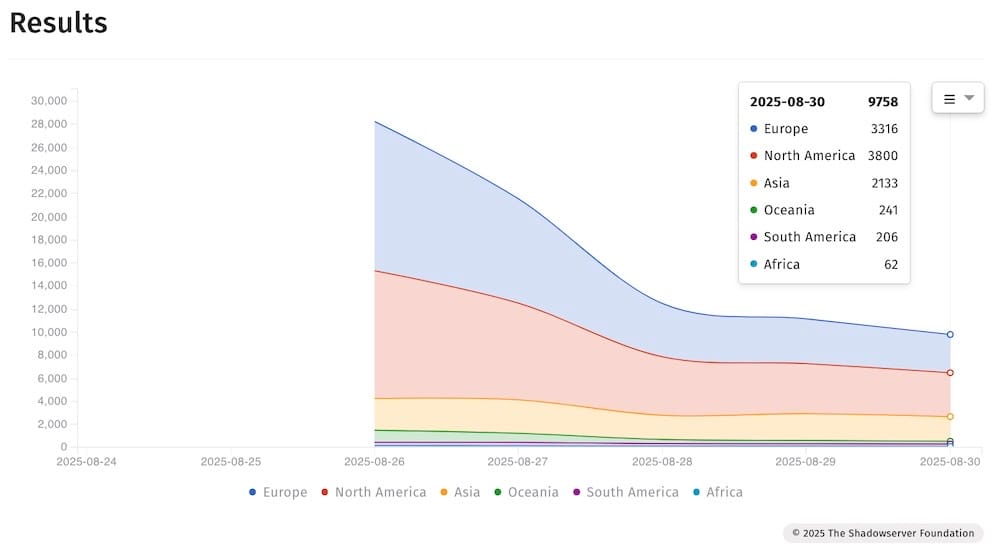
New Citrix flaw exploited to hack NetScaler customers
The Register: Alright, flip the "days since the last Citrix zero day" back to zero because, déjà vu, we're back again with another Citrix zero-day. This one is another bad flaw, aka CVE-2025-7775, which permits remote code execution on an affected NetScaler appliance. By all accounts, this bug is being used to pwn organizations everywhere. Thankfully the numbers of affected devices are declining, but are still in the thousands.
Google to require Android developers confirm their identity
Android Developers: Starting in March 2026, Google will begin requiring Android developers to provide government-issued ID documents for verification. Google says this will help cut down on the amount of malicious software in both the app store and sideloaded apps (which are often used by malware makers). This ID verification process will be required before their apps can run on certified Android devices. Look, I'd love to see an end to Android malware. Hell, I've been calling for the end of the stalkerware industry for years. But is collecting developer's IDs the best way to do this? Ehhh, I'm not so sure.
Google to launch cyber 'disruption' unit
Cyberscoop: Google looks to be dipping its collective feet into disruption waters by way of previewing its new… well, cyber disruption unit, aimed at taking a more-offensive approach to some cyber operations. Few details yet, but this move is likely to blow wide open the debate over "hacking back" and whether offensive operations can (or should) be used to take down malicious operations. But once hacking-back is let out of the box, it's not going back in.
DHS terminates 24 FEMA workers after alleged breach
Nextgov: Homeland Security Secretary Kristi Noem has fired the CIO and CISO of federal disaster response agency FEMA, as well as 22 others, over an alleged breach that allowed hackers into the network. Little is known about the incident, except that data was allegedly (hedging accordingly for obvious reasons) not stolen in the breach. (Firing staff is one surefire way to make people not want to come work with you and fix the things.)
TheTruthSpy stalkerware still putting victims' data at risk
TechCrunch: Security researcher Swarang Wade found a bug that allows anyone to take over any account for TheTruthSpy stalkerware and any of its clone spyware apps. The spyware maker's director, Van Thieu, whose operation I investigated and exposed in 2023, said he "lost" the source code so cannot fix the bug. (Disclosure: I co-bylined this story with @lorenzofb!)
Popular build platform Nx compromised to steal credentials
Wiz: Wiz and others are warning about a supply chain attack targeting users of the AI coding assistant package Nx on npm, which contains malware capable of stealing a user's credentials and other sensitive keys and then makes them public on GitHub. The keys were then used to set more than 5,500 private GitHub repos belonging to 400 users to "public." GitGuardian also has a good blog post on this attack.
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. As a working journalist, I don't run ads or accept sponsors for this newsletter. Please sign-up for a premium subscription for exclusive articles, analysis, and more.
OTHER NEWSY NUGGETS
CBP tapped cops' Flock cams: U.S. Customs and Border Protection were caught tapping into 80,000 license plate scanning cameras provided by surveillance vendor Flock to local police departments. CBP reportedly had access to "more Flock cameras than the average police department" and that CBP was "regularly using that access." Flock now says it's paused federal pilots. (via 404 Media ($))
Nevada hack stretches into weekend: Much of the Nevada state government's website is down after a cyberattack reported last Sunday. The state hasn't described the nature of the attack (yet), as the outage is likely to drag into its second week. Meanwhile: Bloomberg ($) looks at recent hacks targeting U.S. states in the wake of the Trump administration cutting cyber programs and budgets. (via Bleeping Computer, @Lombardo_Press)
IT supplier hack hits hundreds of Swedish municipalities: Swedish software provider Miljödata, used for managing sick leave and human resources reports, was hacked, affecting some 200 Swedish municipalities. Per the Swedish civil defense minister on X, it's "too early to determine the actual consequences" of the breach, but Swedish media reports an extortion demand was made. (via BLT ($), The Record, @CarlOskar)
Kremlin-ordered messenger designed to spy: No less than a week after the Russian government ordered that all new phones and tablets must be sold with a new messaging app called Max built-in (per Reuters ($)), security researchers have since described the app as a privacy nightmare whose purpose is to carry out location tracking and message surveillance. (via Forbes ($), @patrickwardle)
SK Telecom fined after SIM breach: South Korea has fined its top telecom giant SK Telecom some $92 million and ordered the company to improve its security posture. SK Telecom made some $13 billion (USD!) in revenue last year, so the fine is merely a drop in its financial ocean, given the breach included the private SIM card information of over 23 million subscribers. (via Bloomberg ($), Korea Herald)
Dodgy link bug can pop Passwordstate: Enterprise password manager Passwordstate has fixed a high-severity bug that allows hackers to gain admin access to customer password vaults by exploiting a maliciously crafted URL designed for gaining emergency access to Passwordstate. Patch today! (via Ars Technica, Click Studios)
THE HAPPY CORNER
You made it this far… you've earned your peace. It's time to chill in the happy corner.
This week, I spotted a cool project called Unf*ck.email that allows Gmail and Fastmail users to take control of their email inboxes without having to install an app, extension, or granting a third-party access to your inbox (all of which are bad for your privacy!). Thanks to in-built filters, Unf*ck.email uses keyword-based filters to direct your spammy incoming email into folders so you can keep ahead of your most important email. (Some 95% of my work email is noise and spam, and as such I aggressively use Gmail filters, so this Unf*ck.email is a smart approach to take). Of course, the project is also on GitHub.
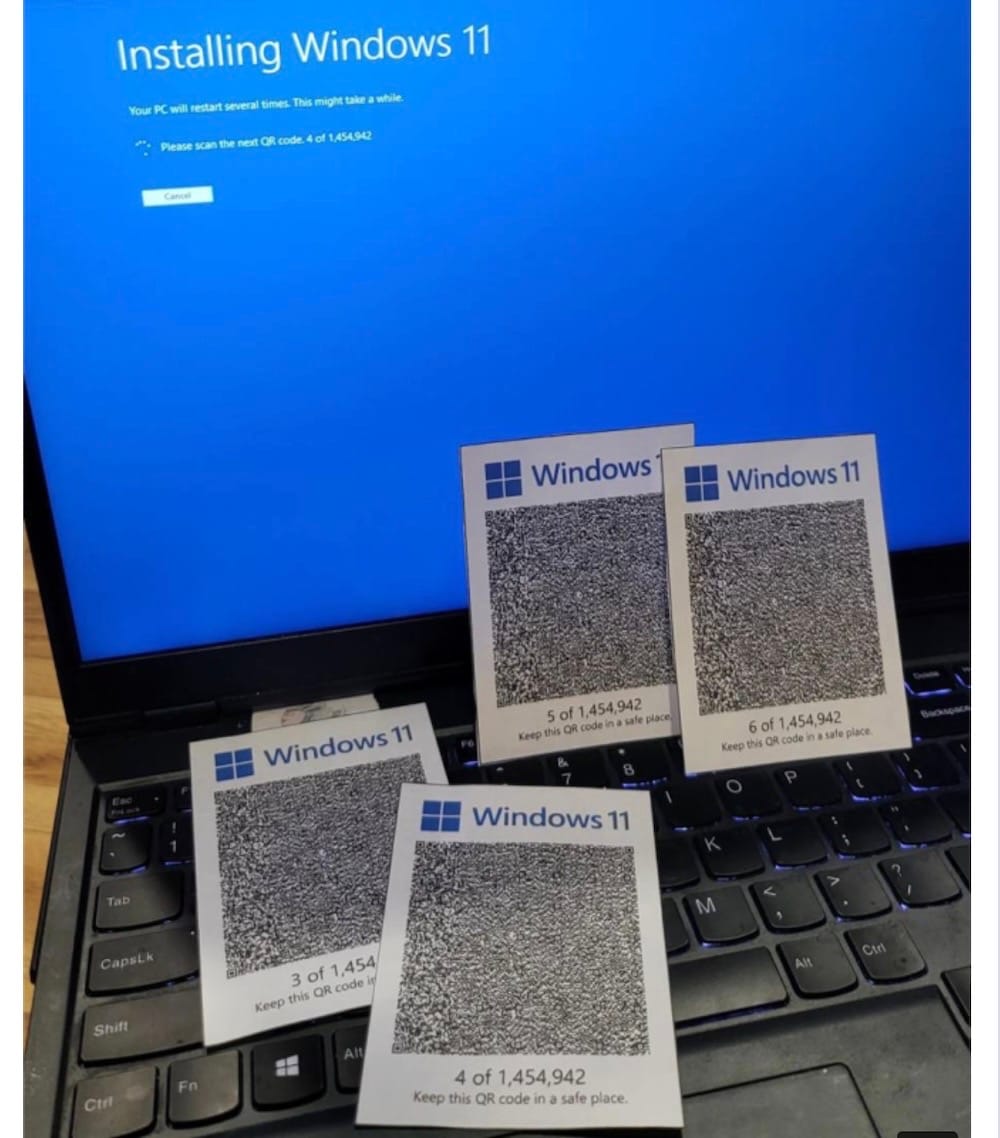
Good luck to @micr0, who is currently installing Windows 11 via QR code. Looks like they're on QR code #7 out of… 1.4 million or so to go… alright then! I'll be sure to check in soon... in the next few years… at some point… to see how it's all going.
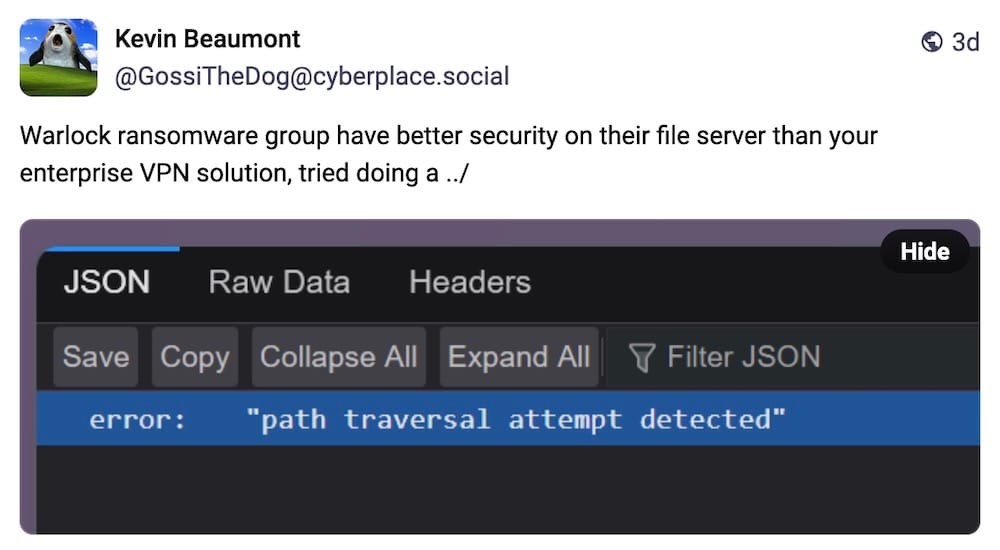
And here's @GossiTheDog this week with a reminder that ransomware gangs are taking their own cybersecurity more seriously than some enterprise tech giants take theirs (they know who they are!).
CYBER CATS & FRIENDS
This week's cyber cat is Oli, who can be seen here performing a cat-in-the-middle attack on his human's computer. Good luck with trying to shield your passwords from those prying eyes, buddy! Thank you so much to Joel F. for sending in!

🐈⬛ Please send in your cyber cats! 🐈⬛ It's been quiet on the cyber cat front of late...! Take a moment to send in a snap of your cyber-cat (or non-feline friend!) and their name, and they will be featured in an upcoming newsletter! (If you've sent in a cyber-cat before, feel free to send in an update!)
SUGGESTION BOX
And that's it for this week... going once, going twice... nope...? OK, that's it! Let's smokebomb out of here and I'll let you get on with the rest of your day.
As a brief programming note, I will be away next week and returning with your usual scheduled newsletter the week following. I haven't taken any time off or vacation yet this year, and so now that I have completed the move over to Ghost, I'm taking a breather to rest and recharge. I can't thank you enough for all of your kind words and comments since making the move. While I'm out, keep an eye out for a deep-dive blog I have landing later this week for premium subscribers, which I think you'll like and find helpful.
Thank you so much for reading this newsletter. As always, please do get in touch if you want to share anything. And please do send in your cyber cats!
Gone phishin'...
@zackwhittaker