this week in security — december 14 2025 edition
THIS WEEK, TL;DR
U.S. wants travelers to submit five years of social media history
USA Today: We start this week at the U.S. border, where the U.S. government is proposing that travelers entering the country on a visa waiver will have to submit selfies and at least five years of public social media history before being considered for entry. The move is ostensibly aimed at preventing immigration fraud, but is widely seen as a pretense for denying visas over political postings, which we're already seeing. The data grab will likely make it more difficult for many to come to the U.S. for any reason, such as going to conferences to share knowledge. Given the prospect of facing weeks in ICE detention over a border guard's hunch of your social media posts from years ago seems like enough of a reason to not want to come to the United States at all.
More: Federal Register | Sky News | PBS | CNN | BBC News
Petco exposes potentially millions of Vetco records due to website bug
TechCrunch: Rough week for Petco after not only confirming one security lapse, but two. The pet wellness company sent out a batch of data breach notices this week, revealing it had earlier this year accidentally exposed (without explaining how!) customers' names and addresses, but also driver's licenses and Social Security numbers(?!). The company hasn't said how many people are affected or anything of substance about the incident. But then I discovered a second major data breach, potentially affecting millions of people's personal information who took their pets to its Vetco clinics. I found the IDOR bug (disclosure alert!) and reported it to Petco, which promptly took the Vetco customer account site down. The company has said equally little about this one.
More: TechCrunch ($) | Chicago WGN9 | SC Media | @zackwhittaker
Doxers posing as cops are tricking tech firms into sharing users' personal data
Wired ($): Excellent reporting by Wired looking at how a prolific doxing group, as told to @davidgilbert by one of its members, would use fake subpoenas and altered screenshots of email requests to trick tech companies into turning over customer data as part of an fraudulent emergency data request — a process often used by cops to get data faster when there's an urgent risk to someone's life. This profile dives into a problem that's long been known about, but clearly still befuddling tech giants like Apple and Amazon (and smaller platforms like Rumble), as all have turned over data to the doxers by mistake.
Archive: KrebsOnSecurity | Bloomberg ($) | More: @davidgilbert
U.S. says hacktivists are conducting opportunistic hacks on critical infrastructure
CISA: Hacktivists are targeting critical infrastructure, such as water and meat processing plants, with opportunistic, low-skill hacks. This is in the same week that the Justice Department indicted an Ukrainian hacker for her alleged role in cyberattacks in these hacks, which prosecutors say were done in support of Russian geopolitical interests. The hacker allegedly worked for CyberArmyofRussia_Reborn, known as CARR, and NoName057(16). CARR was blamed for spoiling thousands of pounds of meat and triggering an ammonia leak at a processing plant in Los Angeles; while NoName was blamed for DDoS attacks targeting a range of websites.
More: Justice Department | Environmental Protection Agency | CNN | GovInfoSecurity | NBC Los Angeles | @realhackhistory
Apple, Google, Microsoft fix zero-days with security updates
The Register: Hold onto your hats, we've got security updates from everyone this week. This month's Patch Tuesday saw Microsoft roll out fixes for at least one Windows zero-day under attack; Fortinet patched a few software bugs, as did Adobe and SAP. But things really kicked off later in the week as Google fixed its eighth zero-day under attack in Chrome this year, setting off a firestorm of patches to fix Microsoft Edge (which relies on Chrome's engine), and updates for pretty much every flagship Apple product. If you haven't updated your devices, now would be a good time for it, as Apple said the bug was abused in an "extremely sophisticated attack against specific targeted individuals." Given that Google's unit dedicated to tracking government-backed threats found the bug, we can probably surmise that a government (or spyware) is to blame.
More: TechCrunch ($) | KrebsOnSecurity | Bleeping Computer | SecurityWeek | @lorenzofb
~ ~
THE STUFF YOU MIGHT'VE MISSED
Cargo stolen from delivery truck after hack
Bloomberg ($): Vape seller Fifty Bar is trying to recover a million bucks in stolen vapes after a delivery no-show. The company found one of its third-party logistics companies was hacked, with the going theory that hackers may have used their access to tell the real delivery driver not to show up on the day, and instead sent their own driver. Proofpoint detailed this threat some weeks ago.
Hackers who breached 700Credit stole over 5 million SSNs
TechCrunch ($): Another batch of at least 5.6 million Social Security numbers have been stolen after a hack at 700Credit, a Michigan-based firm that runs credit checks for car and auto dealerships across the United States. (Disclosure alert: I wrote this story!)
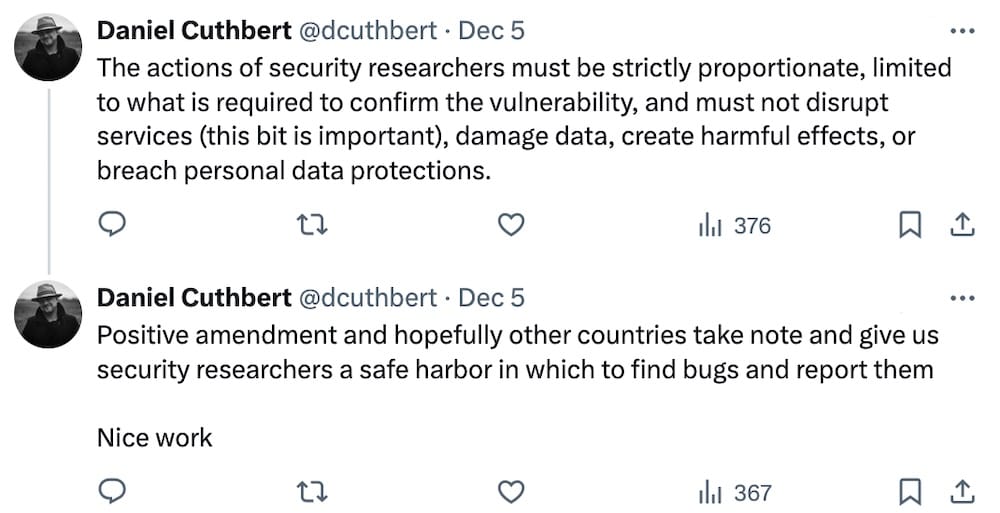
Following Portugal, U.K. plans to exempt researchers from hacking law
The Register: Portugal has amended its hacking laws by adding a provision to carve out exceptions for security researchers who operate in good faith, such as not downloading gobs of data or disrupting services (thanks for flagging @dcuthbert). Not to be outdone, the U.K. is also considering updating its decades-old law to include a "statutory defense" for security researchers.
Google post-mortem's Landfall spyware exploit targeting Samsung phones
Project Zero: Google's top security researchers ripped apart six malicious images found on VirusTotal that were packed with exploit code, capable of planting the recently discovered Landfall spyware on vulnerable Samsung Galaxy devices (patched earlier this year). The teardown looks at how image parsing libraries can be tricked into processing malicious code buried in images, which can be sent to victims over messaging apps.
Chatbot toys talk sex and parrot China talking points
NBC News: To almost nobody's surprise, a bunch of AI-enabled children's toys can be easily tricked into spitting out responses beyond their guardrails, such as discussing sex and replying to questions about Taiwan with pro-Beijing talking points. Brilliant work here by @kevincollier and team. I almost keeled over with laughter at this demo video.
React2Shell exploitation ramps up globally
GreyNoise: The good folks at GreyNoise say they're seeing a ramping up of React2Shell exploitation from across the world. Yes, China's top of the list of attacks, but so is Hong Kong, the U.S., Japan, and Singapore. The threat intel company also posted an update [PDF] this week detailing what they're currently seeing. Google and Amazon Web Services also have blogs for affected customers. (via @neurovagrant)
How one reporter cultivated a top Iranian top hacker as source
The Atlantic ($): Breathtakingly good reporting from @shaneharris, reliving a story from the mid-2010s, recounting how he cultivated a top hacker for the Iranian regime as a source, who told Harris some of Iran's most sensitive cyber secrets. The source vanished, and then the FBI turned up at the reporter's house. Harris is one of the best national security reporters out there, so his storytelling doesn't disappoint.
Man charged for wiping phone before CBP could search it
404 Media ($): A grand jury indicted an activist for allegedly wiping his phone before U.S. immigration officials could search it. The circumstances of the search aren't known but surely sounds like the government is trying to make its problem someone else's. In any case, this is a case worth watching, given… every modern device has this capability.
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing up for a paying subscription starting at $10/month for exclusive articles, analysis, and more, such as:
I've investigated 'stalkerware' for five years. Here's what I've learned
Thousands of North Koreans have secretly infiltrated US and European companies as remote IT workers
Banning TP-Link won't save America from its own terrible cybersecurity
~ ~
OTHER NEWSY NUGGETS
FTC upholds SpyFone ban: The Federal Trade Commission has denied a petition by Scott Zuckerman, the CEO of a company that provided stalkerware apps, to vacate or modify its 2021 order banning him from offering any monitoring products and services, and requiring him to implement an information security program. (via FTC, EPIC)
Coupang CEO out after breach: In an incredibly rare act of post-breach accountability, the CEO of South Korean retail giant Coupang, Park Dae-joon, has resigned following the massive theft of some 34 million people's data. (via Financial Times ($), The New York Times ($), Coupang)
India sat-tracking rattles privacy crowd: India's Modi government is planning to require smartphone makers enable always-on satellite tracking on their devices, per Reuters ($). Amnesty International called the move "deeply concerning," as the surveillance grab would put people like human rights defenders at risk. (via Reuters ($))
Flock f-cks up, twice: An Oregon police chief criticized surveillance vendor Flock for failing to deactivate its license plate scanning cameras, despite being asked to by local city officials. Meanwhile, Cambridge, Mass. officials said it was "terminating its contract" with Flock after the company installed two new cameras without the city's knowledge. If I were a Flock executive, I'd be avoiding both states for a while… (via The Record)
U.S. readies private sector to launch cyberattacks: Bloomberg's top cyber reporter @jamietarabay dropped this Friday bombshell: "The White House plans to make public its intention to enlist private companies in more aggressive efforts to go after criminal and state-sponsored hackers in a new national cyber strategy." Per @wylienewmark:
Danes say U.S. is a security risk: In what is surely absolutely unrelated news, the Danes are now describing the United States as a potential security risk as it prioritizes its own interests. Per the Danes' hovedkonklusion (page 6): the U.S. is “now using its economic and technological strength as a tool of power." (via Bloomberg ($), UDSYN [PDF])
Spain nabs teen hacker: Spanish police have arrested a teenager who allegedly stole 64 million records siphoned from at least 11 companies. Few other details have been released so far. (via Spanish Police, DataBreaches.net, The Record)
Germany blames Russia after air traffic hack: Berlin said it has "clear evidence" linking an August 2024 cyberattack on its air traffic systems to Russia's APT28, aka Fancy Bear. The hackers were also blamed for election interference efforts across the country in recent years. Russia rejected the claims, because of course it did. (via SRF, BBC News)
~ ~
THE HAPPY CORNER
Welcome back to the happy corner. And exhaaaaaaaaale.
Congratulations to 10 years of Let's Encrypt! The free HTTPS certificate issuer marked its 10 year anniversary this week as what is now the largest certificate authority in the world. At the rate it's going, Let's Encrypt will be hitting that billionth certificate in no time.
For my ~this week in security~ blog, I dive into some last-minute cyber and privacy gifts that your friends and family won't hate. Gift guides are often, well, crap, so this year — as someone who's very much a cyber nerd — I dug around for some sort of gifts I would want to buy for someone, as much as I'd be thrilled if someone got for me. Let me know what you think and if you have any suggestions I can add! (No affiliate links or junk!)
On this note from @LilahTovMoon; this is a reminder that if someone has helped you, let them know how much you appreciate them. You'll make their day, and it'll probably make yours, too.
A little bonus cybercat, because why not?
And lastly... As I mentioned last week, I have only three cyber-cat mugs left before they're gone for good. If you want a chance to receive one of these rare cyber-cat mugs (delivered worldwide!), sign up as an Astonishing admin for full access to my exclusive blogs, analysis, and more before the end of 2025 and your email address will be entered into a random draw to win one. The lucky three winners will be notified by email in January. I'll also donate 10% of all new annual Astonishing admin subscriptions for the month of December to a good cyber cause.
Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Hermes, who can be seen here deftfully reading every word of my newsle..z...Z...z z. .... Zzzzz.... hey, wait a minu...! Oh, never mind. I am told, however, that Hermes is especially helpful when his human reads the newsletter to catch up on all the cyber goings-on. Thanks so much to Ula for sending in! (And what a handsome lad!)
🐈 Please send in your snaps! 🐈⬛ Got a cat or a non-feline friend? Send me an email with their photo and name and they will be featured in an upcoming newsletter! If you've sent in a photo before, feel free to send in an update!
~ ~
SUGGESTION BOX
And that's this week's very busy, worldwide snapshot edition of ~this week in security~, thank you so much for reading (or, if you're reading the cybercats first — and I don't blame you — welcome to this week's newsletter!).
I'll be back next Sunday with all of the latest from the world of cyber, national security, and privacy. As for me, it dropped an absolute metric ton of snow overnight and so I'm going in search of some coffee.
Yeeting myself into the outside world,
@zackwhittaker