this week in security — december 21 2025 edition
THIS WEEK, TL;DR
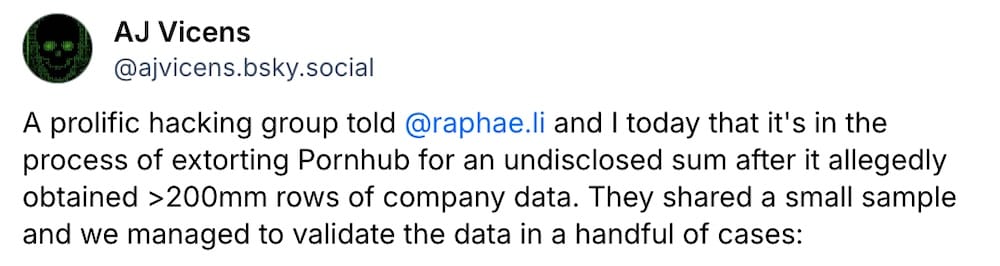
Mixpanel data breach spreads to SoundCloud, Pornhub users' viewing histories, others
Bleeping Computer: The data breach at Mixpanel is spreading and getting worse, with more of Mixpanel's corporate customers — and their users — now confirmed affected. First, OpenAI came forward, then SwissBorg, and now, SoundCloud has confirmed millions of its users had data taken, as did online casino site Stake. But even worse, PornHub users who signed up and paid for access had their registered email address and viewing histories taken in the Mixpanel breach. That's horrifying for a lot of people and for obvious reasons, and just goes to show how bad this Mixpanel breach is. Mixpanel claimed it wasn't actually to blame for the PornHub breach — even though Reuters ($) confirmed the data was accurate by obtaining a copy from the ShinyHunters hackers, who took credit for the breach, and verified with affected users. But Mixpanel's CEO still hasn't answered even the most basic questions about the hack. Sticking your head in the sand only gets you so far for so long.
More: TechCrunch ($) | Reuters ($) | @raphae.li | @mattjay
No patches yet for new Cisco zero-day under attack, affecting hundreds of companies
Cisco: Cisco's very bad year of security flaws hit a perfect 10/10 this week when the tech giant disclosed a top-rated critical bug (tracked as CVE-2025-20393) being used to attack its email and web gateway products. Per Cisco Talos, the company's internal team of hacker trackers, China is likely to blame for the cyberattacks, which Cisco detected on December 10 (but said nothing publicly at the time) and still has no patches available at the time of disclosure a week later, leaving customers pretty much on their own. As such, compromised devices have to be wiped and reset. Data suggests hundreds of companies might be affected. That said, Cisco said devices are only vulnerable if they are reachable from the internet, and have the "spam quarantine" feature enabled — neither of which are enabled by default. This is Cisco's latest cyber-fustercluck this year, thanks to its own buggy products and lackluster security. Meanwhile: Not to be outdone, HPE warned its OneView IT management software has a major bug also with a 10/10 severity score, so patch today before this one is inevitably exploited.
More: Cisco Talos | HPE | Help Net Security | SecurityWeek | TechCrunch ($) | The Register | @mttaggart | @GossiTheDog
Ransomware gang takes credit for hack of U.K. NHS tech vendor
TechCrunch ($): DXS, a little-known tech provider for NHS trusts across the U.K., was hacked, according to a statement published on the London stock exchange on Thursday. While NHS patient records are (generally) decentralized and not stored in a single place, DXS' software runs on the computers in thousands of doctor's offices and handles patients' data, granting the software potentially vast access to personal and medical information. Days prior to the company's statement, a ransomware gang called DevMan took credit for the DXS breach, and claimed to have stolen 300 gigabytes of data. The company notified the ICO, as it's required to do in the event of a data breach, so there's something there. Expect this breach to potentially further unravel down the line.
More: The Register | The Record | Digital Health News
Emails stolen in French interior ministry breach; U.K. government also confirms hack
Euronews: France's Interior Ministry confirmed early in the week that its email servers had been hacked, but its blasé response made it seem like it wasn't a big deal. Until… it was. French media later reported that emails and criminal record files were stolen, while the hackers claim (without evidence thus far) that it stole data on millions of people. France's Interior Minister blamed the sharing of passwords on messaging apps for the breach. (Or, rather, lack of security controls by the ministry itself. "Oh non!! Le mot de passe était 'intérieur'!") According to @gabrielthierry, authorities arrested a 22-year-old "already known to the justice system" through a 2025 conviction of a similar offense. Also this week: BBC News ($) reports the U.K. Foreign Office confirmed systems it operates on behalf of the Home Office, the country's interior department, were hacked. The U.K. didn't have immediate answers, despite knowing about the hack since October.
More: Le Monde ($) | Le Figaro | RTL | Associated Press
~ ~
THE STUFF YOU MIGHT'VE MISSED
Schools are surveillance states, but little proof tech keeps kids safe
Forbes ($): Given the dizzying number of shootings in the U.S., many schools are turning to high-tech surveillance, from drones to license plate readers and bathroom listening devices — and many featuring AI — despite little evidence that the tech contributes to school safety in any meaningful way. But schools are still hooked on this questionable tech. “This community wants… whatever we can do to make our schools safer,” said one school district superintendent. “If that means you have armed security and drones and AI and license plate readers, bring it on." Anything but the guns, though…
TikTok sold to U.S. investors, including UAE firm, despite national security risks
Axios ($): A years-long effort to divest TikTok from its Chinese owners under the guise of alleviating national security concerns is now done, as the video sharing app is now in the hands of U.S. investors, including Oracle, Silver Lake, and… a UAE-backed AI investment fund. Wait, what?! This certainly weakens the government's alleged national security argument and looks more like a corporate land-grab. All this in the same week that an a16z-backed phone farm startup flooding TikTok with AI-generated garbage was hacked, as 404 Media ($) discovered.

Dormant domains caught serving malware
KrebsOnSecurity: Many parked domains, such as registered or dormant websites (often as misspellings of popular brands), are now serving malware, per Infoblox research. Never a better reason to install or set up an ad-blocker!
Browser extension with 8 million users collected AI conversations
Ars Technica: Security firm Koi found eight Chrome extensions with collectively 8 million users that were harvesting and uploading users' complete AI conversations to the internet. This security lapse was discovered despite Google and Microsoft slapping "featured" badges on the extensions in their stores.
Airline website bug exposed access to millions of flight records
Alex Schapiro: Belatedly adding this story from November (whoops), in which Schapiro found an exposed API endpoint on an airline's web systems. This meant it was possible to brute-force a customer's six-character alphanumeric flight record (PNR) code only and without a corresponding surname, allowing access to potentially millions of passengers' reservations and personal information.
Self-hosting users describe fallout from hackers exploiting React2Shell on their servers
Jake Saunders: Home server hobbyists beware: Several people have found their self-hosted servers breached thanks to hackers exploiting React2Shell. In some cases, victims didn't know they were vulnerable to begin with, because they weren't aware the software they hosted (like Umami) relied on Next.js. This write-up might help you dig into any compromises.
Long-time Apple user has entire account locked after redeeming bad gift card
Paris Buttfield-Addison: A horror story as long-time Apple customer Buttfield-Addison tried to redeem what appears in hindsight to have been a tampered gift card bought from a reputable retailer, which triggered a full Apple Account lockout, including his devices. The situation (and resolution) notwithstanding, we are overly reliant on tech giants as custodians of our data, and we have no recourse for when things go wrong. (Oh, and avoid gift cards like the plague.)
~ ~
~this week in security~ is my weekly cybersecurity newsletter supported by readers like you. Please consider signing up for a paying subscription starting at $10/month for exclusive articles, analysis, and more, such as:
I've investigated 'stalkerware' for five years. Here's what I've learned
Thousands of North Koreans have secretly infiltrated US and European companies as remote IT workers
Banning TP-Link won't save America from its own terrible cybersecurity
Last-minute cyber and privacy gifts your friends and family won't hate
~ ~
OTHER NEWSY NUGGETS
Venezuela oil export hack: Venezuela’s state-run oil company is struggling to restart its systems after a cyberattack last weekend. No idea who is behind it, but one might be forgiven into thinking it has something to do with a good chunk of the U.S. military floating just off the country's coast. CNN reported cyberattacks on Venezuela were used during Trump's first term. (via Bloomberg ($), Reuters ($)
TV makers sued for screenshotting: Texas attorney general Ken Paxton is suing television makers for allegedly taking screenshots of customers' TVs and sending them back to their servers without the user's knowledge. Paxton says this violates the person's "fundamental right to privacy," which… yeah… (via Bleeping Computer)
Google sues Darcula: No, not the fanged vampire Dracula… Google is suing Darcula, the moniker of a prolific spammer behind massive numbers of fraudulent text messages purporting to come from USPS, the IRS, and major tech companies. Google is hoping its filing will convince a court to allow the search giant to seize Darcula's domains, which might also help identify more about the spammer behind the operation. (via NBC News)
U.S. finally nominates new NSA director: The National Security Agency might get a new director after eight months of rudderless leadership, if the Trump administration can get the nomination of Joshua Rudd over the line. Rudd is the deputy commander of Indo-Pacific Command, giving him insights into the ongoing diplomatic stalemate with China. (via The Washington Post ($), The Record)
Ransomware negotiators switched sides: Ryan Clifford Goldberg, a former incident response supervisor at Sygnia, and Kevin Tyler Martin, who was a ransomware negotiator for DigitalMint, pleaded guilty to accusations they switched sides and began working for a ransomware crew. A third alleged conspirator wasn't named and hasn't been charged. (via Bloomberg ($), Cyberscoop)
~ ~
THE HAPPY CORNER
Welcome back to the happy corner, where we celebrate everyone and everything this particularly festive season. Happy holidays to all!
Is it just me or does Windows XP look a little different today?
Here's @lookitup.baby with proof that hackers really are the best kinds of people.
I'm not saying a password vase is the way to go, but a password manager is definitely easier to put in your pocket and take with you.
Today I learned that the fictional Nakatomi Plaza in Die Hard, one of the quintessential Christmas movies (a stated fact, this is not in dispute), runs on Unix.
And, your bonus inspirational cybercat of the week.

Got good news to share? Get in touch! this@weekinsecurity.com.
~ ~
BUT WAIT! ONE TWO QUICK THINGS
Before you go and enjoy the rest of your day, just a couple of final things:
If you want to win one of a handful of ~this week in security~ cyber-cat mugs left in circulation, this is your last chance! Sign up as an Astonishing admin (for full access to my exclusive blogs, analysis, and more) before the end of 2025, and your email address will be entered into a random draw in the new year to win a limited edition mug. As I mentioned last week, I'll also donate 10% of all new annual Astonishing admin subscriptions for the month of December to a good cyber cause!
‼️ And finally: Are you a security researcher or journalist? We want to hear from you! Dissent Doe at DataBreaches.net and I are exploring the state of legal and criminal threats faced by researchers and reporters. Please take our survey to help us understand the threats faced today!
~ ~
CYBER CATS & FRIENDS
This week's holiday season cyber-cat is Maverick, who can be seen here in the festive spirit diligently checking their human's cybersecurity homework. Thank you so much to Ethan (representing Mr. Pudaloff's cybersecurity class) for sending in!

🐈 Please send in your cyber-cats! 🐈⬛ Got a cat or a non-feline friend? Drop me an email with their photo and name and they will be featured in a future newsletter!
~ ~
SUGGESTION BOX
On a personal note, this is my final newsletter of the year (le gasp!) But, really, that just means I'll be skipping next week's edition to rest and recoup with my partner, Jordan, and my cats, after a very busy year of reporting (and not taking much vacation time!). I'll be back with your regular weekly dispatch of cyber news on January 4, 2026.
I am incredibly thankful for you and your readership, and for supporting this newsletter (and now blog, following my move to Ghost earlier this year!). It's a joy and a privilege to write this newsletter for you every week. Thank you for reading, thank you for your feedback, your outreach — and your cyber-cat (and friend!) submissions — and, thank you for trusting me to be your guide through the world of cyber.
Have a wonderful holiday, wherever you are. I hope you get some time to relax and chill, and I'll catch you in the new year. As always, you can reach out to me any time with suggestions, feedback, or anything in-between for the newsletter.
Until then, my friends.
@zackwhittaker